The Zero Trust Security model: A Practical Guide

Table of contents
Zero Trust keeps coming up in board meetings and budget reviews, yet the term still gets stretched in every direction. You’re expected to “implement Zero Trust,” but what that means in practice is often unclear, especially when your environments span cloud workloads, legacy systems, SaaS platforms, remote users, and unmanaged devices.
This glossary entry gives you a clear, grounded explanation of the Zero Trust security model, what NIST 800-207 actually says about it, and how it applies to your daily decisions around identity, access, and resource protection.
What Zero Trust means in practice
Zero Trust (ZTA) is a security strategy where no request is trusted by default. NIST SP 800-207 frames it as “the premise that trust is never granted implicitly but must be continually evaluated.”
In other words, never trust. Always verify.
The Zero Trust approach focuses on continuous verification, least privilege access, and protecting resources rather than relying on a network perimeter. Each access request is evaluated on its own, including the identity, device posture, and context.
For your authentication and access controls, this means that every session must be verified, enforced, and monitored. User identity, device health, and access policies work together to decide what is allowed, and only for as long as it’s needed.
How this differs from the traditional perimeter model
The perimeter model assumed your users, devices, and applications lived inside a controlled network. This was a traditional security perspective.
Once someone passed the gateway, they could often move freely. But that assumption doesn’t hold when your workloads run across multi-cloud environments, contractors connect from anywhere, and personal devices sit alongside managed endpoints.
Zero Trust solutions treat every connection as external. Instead of protecting a single boundary, you always verify each request, no matter where it comes from.
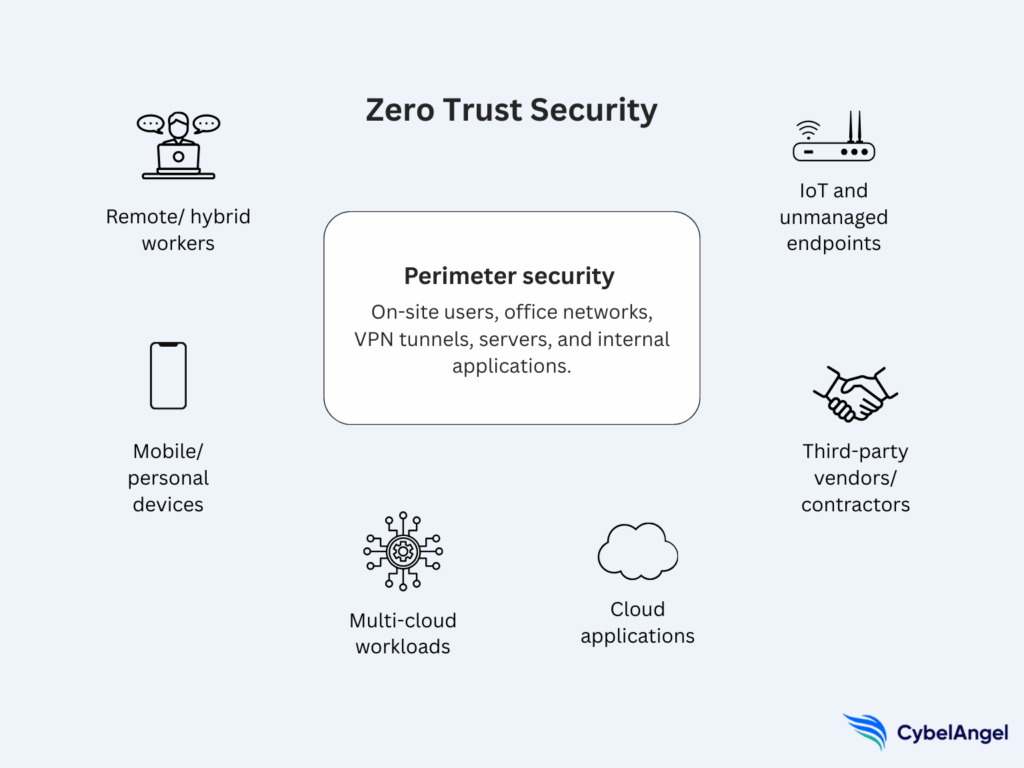
The core principles of Zero Trust
Zero Trust gives you a way to apply consistent access controls across cloud services, endpoints, and internal applications.
