The New Rules of Computer Virus Prevention

Table of contents
For years, you might have followed the same old virus protection formula. Perhaps you installed the antivirus software, configured your firewalls, and then applied patches on schedule. And for a while, that might have been enough.
But hackers aren’t sitting nicely at your perimeter. They’re now fighting from the outside-in, using any weapons at their disposal, such as stolen credentials, phishing kits, or exposed cloud assets.
No amount of antivirus programs can fix the root issue: external vulnerabilities. And you have to manage these gaps before hackers exploit them. Otherwise, it’s only a matter of time. Let’s explore how to secure your external attack surface (and in turn, your peace of mind).
How computer viruses spread today
Back in the day, computer viruses moved through infected floppy disks and email attachments. A single careless download or shared file could infect an entire network.
Over time, antivirus programs and stricter security settings curbed these obvious entry points. But of course, cybercriminals didn’t disappear overnight. They simply adapted.
Nowadays, malware rarely arrives through a single “infected file.” It travels through a complex digital infrastructure that’s riddled with weak points. And every enterprise is exposed to some extent.
For example:
- Phishing emails lead employees to download software
- A misconfigured cloud bucket can expose sensitive information
- Leaked credentials can unlock an entire company’s computer system
- A compromised third-party supplier could transmit malware attacks
A modern infection chain starts with attackers scanning for weak points, and then using them to gain initial access. From there, deploying malware is simply a matter of opportunity. And unlike older methods, attackers can use automated scripts to make it all happen in record time. Here’s a diagram of what this can look like.

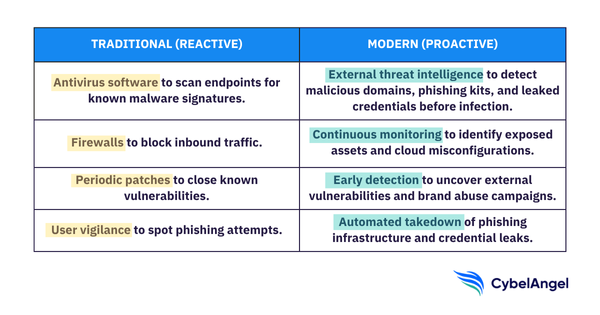
Why traditional prevention methods fall short
Of course, traditional defenses still matter. But they were just built for a different era. Here are some examples:
- Antivirus software: Scans for known malware signatures, but struggles to adapt to polymorphic malware
- Firewalls: Block suspicious traffic, but can’t stop credential-stuffing campaigns with valid logins
- Patching: Closes exploitable code flaws, but can’t address cloned corporate domains or exposed third-party apps
All these cybersecurity measures are important, and they protect what’s on the inside. But they can’t address invisible cyber threats working beyond the perimeter.
Traditional security focuses on responding once a threat is already inside the network. Proactive defense shifts the timeline. It hunts for the exposures that hackers use before they strike. The table below compares traditional and modern malware prevention methods in more detail.
The external vectors driving malware infections
Every major malware outbreak starts with a point of entry. And increasingly, that entry sits outside the company’s direct control.
- Leaked credentials are one of the most common triggers. Usernames and passwords stolen through infostealer malware or past breaches often resurface on dark web marketplaces, where they’re sold in bulk to other threat actors.
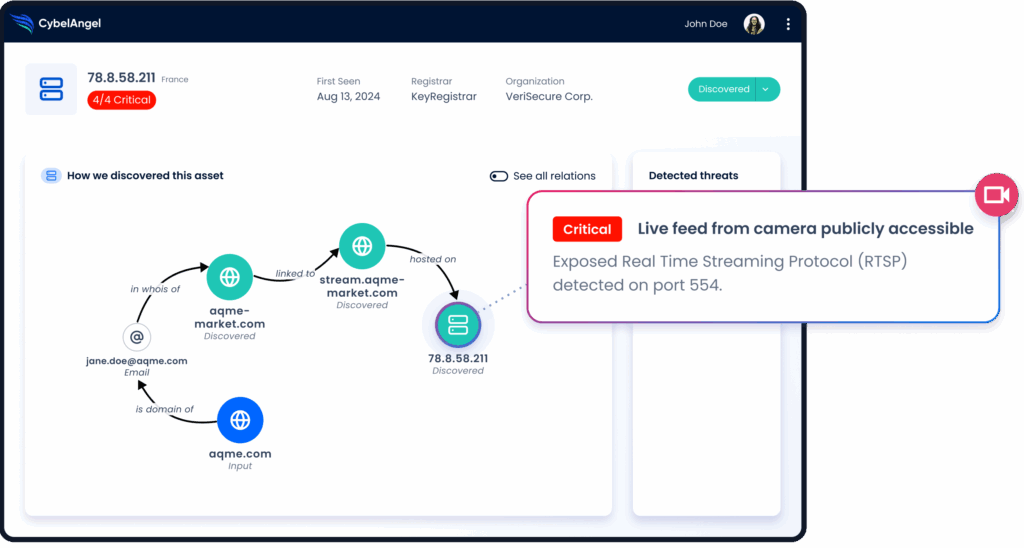
- Exposed assets provide yet another route. A forgotten subdomain, an unpatched web app, or a misconfigured storage bucket can all serve as drop points for malicious code.
