Reviewing Pharmaceutical Threats in 2025 [Threat Note]

Table of contents
This blog is a summary of our latest threat landscape report, “Latest Cyber Threat Dynamics in the Pharmaceutical Sector.” Interested in reading the full report? Get in touch with us to access this content.
What’s happening in pharmaceutical cybersecurity?
The pharmaceutical sector has become a high-priority target for a range of cyber adversaries in 2025. An analysis of 172 recorded incidents between January and late September 2025 confirms that the industry is dominated by data-centric cybercrime, with threat actors keenly focused on monetizing valuable research data and regulated intellectual property.
Ransomware stands out as the single most significant threat, accounting for 29.1% of all attacks, closely followed by data breaches at 26.7%. Other notable threats include DDoS attacks (16.9%), the sale of initial access credentials (14%), and website defacements (13.4%). This landscape underscores the immense value threat actors place on the sector’s sensitive data, which includes proprietary research, clinical trial documentation, and employee credentials.
The ransomware ecosystem
Ransomware remains the most prevalent threat, with 50 incidents recorded since January 2025. The broader healthcare sector, which includes pharmaceuticals, is now the fourth most-targeted industry globally for ransomware, showing a 4.8% increase in attacks compared to 2024.
Key ransomware operators have demonstrated a sustained operational focus on this vertical, employing double-extortion tactics that combine data theft with system encryption.
The most active groups targeting pharmaceutical organizations are:
- Qilin (9 incidents)
- INC Ransom (5 incidents)
- Cl0p (4 incidents)
Both Qilin and INC Ransom have shown a persistent high likelihood of targeting pharmaceutical and healthcare ecosystems. In contrast, Cl0p’s intrusions have been largely opportunistic, driven by the mass exploitation of the MOVEit Transfer vulnerability (CVE-2023-34362). Across all groups, the United States is the most targeted geography, reflecting the high concentration of valuable pharmaceutical assets.
A multi-faceted threat: Espionage, hacktivism, and insiders
Beyond ransomware, the pharmaceutical sector faces a complex mix of other significant threats.
State-sponsored espionage
State-linked groups are actively targeting the sector to collect intellectual property and R&D data.
One notable campaign in 2024:
- Was attributed to the China-aligned group Green Nailao
- It exploited a vulnerability in Check Point Security Gateways (CVE-2024-24919)
- It did this to extract credentials and pivot into VPNs.
While no direct intrusions into pharmaceutical networks were confirmed, the campaign hit several European healthcare organizations, highlighting the risk posed by shared technologies across the interconnected health ecosystem.
Episodic Hacktivism
Hacktivist disruptions saw a 53% year-over-year increase, with 52 incidents recorded.
These attacks included:
- 25 DDoS attacks
- 23 defacements
They were symbolic and short-lived.
Pharmaceutical companies were not deliberately targeted for their sector but rather became collateral damage in broader, country-focused campaigns related to geopolitical tensions, such as the Israel-Hamas and India-Pakistan conflicts.
For example, in August 2025, the pro-Palestine group RuskiNet claimed a DDoS attack against Rafa Laboratories, an Israeli pharmaceutical company, as part of its politically motivated operations.

Initial access and the insider threat
The cybercrime economy is heavily supported by Initial Access Brokers (IABs), who sell footholds into corporate networks.
Our REACT found that in 2025 so far:
- 28 listings advertising unauthorized access to pharmaceutical firms were identified, with a focus on entities in India and the United States.
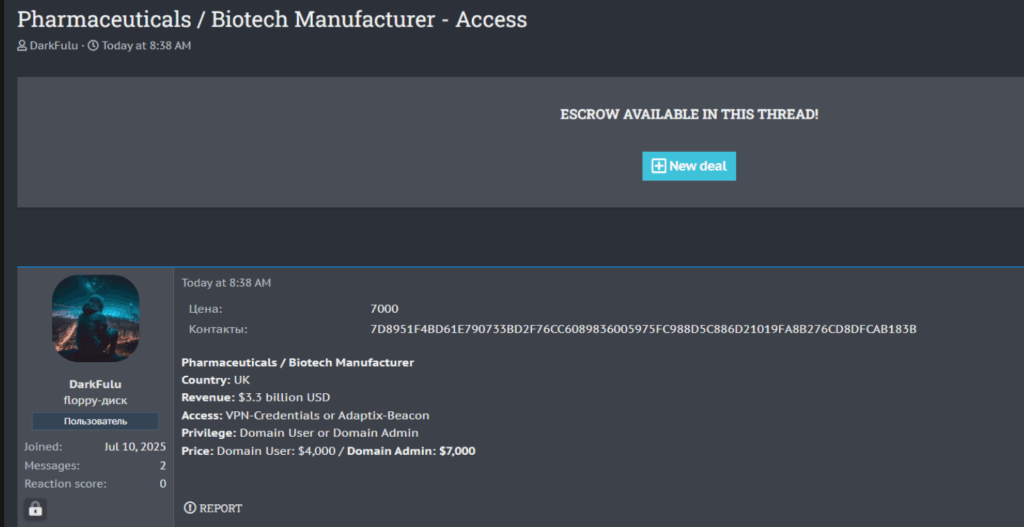
This market for credentials, whether sold by external brokers or malicious insiders, provides a cost-effective entry point for ransomware affiliates, as well as espionage operators.
Wrapping up
The pharmaceutical sector faces a hybrid threat environment where financially motivated ransomware gangs, state-sponsored spies, and opportunistic brokers converge to perpetuate huge damage.
The high value of the industry’s IP ensures it will remain a prime target. Adversaries are successfully exploiting both technical vulnerabilities in widely used enterprise software and identity-based weaknesses, such as compromised credentials. Defending against this diverse array of threats requires a multi-layered security strategy focused on hardening the perimeter, ensuring identity integrity, and managing supply-chain risk.
Get in touch
If you are not a client but wish to have a complete picture of this threat landscape, you can obtain access to the full report by getting in touch.

