Build Stronger Security with MITRE ATT&CK

Table of contents
Learn more about tactics, techniques, and procedures.
MITRE techniques and tactics have been used by organizations to improve their security posture since 2013.
ATT&CK evaluations provide security teams a fighting chance against malicious actors aiming to take control of an organization‘s internal systems.
Here‘s a quick and simple overview of how MITRE security solutions can protect your business and prevent gaps that expose the organization to threats.
1. What is MITRE ATT&CK?
The MITRE Corporation is a US-based not-for-profit organization that provides objective, cost-effective solutions to help businesses address cyber attacks. MITRE has developed an open-source knowledge base of adversary tactics and techniques based on real-world observations.
2. What does ATT&CK stand for?
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
The framework records and organizes adversary tactics, techniques, and sub-techniques to establish a common language that security professionals can use to mitigate risk.
Here‘s a quick overview of the areas covered by the framework:
- Adversarial tactics: Strategic approaches used by malicious actors to compromise systems, networks, or data.
- Techniques: The methods used by adversaries to achieve their goals.
- Common knowledge: Industry-wide cybersecurity practices for stopping attacks.
3. What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework refers to the knowledge base of techniques attackers use at different stages of a cyberattack, while the MITRE ATT&CK Matrix refers to the visual representation of the adversary techniques.
The MITRE ATT&CK Framework visually highlights the tactics (what the attackers are trying to accomplish) and outlines techniques used (how malicious actors achieve their goals).

The matrices display threat intelligence arranged by attack stages—initial system access to data theft or machine control. MITRE matrices can be used across various operating systems including Windows, MacOS, and Linux.

Within the framework, each ATT&CK tactic, technique, and sub-technique also has a related code. This simplifies communication and removes the risk of miscommunication in escalating attacks.
4. What are the 3 main components of the MITRE ATT&CK methodology?
The ATT&CK methodology is used to improve incident response time. ATT&CK tactics and techniques are used rather than the indicator of compromise (IoC) to improve the organization‘s security posture.
There are 3 matrices that businesses can follow:
- Enterprise ATT&CK: The Enterprise matrix is used for a larger corporate network environment. The extensive matrix prioritizes network defense within the tactics, techniques, and procedures (TTPs) attackers can use to gain entry. Security professionals can gain a foothold in the network and move laterally without being detected to protect the most valuable data and systems.
- Mobile ATT&CK: This matrix describes the strategies used by cyber adversaries to infect iOS and Android mobile systems. ATT&CK for Mobile documents incidents that occur without direct access to the mobile device.
- ICS ATT&CK: The ICX Matrix is used for attacks on industrial control systems (e.g. machinery, devices, sensors, and networks) used to monitor operations for factories, utilities, transportation systems, and other critical service providers.
5. How can organizations implement the MITRE ATT&CK framework to improve their cybersecurity defenses?
Mitigation of threats is crucial to protect the organization from the weaponization of data. MITRE provides organizations with a clear overview of techniques and tactics to address common cybersecurity breaches.
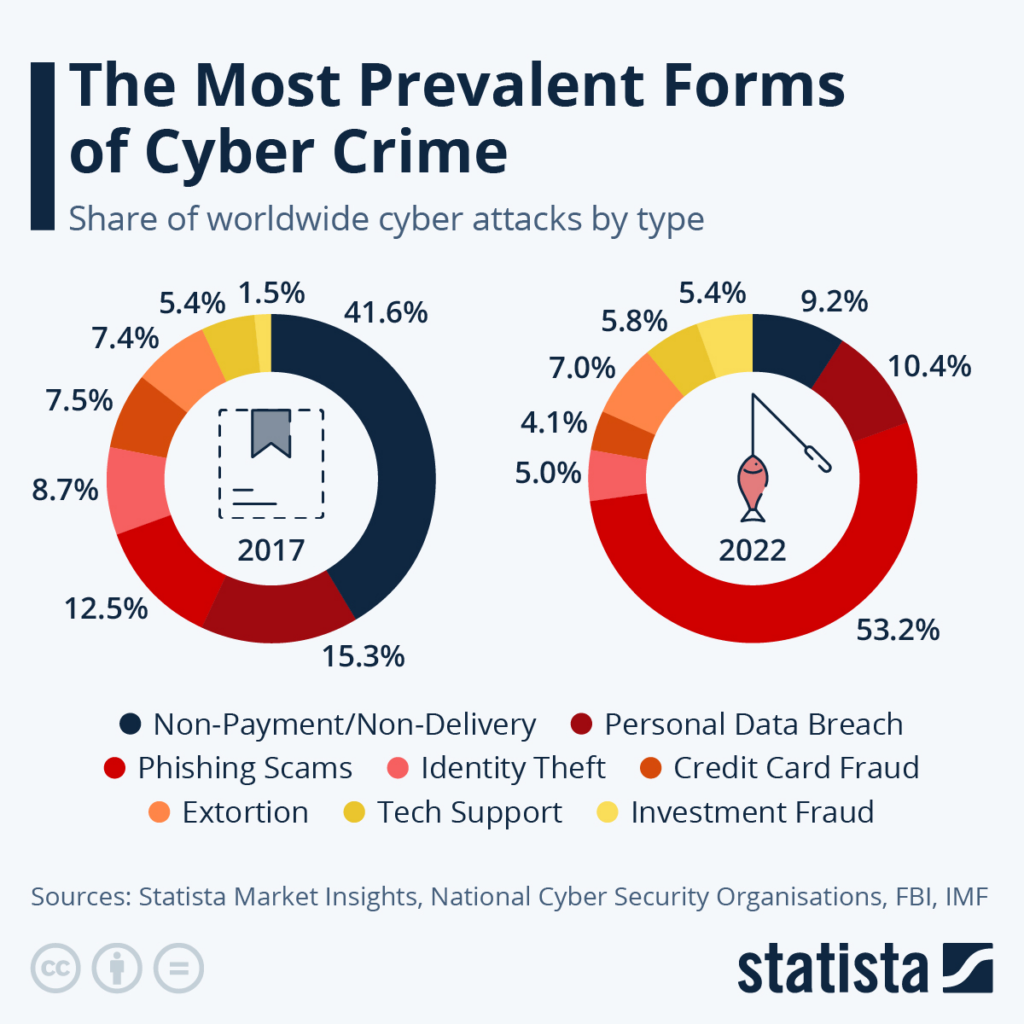
