The Dark Side of Black Friday: Scams, Spoofing, and Exploits

Table of contents
As Black Friday and the holiday season approach, shoppers are primed to snag the best deals online before they miss out. There‘s just one problem—hackers are also looking for their next target to make some quick holiday cash.
Threat actors have a ream of tricks up their sleeves to deceive shoppers into handing over their hard-earned money. Fake storefronts, spoofed domains, and malicious SEO results online make it more difficult for customers to shop online with confidence.
In 2025, between 70% – 80% of retail businesses are reported to have faced cyber attacks, with 81% of customers saying they would stop doing business with a company online after a data breach.
Cyber attacks on retail businesses already cost on average $3.54 million. When a data breach occurs, it takes roughly 280 days to contain, giving hackers plenty of time to make off with sensitive customer data.
In this article, we‘ll explore how e-commerce security is more important than ever, how hackers exploit online vulnerabilities, and what you can do to prevent e-commerce fraud.
The role of AI in e-commerce fraud
In 2025, cybercriminals are leveraging generative AI to launch fraudulent websites, generate fake reviews, and fabricate synthetic identities to scam consumers.
GenAI and deepfakes make it more difficult for customers to discern whether a website is legitimate, leading to stolen credentials and sensitive financial information. According to recent reports, AI-powered fraud is estimated to reach $10 trillion globally in 2025.
Hackers use AI to:
- Create convincing phishing emails and text messages that mimic brand sales and discounts. This form of social engineering exploits customer trust, especially during the holiday season.
- Generate synthetic identities that bypass traditional Know Your Customer (KYC) regulations. Mass-producing synthetic customer identities enables threat actors to apply for illicit merchant accounts.
- Deploy bots that behave like real customers to execute fraud schemes. Hackers use bots to automate account takeovers, fake purchases, and harvest pricing to make their fake websites appear legitimate.
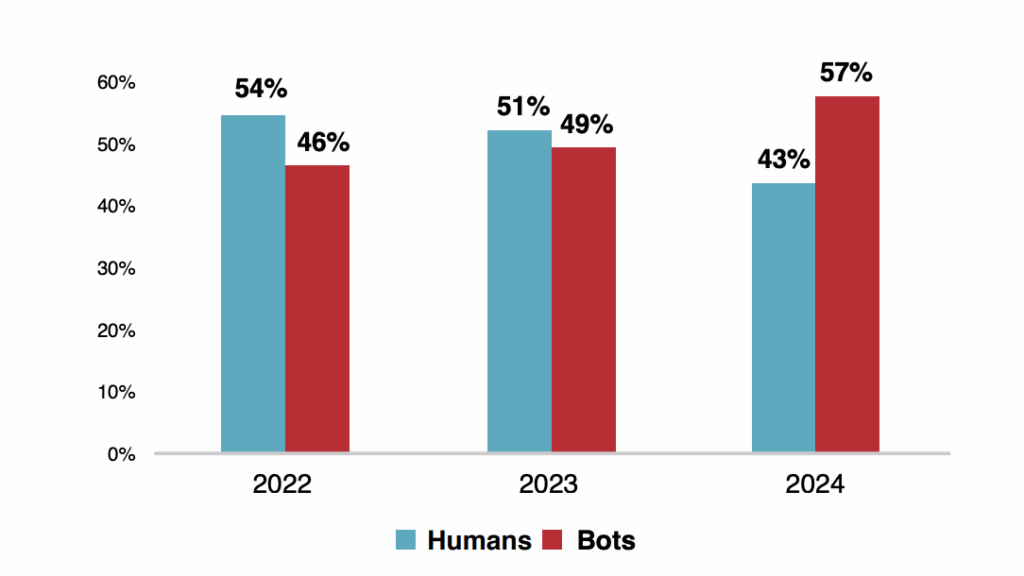
The use of AI in e-commerce fraud undermines traditional verification practices, amplifying risks across the industry.
Online shopping and the widening attack surface
Customers don‘t just shop on desktops; they also shop via mobile apps or through social media. The widening e-commerce attack surface creates new channels for hackers to exploit customer trust.
