LockBit, Qilin, and DragonForce: The New Ransomware Alliance

Table of contents
Three ransomware brands, LockBit, Qilin, and DragonForce, have joined forces. Instead of fighting for market share, these ransomware groups are pooling their resources, from malware and infrastructure to negotiation playbooks. Their alliance marks a shift in how organized cybercrime operates.
Now, the question isn’t which group is behind the next cyberattack. It’s how many of them are working together. Let’s explore the dynamics of this new organization, the background of each ransomware group, and what this means for cybersecurity teams.
Introduction
In Q3 2025, LockBit, Qilin, and DragonForce moved closer together. Analysts at ReliaQuest have traced shared infrastructure, tools, and data-leak resources linking the three groups. This marks a rare level of collaboration in the ransomware landscape, where competition is usually the order of the day.
But the timing can’t be accidental.
- LockBit is rebuilding after last year’s takedown
- Qilin’s ransomware operators are gaining momentum
- DragonForce has evolved from hacktivist disruption to commercial-scale extortion
By joining forces, these threat actors combine technical depth, brand recognition, and a loyal network of affiliates. Let’s explore the individual threat groups, before examining what this coordinated effort could mean for future ransomware attacks.
LockBit: Its rise, fall, and return
Since its debut in 2019, LockBit has become one of the most prolific ransomware brands in the world. At its peak, the group claimed thousands of victims and over $500 million in ransom payments, operating through a vast network of affiliates under a ransomware-as-a-service (RaaS) model.

Figure 1: Screenshot of the LockBit forum, claiming to have stolen data from Subway. (Source: Security Affairs)
That success also drew attention. In early 2024, law enforcement agencies launched Operation Cronos, seizing LockBit’s infrastructure and exposing its internal communication channels. At the time of the takedown, LockBit had been responsible for a third of all data leak site victim postings. However, the ringleader, named as Russian national Dmitry Khoroshev, remained at large.

By mid-2025, LockBit had resurfaced. Its newest version, LockBit 5.0, appeared on the RAMP darknet forum on September 3, the sixth anniversary of the affiliate program. New features include:
- Multi-platform usage: Targeting Windows, Linux and ESXi systems
- Anti-analysis features: Blocking cyber investigators in their tracks
- Faster data encryption: Stealing sensitive information in record time
- Randomized 16-character file extensions: Making it easier to evade detection
LockBit’s ability to recover so quickly highlights how established ransomware groups now operate more like franchises. Even after global takedowns, the brand (and the infrastructure supporting it) continues to reassert its place in the ransomware economy.
Qilin: The strategist behind double extortion
Qilin has positioned itself as one of the most active ransomware threats of 2025. Known for its polished operations and consistent targeting of North American organizations, the group’s top targets are manufacturing, healthcare, and real estate.
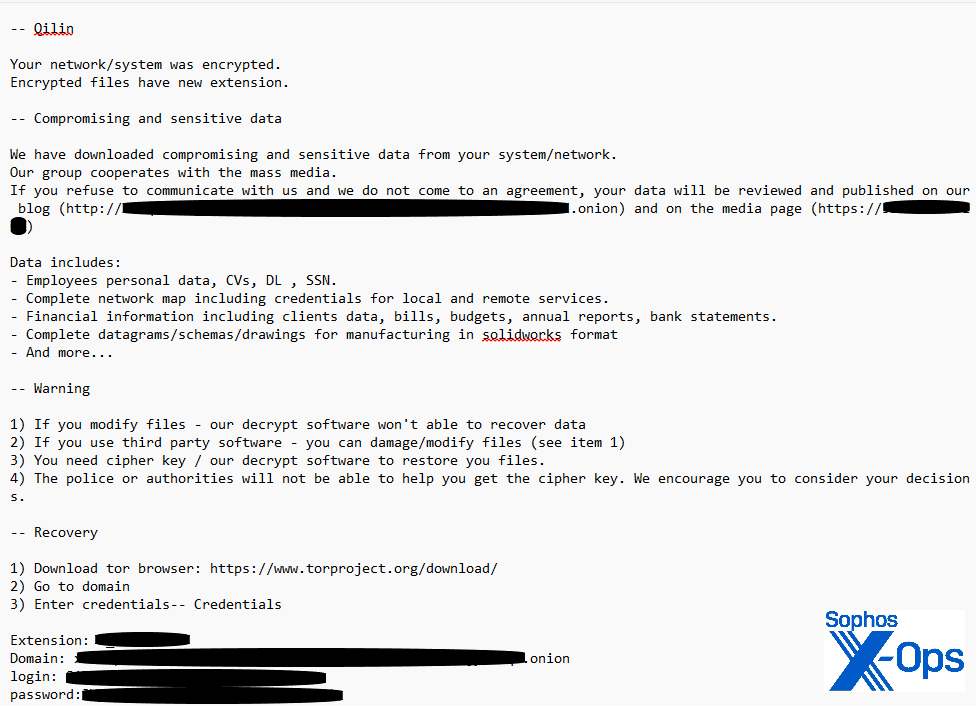
Its double-extortion tactics are highly structured. Victims are encrypted and then threatened with public data leaks, often on Qilin’s own data leak site.
The group’s encryption methods are complex, and its negotiations follow a standardized, almost corporate process, complete with branding, documentation, and consistent messaging. There’s even a “Call Lawyer” feature to add pressure.
In Q3 2025 alone, Qilin ransomware claimed more than 200 victims. Its presence is expanding quickly across affiliate channels, often appearing alongside other RaaS names in dark web discussions. While its motives are primarily financial, Qilin’s disproportionate focus on North America could indicate some geopolitical motivations, too.
DragonForce: From hacktivism to enterprise-scale extortion
DragonForce began as a hacktivist collective. But over time, it changed its tune to focus more on financially motivated cyberattacks. And it isn’t above attacking its own competitors; in April 2025, it claimed to have taken over RansomHub’s data leak site.

