The Hidden Cost of Tool Sprawl [Part II]

Table of contents
For years, security teams have chased visibility by adding more tools, like SIEMs, scanners, dashboards, and alerts. But many now find themselves drowning in noise. The average enterprise stack has ballooned into a maze of overlapping apps and disconnected metrics, leaving CISOs and analysts struggling to pinpoint what truly matters.
Recent reports from IBM and Forbes show the same pattern across industries. Namely, that as tool counts rise, efficiency drops. Teams lose precious time toggling between dashboards, reconciling duplicate alerts, and chasing false positives across siloed systems. The result is confusion, not protection. That’s why tool consolidation is needed to regain control, reduce blind spots, and streamline operations before the next incident hits.
Ps. missed part one of our series? Read it here, and download our ebook for a more indepth review.
The rise (and risk) of security tool sprawl
Nowadays, every new threat seems to demand a new tool, such as…
- Endpoint detection
- Vulnerability scanning
- Cloud posture management
- Dark web monitoring
Each of these functions promise sharper visibility and faster detection. But over time, these well-intentioned additions began to pile up. What started as a handful of best-in-class solutions has evolved into an unmanageable ecosystem of dashboards, alerts, and logins that no one team fully controls.
This phenomenon is known as tool sprawl.
Tool sprawl is the unchecked accumulation of specialized, siloed technologies across IT and security environments. Each point solution may work well on its own, but together they create friction. Data sits in isolated systems, workflows overlap, and critical context gets lost in translation between platforms.
The more tools you add, the less cohesive the picture becomes. And the consequences can be severe.
- Teams battle alert fatigue, with identical issues flagged by multiple monitoring tools
- Metrics vary across dashboards, leaving analysts unsure which source to trust
- DevOps engineers chase the same incident from three different views, wasting hours reconciling discrepancies before they can even begin remediation
It’s ironic. Because while many companies have tried to gain visibility, they’ve actually obscured it. And here’s the cost.
Counting the cost of silos and fragmentation
According to IBM, a business relies on an average of 83 different security solutions from 29 vendors. In some cases, companies may spend millions each year to maintain overlapping security tools; sometimes even paying twice for similar functionality. And this complexity can cost more than 5% of their annual revenue.
Beyond finances, the operational cost is also high. Compared to businesses that rely on a single platform, IBM found that fragmented security tech stacks take…
- 72 days longer to identify a security incident
- 84 days longer to contain it
When data is scattered across multiple systems, teams waste precious minutes (sometimes hours) jumping between consoles to verify alerts. Every extra dashboard adds seconds to a workflow, and those seconds compound when you’re managing hundreds of incidents per month.
These silos also create blind spots.
For example, critical data gets trapped inside specific apps or toolsets, meaning teams can’t see the full chain of events leading to a breach or outage. Root cause analysis takes longer, downtime stretches out, and decision-making often misses the bigger picture.
Without a unified view, even experienced analysts are working with one eye closed. IBM refers to this as “the illusion of ‘more solutions, more security’”.
