The 20 Biggest Cybersecurity Incidents and Threat Intelligence Failures of 2025

Table of contents
Cybersecurity teams spent most of the last year reacting to a difficult mix of data leaks, geopolitical clashes, supply chain compromises, ransomware alliances, and rapid shifts in attacker behaviour. Threats moved faster than usual. Some were easier to spot. Many reached production systems long before anyone realised a vulnerability was being exploited.
This review brings together 20 of the most defining cybersecurity incidents in 2025. Each one highlights where threat detection broke down, or where visibility gaps created space for threat actors to work. This reveals the cybersecurity lessons learned that matter for next year.
Nation-state cybersecurity incidents 2025
State-linked groups shaped many cyber attacks 2025. Their cybercrime operations often blended espionage, disruption, and influence, which made attribution difficult and raised the stakes for national security.
1. India–Pakistan cyber conflict expands into critical sectors
Cyber conflict between India and Pakistan intensified after the mid-year standoff, and most of the pressure fell on government agencies and public institutions. Threat actors released data tied to Pakistan’s Federal Board of Revenue and circulated voter information from Indian state systems.
Some groups used deepfakes and stylised propaganda. Others focused on sites that carry national significance, aiming to unsettle public confidence rather than cause prolonged outages. The steady stream of announcements made it harder to separate genuine compromise from signalling.
- Impact: Leaked citizen data and short outages created anxiety across public services and added pressure on regional businesses.
- Lesson: During geopolitical spikes, organisations need early signals. New domains, cloned portals, and sudden messaging shifts often appear before the main attack.
2. Israel–Iran confrontation intensifies online
The latest phase of the Israel–Iran conflict moved quickly into cyberspace and produced a dense stream of operations from both sides. Within 48 hours of the initial flare-up on June 13 2025, CERT teams reported persistent probing by Iranian groups such as APT34 and APT42. Their campaigns targeted energy, telecommunications, and transport services inside Israel.
At the same time, Israeli operators struck back with disruptive malware attacks and distributed denial-of-service activity against Iranian infrastructure. Analysts recorded a 700% increase in cyber incidents during this period.
- Impact: Government agencies, telecom providers, and transport firms experienced repeated DDoS events and data exposure.
- Lesson: Escalation shifts fast during conflicts. Monitoring for unusual access attempts and sudden surges in infrastructure scans can give teams a small but valuable head start.
3. US charges 12 Chinese hackers in global intrusion campaigns
US-China cyber conflict has always been a hot topic. But this year, the US Justice Department charged twelve Chinese contractors and law enforcement officers for running coordinated intrusion campaigns against government agencies, critical infrastructure operators, and private companies.
The indictment described years of activity tied to two Ministry of State Security units. Their operations collected sensitive data from aerospace firms, national laboratories, defence contractors, and organisations involved in pandemic research. Prosecutors also linked the group to compromises against journalists and pro-democracy activists located outside China.
- Impact: The case exposed the scale of data taken during these campaigns, including information stored across cloud services and corporate networks.
- Lesson: Public attribution helps teams understand long-running intrusion patterns. Once a group’s methods are documented, defenders can strengthen monitoring around the specific sectors and technologies that were previously targeted.

4. North African cyber hostilities and the CNSS breach
Morocco’s CNSS breach became a focal point in a wider surge of regional cyber hostilities. The initial security incident took place in April and affected files stored across the agency’s systems, including medical and identity documentation shared by citizens and employers.
Analysts later linked the activity to Jabaroot, a group that re-emerged with claims against several North African ministries, banks, and private companies. Their posts showed how far the compromise extended and revealed that data from multiple public bodies had been collected over time.
- Impact: Sensitive documents from public institutions circulated on criminal forums and influenced regional tensions.
- Lesson: When state agencies are targeted, downstream verification checks become harder to trust. Continuous monitoring for leaked official documents helps limit further misuse.

5. Disruptions hit WestJet, Hawaiian Airlines, and American Airlines
June brought a cluster of aviation incidents that disrupted booking systems and passenger services across three major carriers. WestJet confirmed a cyberattack that affected internal systems and its mobile app, leaving customers with booking delays and intermittent errors for five days.
Hawaiian Airlines reported a separate incident that interrupted parts of its IT infrastructure, though operations and safety remained stable. American Airlines then faced a widespread outage in its flight information system that caused connectivity issues across check-in, booking, and baggage processes. Tracker data later showed that more than 40% of its flights were delayed and 7% were cancelled.
