Israel–Iran Cyber Conflict: [Flash Report]

Table of contents
The latest phase of the Israel-Iran conflict has expanded into cyberspace, with coordinated campaigns reflecting the scale and intensity of physical operations. Following Iran’s June 13 missile attacks against Israeli military positions, pro-government threat groups on both sides activated cyber operations that mirror battlefield momentum.
What has been happening in the Israel-Iran standoff?
Within 48 hours of the strike, Israeli CERTs reported surging activity from Iran-linked advanced persistent threat groups, notably APT34 and APT42. Their operations focused on reconnaissance, credential harvesting, and probing of Israel’s energy, telecom, and transport sectors. Conversely, Israeli-aligned operators launched destructive malware attacks and low-intensity distributed denial of service (DDoS) actions targeting Iranian infrastructure.
Cybersecurity analysts have tracked a 700% increase in cyber incidents tied to this conflict since mid-June, including phishing, malware infections, and network disruption events affecting allied nations.
Threat actor profiles
The Iran-linked APTs APT34 (OilRig) and APT42 (Charming Kitten) are actively targeting Israeli and Western infrastructure. Their operations have moved from credential harvesting to deeper reconnaissance on operational systems. A notable spear-phishing incident used a spoofed identity of U.S. envoy Jason Greenblatt to compromise devices in Washington, signaling intent to support kinetic actions with cyber sabotage.
On the Israeli side, Predatory Sparrow executed a $90 million crypto-burn against Nobitex, Iran’s largest exchange. The campaign also included data-wiping malware attacks on Bank Sepah, designed not for disruption but for economic degradation. These cyber offensives are tightly integrated with military strategy and exemplify a doctrine of economic warfare.
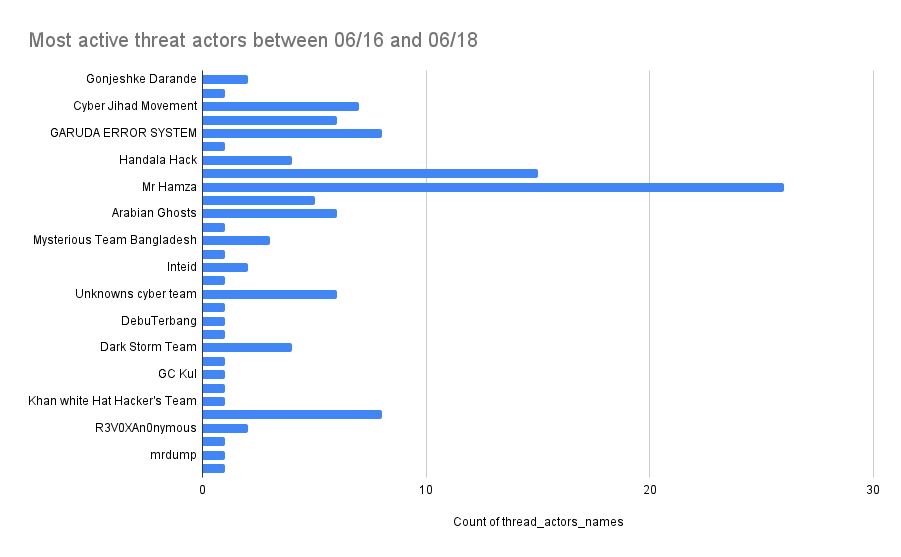
Meanwhile, hacktivist groups like Cyber Jihad Movement, Handala Hack, and Moroccan Black Cyber Army launched widespread DDoS and data breach operations. Their targets included Israeli ministries, telecoms, scientific institutes, and aviation companies. Though their tools are simpler, the frequency and symbolic impact of their attacks contribute to the conflict’s digital intensity.
What we know about the most recent attacks
The cyber conflict has directly impacted organizations in Israel, Iran, and beyond. Between June 16 and June 18, CybelAngel analysts recorded dozens of claimed operations:
- In Israel, 85% of attacks were DDoS events, primarily aimed at government agencies, telecom providers, and aerospace firms. Victims included the Ministry of Energy and Infrastructure, Israel Aerospace Industries, and multiple national news outlets.
- In Iran, Bank Sepah and Nobitex were both struck by data-wiping malware. Iranian officials responded by cutting internet access nationwide, disabling VPNs, and forcing users onto state-monitored networks. The blackout reached over 90% in some regions.
- In Jordan, attackers launched DDoS assaults on the Ministry of Education, Bank of Jordan, and the King Hussein International Airport, suggesting spillover risks to regional digital infrastructure.
An interactive log of over 100 attacks reveals that hacktivist groups such as Cyber Jihad Movement, Handala Hack, and Moroccan Black Cyber Army played prominent roles, claiming responsibility across Telegram and dark web forums.
The strategic intent varies: from symbolic defacements and minor breaches to economically damaging strikes against critical financial institutions. Israeli targets ranged from the Ministry of Finance to consumer platforms like Etti’s Kitchen and leisure firms such as Cityride. Iranian targets focused on economic resilience and information control.
Get in touch to access the full Flash Report
To access our full timeline of attacks, source breakdowns, and implications for business and government operations:
Contact us here to receive the complete Flash Report from CybelAngel REACT.