Common areas that hackers exploit include:
- Unsecured APIs connecting back-end systems. Hackers can exploit vulnerable APIs to gain access to the backend, stealing customer data and manipulating transactions.
- Inconsistent security controls across various channels. Threat actors can attempt to gain access through the desktop storefront or mobile storefront, increasing their chance of entry.
- Social media phishing campaigns. Hackers use social media accounts to perform phishing attacks that impersonate well-known brands to trick customers into handing over their sensitive data.
- Spoofed storefronts. Hackers can fake e-commerce sites that mimic reputable brands by using bots to scrape entire catalogues of inventory. Spoofing makes it difficult for customers to determine fraud schemes from legitimate brands, eroding customer trust.
Large and small businesses are vulnerable to threat actors, especially during the holiday season. E-commerce stores must have adequate online store security to prevent threat actors from gaining entry.
9 ways hackers steal customer data via e-commerce businesses
How do hackers breach company systems? Threat actors use a variety of techniques to hinder business operations.
1. E-skimming
Also known as digital skimming, e-skimming attacks give hackers unauthorized access to customer payment information by injecting malicious code into the e-commerce website.
Attackers target the checkout pages of online stores to gather credit card details, customer names, and billing addresses. This sensitive data is then funnelled to a server controlled by the attacker to launch future cyberattacks.
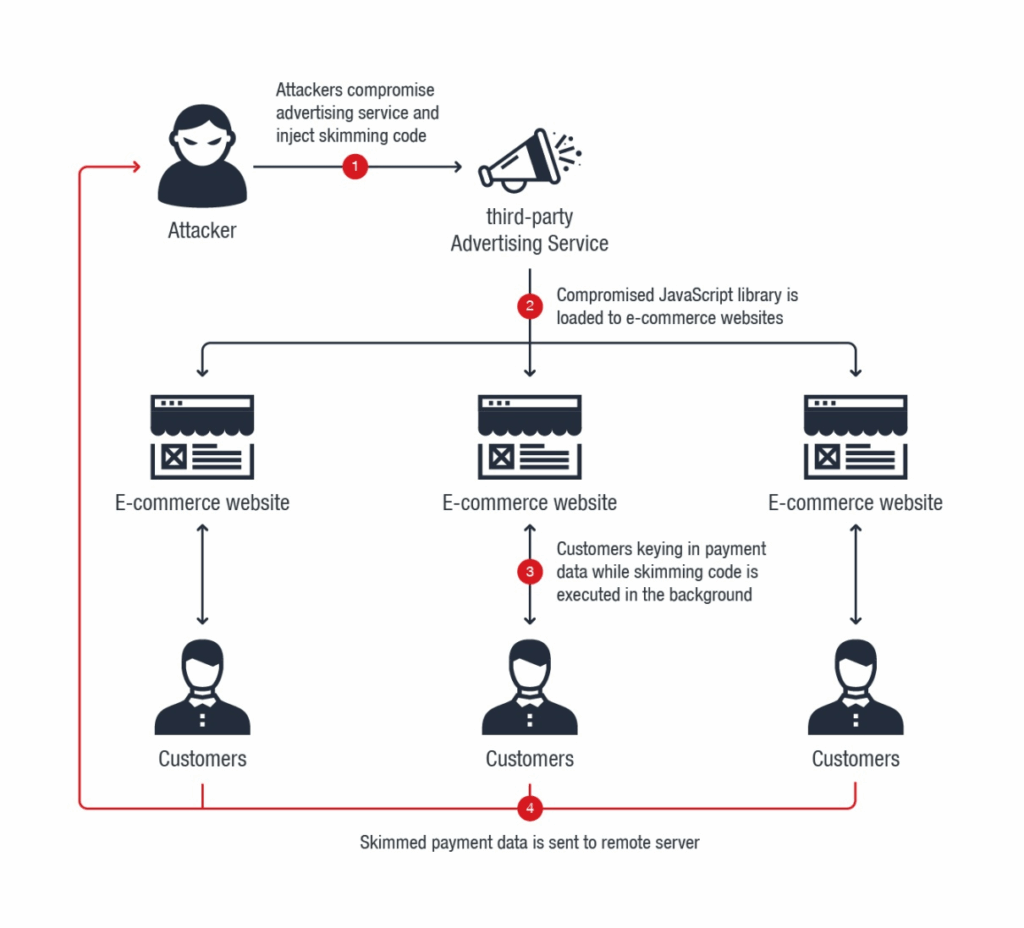
E-skimming attacks utilize compromised third-party APIs and supply chains by hiding the malicious code in longer JavaScript chains that are loaded onto the e-commerce site.