NIST SP 800-207 describes these principles as the foundation of a security model that evaluates every request, limits exposure, and reduces opportunities for lateral movement.
Here are the core elements, kept practical and aligned to real environments:
- Continuous authentication and authorization: Every user access request is checked in real time, often with MFA and device posture signals
- Least privilege access: Permissions match the minimum required action, reducing the blast radius of unauthorized access
- Securing all communication: Traffic is encrypted end-to-end, whether it moves between cloud workloads, APIs, or internal apps
- Context-informed decisions: Identity, device health, location, behavior, and time influence each policy decision
- Continuous monitoring and validation: Logs, signals, and telemetry help detect drift, suspicious activity, and attempts at unauthorized access
- Protecting workloads, endpoints, and API-driven services: Applications, microservices, and devices are treated as individual resources with their own security policies
- Microsegmentation to limit lateral movement: Network security shifts from broad zones and firewalls to fine-grained segmentation around specific resources
These principles only work when they’re applied to every identity, device, and workload you manage. The next section looks at how Zero Trust operates across those layers and how each request is evaluated in real time.
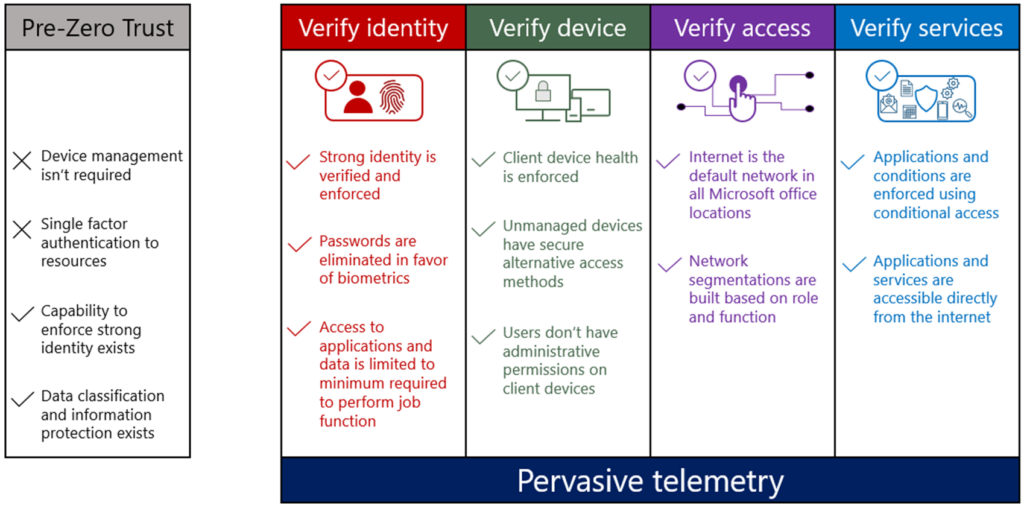
How Zero Trust works across identities, devices, and workloads
Zero Trust evaluates every access attempt through a steady decision cycle. NIST SP 800-207 describes this as a process driven by a policy engine, a policy administrator, and enforcement points placed close to the resources being protected.
Each request is checked as conditions change, creating a consistent way to control user access, device activity, and workload communication.
- Identity and access management (IAM): Identity is the first signal in the decision process. Authentication may involve multi-factor authentication (MFA), single sign-on (SSO), or additional checks tied to user behavior. Permissions follow least-privilege principles, and access can be tightened or revoked whenever new risk signals appear.
- Device posture assessment: The device’s condition shapes the outcome of the request. Endpoint health, configuration state, and recent vulnerability findings feed into the access policy. If posture weakens, the system can restrict or cut off the session until the device meets requirements again.