- Impact: Travellers experienced service disruptions while airlines worked to restore core digital systems.
- Lesson: Aviation relies on tightly linked digital processes. When even one system falters, operational delays spread quickly, which makes early detection and resilient failover strategies essential.
Data breaches 2025
Many of the most damaging information security breaches in 2025 came from gaps in supplier ecosystems and basic access controls. Breaches spread through widely used services and third-party platforms, which left companies exposed even when their own systems were secure. These incidents showed how fragile interconnected environments can be. And data protection is the first thing to go.
6. Shai-Hulud malware attack on the NPM ecosystem
The Shai-Hulud operation targeted the NPM ecosystem by publishing modified packages that blended legitimate code with malicious uploads. These releases appeared in several waves, including activity linked to GitHub, C/CICD, and cloud environments.
Developers downloaded the tampered packages during routine updates, which allowed the malware to move into downstream applications through normal build and deployment processes. The attack also featured automated propagation, enabling rapid spread across repositories that relied on interlinked dependencies.
- Impact: Multiple organisations unknowingly incorporated altered packages from malicious actors, increasing their exposure during routine development cycles.
- Lesson: Package registries function as active attack surfaces. Use automation for dependency checks and rapid validation of new uploads to avoid promoting compromised modules or misconfigurations into production.

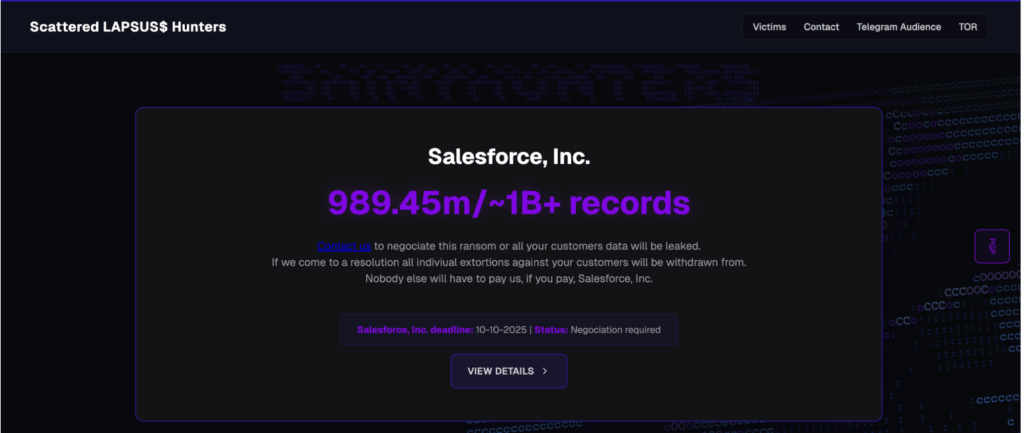
7. Salesforce cybersecurity breach
The Salesforce incident stemmed from an unauthorised login to an employee account, followed by the theft of authentication tokens. This access allowed the threat actors to reach customer environments and download sensitive integration metadata.
The group responsible, known as the Scattered LAPSUS$ Hunters, has a pattern of targeting single vendors to obtain footholds into downstream organisations. Their activity in this case showed how one compromised identity can ripple into multiple customer networks. The breach also highlighted the challenge of detecting malicious use of OAuth tokens because the traffic often resembles routine API activity.
- Impact: Organisations relying on connected apps saw their configuration data exposed, which increased the risk of further compromise.
- Lesson: Supplier incidents move quickly across linked systems. Monitoring for unusual OAuth usage and reviewing token permissions can limit escalation when a partner is breached, along with a strong incident response plan to mitigate the damage.
8. Harvest SAS breach by Run Some Wares
A ransomware attack on Harvest SAS began when the Run Some Wares ransomware group accessed internal systems and extracted a large collection of sensitive data in February 2025.
The group later published financial records, customer information, internal documents, and files containing provider details, treatment data, and insurance identifiers. Their leak site included proof that negotiations had broken down, with deadlines for payment already missed.
- Impact: Exposed documents covered banking data, medical identifiers, contract files, and personal records, which increased the risk of fraud and misuse.
- Lesson: When cybercriminals reach both administrative systems and cloud environments, data spreads quickly. Maintaining visibility across these layers helps security teams respond before information is exfiltrated.

