The Complete Guide to Cyber Threat Intelligence

Table of contents
Threat analysis is becoming more important year over year. Phishing scams, ransomware attacks, and advanced persistent threat groups (APTs) continue to threaten data security around the world.
Gathering threat intel is one of the best ways organizations can protect themselves against attacks.
Cutting-edge threat intelligence tools and threat intelligence platforms (TIPs) combined with specialist guidance help organizations to process data to scale, securing vulnerable endpoints and preventing data breaches.
According to IBM, the cost of a data breach for the victim organization can be up to $4.4 million, with detection and escalation costs totaling $1.4 million. Prevention is always the most cost-effective solution.
In this article, we‘ll dive into how you can harness cybersecurity threat intelligence to build methodologies that stop attackers before they cause irreparable damage.
What is cyber threat intelligence?
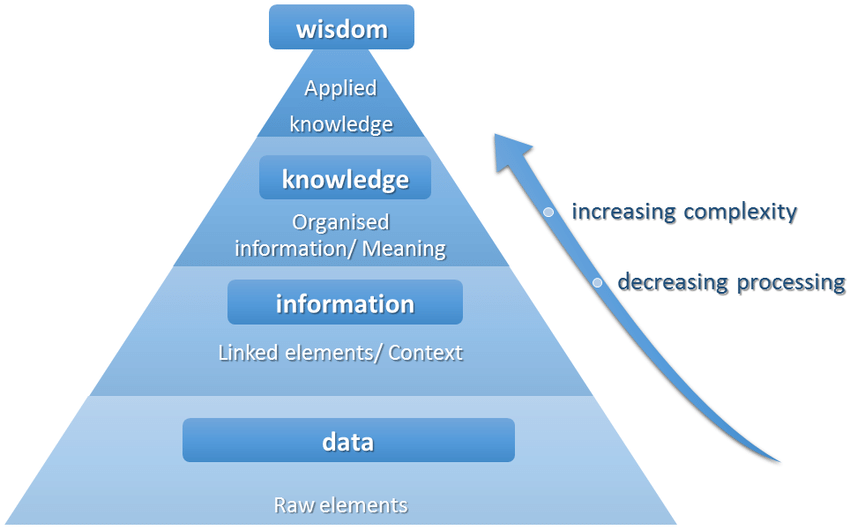
Cyberthreat intelligence is the process of collecting raw data and analysing it to enhance an organization‘s security posture. From the data collected, security professionals can create intelligence reports designed to overcome current and future threats within the threat landscape.
Understanding the Tactics, Techniques, and Procedures (TTPs) used by threat actors is an essential part of threat hunting—improving attribution and thwarting potential attacks.
What are the different types of threat intelligence?
Security teams use different types of threat intelligence to accomplish various goals throughout the organization.
Threat intelligence can help smaller companies to build comprehensive in-house security operations, often targeted by threat actors due to the perceived lack of security.
For larger organizations, threat intelligence can reduce costs and support large teams to gather information and implement effective security tools.
The three main types of threat intelligence include:
- Tactical threat intelligence: Focuses on predicting future attacks and threat detection. Tactical threat intelligence includes searching for indicators of compromise (IOCs) such as IP addresses used in phishing attacks and file hashes of malware attacks. Threat hunting also relies on tactical intelligence to pinpoint APT attacks and other hidden vulnerabilities.
- Operational threat intelligence: Aims to understand the behaviour of threat actors by looking at TTPs, various attack vectors, and the vulnerabilities they exploit. Operational threat intelligence involves real-time monitoring of networks and systems, utilizing actionable intelligence to develop security controls and mitigation strategies.
- Strategic threat intelligence: A high-level overview of intelligence that positions the organization within the threat landscape. Strategic threat intelligence provides C-level decision-makers with a better understanding of the cyber threats facing the organization.
Why is threat intelligence important?
Threat intelligence helps organizations turn raw data into actionable insights. Processed data is used to create in-depth intelligence reports that improve security operations and mitigate risk.
Starting with data, security professionals work to understand threats within the IT environment. With that context, high-level insights can be ascertained, helping C-level professionals make informed decisions.
