DNS Spoofing: Why You Should Never Trust a Domain Name

Table of contents
The domain name system (DNS) is a fundamental part of the web. This system translates the characters in a website’s name (for example, cybelangel.com) into an IP address, allowing browsers to connect to website servers. Domain names are easier to remember than IP addresses and better for branding. However, s on an increasingly frequent basis. Phishing attacks are one enticing option used by hackers to steal sensitive data. The idea is simple: victims are redirected to fake websites which record confidential information such as passwords or bank details. Avoiding the pitfalls of phishing can be difficult. You must check the authenticity of the websites you are visiting – which is much harder than it sounds. It is no longer enough to simply look at the link being clicked on: recent progress in the web means that new characters can now be used in domain names, thanks to the inclusion of UTF-8 character encoding. As a result, the small A in facebook.com is indistinguishable from the Cyrillic character for A in fаcebook.com – but the websites are different. We discussed this issue and more in a previous article. 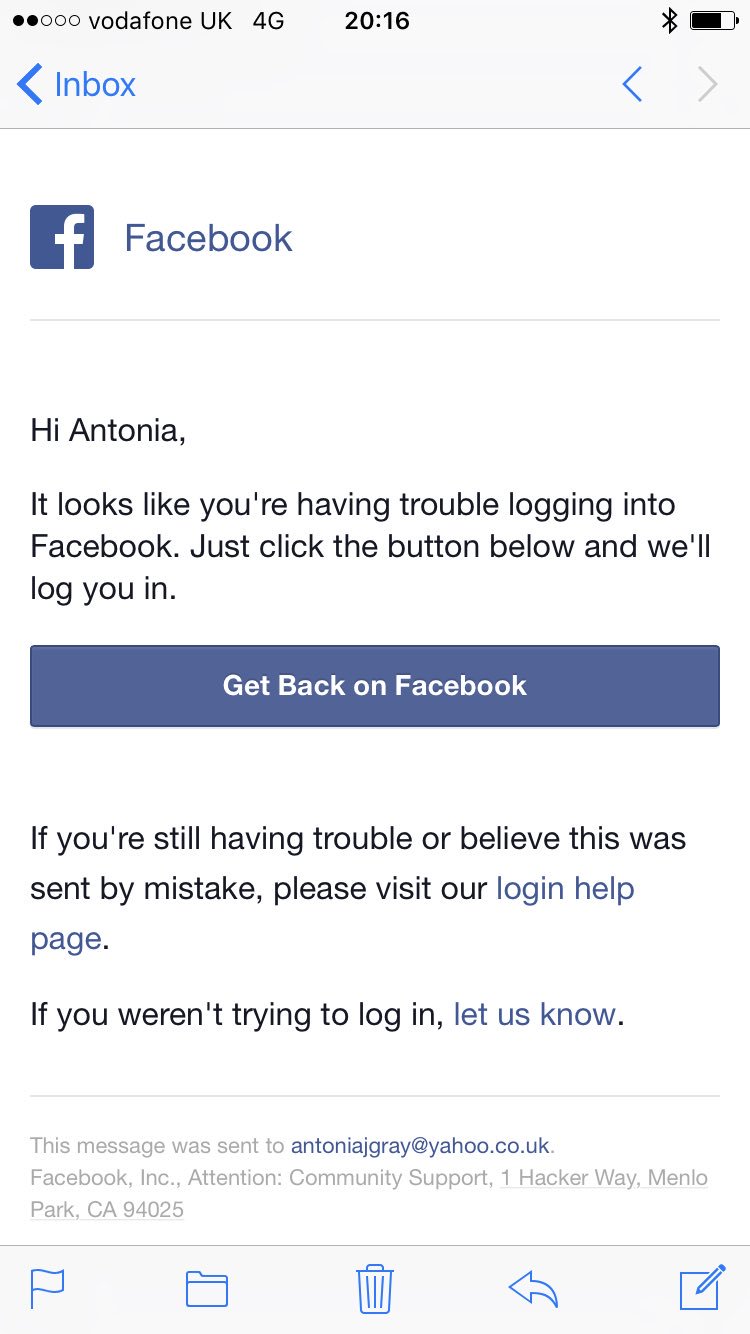 It is therefore easy to make mistakes. You must check the URLs in your browser’s navigation bar to get a better idea of whether websites are suspect.
It is therefore easy to make mistakes. You must check the URLs in your browser’s navigation bar to get a better idea of whether websites are suspect.
HTTPS: essential for sensitive data
Even if the URL in the navigation bar says you are on the right website, your computer may be mistakenly communicating with the wrong server. Malicious computers can place themselves between you and a server, intercepting your communications, especially when you are using public WiFi. The server changes the IP address of the website you are trying to visit by sending you a false DNS reply: the address is correct, but the IP is dangerous. To prevent this from occurring, you should use a secure connection to ensure that the server you are communicating with is the server you actually wish to send data to. HTTPS is a secure communication protocol which checks you are communicating with the right server by using asymmetric encryption keys.  If you do not use HTTPS, you could inadvertently send confidential information to a hacker who has compromised your DNS request.
If you do not use HTTPS, you could inadvertently send confidential information to a hacker who has compromised your DNS request.
Are emails trustworthy?
In emails, the ‘From’ field generally shows the sender’s identity. However, this field is easily modified, and should never be considered proof that the email is from a trustworthy source. To fight against spam and phishing attacks, the DNS system now provides information on the IP addresses that are authorised to send emails from the domain name concerned. This data is sent at the same time as information on the server’s IP address. Email providers use this information to determine whether email from an unauthorised IP address is spam. This helps circumvent a large number of phishing attacks. However, if the domain name is fake, and uses UTF-8 coding for example, this process does not work. It can be extremely difficult to determine whether the email address used to send the message is authentic. 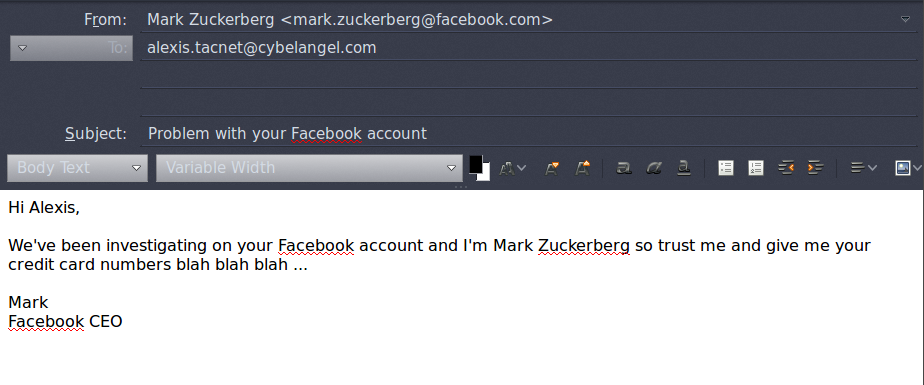 Conclusion: a secure protocol is still a long way off Despite initiatives like DNSSEC, which seek to better secure the DNS protocol, it is very difficult to change the system, given its fundamental importance in today’s world. In the meantime, never trust a domain name – they are far too easy to fake.
Conclusion: a secure protocol is still a long way off Despite initiatives like DNSSEC, which seek to better secure the DNS protocol, it is very difficult to change the system, given its fundamental importance in today’s world. In the meantime, never trust a domain name – they are far too easy to fake.