2. Magecart attacks
Magecart attacks are a subset of digital skimming attacks that target online businesses to steal customer payment information. Instead of just one bad actor, Magecart attacks are orchestrated by a team of hackers who leverage third-party vulnerabilities in e-commerce platforms.
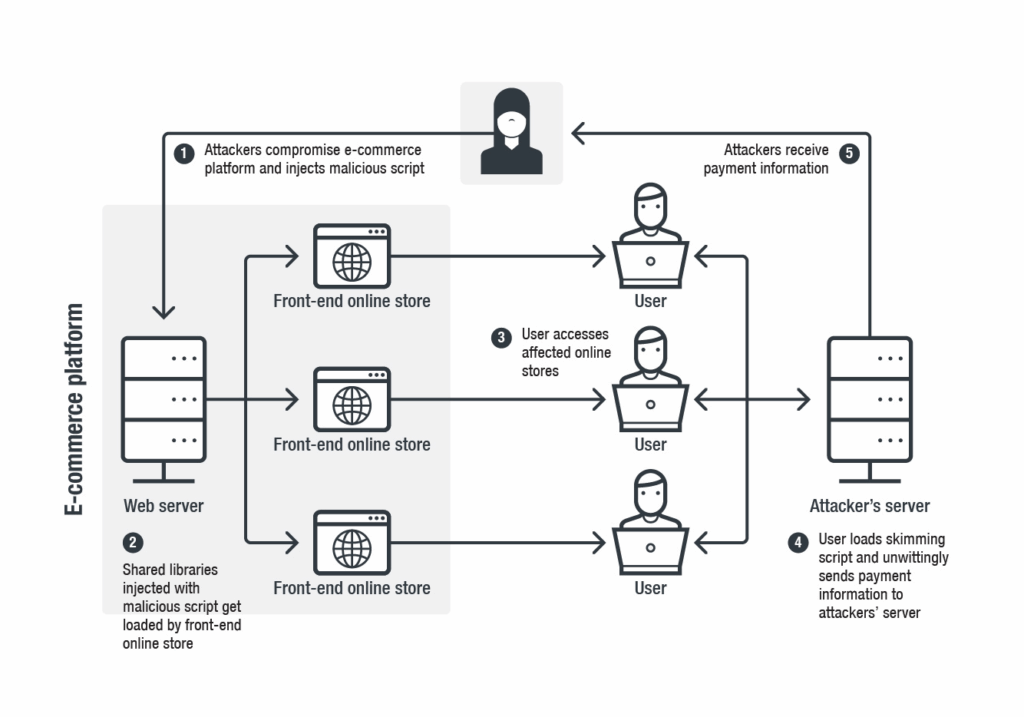
Magecart attacks occur within the browser, making them difficult to detect. The malicious code used is typically hidden within legitimate code on the website, meaning it cannot be detected by web application firewalls (WAFs).
3. Brand impersonation
Cybercriminals use well-known and trusted brands to trick customers into handing over their sensitive information. By creating fake websites and domains, hackers can impersonate trusted brands to harvest sensitive information, sending it to their own server for resale on the dark web.
Hackers often replicate brand logos and website designs, even sending victims phishing emails or SMS messages to harvest information without the victim realizing.