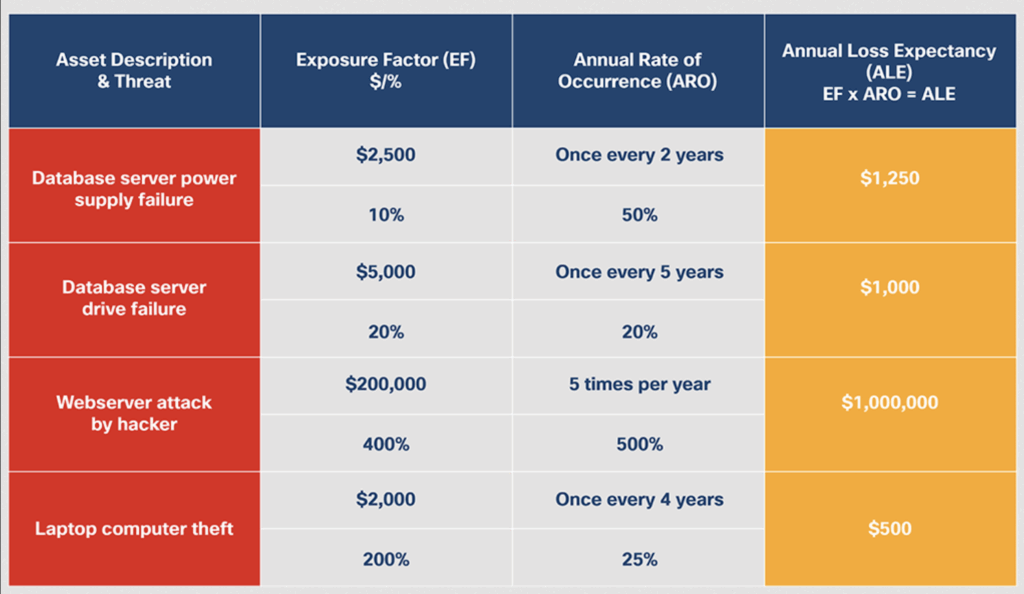
The cost of not having a CTI program can quickly rise, eating into profit margins. A new server can cost up to $20,000, not to mention the time drain on security professionals.
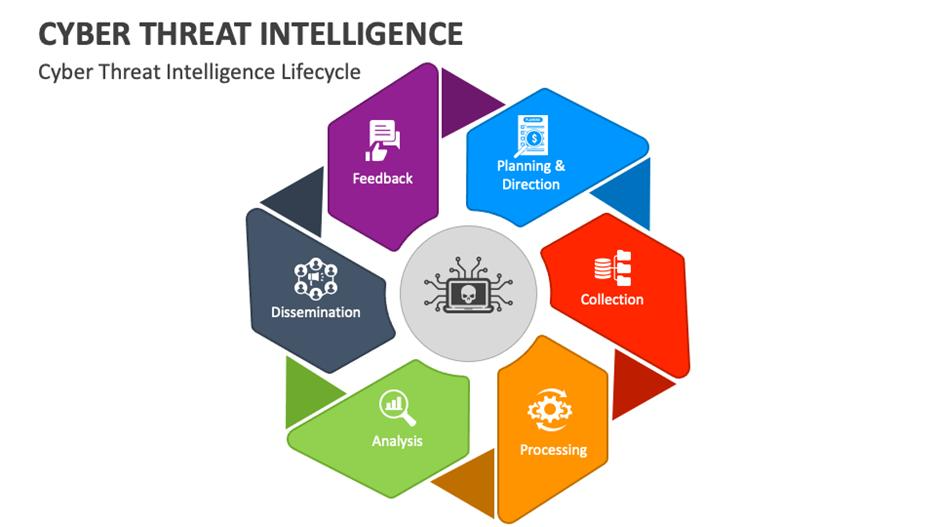
The threat intelligence lifecycle
The threat intelligence lifecycle is a process used in cybersecurity to manage threats. It helps organizations to manage specific threats within the attack surface.
During the threat intelligence cycle, cybersecurity professionals work together with relevant stakeholders to mitigate emerging threats by developing a cross-functional plan tied to measurable business objectives.
