
UX Designers Join the Ranks of Cyber Security Heroes
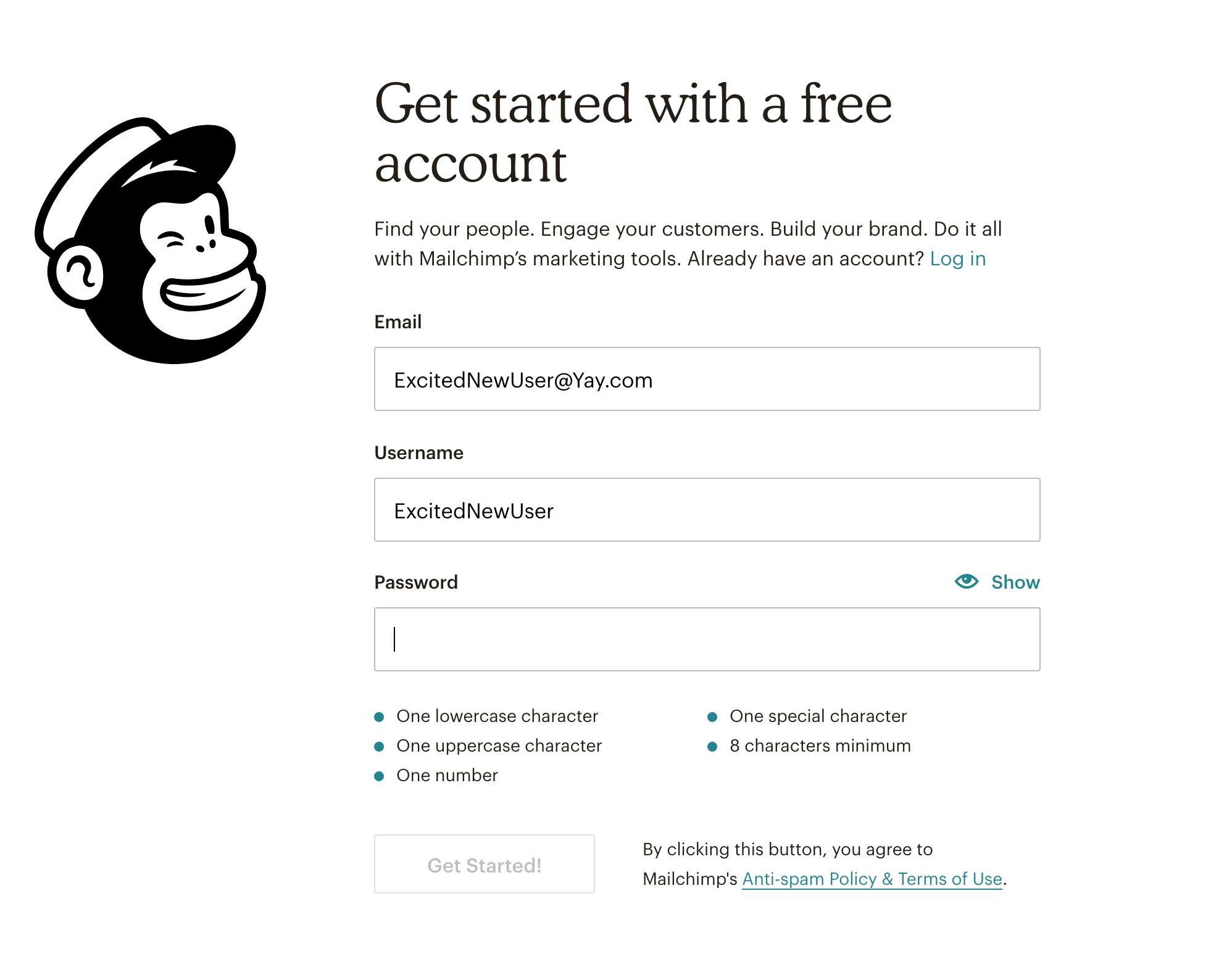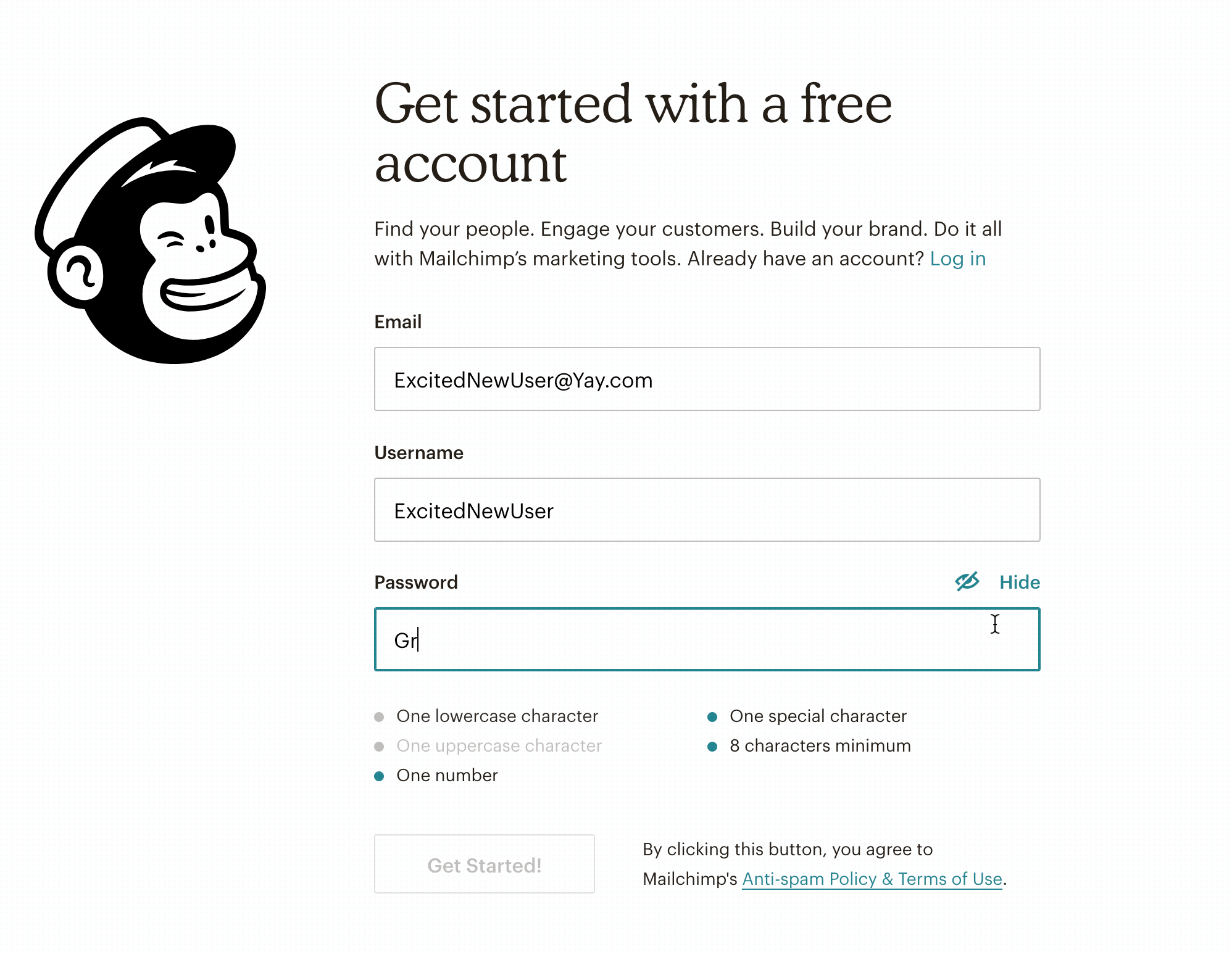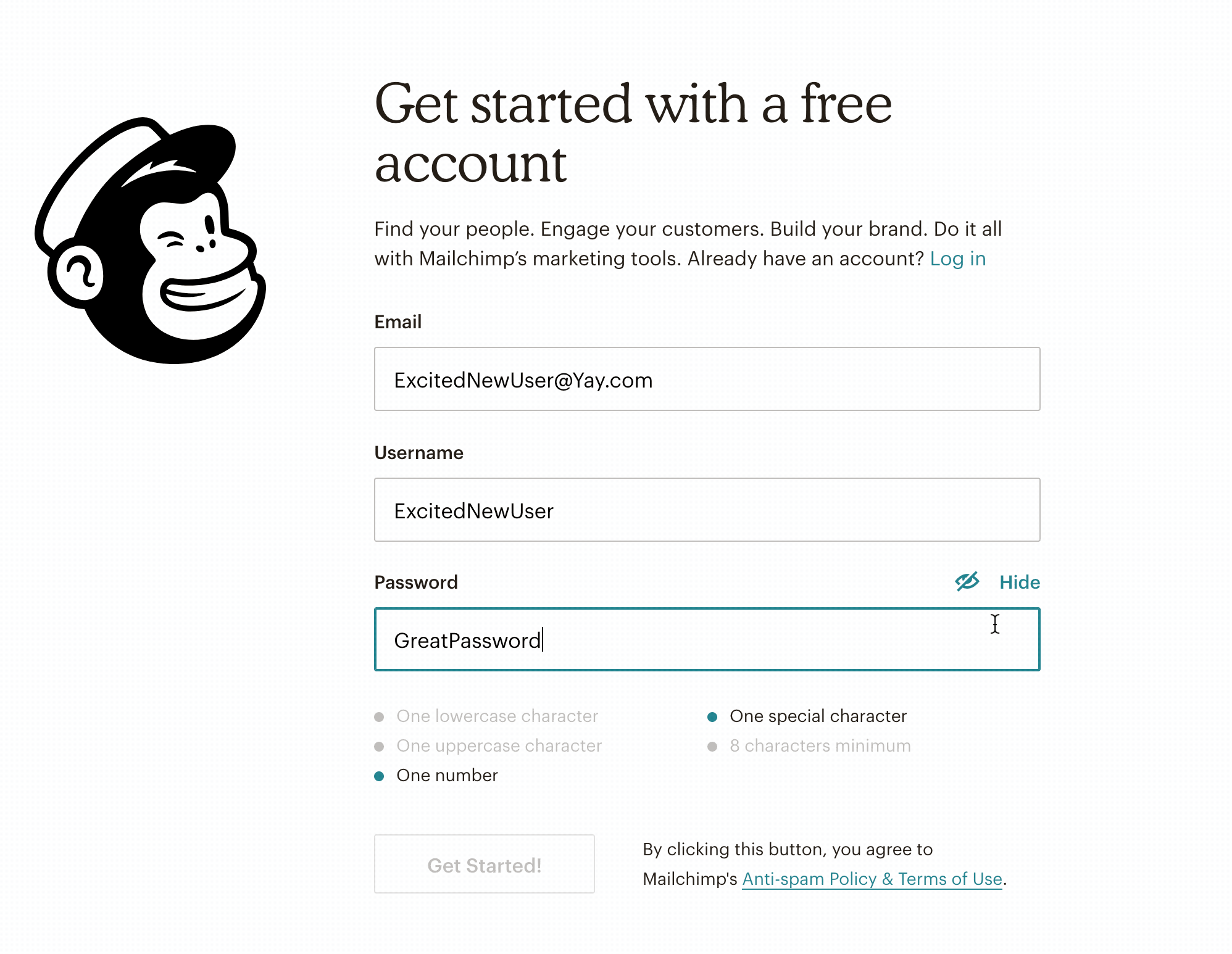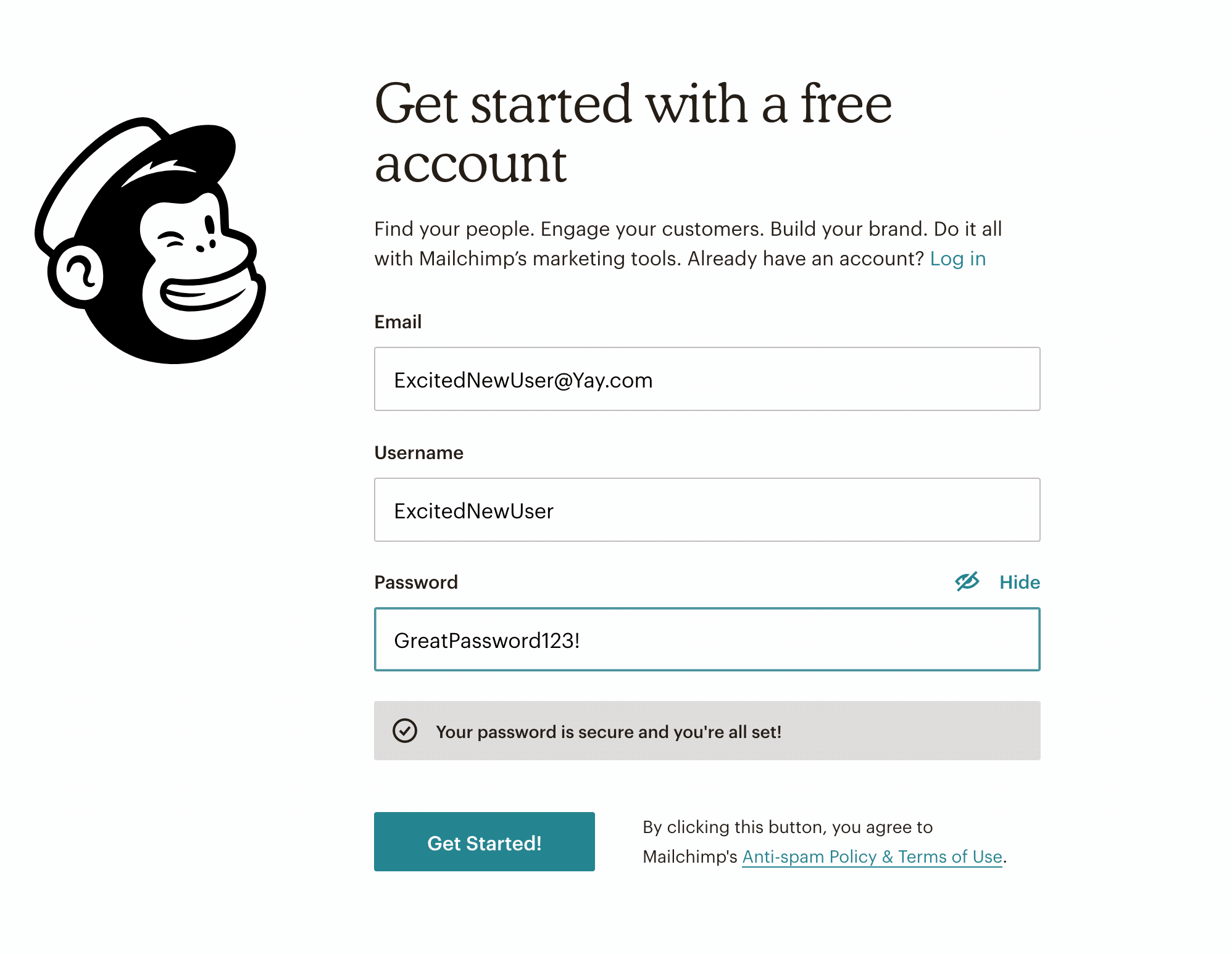
At first glance, an enjoyable user experience (UX) and a strong cybersecurity posture don’t seem to go hand in hand. UX is all about designing a smooth workflow for users and facilitating their actions within an interface. Cybersecurity’s prime concern is the safety of connected systems. Who amongst us hasn’t struggled to log in to a website, trying to remember a complex password that was required by the website’s security conventions? But does cyber security really have to stand in the way of a good user experience? Couldn’t we look at UX as a tool to create more security online? There are several ways to tackle this question, but we’ll focus on one of users’ biggest pain points: authentication. Can we use UX to ease the burden of setting and submitting long, complex passwords? Setting a strong password often feels like a hassle to users, especially when special characters are required. But some products have found ways to make this process simpler. For instance, MailChimp uses a system in which required password criteria are grayed out as the password being set satisfies those criteria.
