
Frightening Top 10 Halloween Passwords
Are you prepared for the horrors of stolen credentials?
The topic of password security is the zombie in cybersecurity discussions — should be dead, but isn’t. And yet, despite frequently hitting the news detailing the horrors of having our passwords compromised, we tend to use the same basic passwords or resurrect our old ones from the grave, both of which are hair-raising when it comes to security. How bad is this problem? The supply of passwords is so great on the Dark Web, it is suppressing the price of a remote password. For Halloween 2020, the CybelAngel Team delved into our database and built a list of the top 10 most used passwords related to pumpkins, ghosts, and vampires. Given the results, it is okay to be scared. 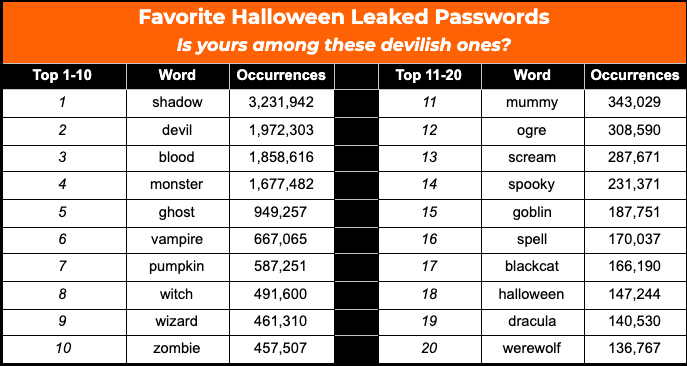 Investigative Criteria: 50 Halloween-theme strings looked at indifferently (e.g.: “blood” also matches “bloody”, “bloodshot”, “666blood”), based on clear text passwords of 9,901,693,500 credentials as of September 2020.
Investigative Criteria: 50 Halloween-theme strings looked at indifferently (e.g.: “blood” also matches “bloody”, “bloodshot”, “666blood”), based on clear text passwords of 9,901,693,500 credentials as of September 2020.
Why are passwords so coveted?
Once a ghoulish attacker gets their hands on the password of a user and combines it with other credentials (e.g.: name, email, passport, birth date), it becomes eerily easy to execute malicious activity — especially when passwords and credentials are dumped on the Web…at little to no cost. A hacked account is one of the springboards for cyber attacks, such as: credential stuffing, spear phishing, identity theft, and other fraud schemes. If you think your old password from an obscure website is harmless, think twice. It may return to haunt you. Knowing this information is an asset for phishing attacks and other dark social engineering schemes. A good hacker knows that you are less suspicious of a scam when it contains a contextual element about you, no matter how recent or ancient. This makes your old password a key ingredient for a spear phishing email like the following one. 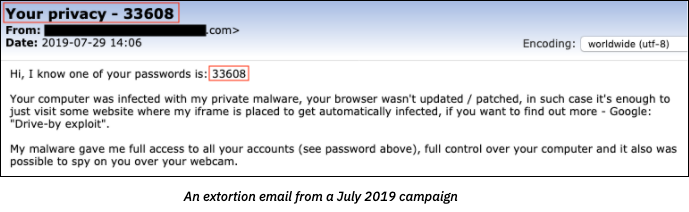 The SEC’s Office of Compliance Inspections and Examinations (OCIE) issued an alert in September 2020, which focused on a hack known as “credential stuffing,” among other frightful cyber criminal tactics. These malicious attacks start with bad actors trolling the Dark Web for stolen or leaked credentials, which they use to access client funds or to take over an employee account. Once an account is taken over, the hacker can wreak other mischievous to macabre exploits. These attacks can include sending emails directing employees to wire money to the hacker’s account or infecting computers with command-and-control (C2) malware to siphon valuable data from the business and compromise the entire enterprise network.
The SEC’s Office of Compliance Inspections and Examinations (OCIE) issued an alert in September 2020, which focused on a hack known as “credential stuffing,” among other frightful cyber criminal tactics. These malicious attacks start with bad actors trolling the Dark Web for stolen or leaked credentials, which they use to access client funds or to take over an employee account. Once an account is taken over, the hacker can wreak other mischievous to macabre exploits. These attacks can include sending emails directing employees to wire money to the hacker’s account or infecting computers with command-and-control (C2) malware to siphon valuable data from the business and compromise the entire enterprise network.
How to create (and easily remember) a good password?
Passwords are the cornerstone to a solid cybersecurity strategy. Creating poor passwords and failing to develop and enforce the accompanying policies can be a tombstone for an organization. Beware of password reuse — using a single password for several accounts, or adding only a slight modification such as appending “1.” While there’s (almost) nothing to be ashamed of, given the number of accounts all of us have created for email services, online merchants, miscellaneous forums, streaming services, social media, and on, and on, the consequences can be scary. Everything from stealing your identity to gaining access to your company’s financials. A one-to-one relationship between a password and an account provides better protection than reused passwords. And while password managers can aid fortify your cybersecurity, these are not the only solution. Here are some tips to create strong passwords that are easy to remember – plus it’s brain exercise! “At least a capital letter, a number, a special character, minimum 10 character-long.” What kind of password does Halloween inspire for you?
- cKwdl3QpZ8bjT?P – Sure, it is a good password, but good luck remembering it.
- May the 4th be with you! – This one has the characteristics of a secure password.
Other bewitching ideas to inspire your passwords…
- Favorite quote → Double2X_toil&trouble
- Your morning commute → ItsA40-minutebroomride
- A line from a song you like → Com3onB@by-Don’tFearRe3@per
- A contextual element from the website you’re registered on → F0rWhomtheB3llTolls!
CybelAngel can protect your enterprise
Last year, the CybelAngel Analyst Team detected 1.2 billion exposed credentials — half of these with an unencrypted password. CybelAngel can protect your company from the dangers of leaked credentials by:
- Monitoring credential leaks in real-time. Don’t wait for cyber attackers to make the first move. Uncover exposed credentials within days and update passwords before your systems are compromised.
- Assessing and mitigating the risk of leaked credentials to prevent VIP impersonation and avoid further account compromise.
Don’t be spooked by compromised credentials and stolen passwords. CybelAngel can provide you a dashboard that indicates where your company’s data is leaking, and how you rank compared to other organizations in your industry—without any obligation. Click here to get your company’s complimentary Data Leak Dashboard. If you suspect a data leak, contact us. Because data leaks are inevitable, but damage is optional.