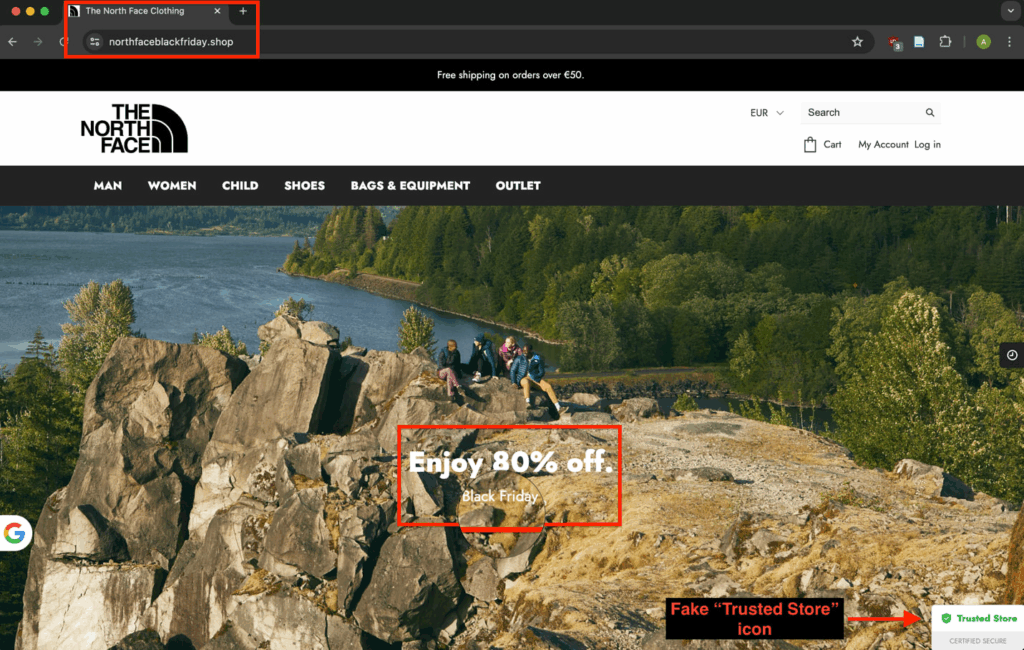
Brand impersonation attacks usually occur during peak holiday shopping periods like Black Friday or Cyber Monday, with fake discounts to create a sense of urgency.
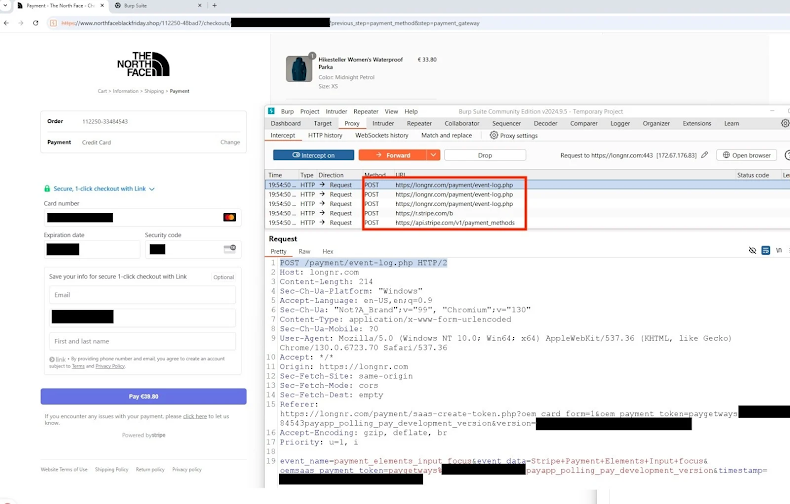
4. Third-party plugin exploitation
Another way for hackers to gain access to personal data is to exploit third-party plugins. Modern e-commerce relies on an interconnected ecosystem of third-party vendors to manage the supply chain. With each new third-party, the risk of abuse increases.
Cybercriminals target misconfigured plugins used by e-commerce sites to manage payment processing, analytics, marketing, or customer support by hijacking access tokens. Hackers can then hijack accounts, modify product listings, or launch fraudulent campaigns.
