Brand Monitoring Isn’t Just For Marketing Anymore…

Table of contents
Brand abuse has become a security issue, not just a marketing campaign concern. Cybercriminals can pretend to be a famous brand, and then mislead customers, harvest data, or run fraud campaigns.
Often, they don’t even trigger traditional security alerts. A fake executive profile or cloned website can circulate for weeks before anyone notices, especially when it lives outside your owned channels.
This article breaks down the tactics used to exploit brands, ranging from social media impersonation to counterfeit listings and phishing domains. You’ll see where these attacks happen, how they spread, and what security teams can do about it.
Brand exploitation tactics, techniques, and procedures (TTPs)
How do cybercriminals take control of a brand and make people believe it’s genuine? There are lots of methods, some of which are opportunistic, and others are part of a wider campaign. But all of them can do serious damage to brand reputation, and damage public perception and trust.
Common techniques include:
- Domain squatting: Registering lookalike domains with swapped characters, or added hyphens to host fake login pages or distribute malware.
- Phishing infrastructure: Spinning up cloned websites, spoofed email campaigns, and fake apps to steal credentials and redirect payments. Nearly 51% of browser-based phishing attempts include brand impersonation.
- Executive impersonation: Creating fake social media accounts that mimic public-facing leadership to solicit employees, customers, or partners.
- Counterfeit product listings: Uploading fake items to ecommerce platforms like Amazon, Alibaba, or Facebook Marketplace to siphon off sales or distribute unsafe goods.
- Social media spoofing: Launching fake brand pages, fake influencer marketing collaborations, or paid ads that direct traffic to scams or credential harvesters.
And these tactics often work together.
For instance, you might visit a squatted domain, which then leads to a fake site, which is promoted via a spoofed social post, resulting in customer data theft or payment redirection.
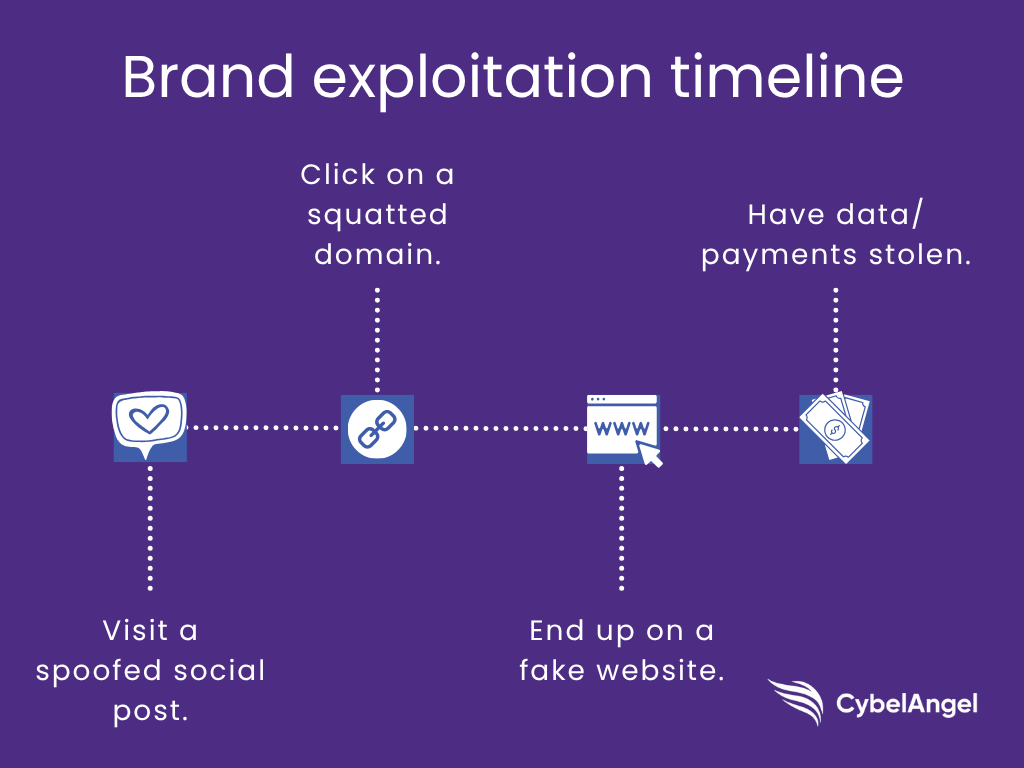
High-volume attack surfaces: Where brand abuse happens
Brand abuse happens on platforms you don’t own. That’s part of what makes it so effective and so hard to catch.
