Credential Intelligence: How to Turn Leaked Logins Into Early Warnings

Table des matières
Passwords get leaked all the time. It might be a misconfigured cloud bucket or malware on an employee’s laptop. But whatever it is, it doesn’t take much for credentials to end up in places they shouldn’t. And once they’re out there, they can cause all sorts of damage.
That’s where credential intelligence comes in. It gives security teams real-time visibility into stolen logins, so they can catch threats early, trace the source, and shut down account takeover attempts before they spread.
What is credential intelligence?
Credential intelligence helps security teams detect and respond to leaked or stolen login credentials.
And it’s more than just spotting exposed passwords. It’s also about understanding where those credentials came from, how they’re being shared, and whether they’ve already been used in an attack.
This intelligence comes from real-time sources like breach dumps, malware logs, dark web forums, and paste sites. When a match is found, security teams can resolve it fast, resetting passwords, adjusting access, or triggering incident workflows.
For example, CybelAngel’s credential intelligence services will identify compromised credentials via:
- Infostealer malware
- Dark web forums
- Unsecured databases
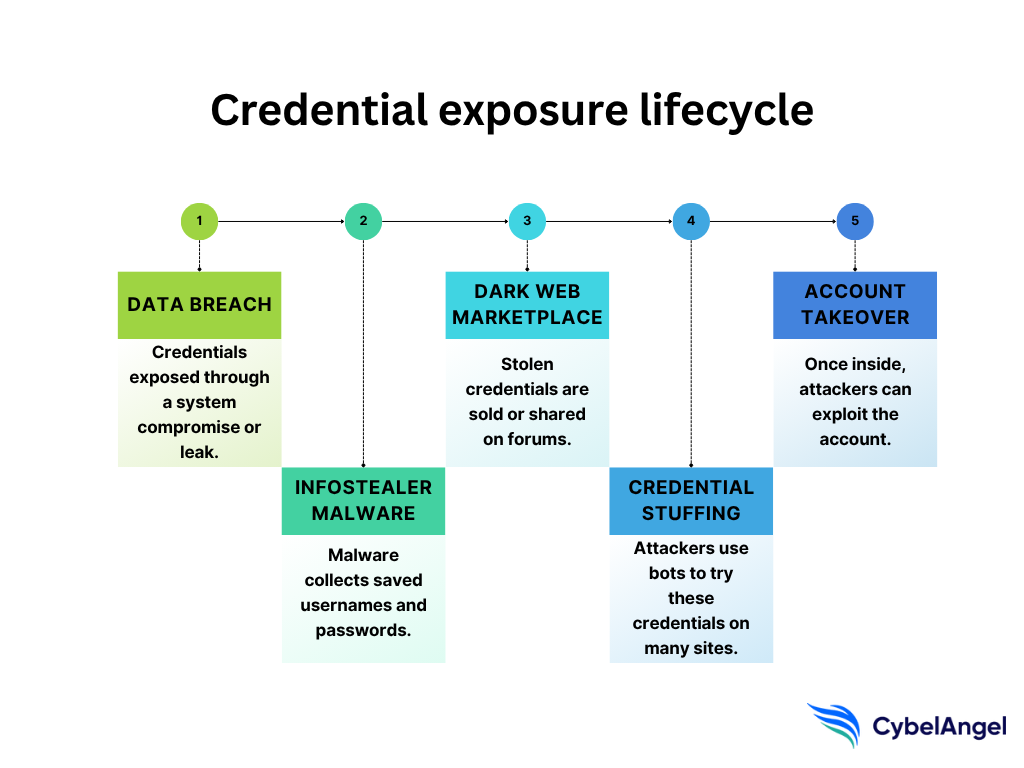
The lifecycle of a compromised credential
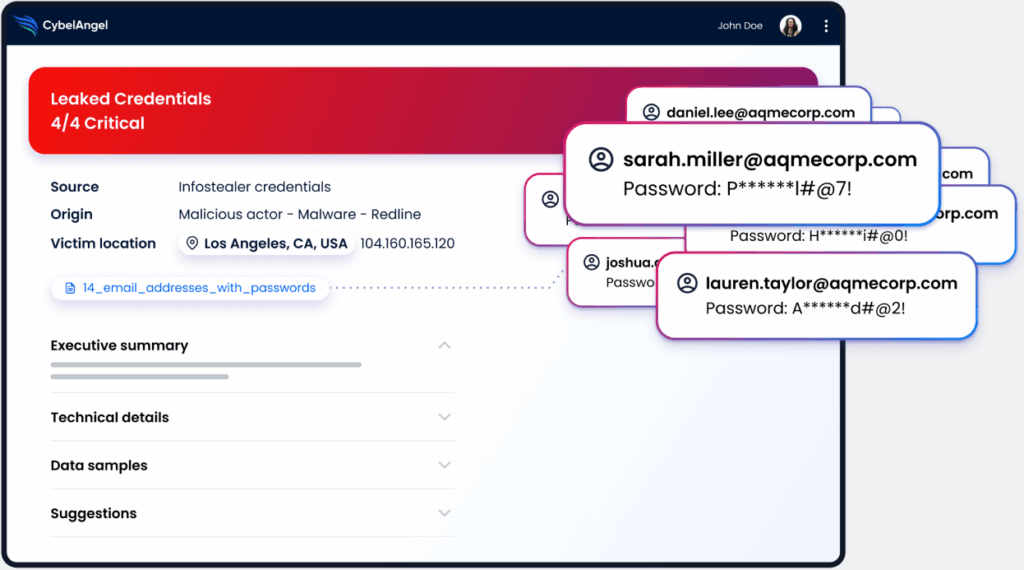
Most leaked credentials will be discovered eventually. Once exposed, they follow a path or “lifecycle” that often ends in unauthorized access or full account takeover.