- Compromised third-party apps and APIs extend the attack surface even further. A malicious file synced through a collaboration tool or a compromised vendor can deliver different types of malware.
- Phishing infrastructure is another major enabler. Attackers register lookalike domains (subtle misspellings or character swaps of legitimate corporate URL) and use them to mimic login portals or distribute infected attachments, such as .exe files. The deception works because the infrastructure itself looks authentic. Some phishing kits now even include full control panels for tracking victim credentials and generating fresh fake pages on demand.
For example, a new phishing-as-a-service (PhaaS) tool called “Whisper 2FA” is being used to target Microsoft 365 users. It takes both credentials and MFA tokens, and it mimics other brands to slip under the radar. Its phishing emails are designed to resemble urgent communication from companies such as DocuSign and Adobe.
Shifting to a proactive, outside-in defense strategy
Today, cybersecurity prevention means seeing what attackers see first. That’s the role of external threat intelligence.
It’s all about the continuous discovery and analysis of internet-facing assets, leaked data, and malicious infrastructure linked to your organization. And it extends visibility beyond the firewall, into the open web, the dark web, and every forgotten corner where exposures can appear.
When you have an outside-in view, you can:
- Detect and remediate vulnerable services (before they’re exploited)
- Identify and take down fake domains and phishing kits (before they start harvesting credentials)
- Trace leaked passwords and malware infected files (before they turn into long term infection chains)
CybelAngel’s approach builds on this principle. Each discovery triggers real-time alerts and guided remediation, allowing security teams to remove the threat long before malware ever touches an endpoint.
Checklist: A tactical prevention framework for security teams
You don’t need to start from scratch. But you do need to broaden your perspective and increase the scope of what you’re looking at. Here’s a framework to get you started.
- Identify: Map every part of your external digital footprint. This includes domains, cloud environments, code repositories, and SaaS instances. In short, anything publicly accessible should be catalogued and monitored.
- Monitor: Keep watching out for leaked credentials, phishing kits, infected files, and fake domains impersonating your brand. These are the first signs that malware operators are targeting your organization.
- Prioritize: Not every alert deserves equal attention. Rank your company’s exposures based on their exploitability and potential business impact. For example, a misconfigured VPN server demands faster action than a parked subdomain.
- Remediate: Make sure you act fast to contain exposures. Coordinate domain takedowns, close open ports, revoke stolen credentials, and patch vulnerable services before they’re weaponized.
- Measure: Track your team’s progress over time. Fewer exposed assets, fewer leaks, and faster remediation cycles are the most reliable indicators of reduced attack surface… and peace of mind in the long run.
Of course, anti-malware software and endpoint controls still help with preventing malware attacks. But external attack surface management will make them stronger by guiding them with real-life insights about how and where the attacks begin.
Case study: Preventing a ransomware outbreak through external visibility
Imagine this: A multinational manufacturing group with over 30,000 employees receives an urgent alert from its external threat intelligence platform.
A set of valid corporate VPN credentials (complete with multifactor recovery details) has surfaced on a dark web forum. The credentials appear to belong to a senior engineer.
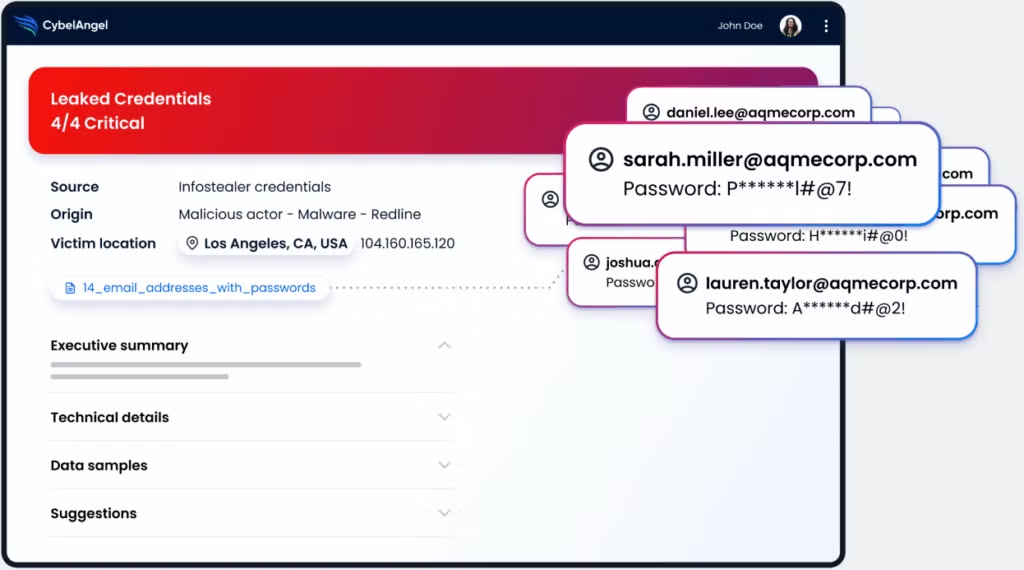
Within minutes, the security operations team verifies the leak and forces an enterprise-wide credential reset.
