The API Threat Report: What 2025 Has Taught Us So Far

Inhaltsübersicht
APIs are the glue that hold applications together. They power logins, payments, searches, and dashboards. (And often, without users even knowing they exist.) But as they’ve grown more powerful, they’ve also become a favorite target for attackers.
In 2025, that risk is more visible than ever. From stolen tokens to broken authorization, we’ve seen how quiet flaws in APIs can lead to major security incidents. This article breaks down the biggest API security risks so far this year. And not just in theory, but through real-world examples.
Introduction
Application programming interfaces (APIs) are designed to connect systems, enable features, and simplify complexity. But that same simplicity can hide serious security gaps, especially when APIs are left undocumented, misconfigured, or exposed to the public internet.
Unlike traditional web applications, API versions don’t always have clear front doors. Many don’t show up in security scans. Some are deployed quickly, tested loosely, and forgotten entirely. But for attackers, they’re ideal entry points.
This guide breaks down the top API security risks seen in real-world breaches this year. Whether you’re tracking broken authentication, excessive data exposure, or injection attacks, these incidents offer practical insight into how APIs are being abused. And how to stop it.
How we got here: The rise of the API attack surface
APIs used to function as internal tools. But as everything moved to the cloud, such as banking, payments, healthcare, and logistics, APIs became public-facing, interconnected, and exposed.
Now, they’re everywhere. In mobile apps, backend services, third-party integrations, and embedded inside microservices. With every new release or product launch, more APIs go live. And not all of them are tracked.
Security teams now face three core problems when trying to secure API processes:
- Discovery is hard: Many API vulnerabilities don’t show up in traditional scans. Some are undocumented or belong to forgotten projects. Others live in dev environments but still accept requests.
- Access control is inconsistent: Different teams manage different API endpoints. Some use API keys, others rely on outdated OAuth flows. Authentication mechanisms vary… or don’t exist at all. Which makes unauthorized access an easy attack vector.
- Die Angriffsfläche keeps growing: More endpoints mean more potential entry points (and security vulnerabilities). Each one handles user input, permissions, and sensitive information differently. All of it becomes fair game to attackers.
This is why API-Sicherheit risks have moved to the top of the agenda.
API security threat examples in 2025
Let’s break down some real-life API security risks that came up in 2025.
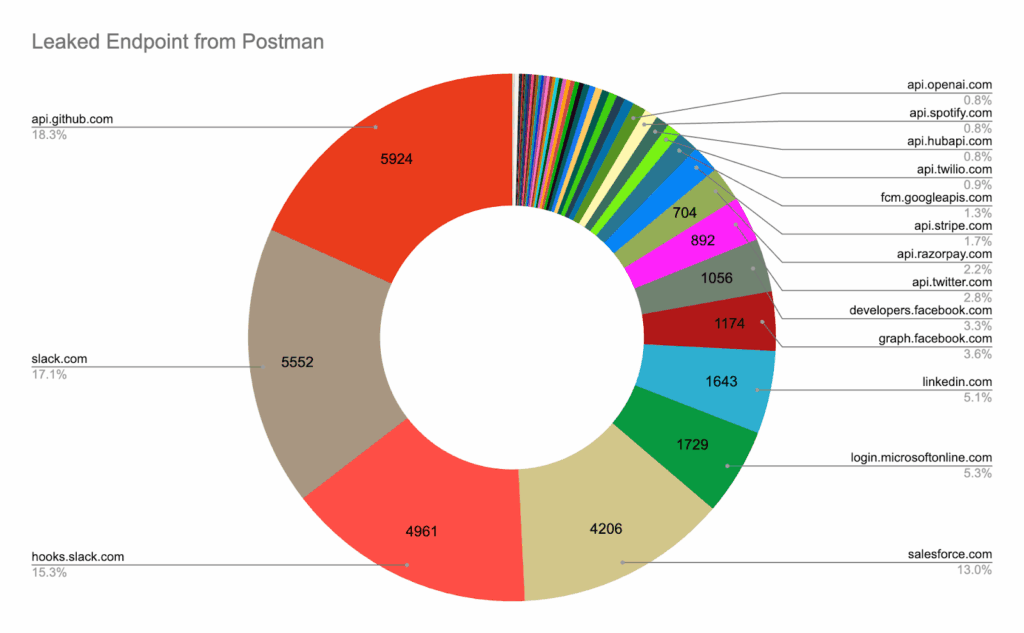
Postman breach leaked real API keys and sensitive data
- When: Dezember 2024
- What happened: It was found that 30,000 Postman workspaces had been exposed, containing live API keys, access tokens, and sensitive payloads (including healthcare records and enterprise credentials).
