How One Leaky Database Becomes an IoT Botnet: Inside the Mirai Attack Chain

Table of contents
You wouldn’t leave your branch vault propped open overnight. But every week, banks and financial firms do exactly that (just digitally).
A single MongoDB misconfiguration or stray public database exposure can unlock more than customer data. It can open a backdoor for hackers to compromise routers, security cameras, or smart ATMs.
It’s the first domino in a chain that ends with infected devices quietly conscripted into IoT botnets like Mirai. From there? DDoS attacks, data exfiltration, and bigger infrastructure compromises can follow.
This piece shows how that pivot happens, step by step. It’s designed for your SOC, your CISO, and everyone tasked with keeping connected devices secure in the financial sector.
The hidden risks of misconfigured databases
A misconfigured MongoDB isn’t just a data leak waiting to happen. It’s an open door for attackers to grab credentials and move deeper.
Many financial organisations still overlook this. They secure branch networks but leave cloud data stores half-guarded. Attackers know this, and they run constant scans for public instances, scoop up passwords, then look for a way to reach routers, cameras, or other Internet of Things (IoT) devices on the same network.
This is how a simple leak can lead to a botnet attack or a major DDoS incident. One gap fuels a chain of compromise that’s hard to contain once it starts.
Here are a few common targets:
- MongoDB: A popular NoSQL database often used for flexible data storage.
- Elasticsearch: Used for search and analytics; leaks can expose logs and sensitive queries.
- Redis: A fast in-memory database that, when open, can be hijacked for remote code execution.
Fortunately, regular audits and robust data leak detection can close this gap before someone else finds it first.
How does a data leak become a botnet attack?
Let’s imagine that a hacker spots your open MongoDB.
They grab credentials, such as an old admin login or API key.
What happens next?
Look sideways.
With that foothold, they scan your network for vulnerable IoT devices: branch cameras, door controllers, or even an old router with default usernames still in place.
This is exactly how Mirai malware first spread.
It brute-forced Telnet logins on thousands of cheap devices, dropped its payload, and linked each one to a command and control server. The result was a Mirai botnet ready to hammer targets with DDoS attacks.
One leaked database can kickstart this whole chain:
- Leak: Exposed credentials found.
- Pivot: Internal scan locates IoT weak spots.
- Infect: Devices become bots for a Mirai variant or similar threat.
- Attack: Your infrastructure, or someone else’s, suffers a distributed denial-of-service flood.
These attacks don’t just drain bandwidth. They risk downtime, fraud, and regulatory fines, especially in the financial sector, where trust is everything.
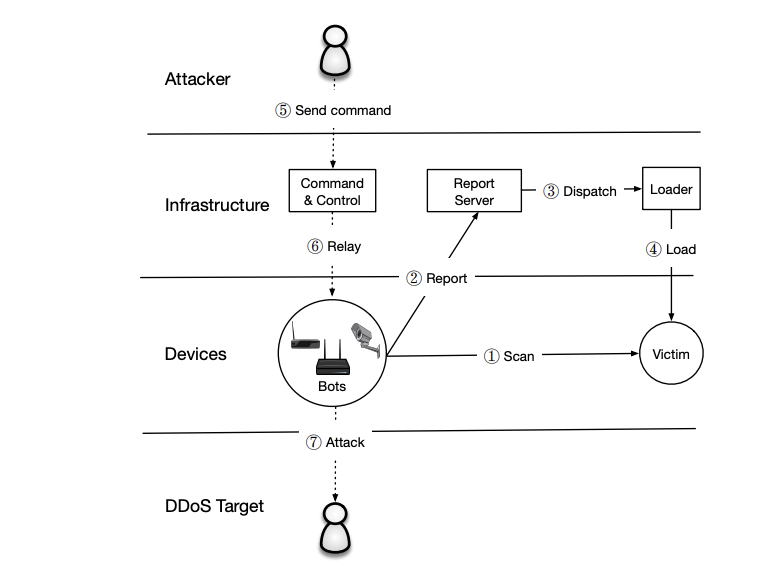
Real example: The Mirai botnet story
In 2016, a piece of simple but devastating malware called Mirai took the internet by surprise. Its creators were later unmasked as Paras Jha (or “Anna-senpai”), Josiah White, and Dalton Norman, who wanted to attack Minecraft servers.
Mirai scanned the internet for cheap, poorly secured IoT devices running Linux. It didn’t exploit fancy flaws. It brute-forced weak Telnet logins, using a built-in list of common default usernames and passwords. Once inside, it turned each device into a bot, quietly phoning home to a command and control server.
