Dangers of Credential Stuffing to Businesses

Table of contents
What is Credential Stuffing?
Credential stuffing is when criminals steal usernames and passwords from one website and use them to try to log into different websites or applications. We are not talking about hacking into one account. We are talking about millions of stolen account credentials being fed by botnets into other websites to try to gain unauthorized access. Botnets try millions of username-password combinations, until one of them allows access to a system. Credential stuffing succeeds when people re-use their passwords on multiple sites — especially their business accounts.
Account Takeover (ATO)
Much has been written about the dangers of having personal accounts hacked, including identity theft and emptied bank accounts. What is often overlooked is the potential link to business accounts. Leaked credentials increase the risk of cyber attacks on corporate networks, ransomware attacks on corporate computers, and data theft. Leaked employee credentials leaves the door open for hackers to take over the employee’s account and penetrate the corporate network. Enterprise account takeover (ATO) attacks most often begin with a data breach when email addresses and passwords are stolen. Then, cybercriminals can gain access to and control a victim’s account. Once control is established, the attacks can range from theft of data to ransomware. A recent Forrester report states ATO has caused between $6.5 billion and $7 billion in annual losses across financial services, insurance, ecommerce, and other verticals.
How big is the problem
According to the latest Verizon Data Breach Investigations Report, the number of credential stuffing attempts organizations are experiencing per year ranged from thousands to billions. The median number of attempts enterprises experienced per year was 922,331. This situation was highlighted by the U.S. Securities and Exchange Commission, which warned of an increase in credential stuffing in the financial industry. 
How are business fighting back
Organizations are attempting to secure their employees’ credential leaks with an increasing sense of urgency. The first step many businesses are taking is to adopt guidelines for password security. This begins with defining password requirements, such as the number of characters, the use of uppercase, lowercase, and special characters, change frequency, and so on. Next, many enterprises are strictly forbidding the use of corporate passwords for third-party applications. While these security measures are good practices, they leave enterprises one step behind the hackers. To be efficient and effective, you need to act before the credentials are sold. You must exhaustively scan for database leaks to take ATO prevention to the next level.
Preventing Account Takeovers
The final step in preventing credential weaponization from credential stuffing or other brute force attacks is credential monitoring. CybelAngel is the only digital risk protection platform that detects and manages leaked credentials before they are compromised. Our customers have the benefit of CybelAngel’s data lake, which contains 10 billion exposed email addresses and passwords. This cache of exposed email addresses and passwords is continuously updated with scans of over 335,000 Deep & Dark Web posts and 3,000 newly exposed databases each and every day of the year. 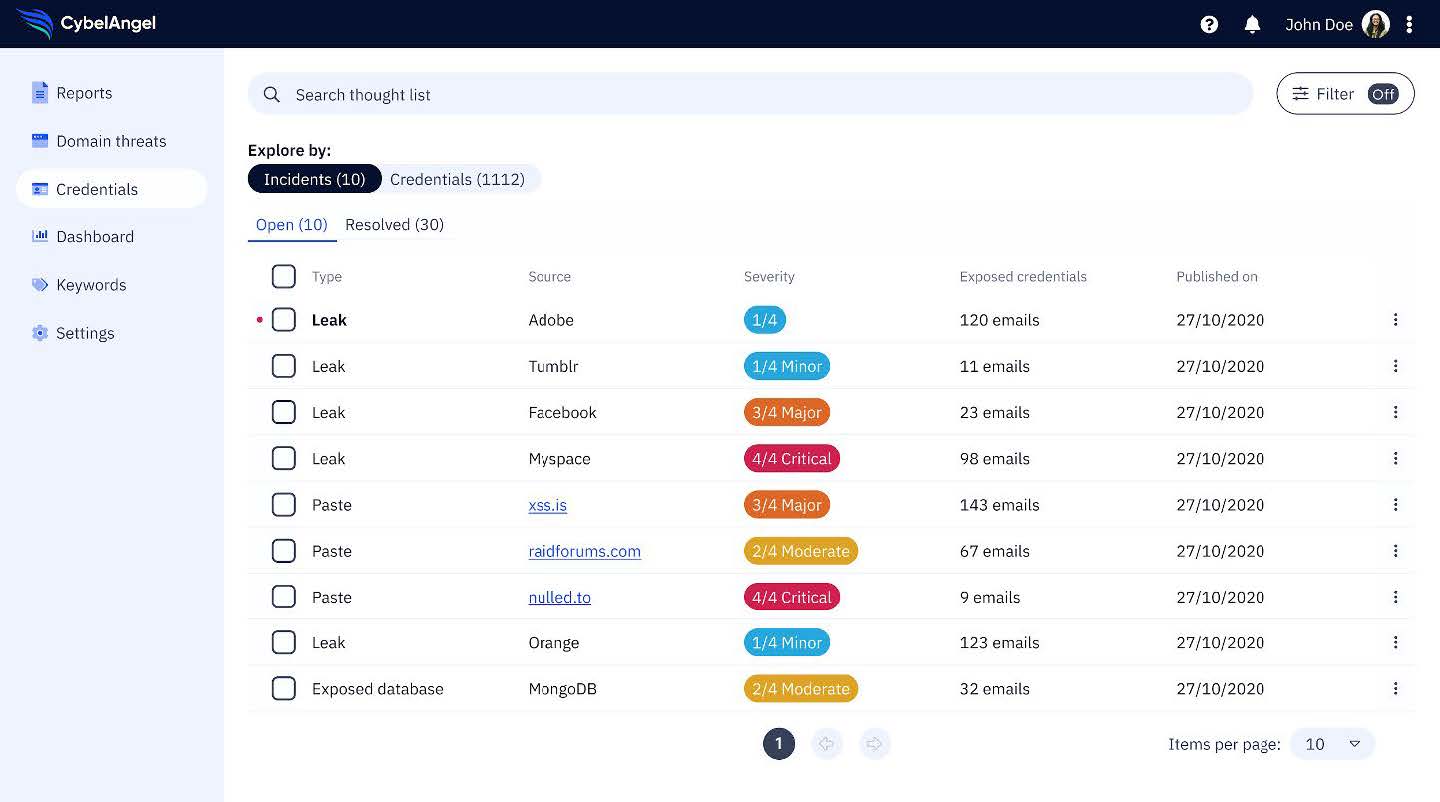 Now, add CybelAngel’s Credentials Watchlist to your arsenal of cybersecurity weapons. Our Credentials Watchlist is a real-time feed of compromised staff credentials coupled with exposure monitoring features. The Watchlist is integrated into the CybelAngel Digital Risk Protection Platform, where the feed is exposed across multiple dashboards. Our customers can access contextualized credential leaks and unique reports, all of which empower their teams to mitigate credential leaks and avoid the threat of VIP impersonations. CybelAngel can protect your business from the dangers of an Account Takeover. Click here to talk to one of our experts about a free trial.
Now, add CybelAngel’s Credentials Watchlist to your arsenal of cybersecurity weapons. Our Credentials Watchlist is a real-time feed of compromised staff credentials coupled with exposure monitoring features. The Watchlist is integrated into the CybelAngel Digital Risk Protection Platform, where the feed is exposed across multiple dashboards. Our customers can access contextualized credential leaks and unique reports, all of which empower their teams to mitigate credential leaks and avoid the threat of VIP impersonations. CybelAngel can protect your business from the dangers of an Account Takeover. Click here to talk to one of our experts about a free trial.

