Der Cyber Resilience Act: Was Sicherheitsverantwortliche jetzt wissen müssen

Table of contents
The EU Cyber Resilience Act (CRA) is the first of its kind. It requires manufacturers of hardware and software to implement security measures throughout the whole product lifecycle.
And this isn’t just a compliance checkbox. It’s a series of essential cybersecurity requirements that can have serious consequences if ignored.
The EU CRA’s obligations will apply from 11 December 2027. Here’s everything that you and your team need to know before that deadline hits.
What is the Cyber Resilience Act?
The Cyber Resilience Act (CRA) is the European Union’s first cybersecurity regulation for software and hardware products.
- Software: Digital products, including apps, operating systems, and code libraries, whether installed on a device or as part of a connected system.
- Hardware: Connected physical devices, including Internet of Things (IoT) devices, smart home tech (such as baby monitors), routers, consumer electronics, and more.
Ultimately, anything with a digital element could fall under the Cyber Resilience Act.
And it falls at an opportune moment.
In a podcast interview in January 2025, John Burke stated, “The truth is that the technology base upon which our critical infrastructure depends is inherently insecure because of decades of misaligned incentives that prioritized features and speed to market over security.”
The CRA’s goal is simple: to reduce these vulnerabilities in digital products and make sure cybersecurity is part of the product lifecycle, from design through to decommissioning.
Its goals are:
- To improve security standards for hardware and software.
- To ensure that manufacturers take responsibility for the cybersecurity of a product’s lifespan.
- To give customers clear information about product security.
Why has the CRA EU regulation been introduced?
To date, most digital products have historically been shipped insecure by default. These have proven to be the ultimate entry point for cybercriminals.
The European Parliament has therefore cited these reasons for their new requirements:
- Cyberattacks target EU organizations more than anywhere else in the world.
- Cyberattack costs are rising by 15% every year in the US alone.
- With estimates of 30 to 40 billion connected devices incoming by 2030, the cyber risk scope is only going to grow.

CRA graphic showing reasons behind its implementation. Source.
What are the benefits of the CRA?
On its official page, the European Cyber Resilience Act cites 7 core benefits of its cybersecurity standards:
- Harmony: Prevent overlapping regulations and keep all manufacturers on the same page.
- Security: Protect businesses and consumers from the potential damage caused by cyberattacks.
- Economy: Safeguard businesses from the potential financial costs of a data breach.
- Reliability: Build customer trust and confidence in digital products, which in turn could benefit businesses.
- Profitability: Generate more demand for digital products, thanks to their improved safety features.
- Transparency: Improve customer satisfaction by giving them more insight into how their hardware and software products are made.
- Privacy: Protect “fundamental rights”, particularly in relation to data and privacy guidelines.
Who does the CRA apply to?
If your company manufactures, imports, distributes, or sells products with digital components in the EU, the CRA applies to you.
That includes:
- EU-based companies
- Non-EU vendors offering software or devices into the EU market
- Supply chain actors, such as importers and distributors
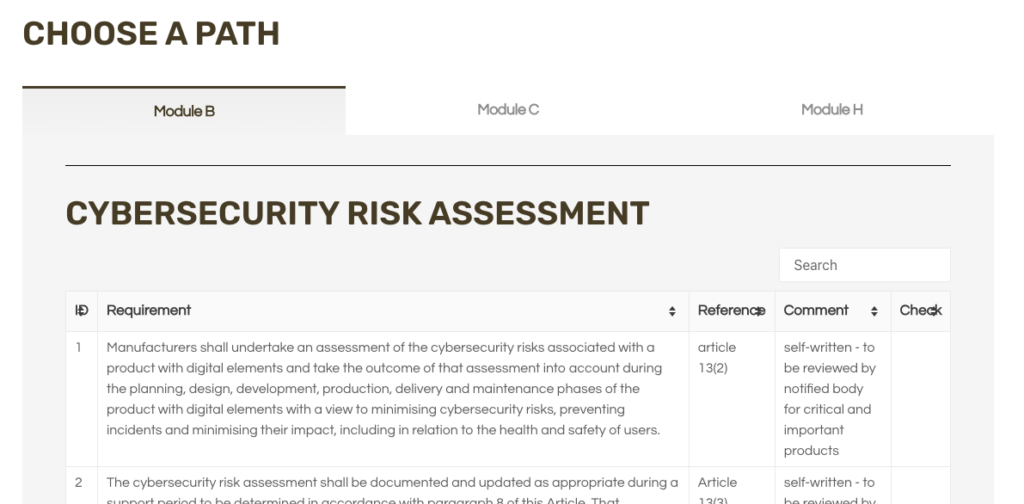
In addition, CRA requirements will vary depending on your sector. There are different guidelines available for IoT device manufacturers, software developers, and supply chain actors.

CRA graphic showing the different mandates. Source.
How are digital products categorized under the CRA?
Under the CRA, products are grouped into three categories based on their cybersecurity risk and the level of access they have to sensitive systems or infrastructure.