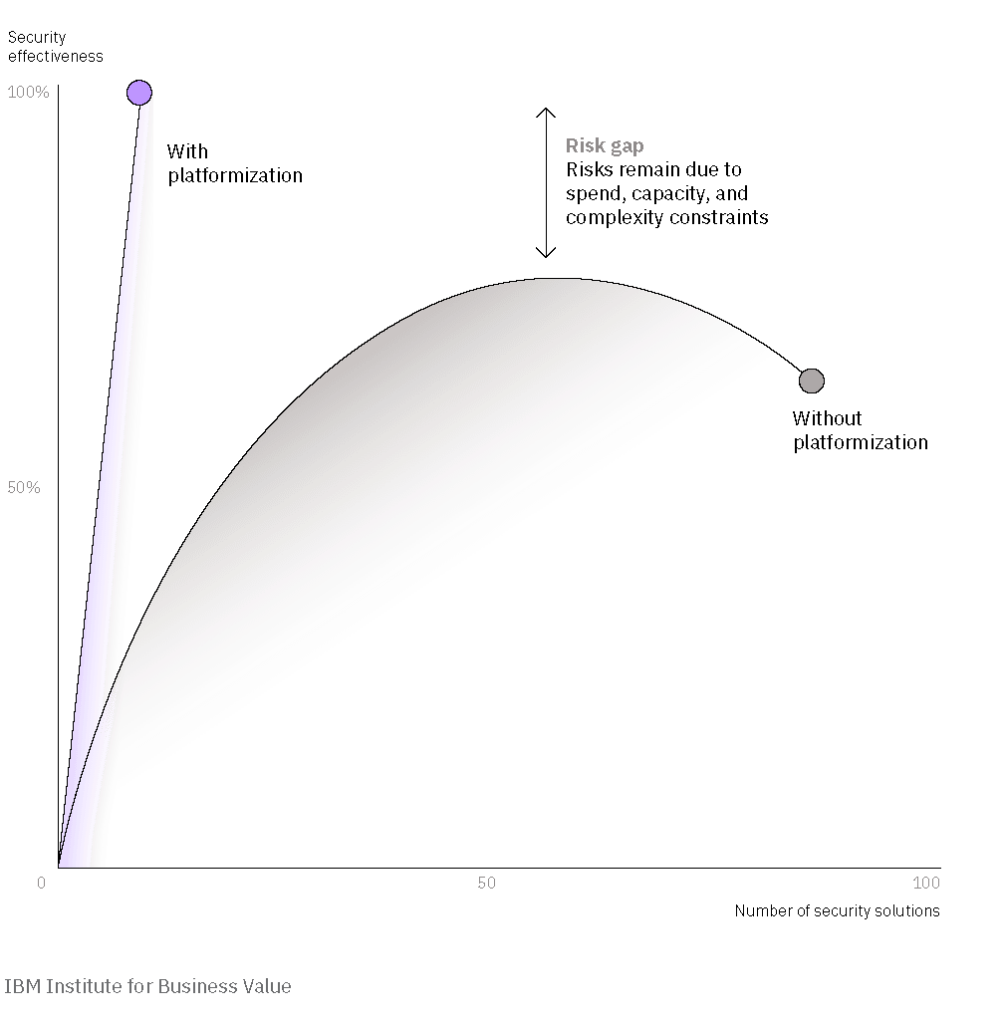
The benefits of tool consolidation for security and IT teams
When teams rely on a patchwork of monitoring tools, every task takes longer than it should. But tool consolidation reverses that trend.
By bringing detection, investigation, and troubleshooting into one place, teams can reclaim hours lost to manual correlation work. The result is leaner operations and noticeably lower MTTR (mean time to repair).
Security platform consolidation also strengthens observability. Instead of piecing together metrics from isolated systems, teams gain a single source of truth with consistent data and shared workflows.
This reduces false positives, tightens prioritisation, and makes incident timelines easier to reconstruct. When everyone sees the same events in the same place, collaboration stops being a bottleneck and becomes a natural part of the response process.
There’s a people benefit, too.
Fewer tools mean simpler onboarding, less training overhead, and more confident day-to-day operation. Junior analysts ramp faster. Senior engineers spend less time fighting with interfaces and more time solving root-cause issues. End-users feel the difference as well, with fewer performance issues, faster remediation, and fewer conflicting alerts from different platforms.
In short, consolidation can improve the entire operational rhythm of a security organisation, with IBM reporting that people with integrated security platforms are 70% less likely to experience workload increases due to fragmentation.