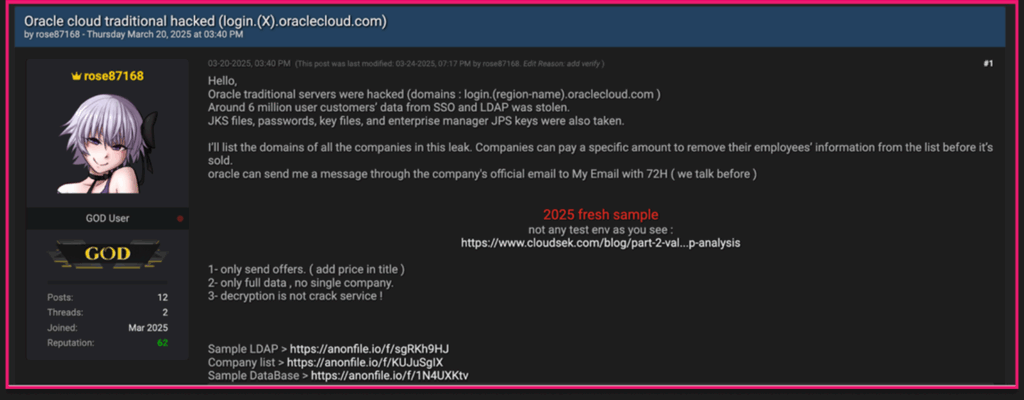
9. Oracle breach exposes customer data
The Oracle data leak in March 2025 involved unauthorised access to cloud infrastructure. Attackers were able to exfiltrate usernames, hashed passwords, and email addresses from Gen 1 servers, which were later offered for sale on cybercriminal forums.
The data security breach did not include financial records or full personal data, such as social security numbers. But it raised concerns because the intruders accessed authentication material that clients relied on for daily operations. Oracle confirmed it had applied security measures to limit further risk and stated that its newer Gen 2 servers were not affected.
- Impact: Exposed credentials created uncertainty for institutions using Oracle’s older cloud services, particularly where logins tied into wider IT systems.
- Lesson: Legacy cloud environments often hold outdated configurations that present avoidable openings. Regular reviews of identity systems, access controls, and migration paths help limit long-term exposure, as well as auditing third-party vendors.
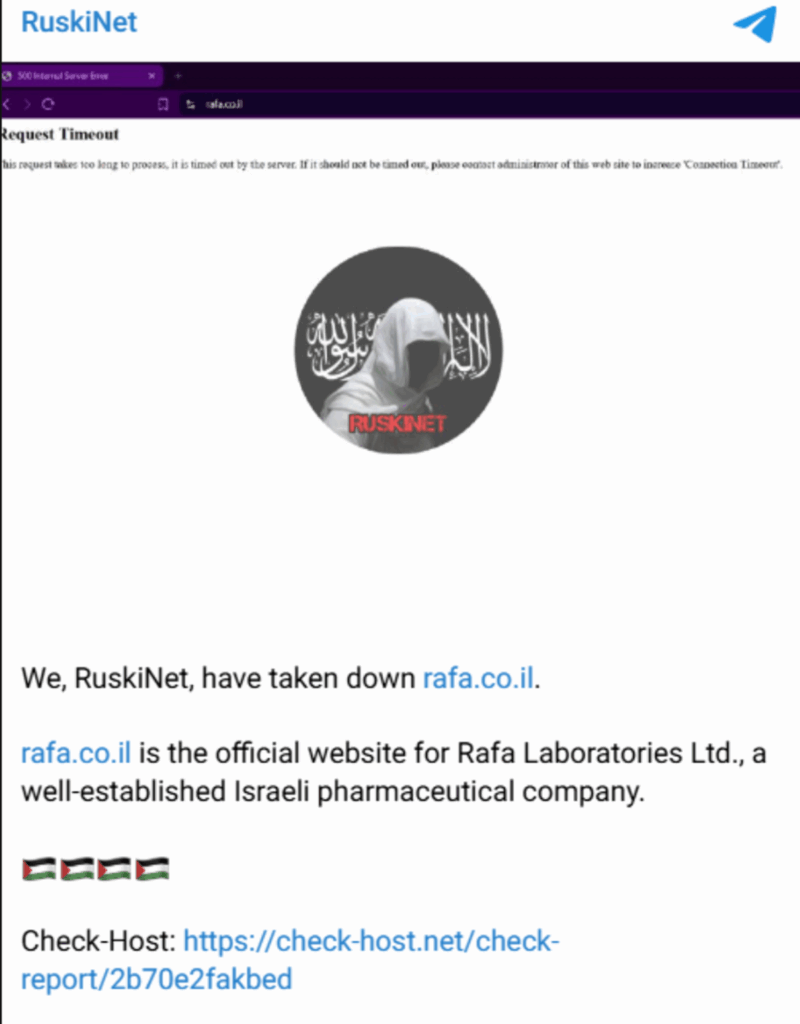
10. Ongoing attacks on the pharmaceutical sector
Pharmaceutical companies continued to experience frequent intrusions in 2025, with ransomware, espionage activity, and insider-enabled access all appearing in recent investigations.
