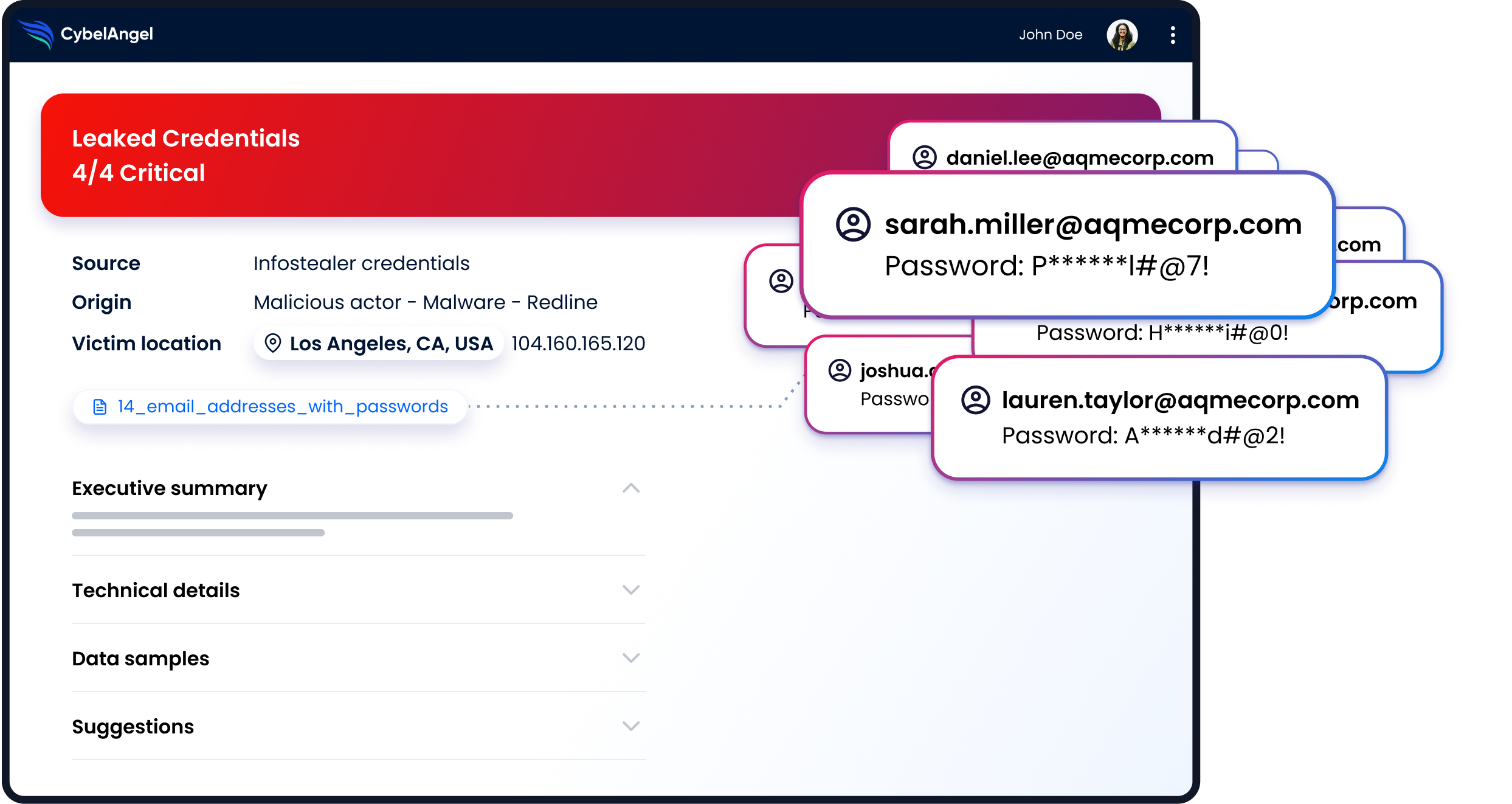
CybelAngel proactively stops the purchase of stolen credentials on the dark web
Discover
- Infostealer credentials, including logins, passwords and navigation cookies
- Exposed API keys & tokens on code repositories
- Unprotected emails & passwords stored on misconfigured databases and servers
Verify
- Contextualized incident reports redacted by a dedicated analyst
- Access to email and password in clear text, IP addresses, date of extraction and platform URLs, etc
- Extended integration options via connectors and RestFUL APIs
Protect
- Prevent multi-million-dollar account take-overs
- Automate remediation through your SOAR and Active Directory
- Stop purchasing stolen credentials on the dark web to take them off-market
“CybelAngel gives us a significant time advantage. They are the only solution to report credentials leaks way before they end up for sale on the dark web. This has proven critical for our VIPs.”