Here’s a breakdown from Forbes:
- 🟡 Standard (Not Critical): This includes the majority of everyday products, such as external hard drives, speakers, and gaming devices. 90% of products fall into this standard.
- 🟠 Class I (Lower Risk Critical): Covers tools with some system-level access, like VPNs, firewalls, browsers, and password managers.
- 🔴 Class II (Higher Risk Critical): Reserved for products with deep access to core systems—think operating systems, CPUs, industrial firewalls, and similar components.
There are different compliance checklists available, depending on whether you offer standard or critical products.
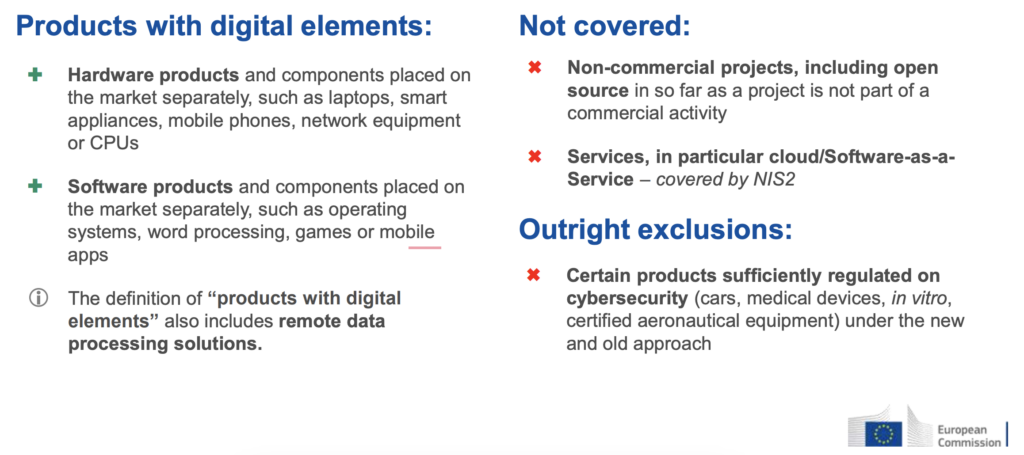
Are there any exceptions?
There are exclusions, such as certain open-source software, pure SaaS which is already covered by the NIS2 directive, or regulated industries like medical devices, marine equipment, and aviation.
But for most security leaders, the risk of inaction is high.
What are the CRA requirements?
The CRA introduces mandatory security requirements across the entire lifecycle of a product (5 years, or shorter if the lifespan is lower).
Here are the major cybersecurity resilience pointers:
- Security-by-design: Cybersecurity must be factored into the planning, design, and development of products. No more bolting it on as an afterthought.
- GDPR-related measures: In particular, manufacturers should have provisions for risk assessment, incident management, and data processing solutions.
- Vulnerability handling: Vendors must create products that can be patched and updated to address any vulnerabilities. Security updates should be standard procedure.
- User-friendly security instructions: They should also have technical documentation for customers to understand the product’s cybersecurity features—in a clear, easy-to-follow format.
- Incident and vulnerability reporting: Actively exploited vulnerabilities and incidents must be reported to CSIRT (Computer Security Incident Response Team) and ENISA (the EU Agency for Cybersecurity) within 24 hours.
- Declaration of conformity: You’ll need to assess the cybersecurity risks associated with your products and ensure they undergo a conformity assessment. If any such product is found to fall short of CRA compliance, you may be required to recall or withdraw it from the market.
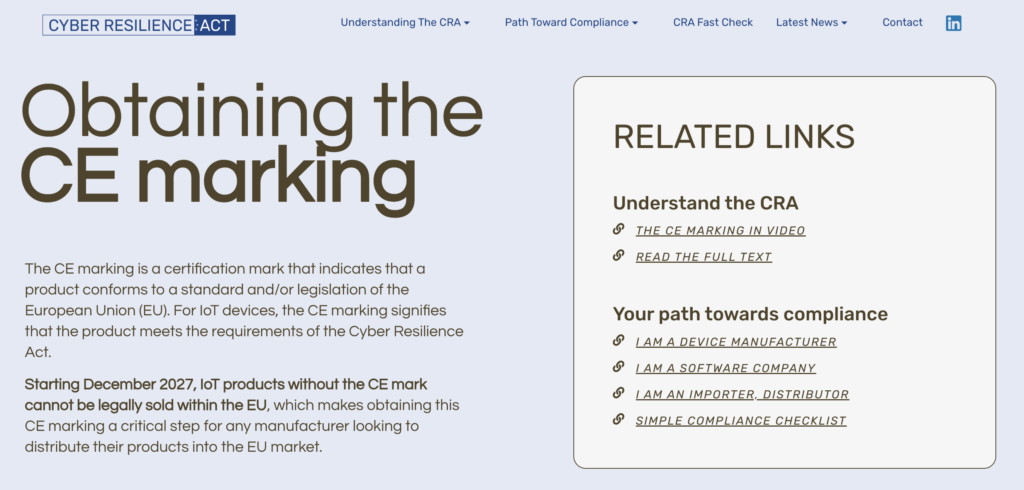
What is the CE marking?