The exposed VPN account is disabled, and corresponding sessions are terminated. Cross-checks in their SIEM reveal that no suspicious connections have been made yet. The attack chain has been broken before it could begin.
Further analysis links the credentials to an info-stealer infection on the engineer’s personal laptop, likely triggered by a malicious email attachment opened weeks earlier.
Without the external alert, those stolen details could have granted direct remote access into the company’s network. It would have been a perfect launchpad for ransomware deployment.
In this case, virus prevention didn’t hinge on antivirus alerts or endpoint scans. It succeeded because visibility extended beyond the firewall. The team saw the exposure before attackers could weaponize it.
CybelAngel’s external threat intelligence enables exactly this kind of foresight. It can detect leaked credentials, rogue infrastructure, and infected files tied to your organization so security teams can take action while there’s still time to prevent an incident.
The human factor still matters
Unfortunately, even the best threat intelligence can’t fully protect against your biggest vulnerability… People. 95% of data breaches happen due to human error.
One distracted click or rushed login can still open the door to malware. Especially when attackers impersonate familiar brands or mimic trusted file-sharing tools. Phishing campaigns now rely less on poor spelling and more on psychological pressure, such as urgency, authority, or curiosity.
That’s why technical controls and human awareness must evolve together, such as with:
- Continuous employee training: Because around 2 million businesses still haven’t arranged cybersecurity training for their teams, despite the risks
- Realistic phishing simulations: Because most adults can’t differentiate between authentic and AI phishing emails
- Clear reporting channels: Because without the right procedures, live threats may slip past unnoticed, and undocumented
These proactive threat prevention strategies keep teams accountable and on the same page. And when paired with the right external threat intelligence tools, they turn people from the weakest link into an active part of virus prevention.
FAQs: Modern malware and virus prevention
Let’s break down some common FAQs on enterprise virus protection.
What are the most common initial access vectors for malware today?
Phishing emails, leaked credentials, and exposed remote services such as RDP or VPNs remain the leading types of virus infection paths. Many campaigns begin when employees download files from unverified sources or interact with malicious pop-up windows disguised as software updates.
Can antivirus software still prevent computer viruses?
Yes, but it works reactively. Antivirus and antispyware programs are still essential for detecting infected files and blocking malicious code on endpoints, but they can’t see what’s happening beyond the network. Pairing these tools with external threat intelligence ensures early warning before the payload hits.
How do computer viruses work?
Viruses embed malicious code into legitimate files or programs. Once executed, they replicate across the operating system, spreading through shared folders, external storage devices, or even the boot sector of hard drives. Some variants, like file infectors, modify existing applications, while others exploit vulnerabilities to gain persistence.
What’s the difference between a virus, worm, and trojan horse?
These are all different types of malware. Here’s how they differ.
- Virus: Attaches to clean files and spreads when those files are opened or shared.
- Worm: Self-replicates automatically, often moving across networks without user action.
- Trojan horse: Disguised as legitimate software or app downloads, used to steal data or install additional malware.
What is proactive virus prevention?
Proactive virus prevention means stopping infections before they reach endpoints. That includes identifying fake domains, leaked credentials, and exposed assets early (before they lead to a data breach).
It also means enforcing strong internet security settings, such as:
- Running Microsoft Windows updates or Apple software updates promptly
- Restricting risky app store downloads
- Reviewing privacy settings regularly
With the right data breach prevention measures in place, teams can confidently stay virus free in the long run.
Conclusion
Virus prevention has outgrown its old definition. Antivirus software and firewalls still matter, but they only see half the picture. Real protection starts earlier. It happens by uncovering the exposures, fake domains, and leaked credentials that make infections possible in the first place.
Security leaders now need prevention that looks outward as well as inward. With CybelAngel’s external threat intelligence, you can detect and remove the delivery mechanisms of malware before they ever reach your network.

