The State of API Security in 2026: Threats, Trends, and What to Prepare For

Table of contents
Thousands of application programming interfaces (APIs) are used daily to power online payments, microservices, and make functions between applications easy. But there‘s a dark side to the convenience of APIs.
Going into 2026, it‘s clear that third-party APIs present a major security risk. Over 80% of surveyed organizations faced problems with API security, and only 10% of organizations currently have an API posture governance strategy in place.

In this 2026 trend forecast, we‘ll break down the top API attack vectors, security standards to help break the cycle of API attacks, and provide insight into how hackers are abusing APIs.
Emerging API threat vectors to watch out for
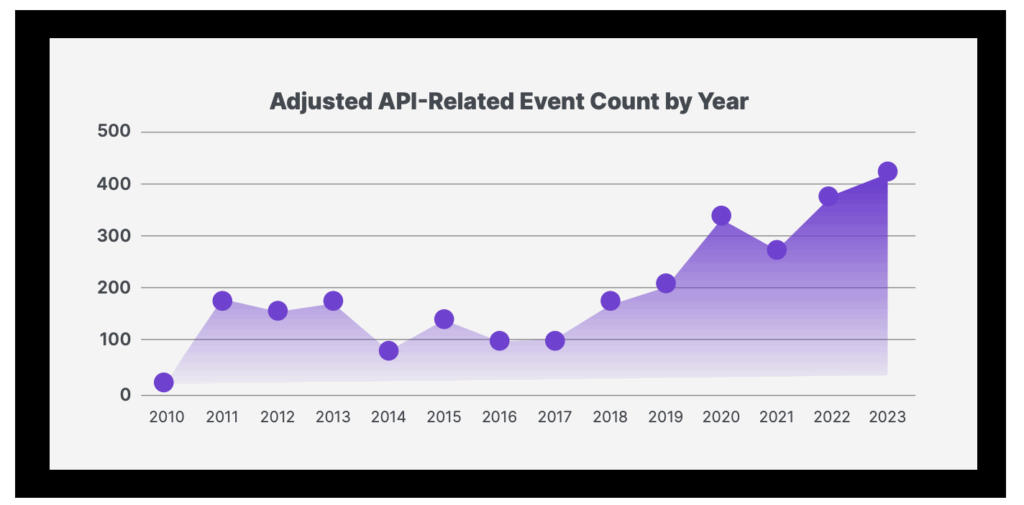
The prevalence of recent API attacks in the last 5 years highlights the need for an API security strategy, coupled with threat detection and strong authentication.
Recent studies from 2024 outline the most prevalent threats. Vectors like SQL attacks increased by 60% year-over-year and will continue to do so into 2026.
Having an unsecured API can open you up to several security vulnerabilities:
- Unrestricted access to business flows, where attackers can hijack business logic for malicious functions.
- Exposure of unprotected files and directories through misconfigured TLS encryption.
- Bypassing of network boundaries by exploiting third-party APIs with server-side request forgery (SSRF) flaws.
API security threats to watch out for
1. AI-powered API attacks
- What is it? AI systems initiate API calls autonomously with bots for daily business flows.
- The risk: Attackers can utilize AI bots to learn from API responses in real-time, rapidly identifying misconfigurations and exposed endpoints.
2. Injection attacks
- What is it? Injection attacks refer to both SQL injection and cross-site scripting (XSS). SQL injections inject malicious code into an API request to gain unauthorized access to a database. XSS is used to inject code into a web page accessed through an API.
- The risk: Attackers can use custom injections within an API request to send malicious input, allowing attackers to modify data, bypass authentication mechanisms, execute commands, or crash services.
3. Supply chain compromise
- What is it? Supply chain compromise involved third-party APIs being targeted by threat actors who take advantage of security misconfigurations and vulnerabilities to gain access to systems without permission.
- The risk: APIs that are integrated into the IT ecosystem without being scanned for vulnerabilities can lead to adversaries placing backdoors through malware injections, disrupting the entire supply chain. Threat actors can also add trojans, droppers, or rootkits to gain access to the wider network.
4. Shadow APIs
- What is it? Shadow API risks refer to the APIs within an organization‘s ecosystem that aren‘t managed or secured, but are introduced usually by employees during app development.
- The risk: When APIs aren‘t managed by the organization‘s security teams, it‘s impossible to secure API against emerging vulnerabilities. Shadow APIs risk exposure to sensitive data, lateral movement leading to escalation to accounts with higher permissions, and exploitation of novel API vulnerabilities.
5. Broken object-level authorization (BOLA)
- What is it? BOLA is a flaw in the access control mechanism of a web application, meaning that the API doesn‘t enforce authorization at the endpoint level, leading to attackers gaining unauthorized access.
- The risk: Broken function-level authorization opens an organization up to significant data breaches and data loss. Once API tokens are leaked or stolen, the API‘s security is compromised.
6. GraphQL vulnerabilities