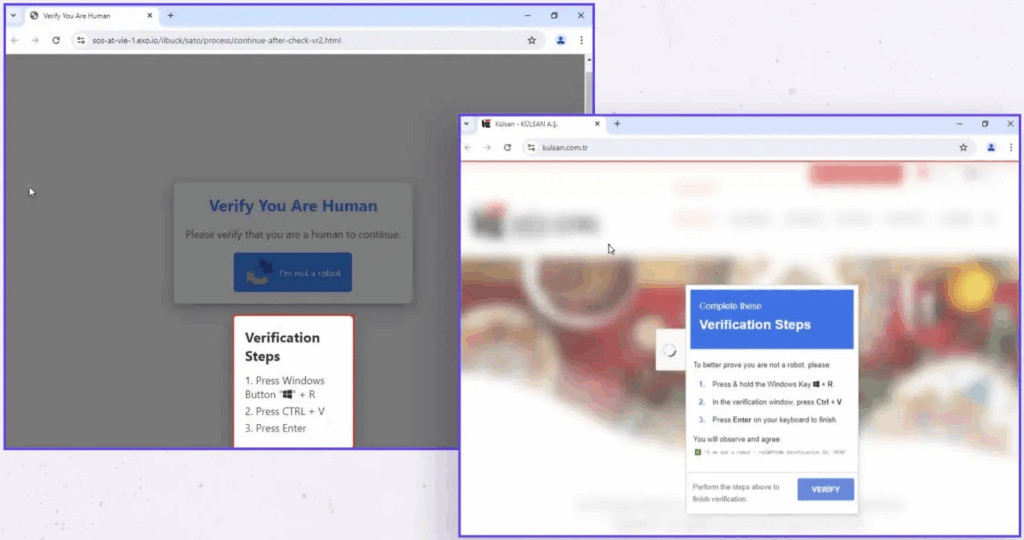
These exploits put customer information and databases at risk—plugin exploits can expose entire customer databases, including encrypted financial information that can be cracked offline.
Plugins often have elevated permissions to perform core functions, meaning they may be overlooked during security audits, giving hackers persistent access.
5. Account takeover
When hackers gain authorized access to an account, they can exploit saved data like credit card details and email addresses for identity theft. Account takeover (ATO) is a real threat—especially when bots are used for large-scale credential theft and brute force attacks.
Techniques used for account takeovers include:
- Credential harvesting: Hackers comb through previous data breaches or purchase stolen data on the dark web to take over accounts. Since many users reuse passwords across different sites, it‘s only a matter of time before an account is breached.
- Credential stuffing or brute force attacks: Threat actors use bots to test stolen credentials across multiple platforms. Once they gain access, they may continue trying more account takeovers to get to high-value targets like online banking.
- Exploiting weak authentication: Accounts that don‘t have multifactor authentication (MFA) are easier to exploit. Attackers gain access by exploiting weak security questions or compromising sites that don’t enforce strong password policies.
- Session hijacking: Attackers use malware or man-in-the-middle (MiTM) attacks to intercept authentication tokens and login traffic to compromise the account.
Account takeovers pose a threat to customer trust, while also draining funds from the business. Cybercriminals can resell vouchers or gift cards purchased online with stolen funds or resell customer data on the dark web. Recent reports found that companies stand to lose $12 – $44 million in annual revenue from customer churn.
6. API abuse
Hackers abuse APIs by exploiting weak authentication and insecure endpoints to gain unauthorized access to customer accounts.
E-commerce sites are known for using APIs to manage payment platforms, shipping procedures, and inventory. However, when APIs aren‘t properly configured, they can provide a way in for hackers.
Credential stuffing attacks on APIs can be used to hijack accounts, scrape large volumes of sensitive information, and bypass payment systems. In some cases, hackers perform Distributed Denial of Service (DDoS attacks) to temporarily stop processes and continue the attack undetected.
7. Cross-site scripting (XSS) attacks
To damage the front-end of a website, threat actors use cross-site scripting (XSS) attacks to compromise accounts and distribute malware.