For example, phishing is one of the most prolific and effective adversarial tactics that has risen in recent years. In 2017, phishing attacks only accounted for 12.5% of cyberattacks. In 2022, this rose to 53.2%, becoming the third most popular cyberattack globally.
In France, 71% of organizations surveyed said they had experienced a targeted spear phishing attack in 2023. Chief Information Security Officers (CISOs) surveyed in the US in 2024 said 9 in 10 organizations were at risk of a material cyberattack in the next 12 months.
Cyber threat intelligence becomes crucial for organizations to protect themselves against the rise in phishing-related threats. MITRE provides specific techniques and tactics to ensure that an attack like phishing doesn‘t hinder daily operations.
In one case, ATTACK techniques enabled the security team to detect suspicious activity on its HR platform. Threat actors had used spear phishing to gain access to the company‘s internal systems to extort funds. The actor infiltrated the verified user account to modify payroll information and used several proxy servers and randomized user agents to avoid detection.
Using the ATT&CK Framework, the organization was able to prevent theft of funds from employees’ payrolls and patch up the entry points used by the attackers.
According to statistics, 60% of businesses worldwide in 2024 stated their level of readiness against cybersecurity threats to be at a formative stage. The drastic rise in attacks like phishing makes it more important than ever for companies to protect themselves against malicious actors.
6. The benefits of protecting your tech ecosystem with MITRE ATT&CK
MITRE can support organizations to ensure that risk is minimized through each phase of the cyberattack lifecycle. To stay ahead of adversary behavior and track vulnerabilities, companies must have a clear and logical way of tracking and solving threats before they snowball.
An X post from Corporate Vice President, Security Fellow at Microsoft, John Lambert. Source.
For the Bank of International Settlements (BIS), an active plan of attack was needed to stay ahead of DeFi attacks that threatened to destabilize the financial industry. In 2021 alone DeFi attacks cost the industry almost $1 billion.
A graph showing that DeFi-related hacks rose from $129 million (2020) to $1 billion (2021). Source.
In 2023, the BIS rolled out a comprehensive seven-point strategy called Project Polaris using the MITRE ATT&CK Matrix, to help prevent DeFi cyber hacks. Analysis of past cyber attacks revealed gaps in security attack modeling systems. Over time, compounding threats to the BIS could erode public confidence in the new currencies, central banks, and the wider financial system.
To build up their security operations, they utilized the MITRE framework to:
- Understand the new threat landscape.
- Adopt modern enabling technologies to support security and resilience.
- Identify areas of improvement and new capabilities to be implemented.
The MITRE ATT&CK Framework was agile enough to enable the organization to find solutions to specific threats and tailor solutions to each unique case in the evolving threat landscape.
FAQs
What are the tactics listed in MITRE ATTACK?
There are currently 185 techniques and 367 sub-techniques in the Enterprise ATT&CK matrix, with updates being continuously added.
A tweet from MITRE ATT&CK sharing the latest updates to the database. Source.
To assist in identification, MITRE has a unique four-digit code to distinguish each tactic and technique. Within a security team, these unique codes make communicating threats efficient so they can be more easily dealt with.
The tactics covered in the ATT&CK Matrix for Enterprise include:
Reconnaissance: Gathering information for planning an attack.