- What is it? GraphQL is a query language used to develop APIs, allowing the client to request specific data and making the process more efficient. However, GraphQL can be exploited through introspection features, revealing the entire API schema if left enabled in production.
- The risk: Organizations often don‘t monitor GraphQL traffic, in contrast to REST, allowing vulnerabilities to fly under the radar. Strong GraphQL security means blocking a threat actor‘s access to sensitive data like passwords, API tokens, or employee IDs.
Case studies
Azure AD exposes user information from an unsecured API endpoint
When: May 2025.
What happened: CloudSEK researchers discovered a flaw in an aviation giant‘s system. An unsecured API endpoint granted access tokens to Microsoft Graph with elevated privileges, leading to the exposure of sensitive information to 50,000 Azure AD users.
What went wrong: The JavaScript bundle with a subdomain included a hardcoded endpoint that could be accessed without authentication, and the Microsoft API token contained elevated permissions. A compromised token could enable a hacker to access sensitive employee data.
The impact: The organization‘s attack surface was increased, leaving it open to future pervasive attacks. The vulnerabilities also introduce compliance risks under GDPR and CCPA, leading to fines and loss of reputation.

Hackers steal Facebook account data with API authentication bypass
When: May 2025.
What happened: Hackers claimed to have scraped data from 1.2 billion Facebook accounts by abusing one of Facebook’s APIs. To date, this is one of the largest data breaches in Meta‘s history.
What went wrong: Weak user authentication allowed threat actors to leverage the endpoint, scraping the data of thousands of users at scale.
The impact: The data was soon posted to dark web forums to perpetrate social engineering attacks; however, researchers caution that the actual number of exposed users is likely lower due to the hacker‘s inconsistent history.

Stripe APIs hijacked for credit card skimming attacks
When: Ongoing since August 2024.
What happened: Legacy Stripe APIs were hijacked by attackers to process fraudulent payments via card skimming on at least 49 compromised e-commerce websites. Stripe warns that the full list of victims is likely higher, and an investigation is still ongoing.
What went wrong: Attackers injected malicious code that overlaid the legitimate checkout page with a fake one to perform a Magecart attack. The overlaid page harvested user payment information and then sent a fake error to reload the page, triggering the legacy Stripe API to validate the credit card numbers before exfiltrating them, sending the working card data to attacker-controlled servers.
The impact: Customers had their sensitive data stolen, allowing attackers to make off with funds and resell user data on the dark web.
Intel employees‘ data exposed from an API vulnerability
When: August 2025.
What happened: A security researcher discovered that they could bypass authentication on Intel’s corporate business card ordering website in India. Nearly 1GB of JSON files were gathered by the whitehat hacker, which contained nearly all details of 270K Intel employees, all from 1 API request.
What went wrong: The researcher uncovered 4 API vulnerabilities that allowed for exfiltration of sensitive information. From these vulnerabilities, they were able to modify sitewide code, allowing access to multiple internal sites.
The impact: It was discovered that Intel’s Hierarchy Management website contained an easily decryptable password that could be used to gain administrative rights to the system. This rendered the encryption void, allowing a potential attacker to gain access to employee information and unreleased products.
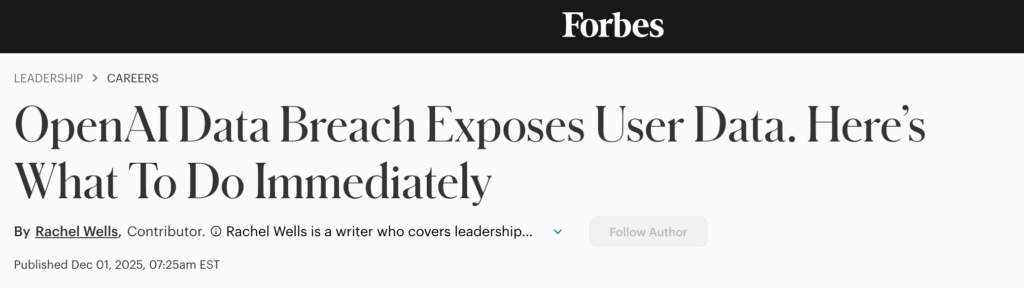
OpenAI exposes customer data in API breach
When: November 9, 2025.
What happened: OpenAI announced that its third‑party analytics provider, Mixpanel, experienced unauthorized access, allowing hackers to export an analytics dataset.
What went wrong: As of posting, OpenAI has not released how the attackers managed to breach Mixpanel, with further investigations currently ongoing.
The impact: Mixpanel‘s CEO warned that the leaked data could be leveraged in phishing and social-engineering attacks, used to compromise organizations.
Top 10 OWASP vulnerabilities identified in 2025
OWASP (Open Web Application Security Project) is a non-profit focused on improving web application security through open-source projects.
The OWASP Top 10 for 2025 showcases the vulnerabilities to watch out for, in addition to the OWASP API Security guidelines to course correct.