Several groups were active in this space, including Qilin, Cl0p, and RuskiNet, each using different approaches to steal data or disrupt laboratories, manufacturing systems, and business operations. Some incidents involved stolen employee credentials sold online, which opened a path for targeted access. Others stemmed from politically motivated hacktivism that aimed at high-profile firms.
- Impact: Breaches exposed proprietary R&D material, internal documents, and sensitive business files that could influence competitive strategy, and snowball into new cyber risks along the way.
- Lesson: Pharmaceutical networks demand consistent monitoring of external credential leaks and early signs of targeted reconnaissance. Detecting initial access attempts gives teams a chance to contain intrusions before attackers reach research systems or manufacturing workflows.
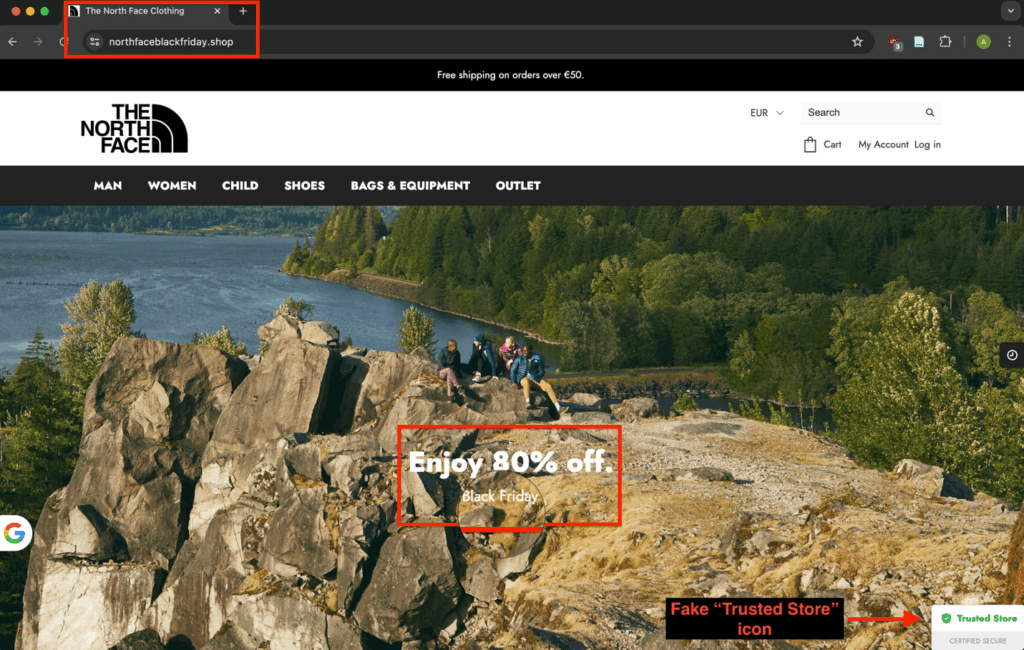
11. Black Friday scams lead to credit card data theft
Like every year, Black Friday has been a prime opportunity for cyber threat groups. It’s a season where they can tailor look-alike retailer and delivery-service pages designed to harvest login details and payment information.
Many scams rely on fake order updates, shipping notices, and promotional offers that mimic the tone and layout of legitimate service providers. The surge in shopping activity made by Black Friday can make these lures more convincing, and users may enter credentials before spotting anything unusual.
For instance, one fraud network created 4,700 fake shopping sites to steal credit card details over the Black Friday season.
- Impact: Stolen account details and card information fed into payment fraud and account misuse.