- What went wrong: Many workspaces were publicly shared without security controls. Developers had saved real tokens, secrets, and request logs that were accessible to anyone with the link.
- Why it matters: Postman is used across the API lifecycle, but it’s not designed as a secret manager. One exposed workspace could give attackers direct access to production systems.
99% of organizations report API security incidents
- When: Februar 2025
- What happened: In Q1 2025, a security provider revealed that 99% of surveyed organizations experienced at least one API security issue over the prior 12 months.
- Where the failures were: The top API security risks reported were injection attacks and Broken Object Level Authorization (BOLA), which together made up over one-third of all incidents. Sensitive data exposure (34%) and broken authentication (29%) followed closely.
- What made this worse: 95% of API attacks came from authenticated sessions, suggesting that simply trusting access tokens is no longer enough. Almost all attacks targeted external-facing APIs. Alarmingly, only 10% of organizations had a posture governance strategy, despite 43% saying they planned to implement one within a year.
- Why it matters: Poor governance and inconsistent API-Sicherheit standards are now slowing software rollouts, with over 55% of respondents reporting delays due to API concerns. The report also noted that generative AI code is introducing new risks.
ChatGPT tool exploited via SSRF
- When: March 2025
- What happened: A server-side request forgery (SSRF) vulnerability in a third-party tool built for interacting with ChatGPT was exploited in targeted attacks, including US government and financial institutions.
- Where the failure was: The flaw (CVE-2024-27564) allowed attackers to inject crafted URLs into the
urlparameter of thepictureproxy.phpfile, redirecting the tool to malicious endpoints without requiring authentication. - What was exposed: Internal resources and sensitive metadata were at risk, particularly in misconfigured environments lacking proper firewall or intrusion prevention controls.
- Why it matters: This risk went under the radar for nearly a year, despite proof-of-concept code being publicly available. Within one week in March 2025, over 10,000 exploit attempts were logged from a single IP address. This shows how damaging overlooked APIs and supporting integrations (especially those powering AI tools) can be.
Human error led to API key leak
- When: July 2025
- What happened: On July 13, 2025, a private API key for xAI’s language models was accidentally published on GitHub by Marko Elez, a developer at Elon Musk’s Department of Government Efficiency (DOGE). The key, embedded in a script called
agent.py, granted access to more than 50 xAI LLMs. - Where the failures were: The exposure wasn’t detected internally. Instead, it was flagged by GitGuardian, a tool that scans for exposed secrets in public repositories. Security researchers warned that the API key could be used without authentication to send requests and retrieve data from xAI systems.
- What made this worse: The key remained live even after public disclosure. And this wasn’t the first time it happened. KrebsOnSecurity previously reported another DOGE employee leaking similar API keys on GitHub, exposing models trained with sensitive government data.
- Why it matters: Elez could access records across US agencies including Homeland Security, Treasury, and Social Security. Mishandling something as basic as API key security suggests serious gaps in access control and supervision.
Cisco ISE flaw enabled unauthenticated API requests
- When: July 2025
- What happened: Cisco revealed a serious flaw in its Identity Services Engine (ISE) software. Hackers could send a specially crafted API request and run code on the system, without needing to log in.
- What went wrong: The API didn’t check user input properly. That meant attackers could trick the system into accepting dangerous commands.
- What was at risk: Any company using certain versions of Cisco ISE (3.3 and 3.4) could have been vulnerable. The bug gave attackers full control of the device, including the ability to run code as if they were an admin.