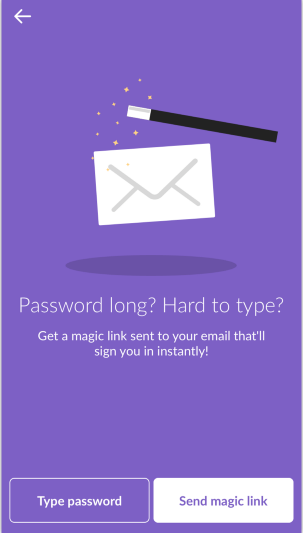
Slack has another good system: the magic link. If a user doesn’t wish to go through the painful process of entering and remembering their password, they can click the “Send magic link” button to receive an email with a link that will log them in immediately.
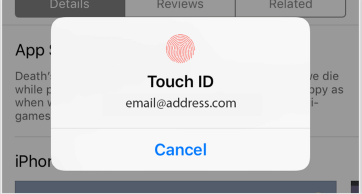
Face ID and Touch ID are also new practices, designed for logging on to your phone. Authentication of phone users is a crucial issue, as on average people log on to their phone about 80 times per day, according to an Apple study. A login process used this frequently must be as seamless as possible.
The innovations highlighted above are interesting solutions to the problem of needing greater security without creating a painful process for users. When designing authentication for a product, UX designers must ensure a pleasant experience. If you neglect your users’ experiences, you may end up with a secure tool, but one with an unhappy user base that could abandon your product or find creative ways to bypass your security features. But even the most pleasing UX may not mitigate what is arguably the most problematic password vulnerability: the use of a single password across all of a user’s accounts. UX designers haven’t yet managed to successfully compel users to use different passwords for all of their accounts. Despite the development of password managers (e.g., 1Password, LastPass, Dashlane), too many companies do not use them, and their employees still use a single password for every account. And that single password is used across all of a user’s professional and personal accounts, including their social network and e-commerce accounts. Although 90% of people know the dangers of reusing a password, 59% of them still do it anyway, according to a poll by LastPass. The dilemma is that not all of the websites a user keeps a common password for have the same cybersecurity posture. So if a password leaked from a user’s personal account on a social network with lax security standards is the same password that the user maintains for their professional email account with their enterprise employer, then any threat actor that obtains that password suddenly becomes very dangerous. Threat actors can use that password to access the employee’s professional account and impersonate the employee in order to launch phishing or fraud campaigns. Such threat actors might send messages to colleagues requesting sensitive information, or send corrupted emails that will spread a virus within the employer’s network. The consequences of these campaigns can be immensely costly. The hope is that thoughtful UX design will continue to make secure password creation so easy that users will be more inclined to create strong yet unique passwords for every account they keep. And with the assistance of password managers, recalling and submitting such strong passwords becomes less of a chore. Given the level of damage associated with the threat campaigns contemplated above, it’s fair to say that not all cybersecurity heroes spend their days in the security operations center hovering over SIEM tools, but instead they may be found in the creative department, prototyping the next authentication innovation that helps users help themselves to stronger cybersecurity stances.