It usually starts with a breach. Maybe credential leaks happen through infostealer logiciels malveillants. Maybe they’re lifted from a phishing page or pulled from a misconfigured database. However it happens, usernames and passwords end up in the wild.
From there, some end up for sale on dark web marketplaces. Others get dumped on paste sites. Many are collected by bots and tested in credential stuffing attacks across banks, SaaS tools, and mobile apps.
Threat actors can then use stolen credentials to take over accounts, steal data, move laterally, or plant ransomware. Often, the victim doesn’t know it’s happening until damage is done.
Intelligence des titres de compétences helps security teams break the cycle. It gives them visibility into exposed credentials early, before those logins are weaponized.
Here’s an example of what the compromised credential lifecycle could look like.
Where do stolen credentials come from?
We often imagine high-profile breaches (think flashing screens and dramatic takedowns). But generally, data gets stolen through the quiet, everyday slip-ups that go unnoticed. What do these look like?
Hameçonnage is one of the top culprits. Attackers can spin up fake login pages and trick users into entering their details. Infostealer malware is another major driver. Once installed, it quietly grabs saved logins from browsers, email clients, and messaging apps.
Then there are misconfigured systems. Databases left exposed to the internet. Dev tools like GitHub or Jira containing hardcoded secrets. Even mobile apps and social media platforms sometimes leak login tokens in the background.
Many of these credentials don’t get reported. They just circulate on Telegram, in dark web forums, or on paste sites. Some are shared as part of “combo lists” that fuel credential stuffing attacks across thousands of platforms.
Here’s a quick breakdown of the main stolen credential use cases.

What threat actors do with leaked credentials
Stolen credentials aren’t always used right away. Sometimes they sit in marketplaces or they’re fed into bots. Either way, once in the hands of a threat actor, even a single leaked login can unlock bigger problems.
One common tactic is credential stuffing. Attackers use automated bots to try the same email and password across dozens of apps, like banking portals, SaaS platforms, internal tools. If a match hits, they’re in.
From there, it escalates. They might quietly access sensitive files, intercept payment flows, or move laterally into more critical systems. In some cases, compromised accounts are used to send courriels d'hameçonnage from trusted domains or to impersonate executives.
Credential reuse makes it worse. A password exposed in a gaming breach can be reused to log into corporate systems if the same login was used at work.
Some attackers even offer ATO-as-a-service (account takeover), where stolen accounts are packaged and sold to others, ready to exploit.

Case study: The 16-billion credential leak
In June 2025, security researchers uncovered one of the largest credential exposures ever, with 16 billion login records spread across 30 unsecured databases. Most were traced back to infostealer malware, which extracts saved usernames, passwords, cookies, and tokens from infected devices.
Much of the data was ready for immediate exploitation. The scale was vast, covering everything from Apple, Google, and Facebook accounts to GitHub, Telegram, corporate portals, and even government systems (see screenshot below).