By concentrating on pertinent threats, the lifecycle reduces the impact of cyber attacks and creates a methodology for effective responses and improved cybersecurity posture.
1. Planning
Cybersecurity professionals first must set the foundation by planning the direction for the entire threat intelligence process.
It‘s important to consider:
- Stakeholders: Identify organizational decision-making stakeholders who will be effective in implementing intelligence efforts. Security teams will collaborate with stakeholders to define the threat intelligence program’s objectives and goals.
- Define assets, objectives, and scope: Determine which assets and data need protection to define the scope of intelligence efforts. From there, resources and budget can be allocated, along with Key Performance Indicators (KPIs) to define the project‘s success.
- Set priorities: Understanding the immediate threats that may impact your organization‘s IT ecosystem can help better direct the threat intelligence process. Prioritize based on previous cyberattacks and emerging threats.
2. Collection
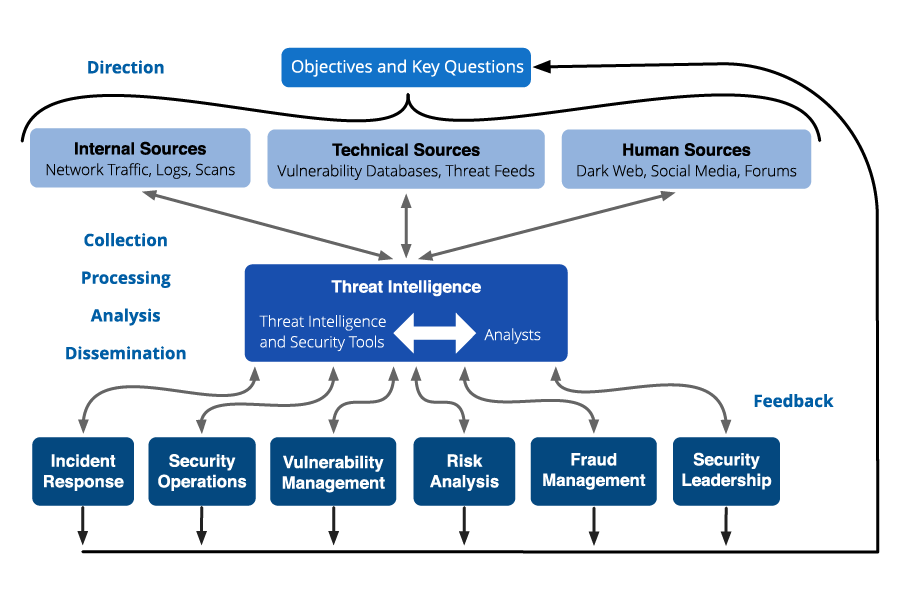
During the collection phase, organizations gather threat data from various sources identified during the planning phase. The collected data includes raw data that will need to be processed to address the intelligence requirements.
Threat intelligence collection should cover all available sources, including internal sources (logs, scans, and network activity), technical sources (threat feeds and databases), and human sources (social media, dark web, and internet forums).
| Source Type | Examples | Use Case |
|---|---|---|
| Internal Logs | Firewall, IDS/IPS, endpoint telemetry | Detect anomalies and internal threats |
| Open Source (OSINT) | News, blogs, social media, forums | Track emerging threats and public chatter |
| Commercial Feeds | Threat intelligence platforms (e.g., Recorded Future, Mandiant) | Enriched, curated threat data |
| Dark Web | Marketplaces, forums, breach dumps | Monitor criminal activity and data leaks |
| Human Intelligence (HUMINT) | Industry sharing groups, analyst networks | Contextual insights and early warnings |
| Technical Sources | Honeypots, malware sandboxes, scanners | Capture TTPs and IOCs |
3. Processing
The raw data collected in the previous phase can now be transformed into an accessible format for analysis. Data should be sorted, decrypted, and translated into a usable form.
When processing raw data, it‘s important to ensure all data is clean, removing any duplicate data entries or corrupted data that may have occurred during the data collection process.
Next, data should be converted into usable formats depending on the stakeholder group. For automation analysis, formats such as STIX, TAXII, JSON, and YAML can be used, while CSV formats are ideal for bulk imports and exports.
