Who is the DragonForce Ransomware Gang?

Table of contents
Who claims to take over a rival ransomware group and then brags about it online? DragonForce does.
Once a little-known hacktivist group, the DragonForce gang has evolved into a professional ransomware operation. They run a RaaS program. They build custom payloads. And they leak stolen data on their terms.
So, who exactly is this group, how do they operate, and who are their victims? Here’s a DragonForce ransomware analysis to break it all down.
DragonForce’s origins and background
The DragonForce ransomware variant emerged around August 2023, but its roots trace back further. Originally known as DragonForce Malaysia, the group began as a pro-Palestine hacktivist group, targeting organizations across the Asia-Pacific and the US. Over time, though, its focus shifted from political attacks to profit-driven ransomware campaigns.
This wasn’t just a rebrand. By early 2023, the DragonForce ransomware group had fully pivoted into ransomware. In March 2024, the group expanded its ransomware-as-a-service (RaaS) offering, launching a franchise-like model.
Affiliates could now run their own ransomware brands, supported by DragonForce’s infrastructure, with everything from client panels and data hosting to 24/7 backend support with anti-DDoS protection.

Technically, DragonForce started with a LockBit 3.0-based variant, then introduced a second strain—a fork of ContiV3—tailored for double extortion attacks. Their malware was designed for broad impact, targeting ESXi, NAS, BSD, and Microsoft Windows systems, with constant upgrades to its encryption engine and features.
Unlike groups that operate in bursts, DragonForce maintained steady pressure. Between August 2023 and August 2024 alone, they claimed 82 victims, hitting sectors like manufacturing, real estate, and transportation, with the US taking the brunt of attacks.
How DragonForce operates: Tactics, Techniques, and Procedures (TTPs)
How does a DragonForce ransomware attack happen? Here’s a breakdown of DragonForce TTPS.
- Initial access: DragonForce typically starts with phishing emails or other social engineering scams, tricking users into opening malicious attachments or clicking harmful links. Once inside, they often exploit vulnerabilities in Remote Desktop Protocol (RDP) and VPN solutions.
- Execution and persistence: After gaining a foothold, DragonForce deploys tools like Cobalt Strike and SystemBC to move laterally and harvest credentials. They use network scanners, such as SoftPerfect Network Scanner, to identify additional targets. A key tactic is “Bring Your Own Vulnerable Driver” (BYOVD), which allows them to disable security software by exploiting known vulnerable drivers.
- Customization and affiliate model: DragonForce’s ransomware-as-a-service (RaaS) program is highly customizable. Affiliates can adjust encryption settings, disable security features, and personalize ransom notes to suit the specific victim. The business model lets affiliates keep 80% of any ransom collected.
- Data exfiltration: DragonForce focuses on stealing sensitive data before launching its encryption phase. Typical targets include intellectual property, financial records, and personally identifiable information (PII). This ensures that even if backups are available, victims still face the risk of a damaging data breach.
- Encryption: The ransomware payload is designed to be flexible and robust. It targets various systems, including ESXi, NAS, BSD, and Windows environments. Affiliates can fine-tune the encryption process, making each attack slightly different.
- Extortion: The gang relies on a dedicated DragonForce leak site on the dark web to pressure victims. If the ransom payment isn’t received, stolen data is publicly posted, adding reputational and regulatory risk on top of operational disruption. While detailed negotiation tactics and ransom demands aren’t widely documented, the combination of data theft and encryption gives them significant leverage.
What makes DragonForce distinctive?
One of DragonForce’s standout moves is its claim to have taken over the infrastructure of RansomHub, which was the largest ransomware group over the past year. This announcement appeared both on the RAMP forum and DragonForce’s Tor-based leak site, signaling a bold attempt by the cybercriminals to absorb or replace a major competitor.

DragonForce has a clear focus on high-value industries. Their attacks typically hit sectors like manufacturing, real estate, and transportation, showing a preference for organizations that are both operationally critical and likely to pay quickly. Their campaigns are global but have had a heavy concentration in the US, UK, and Australia.