- Lesson: Shopping periods change how people read emails and notifications, so awareness efforts and security practices need to adjust as those patterns shift.
12. Tax season scams imitate tax authorities
Tax season is another time of year that continues to draw opportunistic attackers. They rely on urgency and official-looking messages to trick people into handing over sensitive information. This year’s analysis showed a rise in phishing campaigns that mimicked IRS correspondence, promising refunds or warning of account issues. These emails often linked to pages designed to capture Social Security numbers, bank details, and tax-filing credentials.
Experts also flagged exposure of taxpayer documents on criminal platforms, including identity records and financial forms taken from previous breaches. Fake tax preparer accounts added another layer of risk, particularly for people who rely on social media recommendations during filing season.
- Impact: Stolen documents and login details opened the door to fraudulent returns and refund diversion.
- Lesson: Tax scams follow a predictable rhythm each year. Early monitoring for impersonation attempts and checks for leaked taxpayer data give teams more time to block fraudulent filings before they reach tax authorities.
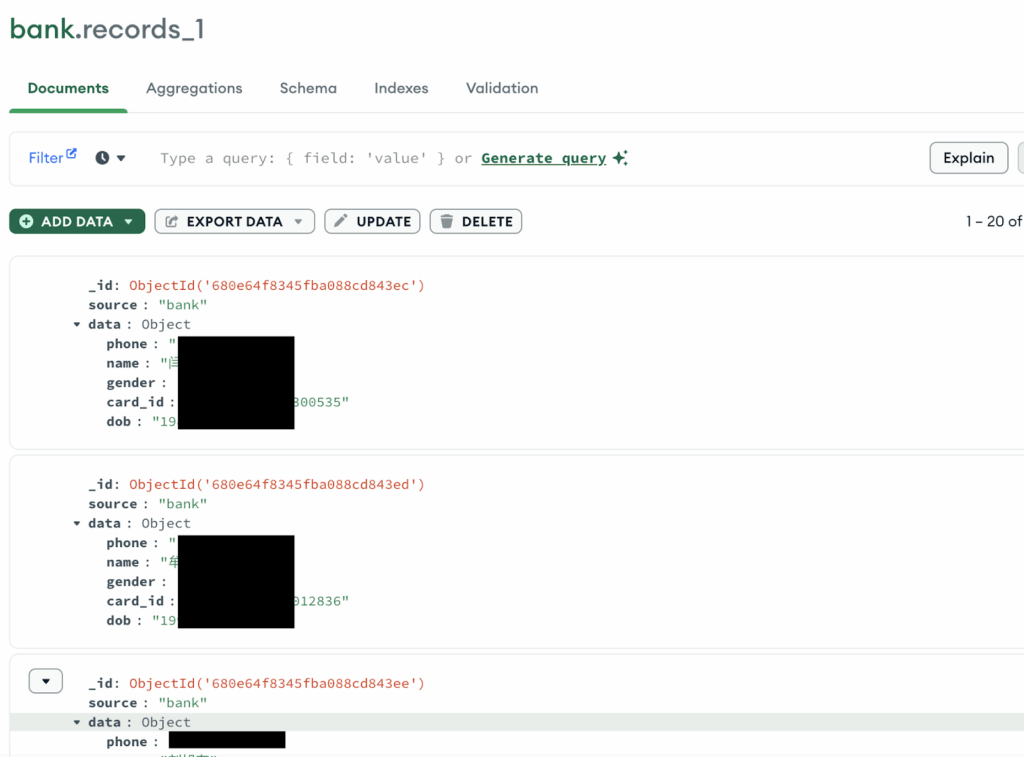
13. Chinese network leak exposes 4 billion personal records
Security researchers uncovered a vast dataset containing more than 4 billion personal records linked to major Chinese platforms, including Alipay and WeChat.
The exposed information covered contact information such as phone numbers, along with home and work addresses, transaction-linked identifiers, and behavioral data showing how users interacted with different online services. The leak was traced to a 631-gigabyte database left accessible without a password, which allowed anyone who found it to browse or download the files.
- Impact: Phone numbers, addresses, and activity profiles became publicly accessible, increasing the likelihood of targeted fraud, identity theft, and unwanted tracking.
- Lesson: Large breaches are often caused by misconfigured storage rather than sophisticated intrusion. Continuous discovery of exposed databases can prevent sensitive information from remaining openly available for long periods.
