What’s Fueling the Ransomware Growth Spike?
Banking trojans are alive and well. Ready to attack.
Ransomware attacks are expanding in such proportions that they have become emblematic of 2020 in Infosec. They affect every business sector, and their intensity is growing. Moreover, 2020 clearly showed an innovating trend from ransomware gangs, with new forms of pressure to obtain the ransom (read our article about Maze, whose techniques are now imitated by 15 other gangs) to professional, business-like behavior when arranging the extortion (read our blog about the CWT hack and their negotiations with the hackers). Analysts are offering numerous reasons to explain the increase in ransomware spreading: lower “barriers-to-entry,” development of “Ransomware-as-a-service” as a complete proposal in the cybercrime ecosystem… but the “old” established players also rode the wave and raised their game. Some of these ransomware actors now inject their own infection capabilities to spread and expand the attack scope of malware they did not develop. The scheme is known as an “affiliate program.” It is notably the case of mature threat actors launching massive banking trojan campaigns, such as Trickbot, Dridex, or Emotet.
Dridex
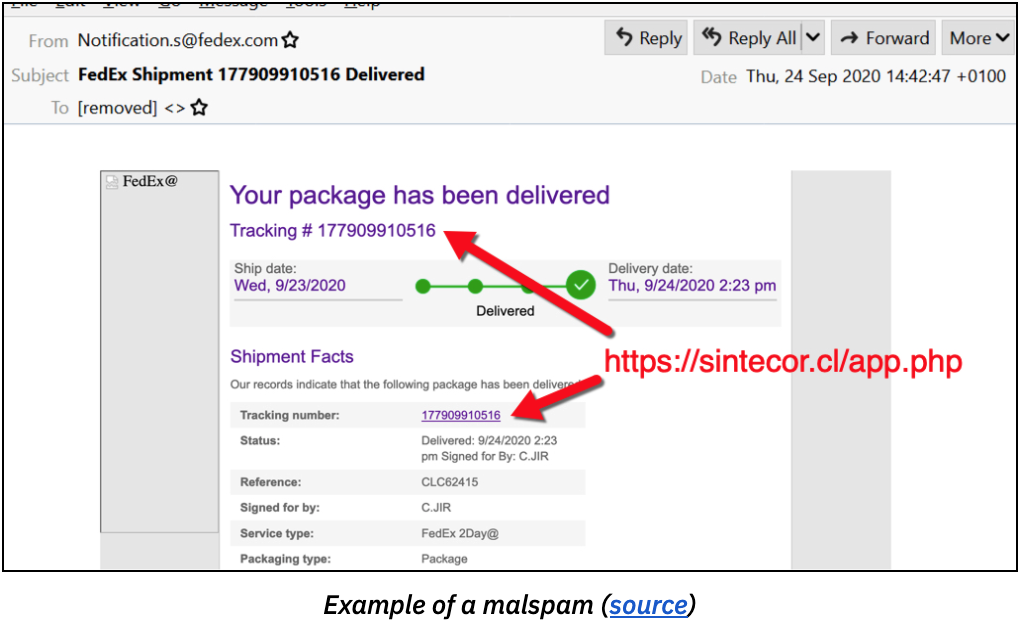
