Aerospace & Defense: 2024-2025 Cyber Threat Landscape [Threat Note]

Table of contents
This blog is a summary of our latest threat landscape report, “Latest Cyber Threat Dynamics in Aerospace & Defense.” Interested in reading the full report?
What threats are trending within the aerospace and defense cybersecurity?
The Aerospace and Defense (A&D) sector has become a primary battleground for geopolitical cyber warfare. Between September 2024 and September 2025, the industry was targeted by 879 claimed cyberattacks worldwide. This activity was overwhelmingly dominated by a massive wave of politically motivated Distributed Denial-of-Service (DDoS) campaigns, which accounted for over 76% of all incidents—more than double the cross-industry average.
This trend highlights how hacktivist groups are using the A&D sector as a symbolic target to amplify their messaging in response to global conflicts and political alliances. While less frequent, highly impactful threats like data breaches (14.2%) and ransomware (4.9%) continue to pose a severe risk, often exploiting the industry’s sprawling and interconnected supply chain.
The reality of key threat types: Ransomware, breaches, and supply chain risk
While hacktivism generates the most noise, financially motivated and espionage-driven attacks present a more significant threat to the A&D sector’s integrity.
Financially motivated campaigns are typically opportunistic rather than specifically targeting the A&D sector. However, when they do strike, the consequences can be severe due to the value of the intellectual property and technical data involved. For example, in September 2025, the
PLAY ransomware group claimed an attack on Edwards Interiors Inc., a U.S.-based manufacturer of high-end aircraft cabin interiors, threatening to leak corporate data.
The most systemic risk to the sector is its supply chain. Prime contractors are often well-defended, so threat actors target smaller, less secure suppliers and subcontractors as a way into the broader defense ecosystem. A notable example is the
Clop ransomware group’s compromise of Mazeres Aero Equipment, a French aeronautical supplier, in February 2025, which resulted in the exposure of operational and client data.
What the Naval Group case study can tell us about industry threats
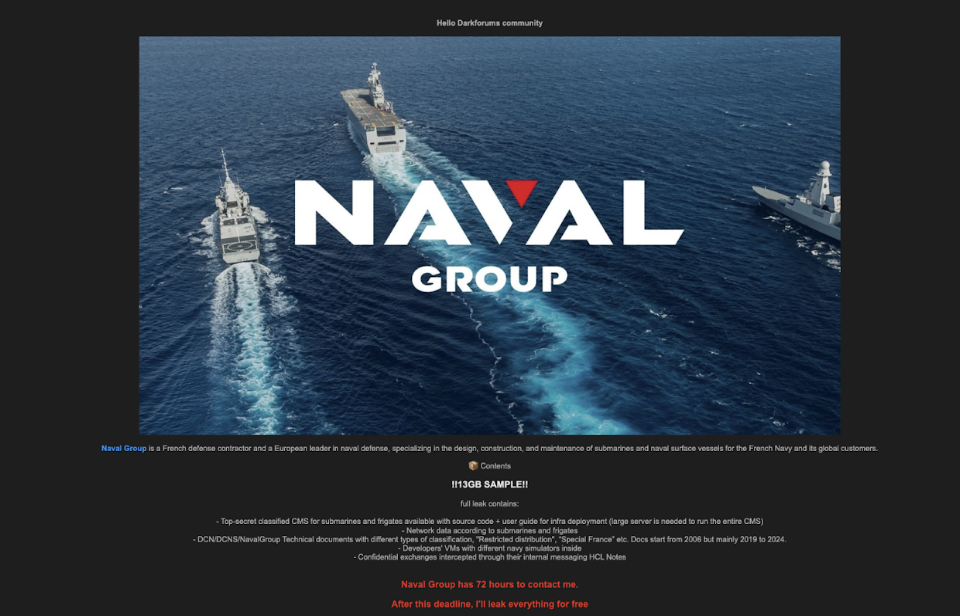
In July 2025, a new threat actor under the alias “Neferpitou” surfaced on a dark web forum, claiming to possess highly sensitive data from the major French defense contractor, Naval Group. The actor issued a 72-hour ultimatum before beginning to leak data samples allegedly containing:
- Source code for Combat Management Systems (CMS) for submarines and frigates.
- Proprietary material for the “STORM” weapon system.
- Developer virtual machines and network configurations.
- Documents classified as “Special France” or “Restricted Distribution”.
If authentic, this breach carries critical national security implications, potentially allowing adversaries to reverse-engineer and develop tailored cyber operations against French naval platforms. Interestingly, the pro-Russian hacktivist group
Noname057(16) also mentioned that its volunteers had compromised Naval Group in early July, suggesting a possible link to the incident.
Threat actor profiles
How can you better understand the muscle and mass behind these attacks? From high-volume hacktivists to sophisticated state-sponsored spies, these players have some things in common.
Hacktivists
Noname057(16)A pro-Russian hacktivist group formed in March 2022,
Noname057(16) is a primary driver of DDoS attacks against Ukraine and its NATO allies. Using its volunteer-based “DDoSia” toolkit, the group has relentlessly targeted French defense contractors in retaliation for military support to Ukraine. Between September 2024 and September 2025, France was the group’s third most targeted country.
Ransomware
Clop
Active since 2019 and associated with the Russian-speaking group TA505.
Clop operates a double-extortion model, stealing data before encrypting files. While opportunistic in its targeting, the group has impacted the A&D supply chain, notably with its compromise of Mazeres Aero Equipment.
Espionage
APT28 (Fancy Bear)
APT28 is a Russian state-linked cyber-espionage group that has been active for over two decades, targeting European and NATO entities for strategic intelligence. French authorities have confirmed APT28 intrusions against national ministries and defense industrial base firms, highlighting the persistent and sophisticated threat of state-sponsored espionage facing the sector.
Wrapping up
Our analysis shows that this sector is on the receiving currently caught in the crossfire of geopolitical cyber conflict. While high-volume DDoS attacks from hacktivists dominate headlines, the more severe and insidious threats come from state-sponsored espionage groups like APT28 and opportunistic ransomware gangs like Clop that exploit weaknesses in the supply chain. We detail more layered context and depth within
Get in touch
If you are not a client but wish to have a complete picture of this threat landscape, you can obtain access to the full report by getting in touch.
Contact Us