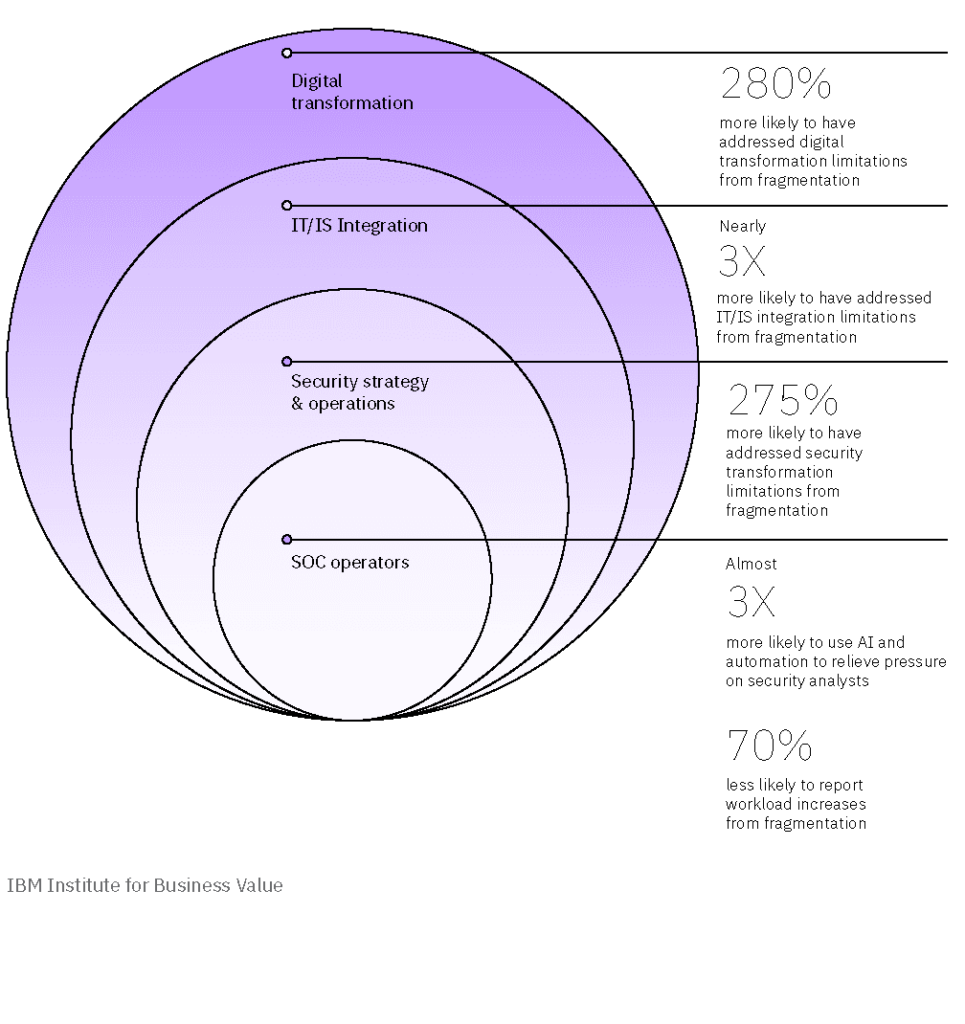
From point solutions to unified platforms
Point solutions earned their place in the stack by doing one thing extremely well. You bought a tool for cloud posture, another for endpoint, a third for attack simulation, a fourth for log analytics. Each solved a narrow problem.
But stitched together over years, this has left many organisations in disarray. And what once felt like freedom of choice now looks like integration debt. A recent Forbes analysis noted that there is now “so much noise in cybersecurity that it’s hard to tell where the real signal lies.”
The industry is shifting away from that model.
Instead of maintaining separate tools for IT monitoring, alert correlation, and remediation, teams are moving toward unified observability platforms that combine telemetry, automation, and AIOps in one place.
IBM’s research points in the same direction, showing that organisations that centralise monitoring and automated analysis see faster mean time to detect (MTTD) and mean time to resolution (MTTR).
Consolidated platforms can funnel events into a single source of truth, including…
- Shared timelines
- Shared context
- Shared playbooks
Instead of replaying the same alert in three tools, teams can focus on verifying impact, narrowing root cause, and triggering the right remediation workflow once. That alone can reduce operational overhead security teams face every week.
Case study: Automation and AI-powered remediation
Before diving deeper, it’s worth looking at an example how some teams are already pulling their fragmented stacks into something more unified. One use case is AI and automation observability solutions.
AI-powered observability tools take in massive amounts of telemetry (e.g. logs, traces, performance signals) and use machine learning to spot anomalies faster than any human team could.
Instead of sorting through a flood of alerts, analysts get a focused view of what matters, often with the likely root cause already highlighted. This removes the guesswork and cuts straight to verification and action.
AIOps builds on that foundation with predictive maintenance and real-time, automated remediation. Self-healing workflows can restart services, roll back failing updates, or isolate problematic components before they trigger downtime.