For example, brands often face impersonation on social media channels like TikTok and LinkedIn, where scammers can exploit hashtags, paid ads, and industry trends to build credibility quickly. And without strong social media monitoring or social listening tools, this can go undetected for weeks.
Here are some of the most commonly targeted environments:
- Social media platforms: Fake pages and impostor accounts are used to promote scams, reroute customers, or impersonate employees. For example, Reuters has reported on fake Twitter accounts mimicking Disney Junior UK.
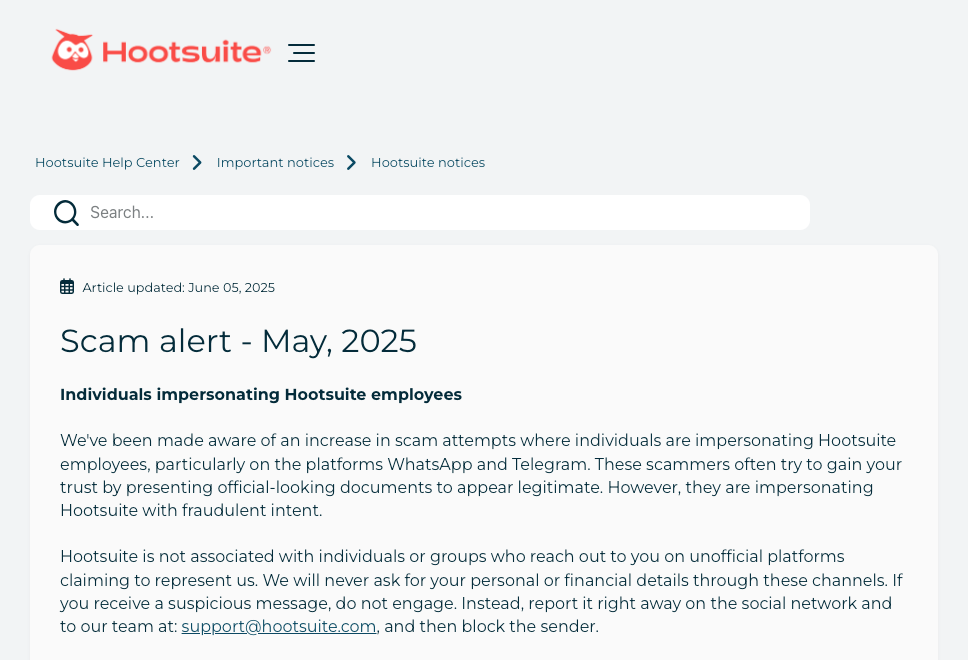
- Messaging apps: Telegram, WhatsApp, and even Slack are frequent channels for unsolicited contact and executive spoofing. These platforms offer reach and anonymity, with little oversight. In May 2025, Hootsuite warned that fraudsters were using WhatsApp and Telegram to pose as company reps, backed by fake documents to gain trust.
- Search engines and SEO: Bad actors run paid ads on Google using lookalike domains, or hijack search results through malicious backlinks and spoofed metadata to outrank legitimate content.
- Marketplaces: Counterfeit products often appear on Amazon, AliExpress, or Facebook Marketplace, complete with fake reviews, cloned images, and official branding. Many brands don’t realize listings exist until customer support flags the fallout.
- Dark web and forums: Leaked assets, impersonation kits, and stolen credentials often circulate on underground forums long before the scam goes live. Monitoring these surfaces provides critical early warning signals.
- Finance and payment platforms: Zelle and other peer-to-peer payment tools have become prime targets for imposter scams. In 2022 alone, attackers used fake branding and communication tactics to steal over $2.6 billion from US consumers, prompting refunds and policy changes from major banks.
- AI-powered voice impersonation: Some attackers now clone the voices of public figures or executives to enhance phishing calls. In one reported case, scammers used AI-generated speech to pose as senior US officials.
Ultimately, attackers go wherever your audience is. That’s why online brand monitoring has to extend beyond your domain, your ad accounts, and your CRM, and reach into the platforms and networks you don’t control.
Regional threat hotspots: Global trends in brand abuse
Brand abuse is a global problem, but it doesn’t play out evenly across the map. Some regions see more activity due to enforcement gaps, low prosecution risk, or the sheer volume of ecommerce and social media users.
