Decoding Scattered Spider’s Latest Messaging [Flash Report]
Table of contents
This blog is a summary of our analysis of recent messages from the threat group Scattered Spider. Interested in our full threat intelligence reporting? Get in touch with us to access this content.
What is Scattered Spider?
Scattered Spider is a highly adaptive cybercriminal group known for targeting large companies and their IT help desks. Also known by aliases like UNC3944, Oktapus, and Muddled Libra, this group specializes in data theft for extortion and has recently been observed deploying ransomware. The FBI and CISA, along with international partners, have been tracking Scattered Spider’s evolving tactics, which blend sophisticated social engineering with technical expertise.
The group’s primary method of attack involves elaborate social engineering schemes.
Scattered Spider threat actors often pose as a target company’s IT or help desk staff to trick employees into divulging credentials or running remote access tools. They are infamous for using techniques like:
- Vishing (Voice Phishing): Making phone calls to employees or help desks to convince them to reset passwords or transfer MFA tokens to a device controlled by the attackers.
- MFA fatigue: Sending repeated MFA push notifications until a targeted employee gives in and approves the request.
- SIM swapping: Convincing cellular carriers to transfer a victim’s phone number to a SIM card in their possession, giving them control over MFA prompts and account recovery.
Once inside a network, Scattered Spider actors are adept at “living off the land,” using legitimate remote management tools like AnyDesk, Splashtop, and TeamViewer to evade detection and move laterally. They also deploy information-stealing malware such as Raccoon Stealer and VIDAR Stealer.
Recently, the group has escalated its impact by deploying DragonForce ransomware to encrypt systems after exfiltrating sensitive data, adding another layer to their extortion tactics.
What do recent Scattered Spider’s messages tell us?
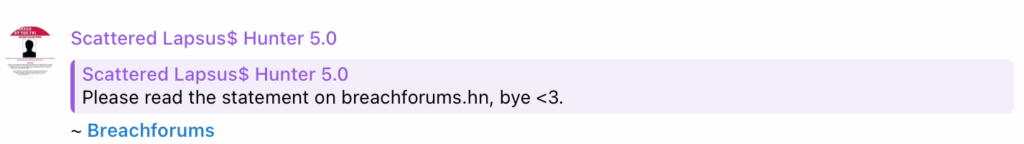
After a period of relative quiet following several high-profile arrests, Scattered Spider resurfaced on September 12th, 2025, with two cryptic messages posted on Telegram and a popular breach forum.
Decrypting Message 1
In its initial message, the group announced a supposed farewell, framing recent, widely reported intrusions—including those involving Jaguar, Google, and Salesforce—as mere “distractions.” They claimed these public attacks were designed to divert attention while they activated “contingency plans.”
The message hints that major, unreported breaches may have already occurred at global enterprises, specifically naming airlines like Air France and British Airways, as well as the luxury group Kering. While acknowledging the recent arrests of alleged members, the group dismisses them as “scapegoats” and claims to have shielded them from liability. The statement is designed to project an image of resilience and control, suggesting that even if the Scattered Spider brand goes silent, new data leaks from major corporations and governments will continue to appear. This tactic challenges the effectiveness of law enforcement actions and leaves organizations uncertain about the true extent of their compromise.
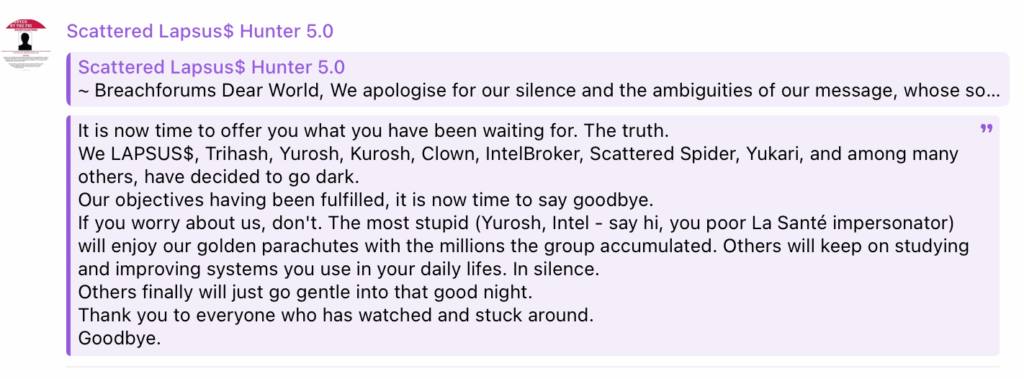
Decrypting Message 2
A subsequent message claimed to represent a coalition of well-known cybercriminal entities, including LAPSUS$, IntelBroker, and Scattered Spider. This post announced that the groups had collectively “decided to go dark,” stating their objectives were fulfilled. Messages suggested that members were either retiring on their illicit earnings, continuing their work quietly, or disappearing entirely.
While the message has a tone of finality, its credibility is questionable. Threat actor groups have a long history of “retiring” only to rebrand and resurface later with new names and refined tactics.
Wrapping Up
The latest messages from Scattered Spider are subtle but masterful in psychological warfare. Whether they signal a genuine exit, a strategic rebranding, or simply an attempt to mislead law enforcement, they underscore the group’s sophisticated understanding of narrative control. The hints of undisclosed, large-scale breaches are a clear threat intended to create fear and uncertainty among potential victims and security professionals.
Follow Scattered Spider‘s next moves with our cyber risk investigative content here on our blog.
Get in touch
If you are not a client but wish to have a complete picture of this threat actor and their evolving TTPs, you can obtain access to our full intelligence reports by getting in touch.