In terms of communication and messaging, DragonForce posts updates and announcements on both underground forums and its own leak site. This keeps the group visible within the cybercrime ecosystem.
DragonForce’s operations appear to be well-organized and efficient. Their ransomware-as-a-service model allows affiliates to launch attacks rapidly, with access to professional-grade infrastructure and customizable tooling. They are opportunistic in their methods, exploiting well-known vulnerabilities and capitalizing on whatever entry points are most effective at the time.
DragonForce and recent attacks
Let’s look at some real-life examples of DragonForce threat actors in action, with cyber incidents across the world.
Victimology
Who are the main DragonForce victims? The gang seems to have built a track record of targeting large, high-profile organizations across multiple sectors.
Notable DragonForce cyberattacks include the Ohio Lottery breach in December 2024, where over 600 GB of sensitive data was stolen. In Australia, Yakult’s operations were hit hard in December 2024, with DragonForce claiming responsibility for exfiltrating nearly 100 GB of data, including contracts and personal identification documents.
DragonForce malware also extended its reach into the Middle East. In February 2025, a major real estate and construction company in Saudi Arabia became a victim, with DragonForce reportedly stealing over 6 TB of data. The attack appeared to be timed to coincide with Ramadan, adding an extra layer of pressure to the extortion.
More recently, UK retailers have been in the crosshairs. Marks & Spencer faced a serious ransomware attack in April 2025, leading to widespread IT disruption and service outages.
DragonForce also claimed responsibility for a breach at Co-op, which included the theft of data linked to millions of members and employees. The hackers even shared samples of stolen data with BBC journalists, demonstrating the scale of the breach and further pressuring the victim.
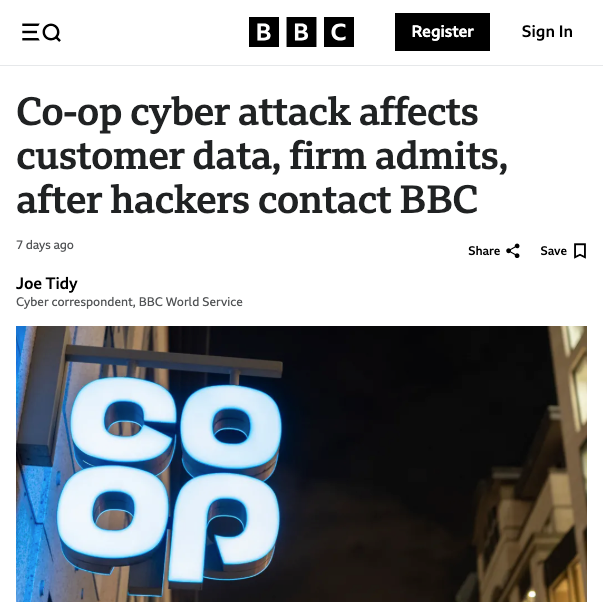
Figure 3: News headline detailing the Co-op cyber attack. (Source: BBC)
Impact
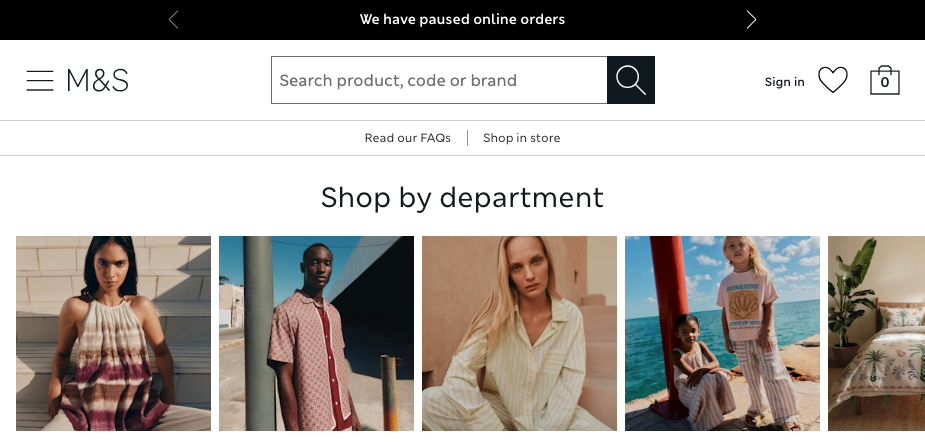
The fallout from DragonForce attacks typically includes operational disruption, financial loss, and significant reputational damage. Victims often face prolonged service outages, as seen with the Ohio Lottery and M&S.