Let‘s look at how attackers can exploit APIs to cause damage:
- Access control vulnerabilities: When permission checks are improperly implemented, they allow hackers to access or modify data.
- Price oracle manipulation: Price oracles are external data feeds used by smart contracts. When abused, hackers can exploit poorly designed oracle mechanisms to inflate or deflate asset prices temporarily, leading to financial losses and system failures.
- Logic errors: Logic errors occur when a flaw in the API‘s design is abused by attackers. Hackers can then bypass user authentication and escalate privileges.
- Lack of input validation: Input validation is a critical API safeguard that prevents attacks and protects data integrity. When user inputs are compromised, hackers can inject malicious data into smart contracts, causing a break in contract logic.
- Reentrancy attacks: Reentrancy is a smart contract vulnerability, allowing repeated external contract calls into a function before the original execution is finished. This leads to attackers exploiting the contract‘s state to perform malicious actions like draining funds.
- Unchecked external calls: When smart contracts fail to verify external calls, the API proceeds with incorrect assumptions about the transaction, allowing hackers to bypass API conditions and manipulate balances.
- Flash loan attacks: Flash loans allow users to borrow funds without collateral in the blockchain. Attackers can exploit flash loans to manipulate markets or drain liquidity protocols.
- Integer overflow and underflow: Integer overflow and underflow in APIs occur when numeric values exceed their limits, causing wraparounds. Hackers can manipulate the errors in this process, allowing them to exceed data type limits, manipulate balances, and bypass restrictions.
- Insecure randomness: When APIs rely on weak or predictable random number generation, hackers can exploit this vulnerability to hijack sessions, forge tokens, and bypass user authentication.
- Distributed denial of service (DDoS) attacks: API unrestricted resource consumption is a vulnerability leveraged by hackers to overwhelm endpoints, escalating to DDoS attacks.
FAQs & API security best practices
What is an API?
An application programming interface (API) is a set of protocols to enable data transfer from one endpoint to another. Developers use APIs to connect applications, save time in the development process.
What security risks do APIs introduce?
APIs are useful and time-saving, but they also introduce risks into your external attack surface. Since APIs are often implemented without security controls, the door is left open for attackers.
Throughout the API lifecycle, developers and security professionals shouldn‘t assume APIs will only be used by employees and implement stringent security controls.
Why are APIs a common target for attackers?
APIs are a common target for attackers as they provide an entry point to the organization‘s sensitive data and business logic. Businesses across the world use APIs daily to manage various apps and platforms, giving attackers a wide array of exploits to try.
How can organizations protect against API misuse?
- Implement firewalls: Web application firewalls (WAF) can block suspicious API requests like data scraping and malicious injection attacks.
- Use OAuth: Hardcoded endpoints aren‘t secure, leading to attackers reusing tokens or leaking hardcoded keys. OAuth only grants limited access and provides temporary access tokens.
- Validate all received data: Including headers, payloads, and business logic as a safeguard against malicious attacks.
- Build an API inventory: Eliminate shadow APIs by building an inventory of deployed API versions. Proper API inventory management reduces endpoint exposure and mitigates risk.
- Set rate limits: Monitoring traffic and enforcing limits will flag suspicious requests before they snowball.
- Monitor traffic and enforce limits: Set rate limits and alerts to flag unusual patterns in API gateways. This way, you can avoid DDoS attacks and track incoming requests.
- Enable runtime protection: Secure APIs in a live environment to ensure active defense against anomalies.
How can organizations discover shadow APIs?
Shadow APIs are unmanaged APIs left behind unknowingly or downloaded outside of the organization‘s security measures. Attackers actively hunt for shadow APIs in the hopes that the organization won‘t discover the suspicious traffic.
To improve security posture, organizations can:
- Use specialized platforms to monitor all API traffic and detect undocumented APIs. API discovery tools can also be useful to automate the process.
- Inspect logs from API gateways, load balancers, and firewalls to spot unusual endpoints being called.
- Review CI/CD pipelines for APIs deployed outside governance structures.
How can organizations secure APIs in AI-powered systems?
Securing APIs against threat actors utilizing AI is essential. Hackers often craft malicious prompts to bypass traditional API security measures.
Stop potential threats with these security solutions:
- Sanitize and secure AI inputs before passing them through.
- Enforce schema validation at the API gateway and reject any request that doesn’t match.
- Test APIs with crafted malicious inputs like prompt injection, malformed data, or model evasion attempts.
What should organizations do after detecting an API breach?
In the face of a cyberattack, it‘s important to react quickly to minimize data exposure:
- Contain the breach by disabling or restricting compromised APIs.
- Review all API endpoints against function-level authorization flaws to prevent unauthorized access.
- Revoke exposed tokens, API keys, or credentials.
- Implement your incident response plan and regulatory requirements.
- Collect logs and request payloads to document the incident.
Secure Your API Ecosystem with CybelAngel’s Threat Intelligence
API‘s are a convenient way to ensure integration across systems, but they pose a cybersecurity risk to the entire organization.
From broken authentication to AI-powered attacks, API security risks are evolving year over year.
Ensure security best practices from the front-end to the back-end with expert threat intelligence.
CybelAngel helps security professionals protect endpoints, detect anomalies in API traffic, and protect your data from being exposed.