This leads to fewer outages, faster recovery, and far less time wasted chasing false positives. In short, automation turns troubleshooting into a scalable process. It keeps pace with cybersecurity threats, without burning out teams in the process.
However, even with the advantages of automation, team members can’t afford to grow complacent. AI can still mislabel anomalies, over-prioritise benign events, or overlook subtle indicators that an experienced analyst would catch. Consolidated platforms work best when AI augments human judgement, rather than replaces it.
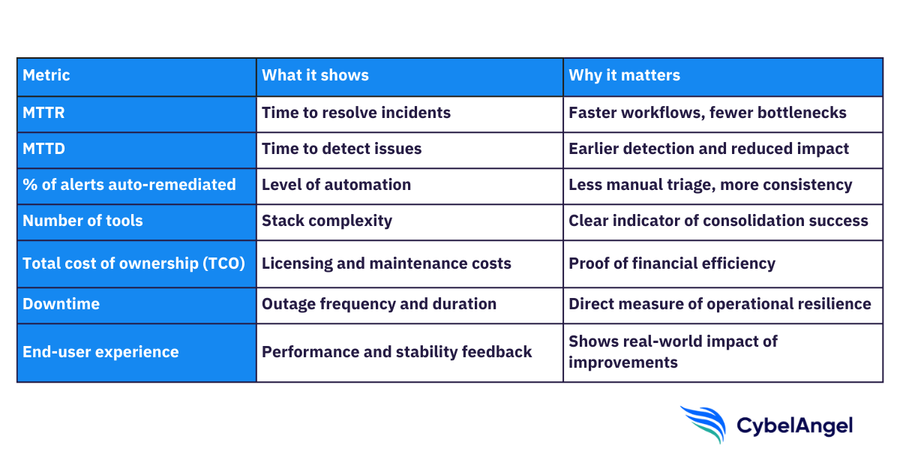
Measuring success: Metrics that matter
Once consolidation begins, the simplest way to understand its impact is to measure it directly. Teams typically track a combination of operational, financial, and user-experience metrics, including:
- MTTR and MTTD trends: Faster detection and resolution as analysts stop juggling fragmented dashboards.
- Percentage of alerts auto-remediated: A practical gauge of how well automation is reducing manual triage work.
- Reduction in the number of tools: Fewer licenses, fewer integrations to maintain, and clearer ownership.
- Lower total cost of ownership (TCO): Savings across licensing, maintenance, training, and infrastructure.
- Decreased downtime: Fewer outages and faster recovery when issues do occur.
- Improved end-user experience: Smoother performance and fewer service disruptions as root-cause work becomes more efficient.
How to plan a tool consolidation initiative
A successful tool consolidation starts with understanding what you already have, and then getting your whole IT operations on board. Here’s an end-to-end checklist to make it happen.
- Inventory existing tools and apps: Map every product across IT, security, and DevOps. Make sure you capture its purpose, ownership, and usage to spot any redundancies or overlaps.
- Identify overlapping functionality: Compare capabilities to see where multiple tools serve the same purpose or generate duplicate data.
- Assess integration points and data silos: Note where data is trapped, inconsistently shared, or requires manual correlation across dashboards.
- Align IT operations, DevOps, SecOps, and finance: Bring stakeholders together to agree on priorities, workflows, and expected outcomes from consolidation.
- Pilot consolidation in one focused domain: Start with something contained, like monitoring tools, to validate integrations, workflow improvements, and stability.
- Track metrics during the pilot: Measure stats such as MTTR, alert noise, downtime, cost savings, and user feedback to build evidence for wider rollout.
- Invest in onboarding, training, and communication: Ensure teams know how the new environment works, why certain tools were retired, and how the change improves day-to-day operations.
When done right, the cybersecurity ROI will quickly become apparent, and you’ll be able to future-proof your operations for the long run.