- Why it matters: This type of flaw is extremely dangerous. It didn’t require a password or special access. Just one API call could take over a critical system unless patched quickly.
The causes of 2025’s API failures
You’d expect the biggest API threats to come from new vulnerabilities or cutting-edge attacks. But this year’s data tells a different story. The problems we’re seeing in 2025 are mostly repeat offenses. Let’s break down some patterns which keep coming up.
- Authentication just isn’t enough: Even when users are properly logged in, that doesn’t mean they should have access to everything. 95% of API attacks this year came from authenticated sessions, meaning attackers are getting through the front door, then moving sideways to access sensitive data.
- Governance and visibility are lagging: Most teams still don’t have a full API inventory or security policies in place. Older endpoints go unmonitored. Third-party APIs slip through risk assessments. And only 10% of organizations surveyed in 2025 had any sort of API posture governance strategy in place.
- Authorization gaps are everywhere: APIs often don’t check what a user is allowed to access. That’s why Broken Object Level Authorization (BOLA) continues to top the OWASP API Security list. Whether it’s skipping permission checks or letting anyone pull sensitive fields, it’s still one of the easiest ways for attackers to escalate.

How to reduce API security risks
Fixing API security doesn’t mean overhauling your entire architecture. Most risks can be reduced by doing the basics consistently, and giving cybersecurity teams visibility into what’s exposed in real-time.
Here are the security best practices that make the biggest difference.
- Build a full API inventory: You can’t protect what you can’t see. Use automated API discovery tools to surface every endpoint, including third-party services, legacy versions, and shadow APIs. Tag them by function, owner, and environment.
- Limit sensitive data exposure: Only return the data a user actually needs. Avoid sending full objects or verbose error messages. Strip internal IDs, user metadata, and anything else that could lead to a data breach.
- Enforce strong authentication and authorization: Apply robust authentication (OAuth, API keys, or mutual TLS). Then go deeper with granular authorization. Every API call should check who’s making the request, and whether they’re allowed to access that object.
- Monitor traffic and enforce limits: Set rate limits and alerts to flag unusual patterns. Use an API gateway or WAF to spot malicious payloads and stop common attacks before they reach the backend.
- Treat governance as a shared responsibility: Security isn’t a checklist. It’s a long-term program. Define secure coding standards, track metrics over time, and make sure product, dev, and security teams all know what “good” looks like.
- Validate all user input: Unfiltered input is one of the most common ways attackers exploit APIs. Validate everything, like query strings, headers, bodies, and even file names. OWASP has excellent cheat sheets to help developers fix issues like injection and broken object-level authorization (BOLA).
Need help automating the hard parts of your security measures, like discovery, monitoring, and detection?
CybelAngel helps you uncover API risks across your digital ecosystem, including third-party providers you don’t control. Explore CybelAngel’s external threat intelligence solutions to learn more.
FAQs about API security
What is an API?
An API (Application Programming Interface) lets software systems talk to each other. APIs power logins, payments, apps, and more, often in the background.
What are API security risks?
These are vulnerabilities in how APIs are built, exposed, or used. Common risks include unauthorized access, data leaks, injection attacks, and broken authentication.
What’s a shadow API?
A shadow API is an undocumented or forgotten API endpoint. These are risky because they may not follow security policies, but still be accessible online.
What is BOLA?
BOLA stands for Broken Object Level Authorization. It means users can access data they shouldn’t (like another person’s account details) because the API isn’t checking permissions properly.
What is a WAF?
A WAF (Web Application Firewall) filters and monitors traffic between users and your application. It helps block malicious API requests, like SQL injection attacks or scraping.
What’s the difference between user authentication and authorization?
Authentication confirms who someone is (e.g., logging in). Authorization controls what they can do or access after that. APIs need both.
Einpacken
APIs power nearly everything we do online. But when mismanaged, they can also create quiet pathways for attackers to slip through.
2025 has shown us that API security risks aren’t new, they’re just increasingly overlooked. However, with the right tools and cheat sheets, they can be kept in check.
CybelAngel helps security teams detect unknown APIs, exposed endpoints, and critical risks before they become data breaches. Demo buchen to learn more.