Like a cybercriminal’s swiss-army-knife, the Dridex malware evolved from a banking trojan to operating various modules such as a keylogger, web injection, remote control, spam, etc. It is now used as the initial delivery mechanism for targeted ransomware attacks, such as WastedLocker. Dridex has recently been on a surge (since mid-September 2020), through a worldwide phishing campaign that exploits fake invoices allegedly sent by FedEx and UPS. 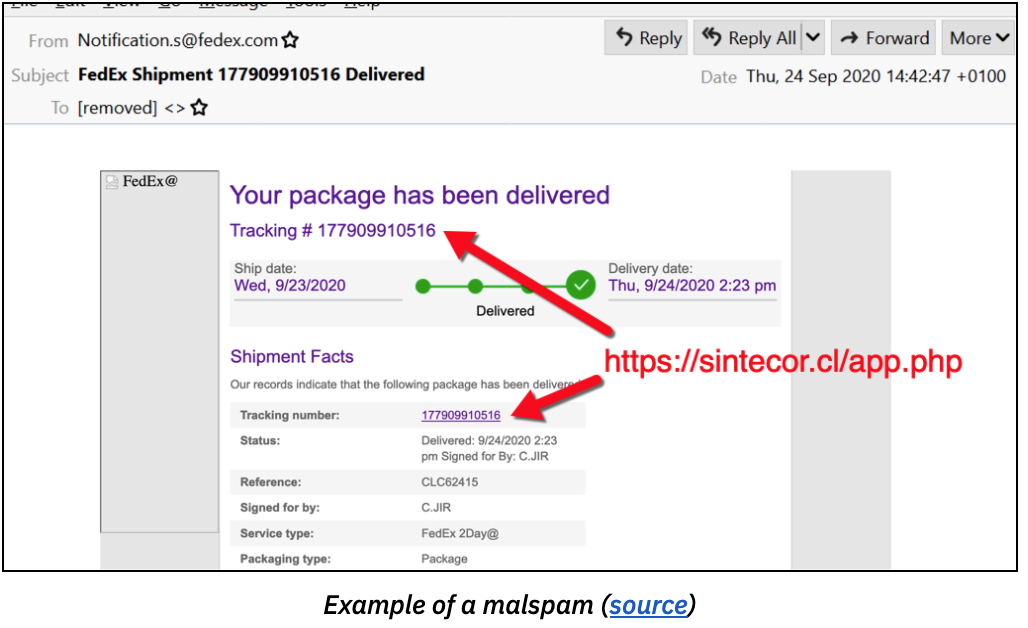
Trickbot
The Healthcare industry continues to be a top-target for cybercriminals that look for valuable PII from patient information. As recently as two weeks ago, 48,000 documents (240 GB) were first stolen from New Jersey University Hospital’s network, then encrypted by a malware called SunCrypt. Two months earlier, an UH employee was reportedly infected with the TrickBot trojan. Though remediated, this incident apparently opened the door to further compromise the full IT system and the deployment of SunCrypt. Furthermore, the group (allegedly part of the Maze cartel) claimed to possess UHNJ’s files on their website: 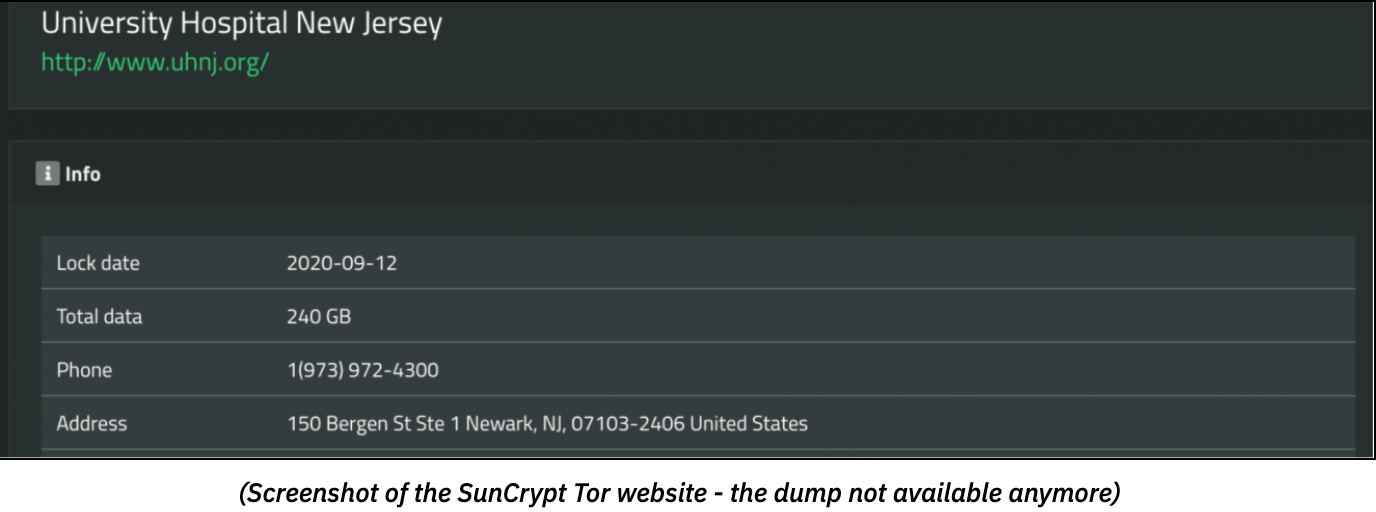 Historically, Trickbot was infamous for spreading Ryuk, another ransomware family. Recent observations show that it is now pushing the Conti ransomware, branching its service out.
Historically, Trickbot was infamous for spreading Ryuk, another ransomware family. Recent observations show that it is now pushing the Conti ransomware, branching its service out.