The CE mark shows that a product’s functionality meets EU standards. Under the CRA, this includes cybersecurity requirements for IoT devices.
From December 2027, products without it can’t be legally sold in the EU, making it essential for internal market access.
The CRA timeline and enforcement
The Cyber Resilience Act has officially entered into force, triggering a transition period that gives manufacturers time to align with the new requirements.
Here’s what to expect:
- Full compliance is mandatory within 36 months, giving companies until late 2026 or early 2027 (depending on the final entry date) to meet most of the CRA obligations.
- Reporting duties kick in sooner—just 21 months after entry into force. By then, manufacturers must be ready to report actively exploited vulnerabilities and major security incidents involving their products.
Non-compliance isn’t just a reputational risk. The penalties are significant: companies can face fines of up to €15 million or 2.5% of global annual turnover, whichever is greater.
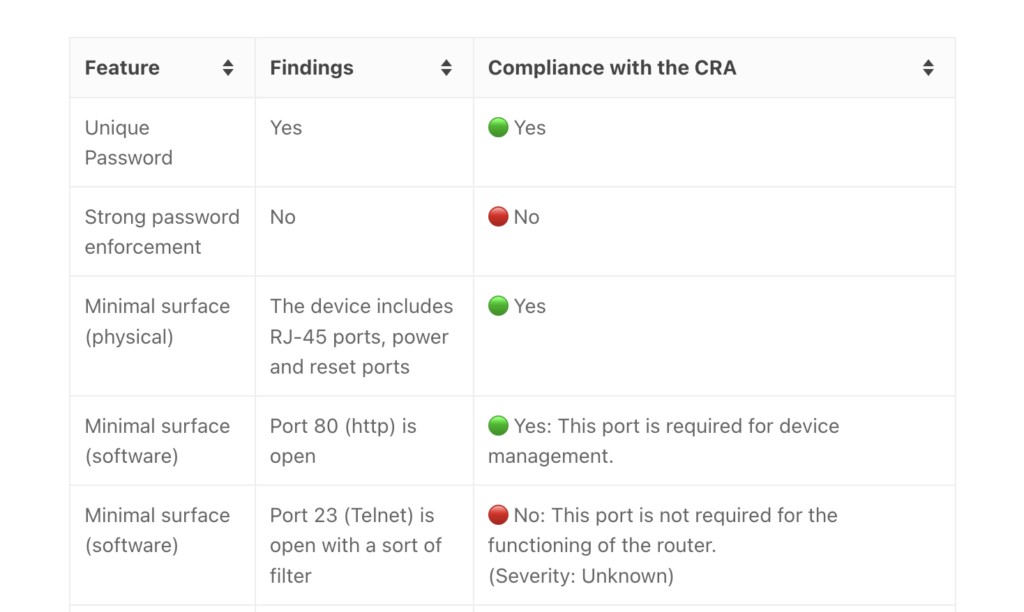
The CRA’s key risks and challenges
While the CRA is a welcome development for customers and businesses, its implementation does present some unique challenges.
Security teams and product leads face some tough questions, including:
- How do we identify which products fall under CRA scope?
- Are our current software development practices CRA-ready?
- Can we provide documentation for every cybersecurity risk?
- What’s our process for vulnerability disclosure and incident reporting?
The CRA has also raised concerns within the open-source community. Groups like the Linux Foundation have pointed out that vague definitions and broad obligations could unintentionally place an unfair burden on open-source contributors.
They also suggest that the CRA could drive a 6% average price increase in digital products.
This pricing increase is due to budgeting implications. There are many costs associated with fulfilling CRA obligations.

Fortunately, the CRA website provides a compliance cost calculator to help businesses establish their implementation costs.
But for many, the biggest challenge will be visibility, into supply chains, third-party libraries, and embedded components.
However, tools like CybelAngel can lift this pressure.
CybelAngel is an external threat intelligence platform that helps organizations secure all their public-facing digital assets, from data breach prevention to attack surface management.
What should CISOs be doing right now?
Here’s where to start:
- Inventory your digital products: Know what’s in scope. Don’t forget embedded software, firmware, or connected modules. Use a threat intelligence tool like CybelAngel to get full visibility.
- Assess your DevSecOps practices: Are secure coding, threat modeling, and SBOMs (software bills of materials) part of your workflow? Now is the time to implement secure development pipelines.
- Review your incident response and disclosure process: Who handles reporting to ENISA? Also, check your vulnerability disclosure and patching workflows.
- Coordinate with legal and compliance teams: The CRA is a legal obligation—fines can go up to €15 million or 2.5% of global turnover for non-compliance. Be ready for CE marking and third-party audits.
Final thoughts
The CRA signals a move away from insecure-by-default software.
For security leaders, this is more than compliance, it’s a chance to embed security as a core product quality.
Don’t wait for the 2027 deadline. The time to align your strategy is now, and your business and customers will thank you for it later.