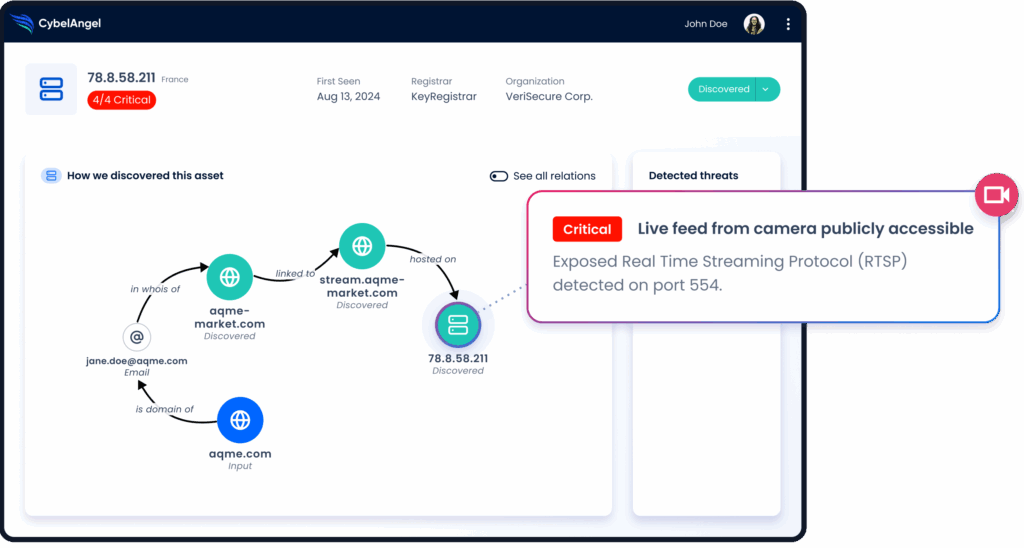
CybelAngel: Unified visibility beyond the perimeter
External risks don’t sit neatly in one place. Exposed assets turn up in cloud platforms you forgot you were using, credentials surface on criminal forums, and supplier systems reveal weaknesses long before anyone tells you.
CybelAngel pulls those threads together.
Its attack surface mapping, dark web intelligence and third-party insights all feed into one coherent view, so you’re not piecing the story together from separate tools.
You see issues earlier, you act faster, and you avoid the usual back-and-forth between teams trying to make sense of fragmented signals. It’s tool consolidation where it’s most needed, sitting at the edges of the organisation, where blind spots tend to hide.
Frequently Asked Questions
Tool consolidation means reducing overlapping products and folding separate monitoring, detection, and troubleshooting functions into a smaller number of coordinated platforms. It’s become a priority because teams are losing time (and visibility) to fragmented systems, which slows response and increases risk. Consolidation helps streamline workflows, reduce noise, and create a clearer picture of what’s happening across the environment.
The simplest way is to map current spend (e.g. licences, maintenance, integrations, training) against what consolidation removes or replaces. Then factor in operational gains, such as lower MTTR, fewer outages, reduced alert fatigue, and less time spent juggling dashboards. When you quantify both the financial and productivity savings, the business case becomes straightforward.
Not necessarily. Many organisations keep a few specialised tools and consolidate everything around them. The aim isn’t to force everything into one platform, but to reduce fragmentation so teams work from a shared source of truth. If a tool brings unique value, it stays. It just needs to integrate cleanly with the rest of the workflow.
Automation reduces the manual steps that slow down investigations. Instead of sorting through duplicated alerts, teams receive pre-correlated signals with likely root causes attached. Automated playbooks can also trigger fixes (e.g. restarting services or isolating assets) which keeps issues contained while analysts verify the result.
The biggest risks usually come from poor planning. For example, CISOs might be retiring tools before teams are ready, disrupting integrations, or underestimating how embedded certain workflows are. Successful projects take a phased approach, run pilots, and invest in training so teams aren’t blindsided by changes in their day-to-day operations.
When data lives in fewer systems, it’s easier to audit, correlate, and produce consistent reports. Consolidated platforms also reduce the risk of missing evidence or overlooking misconfigurations that sit outside your main monitoring path.
Conclusion
Security teams are finally stepping back from the tangle of disconnected tools. They’re recognising that resilience comes from clarity, not quantity. Consolidation is part of that shift, helping to optimize teams’ operational efficiency in integrated, clean workflows.
CybelAngel helps extend that clarity to the outside world, giving organisations unified visibility and automation where blind spots tend to hide. The result is a stronger posture, smoother operations, and a security programme that can finally keep up.