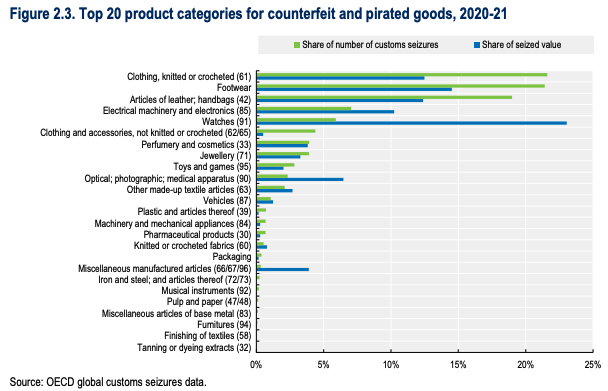
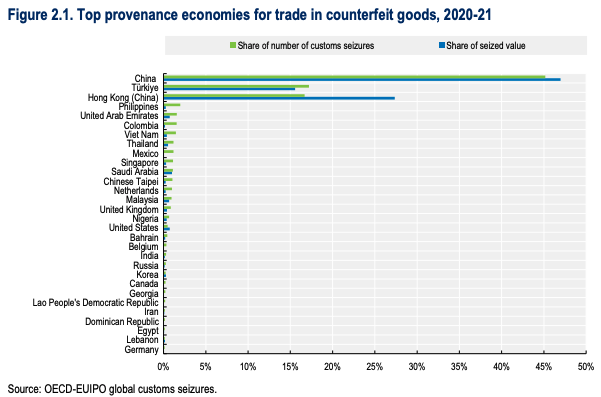
The EUIPO and OECD estimated that the global trade in counterfeit and pirated goods has reached $467 billion, with high-volume activity linked to Southeast Asia, the Middle East, and South America.
Products shipped from these regions often carry spoofed branding or impersonate well-known financial institutions, especially in online marketplaces.
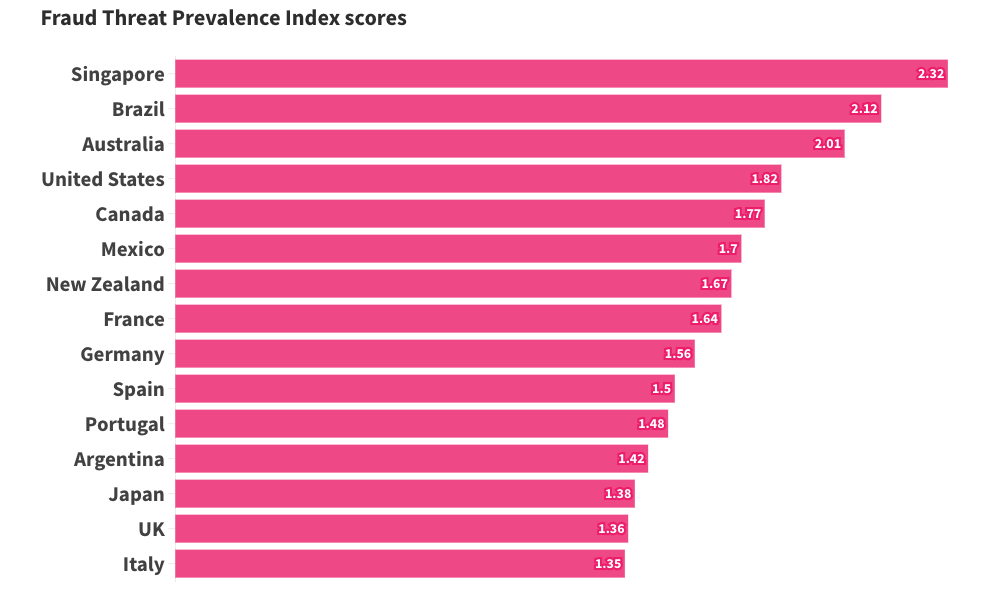
New fraud data from the Social Market Foundation reveals which countries face the most serious levels of consumer deception. Singapore, Brazil, and Australia rank highest for fraud prevalence across 15 surveyed nations.
Let’s break this down:
- Singapore & Brazil: High rates of consumer fraud and strong online engagement make these regions hotspots for scams involving payment apps, fake financial services, and brand misuse.
- Australia & the US: Both countries appear in the top five for fraud exposure, reflecting strong digital economies paired with rising impersonation threats.
And cross-border takedowns remain complex, especially when sites are hosted in one country, registered in another, and promoted from a third. That’s why global brand monitoring tools need to operate in real time, with legal escalation and takedown workflows already in place.
The cost of inaction: What brand exploitation leads to
When attackers impersonate your brand, the consequences fall on you. Customers lose money. Support teams face the backlash. And trust, once broken, takes time to rebuild.
Even if the scam sits on a third-party site or app, most people won’t know the difference. If your name or logo is on it, they assume it’s legitimate. That misdirection is exactly what makes these attacks so effective and damaging.
