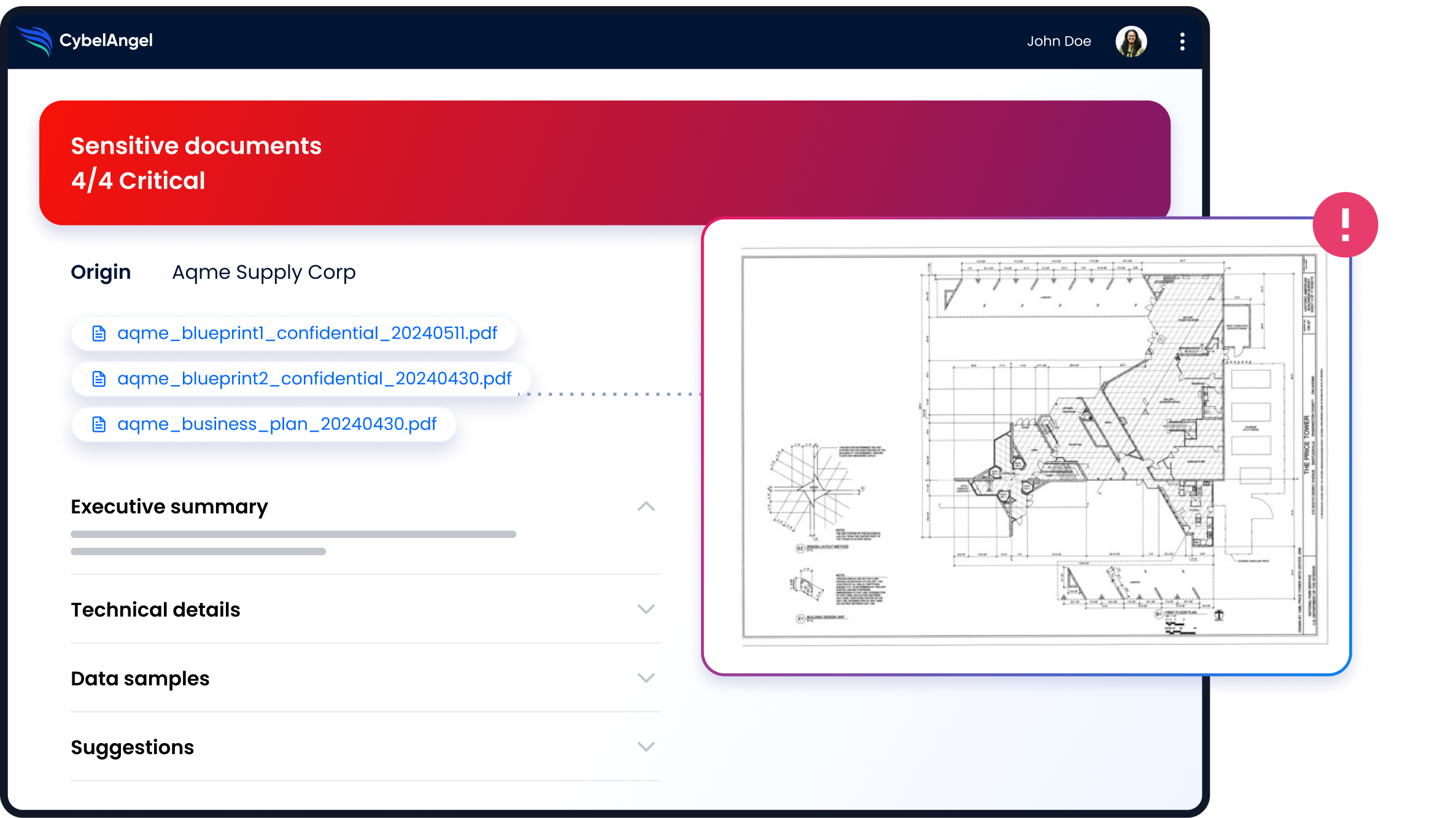
Almost 60% of businesses have experienced significant data breaches due to third-party actions, with the average total cost of a data breach now estimated at $4.88 million in 2024, marking an increase from previous years. This underscores the limitation of conventional IT solutions in safeguarding critical data throughout intricate, digital supply chains.
CybelAngel conducts daily scans of over 4.3 billion IPs, employing comprehensive, document-centric scanning techniques across all publicly accessible sources.