The group mainly targets entities in the US, UK and Australia, and its malware has been reused by other cybercriminals, including Scattered Spider. This shows that while DragonForce competes with rival groups for attention, it also enables others by sharing tools and infrastructure.
What this new alliance could mean
It’s difficult to see exactly how the LockBit–Qilin–DragonForce alliance operates, but analysts have described, “the sharing of techniques, resources, and infrastructure.” Even if their exact roles remain hidden, it’s clear that each group will bring something different.
For example, LockBit could provide the infrastructure and encryption tools, Qilin might handle the negotiation playbooks, and DragonForce could run the publicity machine through its leak platforms and propaganda channels.
Whatever the exact workings, this kind of cooperation also makes the ransomware ecosystem harder to contain. Ransomware-as-a-service now runs more like a supply chain than a gang network.
Affiliates can move between brands, tools can be repurposed, and takedowns like Operation Cronos only scatter talent across new banners. Q3 2025 saw over 1400 ransomware and digital extortion incidents, a sign that takedown efforts may be outpaced by reinvention.
This particular alliance might not last forever. But for now, it shows how decentralized ransomware has become. And of course, how easily one group’s comeback can fuel another’s rise.
How defenders should react
New ransomware alliances can confuse security teams. Attack cycles move faster, tactics are blended, and tools are being used across multiple groups (such as in the case of DragonForce and Scattered Spider).
Security teams can’t afford to follow the “one-group-one-toolkit” model, anymore. Instead, they need to be mindful that indicators of compromise (IOCs) can be shared and rebranded across different threat groups. Instead of attributing cyber threats to one specific group, they need to spot the patterns, such as:
- Similar payloads
- Reused infrastructure
- Synchronized data theft activity
And plenty of industries are under pressure. Critical infrastructure, healthcare, and supply chain providers remain prime targets, often because of complex vendor networks and low tolerance for downtime. These sectors also face zero-day exploitation, MFA bypass, and double extortion. Each can now be purchased or borrowed between affiliates, shrinking defenders’ reaction time.
Building resilience
Static playbooks don’t work anymore. Defending against RaaS alliances requires flexibility and visibility across both internal and external assets.
Key steps include:
- Update incident response playbooks to reflect shared infrastructures and overlapping campaigns.
- Monitor dark web chatter for signs of affiliate recruitment or coordination in the threat landscape.
- Integrate external threat intelligence to map out attacker networks, social engineering tactics, and tool reuse.
- Prioritize asset discovery to identify exposed systems, credentials, and suppliers.
- Maintain strong hygiene through consistent patching of vulnerabilities, segmentation, and least-privilege access.
These aren’t new measures. But they do matter more when multiple ransomware brands are pulling from the same toolkit.
Securing from beyond the perimeter
CybelAngel’s external threat intelligence platform gives security teams visibility into this evolving ransomware ecosystem. It tracks exposures across dark-web forums, data-leak sites, and supplier networks, connecting the dots between emerging ransomware brands and shared infrastructure.
Having live intelligence feeds helps CISOs to handle threats before they become an issue. Plus, they can anticipate changing cybercriminal behaviors, instead of constantly reacting to them. Book a demo with CybelAngel to learn more about how this kind of foresight is critical to your team.
FAQs
1. What makes the LockBit–Qilin–DragonForce alliance different from past collaborations?
This partnership shows an unprecedented level of resource sharing between major RaaS brands, from infrastructure to affiliates, effectively forming a joint ransomware ecosystem.
2. How do ransomware groups like these rebuild after takedowns?
They decentralize. Affiliates migrate to new brands, reusing code, servers, and leak sites under fresh identities.
3. How can external threat intelligence reduce ransomware risk?
By detecting exposures and chatter before attackers act, giving defenders time to contain risk before encryption or data theft begins. Tools like CybelAngel can help with this.
Conclusion
The LockBit–Qilin–DragonForce alliance shows how ransomware has become an adaptive ecosystem.
Groups now share infrastructure, affiliates, and code, making disruption harder and recovery faster. For CISOs, that means threats don’t disappear with one takedown; they simply regroup under a new name.
CybelAngel’s external threat intelligence helps detect those links early (from leaked data to reused infrastructure) giving defenders time to respond before attacks unfold.
