
Are domain squatters hijacking your business?
When there are fake search results for your enterprise, what do you do? What if the fake results link to malware or illicit content? It hurts when pirates commandeer your brand online. What do you do if hackers misrepresent your company name, products or services online? When someone registers in bad faith domains that are associated with your enterprise, then your brand — and your business — are at risk.
What is domain squatting?
Domain squatters are modern day privateers who commandeer the Internet domains of others. Domain squatters register, traffic in, or use an internet domain with bad faith to profit from the goodwill of a trademark belonging to someone else. Hijacked web domains are not new; and their incidence is up. According to the World Intellectual Property Organization (WIPO), the “pandemic appears to have fueled an increase in cybercrime. This is also true for cybersquatting cases…which has clocked a steady increase.” In the chart below, see the increase at the WIPO this year for case filings for cybersquatting. 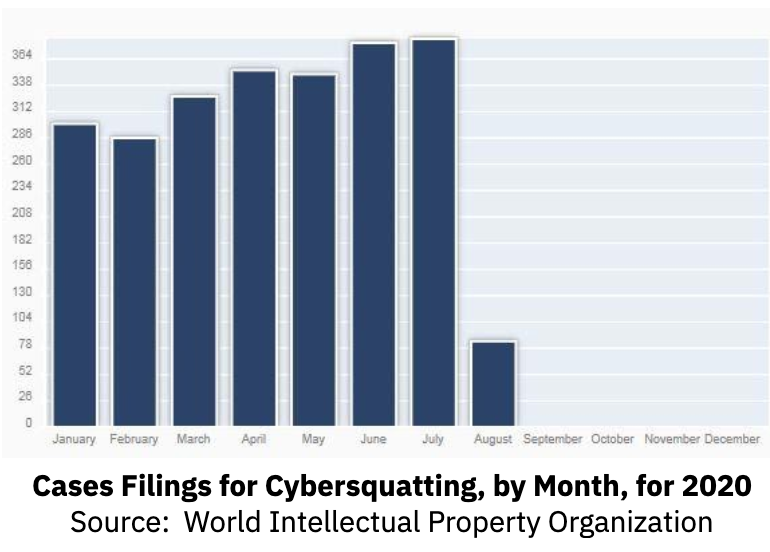 In today’s digital world, it’s faster to find data online than in person — so enterprises must ensure there are no fake domains associated with their business. When domain squatters register an internet domain associated with the domain of your company, they may try to sell that domain to your company — or use the domain for nefarious activity, such as hosting malware, pornographic, or other content that the user was not expecting. When fake search results reflect negatively on your enterprise, it does damage to your reputation and business, regardless of whether it’s your site.
In today’s digital world, it’s faster to find data online than in person — so enterprises must ensure there are no fake domains associated with their business. When domain squatters register an internet domain associated with the domain of your company, they may try to sell that domain to your company — or use the domain for nefarious activity, such as hosting malware, pornographic, or other content that the user was not expecting. When fake search results reflect negatively on your enterprise, it does damage to your reputation and business, regardless of whether it’s your site.
Focus on business, not hijacked domains
At CybelAngel, we focus on hijacked domains so you don’t have to. We use augmented machine learning to identify sensitive data leaks, including hijacked domains. Big names that have been hijacked are reported to include: Chevron, the Red Cross, UNESCO, 3M, Getty Images, Hawaiian Airlines, Arm, Warner Brothers, Honeywell, Autodesk, Toshiba, Xerox, the NHS, Siemens, Volvo, Clear Channel, Total, and others (according to The Register). In that discovery, over “240 website subdomains belonging to organizations…were hijacked to redirect netizens to malware, pornographic material, online gambling, and other unexpected content…And it’s all due to the way they were hosted in Microsoft’s Azure cloud.” In one example, a subdomain of Xerox was hijacked to host pages that linked to websites that advertised escorts, kitchenware, and oil paintings — all in the hope that the reputation of Xerox.com would boost the linked-to sites in search engine rankings. With CybelAngel at work, we identify and track domain squatters and sensitive data leaks all the way through remediation (as requested). Whether it’s cybersquatting on a client’s products, services, brand, or Internet domains, when our platform identifies a significant risk, the risk is assessed and an instant alert goes to the client, along with a rank of risk severity.
Types of Cybersquatting
Beyond criminal, there are other forms of cybersquatting. We will focus on Criminal Cybersquatting, Protective Domain Squatting, and Unintentional Domain Squatting.
Criminal Cybersquatting
With so many ways to hack a domain, it’s essential to know the types of cybersquatting so you can prevent them. Below are the main ways that hackers will attempt to hijack your domain.
Typosquatting – Also known as URL hijacking, a string site, and fake URL, typosquatters take advantage of typical misspellings used in search. Typosquatters will use misspellings, different phrasing, variations of target domain, and fake websites.
Identity theft – Cybersquatters monitor when a domain owner does not renew a domain, and will swoop in and surreptitiously register that domain. Next, the hacker may try to sell the domain to the original owner or link the domain to whatever site they want, including potentially a copy of the original website.
Name jacking – This is when someone registers a domain name associated with a famous individual. Celebrities are often targeted for this kind of cybersquatting. There is no trademark protection for people who are not famous. If someone registers a domain in your name and you are not famous, it is difficult to force that person to release the domain.
Reverse cybersquatting – This is when someone tries to pressure the domain owner into transferring legitimate ownership to another person or organization that has registered a trademark that is reflected in the domain name.
Protective Domain Squatting
This is a proactive measure that enterprises take to prevent the hijack of their domains. This legal form of domain squatting is when companies register multiple versions of their domains in order to protect their brand name. The company does not intend to use these domains, but registering them prevents criminals from doing so.
Unintentional Domain Squatting
Registering a domain that is your name — and similar to a trademarked brand name — can put you in a situation where you are forced to relinquish the domain. This situation is unintentional domain squatting: when a person registers a domain that they did not know was similar to a trademarked name. When this happens, the trademarked business may try to buy the domain from you or take you to court to obtain the domain name. For a good story about unintentional domain squatting, see what happened with teenager Mike Rowe registered MikeRoweSoft.com and Microsoft sent him a 25-page order to cease and desist.
Protect your domain against hijacks
Find out where your data is vulnerable, before criminals do. CybelAngel is armed with advanced machine learning and cybersecurity analysts who protect against online pirates. Download our free Dashboard for Data Leaks to find out where your data is leaking. At CybelAngel, we use heavenly technology to ensure smooth sailing on the web. If you are concerned about cybersquatting on your domain, contact us. CybelAngel detects and tracks down all kinds of risk to sensitive data, including cybersquatting, anywhere it occurs on the web.