14. SimonMed Imaging confirms cyberattack affecting 1.27 million individuals
SimonMed Imaging later confirmed that a January 2025 cyberattack exposed the protected health information of roughly 1.27 million individuals. The Medusa ransomware group claimed responsibility and said it had stolen more than 212 GB of data.
According to HIPAA, the information is not currently listed on Medusa’s leak site, which may indicate that the ransom was paid. Despite the incident occurring in January, affected patients did not receive notification letters until October.
- Impact: Medical records, insurance details, diagnoses, treatment data, and identification numbers were compromised, creating sustained risk for fraud and misuse.
- Lesson: Long gaps between an intrusion and public notification can deepen operational and regulatory exposure. Consistent monitoring of clinical systems and vendor activity helps reduce the chance of similar delays.
Ransomware attacks 2025
Ransomware groups adapted by forming alliances and sharing infrastructure. This created faster campaigns and unpredictable attack patterns. Traditional tracking of single groups became less useful once toolsets and dark web leak sites began to overlap.
15. LockBit, Qilin, and DragonForce form a ransomware alliance
Q3 2025 saw LockBit, Qilin, and DragonForce move into closer coordination. Experts traced shared tooling, infrastructure, and data-leak resources linking the three groups. It is an unusual moment in the ransomware ecosystem, which normally pushes operators to compete rather than collaborate.
But the shift appears to benefit all three. LockBit is rebuilding after its takedown. Qilin’s operators have been gathering momentum. And DragonForce has continued its move from disruptive hacktivism into organised extortion. Analysts noted a pattern of shared “techniques, resources, and infrastructure,” even if the internal mechanics of the alliance remain out of sight.
- Impact: The collaboration may lead to faster attacks and blurred attribution.
- Lesson: Criminal alliances like these will shift defensive priorities. It means that tracking infrastructure becomes as important as tracking individual groups.
AI powered security breaches 2025
AI tools changed how attackers craft convincing content and interact with victims. The speed and scale of AI generated material helped criminals test ideas and adjust tactics with little effort. This raised the pressure on security teams because detection depended on understanding behavior, not just spotting errors in an email.
16. AI generated fake news networks
Investigators have identified large networks of fake AI-driven news sites that publish fabricated stories and impersonate legitimate outlets.
These pages recycle political narratives, copy branding from real publications, and rely on automated content engines to push out high volumes of misleading material. Some domains were linked to financially motivated operators, while others appeared tied to influence campaigns targeting voters in several regions.
- Impact: False reporting spreads quickly across social platforms, creating confusion around real events and fuelling divisive narratives. These campaigns can compromise election integrity and brand safety, as well as creating openings for social engineering attempts that later enabled unauthorized access.
- Lesson: Teams need clearer risk management processes for verifying sources, tracking cloned domains, and spotting coordinated posting patterns.
17. AI powered phishing tactics
Attackers are now using AI tools to write cleaner emails, copy a company’s tone of voice, and personalise lures with real-time scraped data. These messages can bypass traditional red flags because they look polished and match internal communication styles. In several examples, AI-generated content and spoofed domains are used together to push victims toward credential-harvesting pages.
- Impact: Employees receive messages that feel legitimate, which increases the likelihood of quick replies or password submission.
- Lesson: Security teams need regular exposure to real-world phishing examples rather than static checklists. Monitoring for sudden clusters of new domains and unusual login attempts also helps uncover campaigns that rely on AI-driven automation.
Insider threat landscape 2025
Insider incidents became more common and more difficult to manage. Misused credentials and quiet data theft created long investigations and expensive containment work. These cases highlighted how access governance shapes the outcome of nearly every security event.