- Workload-to-workload protection: Applications and services also authenticate to one another. Workload interactions use encrypted channels, verified identities, and clear access policies to reduce unnecessary trust paths. This helps maintain consistency across multi-cloud and hybrid environments.
- Continuous verification cycle: Every access attempt moves through the same loop. It gathers signals, evaluates them, and then enforces the decision. This cycle continues throughout the session, allowing the system to react to new context without waiting for a user to reauthenticate.
But Zero Trust only works when these checks happen automatically and at scale. The next section looks at the architecture that makes this possible and how each component supports the decisions behind every access request.
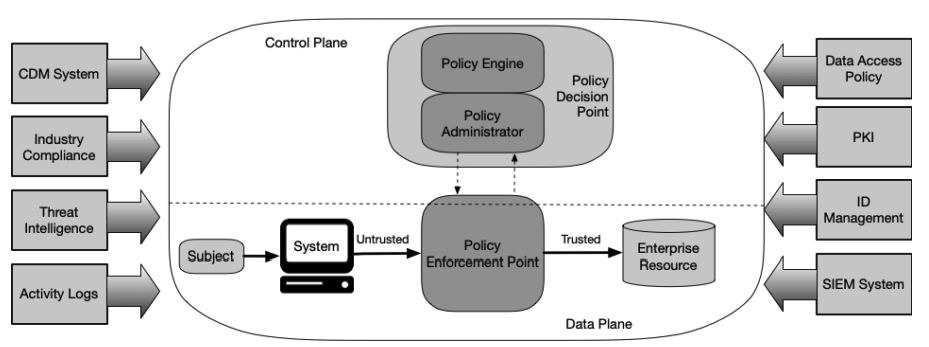
Zero Trust architecture components (NIST 800-207)
Many organisations have already started moving toward Zero Trust architecture. Microsoft has built it into Entra, Google pioneered the model with BeyondCorp, and federal agencies now use NIST SP 800-207 as their reference point. The architecture is straightforward once you understand the main components and how they work together across cloud environments and on-premises systems.
At the centre is the policy engine (PE). This is where decisions are made. Every request is checked against access policies, identity signals, device posture, and any relevant security controls. NIST describes this as the point where the organisation decides whether a connection should continue or stop.
The policy administrator (PA) turns that decision into a real action. It sets up the connection, tears it down when needed, and issues whatever tokens or keys are required for the session. You can think of it as the hands of the system, carrying out what the policy engine decides.
Policy enforcement points (PEPs) sit close to the applications, workloads, and data you want to protect. They intercept each request before it reaches the resource. In a Zero Trust Network Access (ZTNA) setup, these enforcement points form the gateway layer that controls entry into cloud environments and on-premises systems.
Behind these components are the data sources that feed the decision process. Rather than list them exhaustively, it helps to group them by purpose:
- Signals about who is making the request (identity providers, IAM platforms).
- Signals about the environment (SIEM events, CDM findings, configuration drift).
- Signals about external threats (threat intelligence feeds, known malicious hosts, or leaked assets).
Together, they give the architecture the context it needs to apply accurate access policies and data protection measures.
This is also where external threat intelligence becomes important. Internal tools can confirm identity and device posture, but they can’t always see exposed cloud assets, leaked credentials, or infrastructure linked to active campaigns.
Bringing in outside threat detection, such as with CybelAngel, strengthens every Zero Trust decision and reduces the chance of unknowingly granting access to a compromised user or endpoint.
Zero Trust use cases for real-world environments
Zero Trust becomes useful the moment your environment grows beyond a single, predictable network. Most CISOs now oversee cloud platforms, SaaS, remote teams, and a mix of managed and unmanaged devices. NIST outlines several scenarios where Zero Trust improves control and reduces uncertainty, especially in distributed setups.