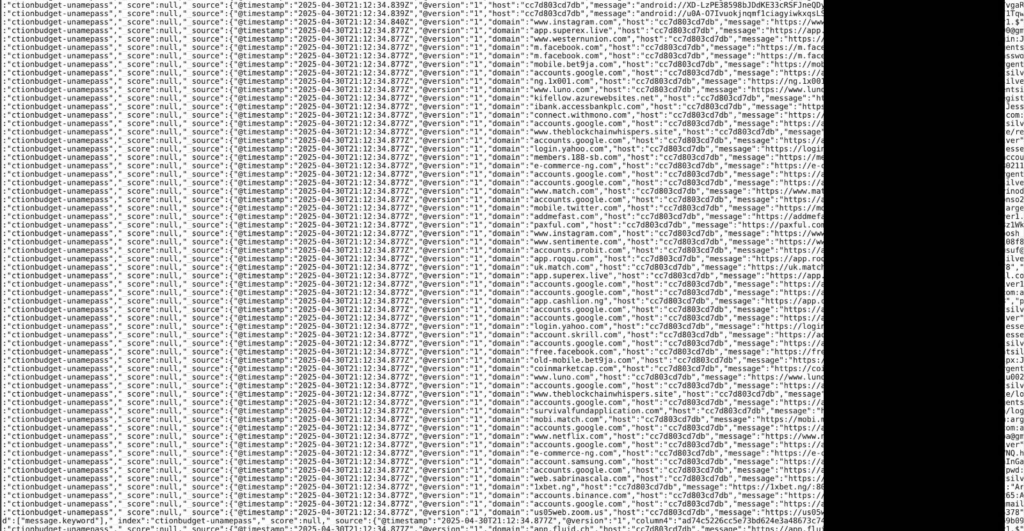
With this many records, cybercriminals could have access to millions of accounts. Many entries also included active session tokens, making them valuable for instant account takeover (ATO) without needing the password at all.
This example shows that without adequate account takeover prevention and cyber threat intelligence, anyone could fall victim to credential leaks.
Figure 6: News video detailing the credential leaks. (Source: Fox 4 Dallas-Fort Worth)
How credential intelligence fits into your security stack
Most security stacks detect what’s happening inside your perimeter. But credential intelligence adds visibility to the outside, including leaked logins, stolen credentials, and early signs of account takeover (ATO) activity.
Credential intelligence works like a radar. It monitors the dark web, paste sites, and malware logs for any sign of compromised credentials tied to your organization. Once a match is found, it alerts your team, often before the credentials are ever used.
CybelAngel's credential intelligence solution helps security teams:
- Detect credential leaks in real time, such as through dark web monitoring
- Monitor third-party risks and personal-use logins
- Reduce dwell time between leak and response
Ultimately, credential intelligence becomes your data leak monitoring tool. And it makes the difference between catching an ATO early or cleaning up after it spreads.
7 actionable steps for security teams
Credential intelligence solutions are most effective when paired with a data leak prevention process. These cybersecurity steps help ensure vulnerabilities are detected and neutralized quickly:
- Build a credential exposure workflow: Define exactly what happens when a leak is detected, including who gets notified, how passwords are reset, and what systems are checked for suspicious logins.
- Prioritize by risk: Focus first on credentials tied to sensitive systems or high-privilege accounts. Not all exposures carry the same impact.
- Automate where possible: Use integrations with SIEM, SOAR, or IAM platforms to trigger password resets or block logins from flagged credentials without manual intervention.
- Track reuse patterns: Identify employees reusing passwords across personal and work accounts. Provide targeted training or enforce stronger authentication.
- Integrate with threat intelligence: Link credential exposure alerts to broader threat intelligence feeds. This helps map activity to known threat actors or campaigns.
- Review and update policies: Regularly revisit password security, MFA enforcement, and incident response plans based on trends in credential leaks.
- Test your response: Run tabletop exercises to simulate a credential stuffing attack, ensuring the team can react under realistic conditions.
FAQ
What are compromised credentials?
Compromised credentials are usernames, passwords, or other login details that have been stolen, leaked, or exposed through breaches, malware, or misconfigurations.
How do cybercriminals use stolen credentials?
They can attempt account takeover (ATO), launch credential stuffing attacks, impersonate users, or sell the data on dark web marketplaces.
What is credential stuffing?
Credential stuffing is when attackers use automated bots to test stolen username and password combinations across multiple websites and apps, exploiting password reuse.
What is infostealer malware?
Infostealers are malicious programs designed to collect stored logins, cookies, tokens, and other sensitive data from an infected device.
How can organizations detect credential leaks?
Through credential intelligence platforms that scan dark web sources, paste sites, and malware logs for exposed logins linked to their domains.
What is the difference between credential intelligence and threat intelligence?
Credential intelligence focuses specifically on detecting, validating, and remediating exposed logins. Threat intelligence is broader, covering a wide range of adversary tactics, tools, and campaigns.
Does multi-factor authentication stop all credential-based cyber attacks?
MFA greatly reduces the risk but isn’t foolproof. Some attackers use stolen session tokens or bypass MFA via hameçonnage or social engineering.
Conclusion
The 16-billion-credential leak shows just how large and fast-moving the market for stolen logins has become. Infostealer malware, phishing, and unsecured databases feed a constant supply of valid credentials into the hands of bad actors.
CybelAngel's credential intelligence platform continuously scans the dark web, paste sites, and malware logs for exposed logins tied to your domains.