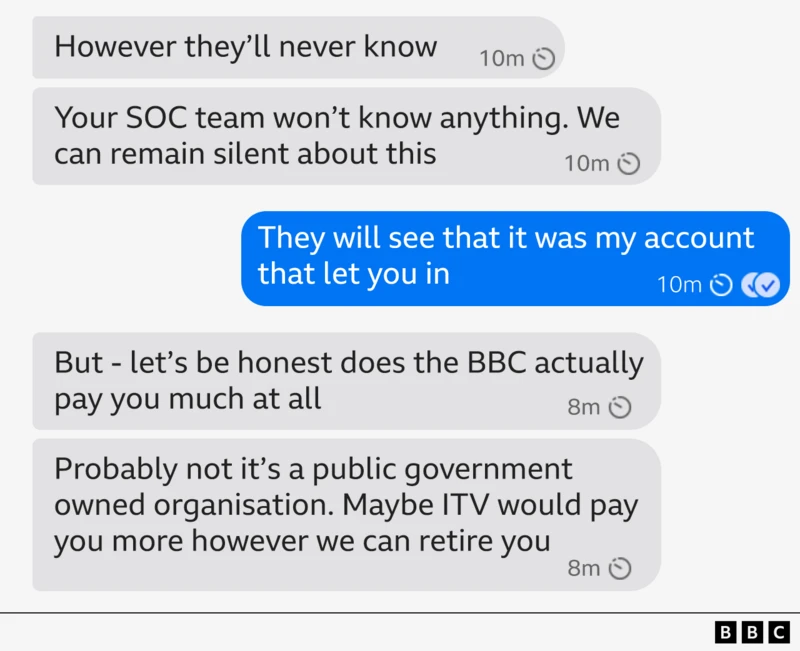
18. BBC journalist exposes social engineering tactics
BBC reporter Joe Tidy spent several days in conversation with someone claiming to be part of the Medusa ransomware group. He unpacked the whole experience in a BBC article, revealing the common social engineering tactics adopted by cybercriminals.
The exchange began on Signal with promises of life-changing wealth, and quickly revealed how attackers mix charm, pressure, and staged goodwill to recruit insiders. The criminal offered a cut of any ransom, sent repeated follow-up messages, and even suggested a $55,000 “deposit” to win trust.
As Joe resisted, the tactics escalated. The attacker shifted tone, increased message frequency, and triggered waves of unsolicited MFA requests to create stress. The threat actor eventually vanished without gaining access.
- Impact: The incident offered a rare inside view into how attackers cultivate insider threats. It showed how quickly rapport-building, financial incentives, and MFA fatigue can wear down a target’s decision-making.
- Lesson: Organisations should prepare employees for real conversational pressure, not just generic phishing examples. Clear escalation paths, strong MFA protections, and support during suspicious interactions help prevent social engineers from exploiting uncertainty or fatigue.
19. Insider threats rise across organisations
83% of organisations experienced at least one insider attack in 2024, and the number of companies reporting 11–20 incidents jumped sharply from 4% to 21%. The shift reflects how hybrid cloud adoption, sprawling digital ecosystems, and everyday operational shortcuts create more room for mistakes and misuse. And this can only have accelerated further in 2025.
- Impact: Insider incidents now disrupt operations more frequently, and the gap between perceived control and actual enforcement is widening.
- Lesson: Insider risk management has to mature alongside cloud and hybrid adoption. Organisations need stronger, unified visibility across accounts and systems, better employee awareness, and clear enforcement of access policies.
API, cloud, and infrastructure major hacks 2025
APIs and cloud services expanded faster than many organisations could track. New endpoints appeared without documentation and exposed sensitive data to anyone who went looking. These gaps made it clear that external visibility is essential for understanding modern attack surfaces.
20. 99% of organizations report API security incidents
A February 2025 API threat report showed that nearly every surveyed organisation had faced at least one API security issue in the previous year. Injection flaws and Broken Object Level Authorisation (BOLA) accounted for more than a third of all incidents, followed by sensitive data exposure and broken authentication.
The findings also revealed that 95% of attacks came from authenticated sessions, highlighting how easily weaknesses hide behind valid tokens. Despite this, only a small fraction of organisations had a formal governance strategy in place.
- Impact: Operational delays are becoming common, with more than half of teams reporting slowed software rollouts due to API concerns. External-facing APIs remain the most targeted, and generative AI codebases are adding new sources of risk.
- Lesson: API security needs consistent governance. Organisations must strengthen posture management, tighten authorisation checks, and treat authenticated sessions as potential entry points, not assurances of safety.
Conclusion
These twenty incidents show how quickly threats shifted in 2025. Some attacks relied on technical skill. Others exploited predictable behaviour. All of them revealed gaps in visibility across external assets and supplier networks.
CybelAngel supports teams by uncovering unknown assets, detecting malicious infrastructure, and identifying threats before they reach customers or production systems. Better visibility leads to faster decisions, and faster decisions reduce the impact when incidents unfold. Book a demo to see how you could stay one step ahead in 2026.