4. Analysis
The analysis stage aims to transform raw data into meaningful, actionable insights to make informed decisions and guide the organization‘s security posture.
Thorough analysis can identify vulnerabilities within the IT ecosystem, identify patterns and anomalies, and indicate where a potential data breach could take place.
Cybersecurity professionals should question:
- Are there correlations between different indicators of compromise (IOCs), events, or threat behaviors?
- Can the anomalies be attributed to a known threat actor group?
- How do the threats relate to the broader threat landscape?
- What is the risk of the emerging threats?
- How can professionals use the data to inform strategies to thwart adversary goals?
5. Dissemination
After analysing all relevant data, stakeholders can now be informed of the findings to steer the decision-making process.
Weekly or monthly threat reporting for relevant stakeholders and real-time feeds turns intelligence into actionable insights. Threat intelligence can then be used by high-level executives to inform strategic planning and allocate budget for security activities.
| Stakeholder Group | Intelligence Focus | Format & Delivery Method |
|---|---|---|
| C-Suite & Executives | Strategic risks, business impact, regulatory exposure | Executive briefings, slide decks, dashboards |
| Board of Directors | Governance, risk posture, compliance | Summary reports, presentations |
| Security Leadership (CISO, SecOps) | Threat trends, strategic planning, resource allocation | Threat landscape reports, dashboards, internal briefings |
| SOC Analysts | Real-time threat data, IOCs, alerts | IOC feeds (STIX/TAXII), SIEM alerts, chat notifications |
| Incident Response Team | TTPs, forensic data, containment actions | Tactical reports, playbooks, ticketing system updates |
| Threat Hunters | Hypotheses, detection logic, adversary emulation | Hunt packages, Sigma rules, internal wiki |
| Vulnerability Management | CVEs, patch prioritization, exploitability | Patch bulletins, RSS feeds, ticketing system tasks |
| Risk & Compliance | Regulatory threats, audit findings | Risk summaries, compliance dashboards |
| IT & DevSecOps | Supply chain risks, code vulnerabilities | API alerts, GitHub issues, CI/CD pipeline integrations |
| General Staff | Awareness, phishing, hygiene practices | Newsletters, training modules, simulated phishing campaigns |
6. Feedback
The last stage in the CTI lifecycle involves meeting with stakeholders and analysts to evaluate the effectiveness of the intelligence. It‘s important to include decision-makers to refine future threat intelligence operations as needed or adjust priorities as new threats emerge.
This stage is often overlooked; however, it is crucial to develop effective incident response protocols and improved risk management.
Best practices for CTI lifecycle management
1. Start with clear intelligence goals
When starting your threat intelligence journey, it‘s important to define intelligence requirements (PIRs) that align with business goals and stakeholder needs.
Emerging threats that target your industry and geography put threats into context, allowing teams to create accurate incident response plans.
2. Diversify your data sources
Great threat hunting and intelligence management rely on a broad array of data.
Use a combination of internal sources, including logs, open-source intelligence (OSINT) such as social media and dark web monitoring, and technical sources like threat feeds.
3. Invest in threat intelligence analysis
To accurately analyze threat data, security professionals need threat intelligence tools to process the often large volumes of data.
Cyber threat intelligence tools lower the rate of false positives and filter out irrelevant information.
4. Utilize threat intelligence feeds
Threat intelligence feeds deliver real-time threat data to help organizations detect, prevent, and respond to malicious activity. These feeds can help teams narrow in on IOCs faster, enabling better endpoint detection and response (EDR).
5. Use automation
Automation is another tool professionals use to streamline data collection and processing. SIEM integrations, for example, collect data from various sources into a centralized platform to collect, correlate, and analyze security events in real time.
This intelligence helps teams prioritize vulnerabilities and threats based on real-world use cases, improving overall incident response.
Wrapping up
Cyber threats continue to evolve as technology like deepfakes and AI becomes more sophisticated. To make an impact, CTI programs must evolve alongside emerging threats, adapting to the ever-changing threat landscape.
Analyzing past incidents and incorporating feedback from relevant stakeholders is a sure-fire way to refine and strengthen your organization‘s cybersecurity posture.

