
How CISOs Protect Shareholder Value
When a CISO informs the Board of Directors, what’s the top metric to report? CISOs must prove that they are protecting shareholder value. To do so, CISOs must demonstrate that their program yields maximized value and minimized risk for shareholders. CISO Board Value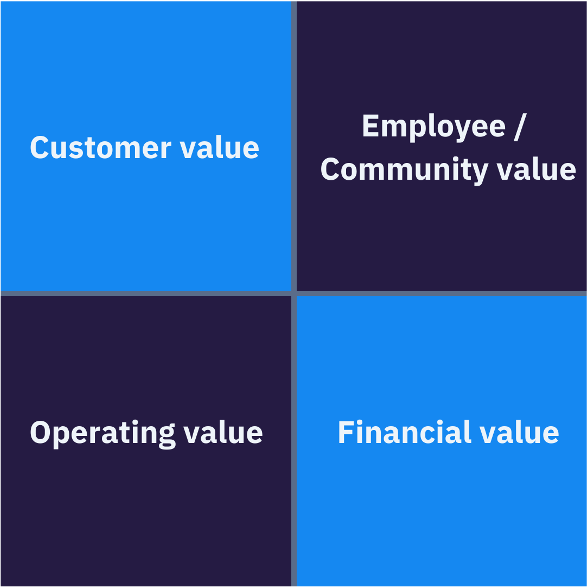 Shareholder value is constituted of:
Shareholder value is constituted of:
- Customer value
- Employee / Community value
- Operating value
- Financial value
When we examine the four areas of shareholder value, we see where CISOs can show specifically how they are protecting shareholder value.
Customer value
What are the benefits and risks of cybersecurity for customers? If a CISO can safeguard customers’ personally identifiable information and business data with your organization, that is a significant way to demonstrate protecting shareholder value. Another way to demonstrate that you are diminishing risk to customers is to share that your data protection policy complies with the General Data Protection Regulation Act (GDPR) in the European Union, and the Consumer Privacy Act (CCPA) in California. Try this exercise to articulate your customer value to shareholders:
- List all the ways that your cybersecurity program protects customers.
- Quantify how many customers are protected.
- Quantify the annual monetary value of those customers who are protected.
Employee/Community value
What are the benefits of cybersecurity to your employees or community members? If a CISO can prove that they are maximizing benefits and minimizing risk to their employees/community, that is a valuable way to demonstrate protecting shareholder value. Try this exercise to articulate your employee/community value to shareholders:
- List all the ways that your cybersecurity program protects its employees/community.
- Quantify how many employees/community members are protected.
- Quantify the annual monetary value of those employees or community members who are protected.
Financial value
What are the benefits of cybersecurity to your business success? If a CISO can prove their programs maximize benefits and minimize risk for the business, that is a strong way to demonstrate protecting shareholder value. Try this exercise to articulate your financial value to shareholders:
- List all the ways that your cybersecurity program protects the business.
- Quantify how much of the business is protected.
- Quantify the annual monetary value of the business that is protected.
Operating value
What are the benefits and risks of cybersecurity to your operations? If a CISO can prove that they are supporting changing computing environments despite increased risk (example, after cloud migration or after allowing employees to work remotely), that’s an effective way to demonstrate supporting operations. Try this exercise to articulate your operating value to shareholders:
- List all the ways that your cybersecurity program protects operations.
- Quantify how much of the operation is protected.
- Quantify the annual monetary value of the operations that are protected.
 Forecast potential losses
Forecast potential losses
In addition to reporting how they protected shareholder value, CISOs also commonly report projected losses from data breach. If the average cost of a data breach is 8.8 million dollars, how many 8.6 million dollar data breaches would you forecast for your organization? In order to forecast the likelihood of a data breach, one needs to estimate the size and vulnerability of an organization’s attack surface.
Size up your attack surface
Size matters when it comes to securing an attack surface. These days, CISOs must secure data on devices, routers and networks that are beyond their control — and visibility. The attack surface has grown exponentially for CISOs because of:
- Remote access to data from unsecure devices, routers, and networks
- The acceleration of digital transformation and migration to cloud
The shift in how and where data is accessed means that data is now beyond the reach of many CISOs. When forecasting potential losses caused by data breach, make sure to estimate the size of your attack surface inside and outside the IT perimeter.
Determine your vulnerability
Did you know that there are plenty of misconfigured AWS S3 buckets, compromised credentials, and misconfigured IoT devices that are easily found on the web? When forecasting potential losses caused by data breach, make sure to estimate the vulnerability of your attack surface. To get a glimpse of how many open servers are leaking data for your company, try our live scan. Criminals and security researchers try to detect vulnerable “things” connected to the web, including company data on misconfigured cloud storage, shadow IT, and more.
Use a digital risk platform to protect shareholder value
When a CISO reports how they protect shareholder value, they can include their use of a digital risk protection platform, like CybelAngel. With CybelAngel, CISOs can easily generate reports for the Board that demonstrate how data is safeguarded in the cloud, on third-party sites, and on the dark web. With a larger attack surface and greater vulnerability than seen in the past, data leaks outside the IT perimeter are inevitable; but damage is optional. To protect shareholder value, top organizations around the world contact CybelAngel to monitor their attack surface. For more on protecting shareholder value, see our series for CISOs: How CISOs weave cybersecurity into business strategy, part one and part two. So when you report how your cybersecurity programs protect shareholder value, remember to include CybelAngel in your proof. CybelAngel helps CISOs avoid reporting costly data breaches to the board. With CybelAngel, CISOs have the latest in cybersecurity to detect and remediate data leaks before they become data breaches, which helps keep shareholders happy.