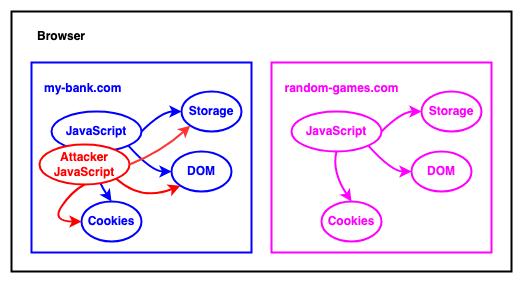
Web browsers use the principle of same-origin policy—a security feature that ensures website data is kept separate. In a successful XSS attack, the attacker can subvert the same-origin policy by tricking the target site into executing malicious code. Hackers inject malicious code via JavaScript to steal cookies, hijack sessions, redirect users, or perform unauthorized actions.
E-commerce sites are a prime target for XSS attacks because of high customer trust in online shopping and the high-value customer data they contain.
8. Malicious SQL injections
To steal data or even take full control of backend databases, hackers use SQL injections. These kinds of attacks are easy to exploit and can directly expose sensitive data stored in a website’s database. For this reason, most data breaches are the result of SQL injections.
Classic SQL injection (sometimes called band injection) adds parameters to the user‘s input to reveal the username and password when logging into a website. This code injection bypasses login authentication, giving the hacker access.
Here’s a comparison table of the main types of SQL injections:
| Type of SQL Injection | How It Works | Example Technique | Impact |
|---|---|---|---|
| Classic (In-band) | Attacker uses the same channel to inject and receive results. | OR '1'='1' in a login field. | Bypass authentication, access data directly. |
| Union-based | Uses the UNION operator to combine malicious queries with legitimate ones. | UNION SELECT username, password FROM users | Extracts data from other tables in the database. |
| Error-based | Exploits database error messages to reveal structure. | Forcing query errors to expose table/column names. | Reveals schema details, aiding further attacks. |
| Blind (Boolean-based) | Infers data by observing true/false responses. | AND 1=1 (page loads normally) vs. AND 1=2 (page changes). | Slowly extracts data without visible errors. |
| Blind (Time-based) | Uses delays to infer conditions. | IF(condition, SLEEP(5), 0) | Confirms database details by measuring response time. |
| Out-of-band | Uses external channels (DNS/HTTP requests) triggered by the database. | Database sends data via DNS lookup. | Useful when in-band and blind methods fail. |
9. Ransomware attacks
Ransomware attacks can cripple business operations, leading to significant financial losses, downtime, and potential loss of customer data. In some cases, paying the ransom does not guarantee the safe return of the data.
Cybercriminals are well aware that many e-commerce sites have security issues and lack proper security solutions. When faced with a ransomware attack, retailers are more likely to pay the ransom than risk further downtime.
According to recent reports, ransomware attacks in the retail sector globally have spiked by 58% in Q2 of 2025. It‘s not just small businesses, either—large retailers like Marks and Spencers (M&S) and Harrods in the UK faced a major ransomware attack earlier this year, causing significant operational disruption and a loss in consumer trust.
Defensive security measures to implement
To combat evolving cyber threats, e-commerce sites must implement security controls and procedures.
Here are some security measures to keep in mind when launching your e-commerce site.
1. Adhere to regulation standards
The Payment Card Industry Data Security Standard (PCI DSS) was developed in 2004 to enhance card payment account security. PCI DSS provides merchants with a structured framework that includes 12 core requirements and encourages integrating security measures to stop financial fraud.
The latest version, v4.0.1, was launched on March 31, 2025, with a stronger emphasis on multi-factor authentication and phishing-resistant security.
Some of the updates include:
- The use of cryptographic hashes to render Primary Account Numbers (PAN) unreadable.
- Required multi-factor authentication for all (non-administrative) access.
- Clarifying requirements for managing payment page scripts.
Specifically within Europe, General Data Protection Regulation (GDPR) applies to all aspects of data protection in Europe and nationally.
For e-commerce, GDPR requirements are essential for managing sensitive customer information such as name, address, payment details, and order history. Negligently handling this data can result in a violation, including fines.
