
Negligence Drives 90% of Data Breaches
Brands take years to build and milliseconds to disintegrate
Enterprises spend years building their brand image and reputation with their target audience and business partners. With threat actors hyper-focused on enterprises, it has never been more critical to protect your critical data both inside and outside your company’s walls…and your brand. Two examples of crippling data breach damage to consumer brands are Target and, more recently, Capital One.
- Target’s data breach exposed nearly 110 million customers’ information. This caused the company’s sales to fall 4% with profits crashing almost 50% the following quarter. Then, Target’s CEO was subsequently dismissed.
- In the recent case of Capital One, 103 million users were exposed after an Amazon employee stole customer records from Capital One, including: social security numbers, credit card information, and other personally identifiable information. Recent estimates place Capital One losses at nearly $300 million.
Both of these examples provide a stark reminder of just how fiscally damaging a data breach can be. 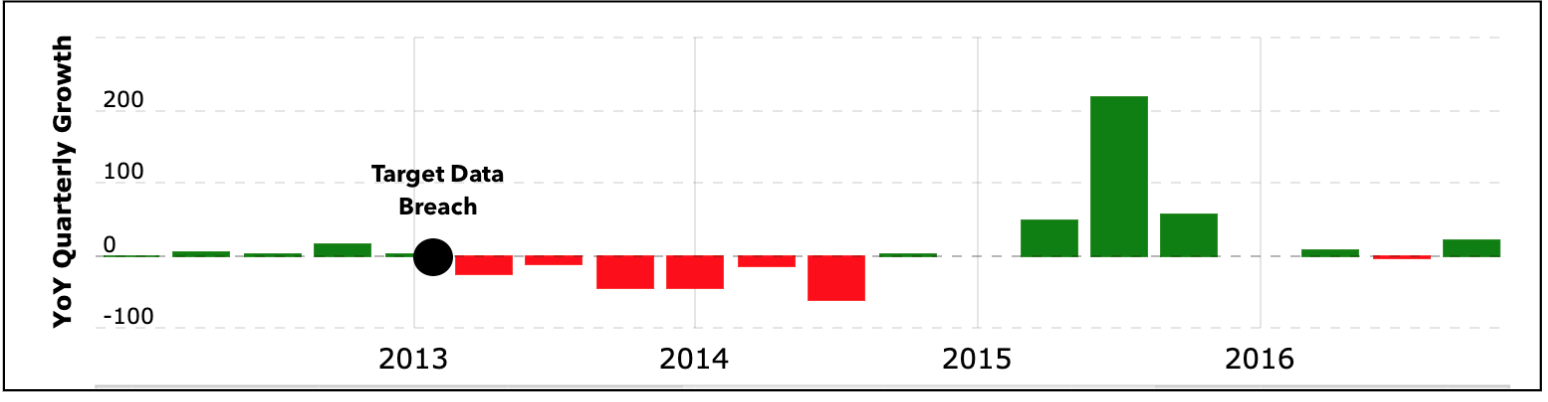
Target’s year over year growth, showing a tremendous decline due to their 2013 data breach
A consumer data breach awareness study found more than 83% of consumers are aware of their respective retailer’s recent data security breaches. Furthermore, 59% of respondents said that a “single data breach would negatively impact their likelihood of buying brands from a consumer company.” This awareness demonstrates the crucial need for a tight defense against employee negligence vulnerabilities.
Employee mistakes result in data leaks
The business landscape is more complex and evermore dependent on digital data, which underscores the need to ensure your company has a robust and well communicated cybersecurity program. CybelAngel finds that more than 90% of data breaches are due to negligence that might have been prevented with cybersecurity training, processes, procedures, and tools. Examples of these incidents include:
- An overzealous or new employee foregoing security procedures for simplicity or time saving
- An IT employee involved in shadow IT activities
- A third-party vendor leaving a server open with sensitive documents exposed
The possibilities are endless, as are the risks.
How to prevent employee negligent data leaks
With only 10% of leaks being perpetrated by malicious actors, educating your employees should be paramount. Avoiding 90% of negligent data leaks and being prepared when a leak occurs is a key business practice. Given leaks are inevitable, there will come a time when an employee makes a mistake configuring a server or leaving a computer backup server unprotected after moving sensitive documents to their personal system will occur. The key is to minimize these scenarios and to create thoughtful safeguards and training to prevent such negligence. As threat actors continue to target weak links in global industries and inevitably your company —vigilance, preparation, and the ability to adapt are critical data security measures.
Stop a data leak becoming a major breach
Forward-thinking enterprises know that a 360° Cybersecurity Program includes digital risk protection to protect critical assets and brand reputation. These businesses know their program must include constant and comprehensive monitoring for data leaks — within and beyond their corporate perimeter to stop data breaches. Our clients know the CybelAngel digital risk protection platform fulfills these expectations by expertly executing on three key success factors.
- Comprehensive scanning outside of your enterprise perimeter is integral to detecting data leaks. This scanning must include: surface web, deep & dark web, domain name servers, cloud applications, connected storage, and open databases and datasets.
- Speed to detect is critical. Finding confidential and/or sensitive data before it is stolen and exploited is key to a strong digital risk solution.
- Timely alerting is key. Comprehensive scanning means having to sort, filter, and identify the most critical alerts. Machine learning algorithms funnel the hundreds of thousands of data sources, thousands of files, and hundreds of threats to arrive a manageable number.These threats are prioritized by cyber experts, who eliminate false positives. Then, the remaining potential data leaks are prioritized by data leaks most likely to become major breaches.
Find out what and where your data is leaking with CybelAngel’s no obligation data leak exposure dashboard. Learn the # of exposed documents, open servers, and leaked employee credentials, as well as where this data is leaking.