Resource development: Establishing resources to support attack operations.
Initial access: Penetrating the target system or network.
Execution: Running malware or malicious code on the compromised system.
Persistence: Maintaining access to the compromised system (in the event of shutdown or reconfigurations).
Privilege escalation: Gaining higher-level access or permissions (e.g., moving from user to administrator access).
Defense evasion: Avoiding detection once inside a system.
Credential access: Stealing usernames, passwords, and other login credentials.
Discovery: Researching the target environment to learn what resources can be accessed or controlled to support a planned attack.
Lateral movement: Gaining access to additional resources within the system.
Collection: Gathering data related to the attack goal (e.g., data to encrypt and/or exfiltrate as part of a ransomware attack).
Command and control: Establishing covert/undetectable communications that enable the attacker to control the system.
Exfiltration: Stealing data from the system.
Impact: Interrupting, corrupting, disabling, or destroying data or business processes.
What are MITRE ATT&CK Techniques?
MITRE ATT&CK techniques are specific techniques used by the threat actor during an attack. Each tactic mentioned in the framework has corresponding techniques based on real-world scenarios. Each technique has:
- A description and overview.
- Known sub-techniques that may fall under a larger umbrella technique. E.g. Phishing includes spear phishing by attachment, by link, and by service.
- Related procedures for stopping an attack such as alerting to types of malicious software used to perform the technique.
- Mitigation of threats such as user training or antivirus software.
- Improves detection of threats such as log data or system data to monitor the success of a particular technique.
What is the MITRE ATT&CK Navigator?
The ATT&CK Navigator is a web-based tool for annotating the ATT&CK matrices. It can be used to visualize defensive coverage, assist in red/blue team planning, and address the frequency of detected techniques within the organization.

Security teams can:
- Visualize the “why” behind an attack with annotation tools such as color coding, highlighting, and filtering.
- Create custom layers on top of the ATT&CK matrix to represent different data points, such as detected techniques, gaps in detection, or attack paths.
- Collaborate with teams across locations in one centralized place.
- Map detections across the organization to mitigate threats.
What are some popular MITRE use cases?
MITRE ATT&CK includes activities that organizations can utilize to optimize internal security operations.
Here are some popular use cases for MITRE ATT&CK:
- Alert triage, threat detection, and response. Prioritize the mountains of information that security professionals would usually have to sift through in a typical enterprise network. For example, MITRE ATT&CK can assimilate information from EDR of endpoint detection and response, to speed up incident response times.
- Threat hunting. Threat hunting is a proactive exercise where security professionals search the network for incoming threats. MITRE ATT&CK provides many “jumping off” points for security teams, making starting or continuing a threat hunt easier.
- Red teaming or adversary emulation. To educate employees about the dangers of cyber attacks, security professionals can engage in red teaming or adversary emulation to simulate a real-world cyberattack. These internal activities help organizations measure the preparedness of people, policies, and practices while helping to identify vulnerabilities.
- Security gap analysis and security operations center (SOC) maturity assessments. Security gap analysis evaluates how an organization’s current cybersecurity practices align with industry standards, whereas a SOC assessment provides a score that measures the organization’s effectiveness in mitigating cyberattacks. MITRE supports security operations centers in performing round-the-clock monitoring of the network environment to identify and address threats.
What is the difference between NIST and MITRE?
NIST is an alternate framework that also helps organizations to defend themselves against cyberattacks. While both NIST and MITRE share the goal of empowering organizations to defend themselves, the approach they take is different.
NIST focuses on helping businesses to standardize guidelines for organizational cybersecurity risk management. They blend outlined best practices with US compliance laws.
ATT&CK on the other hand provides actionable information for understanding and defending against specific cyber threats.
Both frameworks help organizations understand their adversaries better, test their networks for vulnerabilities, and set up countermeasures.
How is MITRE ATT&CK different from Cyber Kill Chain?
Developed by Lockheed Martin, Cyber Kill Chain is a model for identifying and preventing cyber threats with a focus on stopping each phase of an attack by “breaking the chain.”
Cyber Kill Chain differs from MITRE ATT&CK in the methods given to stop an attack. Lockheed Martin‘s platform claims all cyberattacks must follow a specific sequence of attack tactics to achieve success.
MITRE by contrast provides techniques and tactics for stopping attacks, but acknowledges that each case is unique and may require a different sequence of steps to stop an attack.
Final thoughts
Understanding the benefits of MITRE ATT&CK helps your organization stay one step ahead of cybercriminals. Security teams can be hindered by delays in response time or communication strategies costing the organization in damages.
Cataloging each threat, having a common language between teams, and proven techniques to combat attacks at your fingertips gives security teams an edge to quash attacks before they escalate.
Catch up with our annual report
Interested in more comprehensive threat analysis? Check out our brand new annual report written by our CISO Todd Carroll.