Common use cases include:
- Remote work: Granting secure access without routing everything through a VPN, as shown in NIST’s remote employee model (p. 23–24)
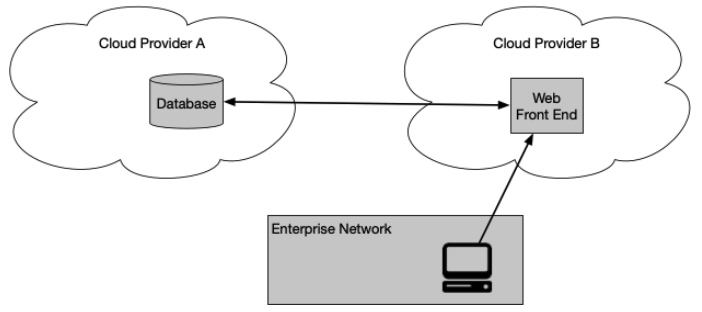
- Multi-cloud and hybrid environments: Ensuring consistent segmentation and workload protection across cloud-based providers
- API-to-API and service interactions: Verifying workloads before allowing east–west traffic
- Protecting sensitive information: Creating tight controls around high-value data
- IoT devices and unmanaged endpoints: Allowing connectivity without exposing core assets
- Containment after a breach: Limiting the spread of a cyberattack through microsegmentation
- Cloud service access: Enabling users to reach corporate services directly without relying on the traditional perimeter
These use cases show how Zero Trust adapts to the realities of modern environments instead of assuming a fixed, internal network. Visit pages 23-28 of the NIST Zero Trust cybersecurity outline to see the full breakdown.
Common misconceptions about Zero Trust
Zero Trust often sounds heavier than it is. Several assumptions tend to get in the way:
- It does not require removing VPNs; it reduces the reliance on them.
- It is not a single product you can buy.
- It does not demand a full infrastructure rebuild.
- It does not harm user experience when designed well.
- It does not abandon perimeter security; it simply shifts focus to the resource level.
If IT teams adopt a clear Zero Trust strategy, they can avoid these pitfalls and keep the model practical.
The benefits of adopting a Zero Trust security model
The main value of Zero Trust is control.
It gives security teams a way to make access decisions based on identity, posture, and context instead of relying on broad trust zones.
It also reduces the impact of unauthorized access by shrinking the attack surface and introducing predictable access paths across cloud services and internal systems.
For many CISOs, the most tangible benefit is operational consistency. They get one set of access controls that applies to endpoints, applications, and workloads across the organisation.
How to start building a Zero Trust strategy
A Zero Trust strategy takes shape by understanding who interacts with your systems and what they need to reach. NIST recommends starting with a clear view of your actors (people, services, and machines) and the assets they depend on. Once you know the data flows, you can define access policies that reflect real business needs and rank them by risk.
From there, choose a workflow that’s small enough to test but important enough to matter. Deploy Zero Trust controls around that flow, monitor how it behaves, and expand gradually. This step-by-step approach avoids disruption and builds confidence as each segment becomes more predictable.
Where external threat intelligence strengthens Zero Trust
Zero Trust depends on strong, reliable signals. Internal tools confirm identity and device posture, but they don’t reveal what’s happening beyond your perimeter. That gap matters when attackers exploit exposed cloud storage, forgotten assets, or leaked credentials.
External threat intelligence fills those blind spots.
CybelAngel identifies risks such as misconfigured cloud resources, shadow APIs, sensitive data exposures, and dark web activity tied to your environment.
These insights feed directly into access decisions, helping you reduce implicit trust and reinforce authentication, policy enforcement, and overall security posture.
Conclusion: ‘Never trust always verify’
Zero Trust lets you apply security measures across cloud services, the corporate network, and remote access workflows. By grounding each decision in identity verification, device posture, and context, it strengthens the function of your existing controls and reduces the likelihood of data breaches.
Strong external visibility makes this model far more effective against modern cyber threats. With CybelAngel providing outside-in intelligence, your security team can validate trust decisions with greater confidence and detect risks that traditional tools can’t see.
You’ll end up with a more resilient, predictable, and secure approach to protecting your organisation.