2. Implement secure payment gateways
Payment gateway security ensures that vendors manage customer transactions in a safe and secure manner.
Secure payment gateways:
- Encrypt customer data, including payment information.
- Connects the vendor‘s payment processor securely to the customer-facing checkout.
- Forwards the transaction securely to the vendor‘s bank, verifying transaction details.
- Minimize and reduce fraudulent transactions, preventing e-commerce fraud.
3. Run antivirus protection
Running a comprehensive antivirus software is essential to stopping cybersecurity threats before they escalate.
Online stores process large volumes of personal and financial information, making them prime targets for malware, ransomware, and phishing attacks. Antivirus solutions provide real‑time scanning, threat detection, and system monitoring to block malicious software before cybercriminals make off with valuable customer data.
4. Invest in penetration testing
Penetration testing or ethical hacking helps e-commerce brands identify, test, and highlight vulnerabilities in their e-commerce systems.
Pentesters can evaluate how effective your current cybersecurity protocols are and if they can be breached.
5. Monitor suspicious activity
Monitoring your entire e-commerce IT ecosystem end-to-end ensures that malicious flags are seen and dealt with.
Real-time monitoring of your external attack surface can identify vulnerable APIs, detect shadow assets, and help your team prioritize cybersecurity efforts in a risk-driven approach.
6. Verify your website with SSL certificates
SSL certificates verify the website owner and encrypt traffic to prevent abuse.
- Provides web browser encryption: SSL/TLS encryption uses a mix of public-private keys and symmetric cryptography to protect the data exchanged. SSL/TLS uses message authentication codes (MACs) to ensure the data isn’t altered in transit.
- Ensures HTTPS: The most secure way of connecting to a website, HTTPS ensures that all web traffic is encrypted. When active, users can recognize it by the padlock icon in the URL bar.
- Authenticates browser sessions: SSL certificates verify that a user is connecting to the correct server (owned by the e-commerce site and not a hacker). This protection prevents domain spoofing.
7. Develop an incident response plan
Planning for what to do when a breach occurs is important for all businesses. Business owners should ensure that their incident response plan includes learnings from past cyber attacks, a zero-trust policy for all administrative controls, and a comprehensive data backup plan.
FAQs
What can e-commerce sites do to boost website security?
E-commerce businesses can implement a multi-layered security strategy that encompasses the entire attack surface. Consider the entire attack surface, including vulnerable APIs and endpoints, security controls for third-party service providers, cloud infrastructure, and website storefronts. Addressing potential security risks before they occur is crucial to preventing data breaches.
Why are strong passwords important for customers and employees?
Strong passwords including letters, numbers, and symbols ensure that passwords can‘t be easily guessed by attackers. Brute force attacks, when multiple combinations are tried, often result in exposed user accounts if passwords are too short or simple. See our article for password best practices.
How can e-commerce businesses prevent account takeovers?
To prevent account takeovers, e-commerce businesses can implement secure access controls, like multi-factor authentication (MFA) and real-time monitoring of account activity to flag suspicious activity. Prevention is key to stopping hackers from gaining unauthorized access.
How can businesses prevent security breaches during the holiday season?
During the holiday season, e-commerce sites experience a spike in traffic and transactions, making them prime targets for cyberattacks. Utilize PCI DSS-compliant payment gateways that use encryption for all transactions, monitor for Magecart-style skimming attacks on checkout pages, and use real-time monitoring to spot anomalies in login attempts.
What are some best practices for customer data protection?
To protect customer data, e-commerce sites can implement encryption on all customer data in transit and at rest using SSL certificates, preventing hacker interception. Tokenization can replace sensitive cardholder data with unique tokens, reducing potential exposure. Additionally, apply role-based access controls, allowing only authorized staff to view sensitive data.
Wrapping up
E-commerce cybersecurity is the foundation for safe shopping in our modern world. Investing in strong security measures can help e-commerce brands stay ahead of evolving attack methods, while lowering risk and protecting customers.
With the right protection, e-commerce brands can protect their revenue and reputation, building trust across the digital landscape.