Emotet
As the most used malicious code of the last few years, Emotet deserves its reputation as one of the top threats. Like Dridex, it evolved from a simple banking trojan to a multitask set of tools. Emotet has not been used as a banking trojan since 2017, but has widely distributed other malicious payloads — for example, other trojans such as IceID, BokBot, Qbot or ransomware. After a 5-months calm period, Emotet has surged since last July, spreading less indiscriminately, targeting big organizations, especially in Europe and East-Asia. Beyond the classic phishing email campaigns, the threat actors also set up a new email thread hijacking technique. Once a mailbox is infected, Emotet extracts the content of certain emails, then automatically craft emails that look like an answer to a pre-existent email thread (e.g. “Re: re: re: lorem_ipsum” or “Fwd:” ). Thus, the victims are more likely to download the attached files and allow macros to compromise their computer. Corrupted files may also be spread through malicious URLs, giving a malicious payload hidden on legitimate websites access to a host (read our story about this attack vector). Users may lower their guard, as the domain is a well-known and legitimate service. 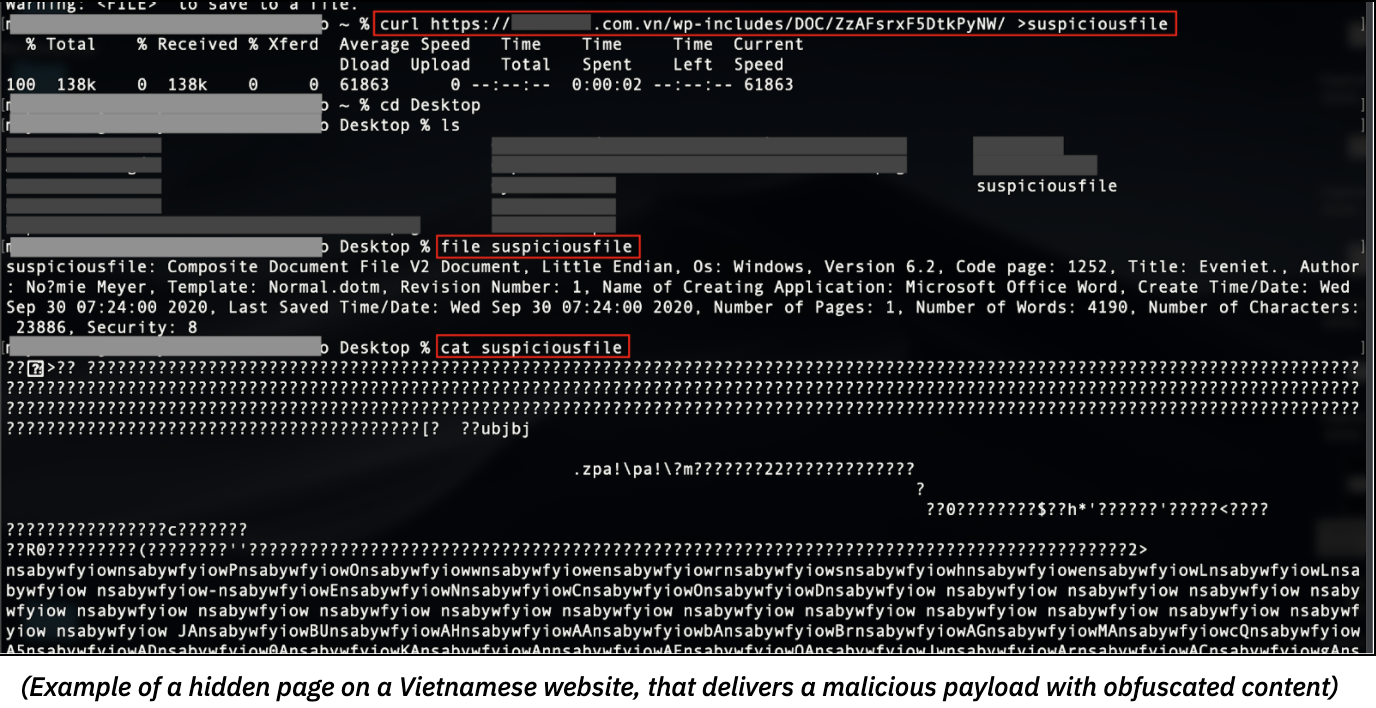 Whether the attacks target specific organizations or aim to spread worldwide, the initial infection vector remains a form of phishing, more or less skilled and personalized. Hence, beyond antivirus and hardware protection systems, the best way to prevent your organisation from infection is to improve training and security measures against social engineering, account takeover and cybersquatting, that deceive employees. By monitoring data leaks on all layers of the internet, and by protecting customers’ intellectual property, brands and employees’ personal information, CybelAngel provides a comprehensive and relevant solution to prevent social engineering schemes and IT system infections.
Whether the attacks target specific organizations or aim to spread worldwide, the initial infection vector remains a form of phishing, more or less skilled and personalized. Hence, beyond antivirus and hardware protection systems, the best way to prevent your organisation from infection is to improve training and security measures against social engineering, account takeover and cybersquatting, that deceive employees. By monitoring data leaks on all layers of the internet, and by protecting customers’ intellectual property, brands and employees’ personal information, CybelAngel provides a comprehensive and relevant solution to prevent social engineering schemes and IT system infections.
CybelAngel can prevent a breach of your data
Do you know the scope of your organization’s risk for a data breach? Get your free CybelAngel dashboard. See where your company’s data is leaking, and how your digital risk compares to other organizations in your industry. Click here to get your company’s complimentary Data Leak Dashboard. If you suspect a data leak, contact us. Because data leaks are inevitable, but damage is optional.