For example, at the time we wrote this article, the Marks & Spencer website still displayed this banner, “We have paused online orders.”
Also, stolen data, including sensitive information, adds legal and compliance challenges. Public leaks exacerbate the damage, undermining trust and inviting regulatory scrutiny, such as in the case of Yakult Australia.
Attribution
Attribution in ransomware cases is rarely straightforward, and DragonForce is no exception. While the group actively claims credit for its attacks via its leak site and underground forums, independent verification can be difficult.
In some cases, victims, law enforcement, and security researchers have linked specific breaches to DragonForce with a high degree of confidence, such as the Ohio Lottery and Yakult breaches, based on matching ransomware signatures and public statements.
How cyber professionals can defend against DragonForce
DragonForce isn’t reinventing ransomware. They’re just executing it well, with strong infrastructure, tailored payloads, and growing reach. That means defenders don’t need magic. They need fundamentals, done consistently, across prevention, detection, and response.
Here are some cybersecurity measures to prevent ransomware attacks.
1. Prevention
The best defense against DragonForce is keeping them out.
- Patch exposed systems quickly. DragonForce is known to exploit common entry points like VPNs and RDP. Prioritize patching internet-facing services and known vulnerabilities.
- Enforce MFA everywhere. Especially on remote access services, admin panels, and backup systems.
- Segment your network. If ransomware hits, segmentation can limit lateral movement.
- Restrict admin rights. Only give users what they need. Monitor for privilege escalation.
- Train users on phishing. Test and simulate regularly. DragonForce often starts with a malicious email.
- Secure backups. Keep them offline or immutable, and test recovery often. Backups don’t help if they’re encrypted, too.
Detection
Catching DragonForce cyber threats early is key, before exfiltration or encryption can happen.
- Monitor for lateral movement tools. Cobalt Strike, SystemBC, and SoftPerfect Network Scanner are part of DragonForce’s toolkit.
- Look for BYOVD activity. Detection of unusual driver loads or attempts to disable EDR tools can indicate an attack in progress.
- Watch for data staging. Sudden spikes in data access or transfers to internal staging areas should trigger alerts.
- Hunt for ransom note artifacts. Even during custom payload delivery, notes often follow patterns and can be flagged.
- Enable logging across endpoints and servers. Especially PowerShell, Windows Event Logs, and network traffic.
Response & recovery
When a cyber incident does happen, speed and structure matter.
- Follow your incident response plan. Don’t improvise under pressure. Run the playbook.
- Isolate affected systems immediately. Contain the damage fast.
- Engage legal and communications early. Data leaks bring regulatory and reputational risk.
- Preserve logs and artifacts. Even if systems are encrypted, evidence matters for attribution and response.
- Report to authorities. Share indicators of compromise (IOCs) with CISA or law enforcement. This helps build threat intel across the industry.
- Review and update controls post-incident. Every attack is an opportunity to close a gap.
For deeper technical guidance, CISA’s Ransomware Guide is a solid reference for teams building layered defense strategies.
Figure 5: Tweet/ X post from CISA. (Source: CISA)
Wrapping up
DragonForce isn’t the biggest ransomware gang out there (yet). But they’ve grown quickly, and their tactics are evolving. For defenders, the lesson is clear: you can’t wait until ransomware hits the endpoint. You need to spot threats before they reach your network.
That’s where CybelAngel comes in.
Our external threat intelligence solution helps security teams detect ransomware exposure early, across third parties, supply chains, and the dark web. From leaked credentials to unsecured assets and early signs of compromise, we give you visibility where traditional tools can’t.
Fighting ransomware starts outside the perimeter. Book a demo with CybelAngel to see how you can secure yours.

