
How to Avoid Cybersecurity Tool Sprawl and Resource Waste
Discover why 75% of organizations are consolidating security vendors.* The hidden paradox threatening security teams..
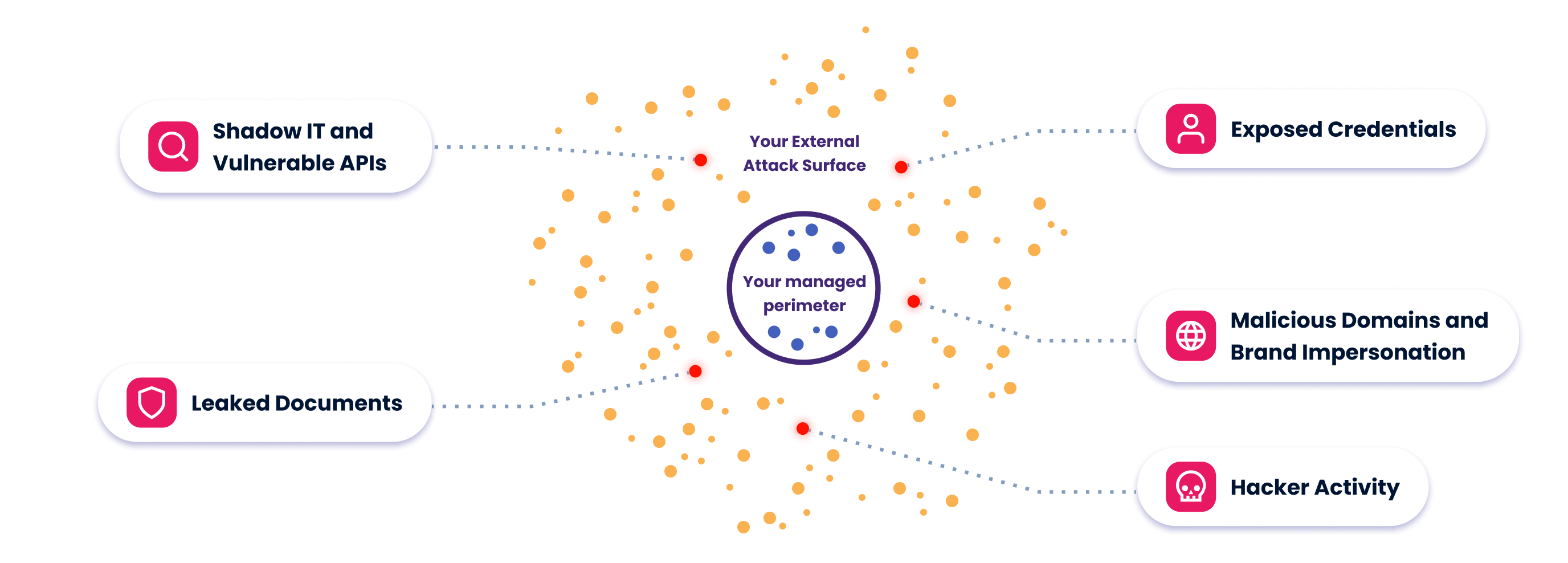
Thanks to daily and comprehensive scans of the internet, CybelAngel provides you with a holistic view of all the exposed assets and vulnerabilities you potentially have outside of your IT network.
The dual power of CybelAngel’s unique AI model, which processes billions of data points every day, combined with an experienced and dedicated analyst team, ensures you always receive the information and level of detail you need for your incidents.
With detailed incident reports that include file paths, document classification, threat actor profiles, and TTPs (Tactics, Techniques, and Procedures), you can remediate quickly. CybelAngel also supports all takedown efforts with specialized threat investigations, third-party risk management, and M&A cybersecurity due diligence services.




The CybelAngel blog provides straightforward, context-driven insights into external threats, API issues, and emerging vulnerability patterns. Delve into actionable insights for you and your SOC team today!
Demystify CybercrimeHere's how top security leaders are preparing for 2026

The most innovative clients across various industries—including finance, manufacturing, pharmaceuticals, luxury, and retail—trust CybelAngel to secure their attack surface.
Request a Custom DemoLearn more about the products and services offered by CybelAngel, the leading Cyber Threat Intelligence platform. From comprehensive Asset Discovery and Monitoring to proactive Data Breach Prevention, Third-Party Risk Assessments, and M&A Cyber Due Diligence, CybelAngel empowers organizations to effectively secure their external digital assets, manage vulnerabilities, and mitigate cyber threats before they occur.
Tap into our external threat intelligence cyber insights to get a fresh perspective.