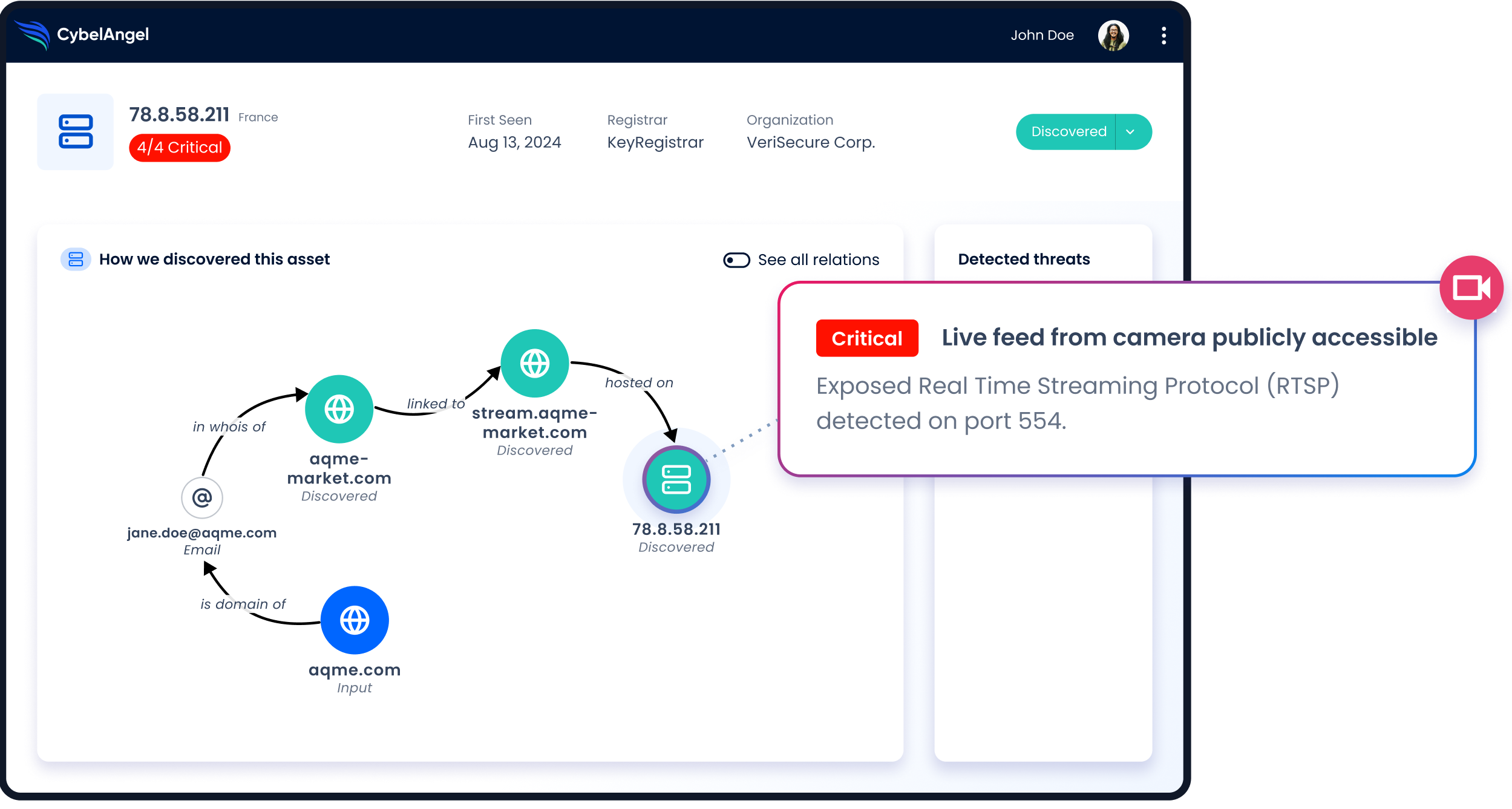
Detect all shadow assets, such as connected file servers, SaaS solutions, databases, industrial systems, DevOps tools, remote desktop services, and IoT devices
Discover
- Shadow assets, including connected file servers, SaaS solutions, databases, industrial systems, DevOps tools, remote desktop services, and IoT devices.
Attribute
- Assets to who they effectively belong, while visualizing all the connections that led to their discovery, and reduce your attack surface
Prioritize
- Concentrate on identifying highly vulnerable machines using a risk-driven scoring approach that is tailored to your specific business needs and realities.
“With CybelAngel, we establish a new border of detection outside of our architecture, encompassing the world of our partners and suppliers, where we can’t, by design, take control of their security.”