The longer the brand impersonation goes undetected, the greater the cost to your online reputation. You may face:
- Losing customers who fall for fake messages, login pages, or support accounts.
- Getting pulled into legal trouble if regulators decide your response was too slow or too weak.
- Wasting time and money on cleanup, from internal reviews to crisis comms to SEO recovery.
- Watching your brand slip in search because fake domains and links are drowning out the real ones.
Plus, brand impersonation often scales quickly. One fake post might inspire copycats. And one spoofed domain could be cloned dozens of times. Without early detection, what starts small becomes harder to contain and more expensive to clean up.

Detection and monitoring: What modern brand protection looks like
Most brand impersonation campaigns don’t start with a headline. They start small, such as with a new domain registration, a fake profile, or a phishing link buried in a social post. By the time they reach customers, the infrastructure is already in place.
That’s why early detection matters. You need visibility into the platforms, marketplaces, and networks where your brand could be misused, even if you don’t control them.
Effective brand monitoring today includes:
- Domain tracking: Monitoring new registrations that resemble your brand name or redirect to suspicious infrastructure.
- Social media detection: Flagging fake profiles, spoofed executive accounts, unusual social mentions, and impersonation attempts across major platforms.
- Marketplace scanning: Identifying counterfeit product listings and fake storefronts using your brand assets.
- Phishing infrastructure discovery: Catching cloned websites and email campaigns before they reach critical mass.
- Dark web monitoring: Detecting leaked brand materials or impersonation kits before they’re used.
But it’s not just about alerts. Monitoring must include real-time prioritization, context, and takedown support, so that teams know which risks to act on and how fast.
CybelAngel helps global brands detect impersonation campaigns early, across domains, marketplaces, social media, and the dark web. With real-time alerts and takedown support, your team can act before customers are affected.
Learn more about its online brand protection services, and you’ll be one step closer to safeguarding your business.
What to do when your brand is targeted
Detection is only half the battle. Once brand abuse is identified, your response needs to be fast, coordinated, and repeatable, especially if the impersonation is already live and visible to customers.
The first step is containment. That might mean issuing takedown requests to domain registrars, reporting fake social profiles, or escalating fraudulent listings to marketplaces. Each platform has its own process, and timing matters. Delays can increase both exposure and damage.
From there, the response should involve more than one team. Security might handle the technical investigation. Legal manages takedown requests. Comms supports customer messaging. It’s not always a crisis, but it needs a plan.
Here’s what that plan should include:
- Clear roles: Know who owns each part of the crisis management response, and how teams will communicate.
- Template workflows: Pre-approved takedown language, legal notices, and escalation paths.
- Internal alerts: Real-time notifications when a brand threat is detected, not hours later.
- Post-incident reviews: Learn from each case. Update your brand protection checklist, tooling, or thresholds based on what worked (and what didn’t).
- Customer feedback: Do a brand sentiment analysis to understand how impersonation might have affected brand awareness, customer experience, and public perception.
Even if the impersonation is handled quietly, the next one won’t always be. A well-defined playbook makes the difference between a fast takedown and a public mess.
Choosing the right brand protection partner
Brand risk management takes more than Google Alerts. It requires reach, speed, and support across platforms, regions, and threat types. Manual brand tracking just doesn’t scale. You need to automate your reputation management to avoid being caught out.
When evaluating a tool to optimize your brand monitoring strategy, look for:
- In-depth coverage: Can they monitor your brand presence via domains, social media posts, marketplaces, and the deep/dark web?
- Real-time detection: Do they offer live alerts when threats appear, not days later?
- Takedown capability: Can they assist with removal, not just surface the problem?
- Contextual intelligence: Do alerts come with risk scoring or indicators that help you triage mentions of your brand?
- Cross-team usability: Is the brand abuse detection platform accessible to both security and brand/comms teams?
Some providers focus solely on marketing mentions. Others detect threat metrics but leave takedowns to you. The strongest brand management tools close the loop (from detection through resolution) and help you measure what’s improving over time.
CybelAngel offers digital brand protection, with global coverage, analyst support, and proven takedown workflows. Book a demo to see how it could help you track brand mentions, review sites, and stay on top of your brand health.
Final thoughts
Because impersonation can undermine campaign performance and damage SEO, it affects more than trust. It also erodes your marketing strategies, weakens your online presence, and damages brand performance.
Monitoring brand mentions is paramount. Brand protection should be your top priority; it belongs in your threat intelligence program, your SOC dashboard, and your response playbooks. Because when attackers go after your name, your customers are the ones who pay first.