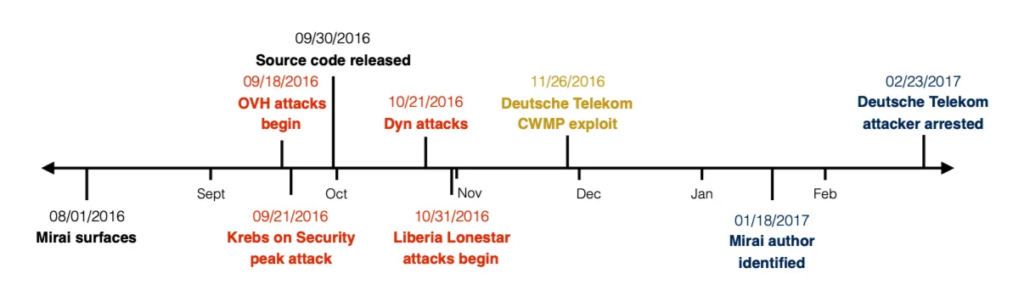
The botnet swelled fast. At its peak, Mirai controlled hundreds of thousands of infected devices worldwide. In September 2016, its operators unleashed large-scale DDoS attacks that overwhelmed targets like security researcher Brian Krebs’ site, called Krebs on Security, OVH, and the DNS provider Dyn. When Dyn went down, big brands from Twitter to GitHub to Netflix went dark for hours.
After the Mirai source code leaked online, new Mirai variants popped up, tweaking the original code to hunt even more vulnerable IoT endpoints.
Many still linger today, targeting unpatched devices and recycled passwords. For example, in March 2025, it was reported that Mirai botnets are exploiting CVE-2025-1316 zero-day vulnerabilities in security cameras.
One simple method (scanning for exposed devices and brute-forcing logins) built one of the largest DDoS botnets ever seen. And it started with the same weak spots many networks still have now.
Why financial institutions are high-risk
Banks and financial services sit on two tempting targets at once: valuable data and a sprawling web of connected hardware.
Branch routers, smart ATMs, office cameras, and IoT building controls all make life easier. But they also widen the attack surface. Many run on outdated firmware, with weak credentials or poor security patch cycles. And that’s exactly what Mirai malware and its clones look for.
Even a small foothold can turn into a major DDoS attack vector, draining bandwidth and eroding customer trust. Worse, regulators don’t look kindly on preventable breaches or downtime, and fines and audits often follow.
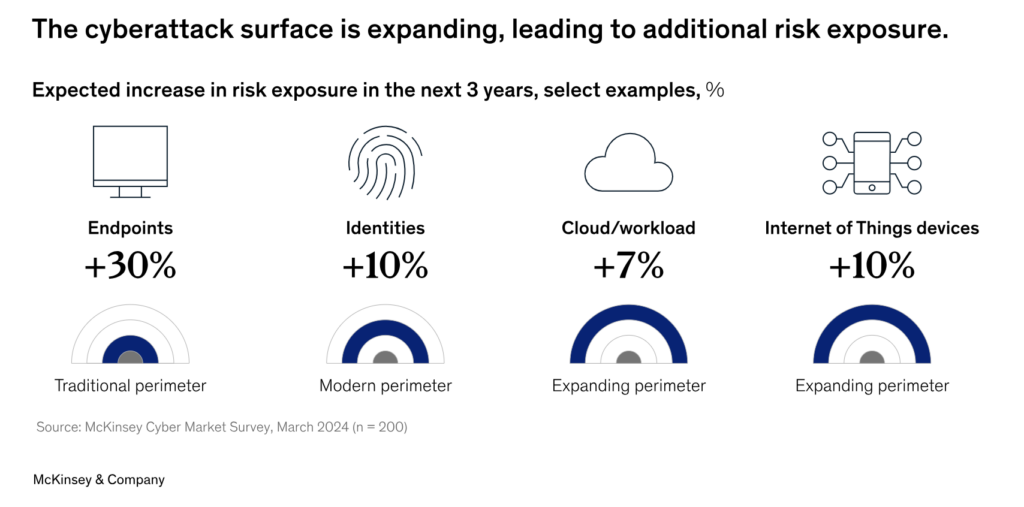
Attackers understand this. They see banks as high-reward, low-effort prey if basic gaps stay open. And with the cyberattack surface expanding (see below), this issue is only going to become more pressing.
How to break the chain: Practical defenses
Defending against a pivot from a database leak to a botnet infection isn’t complicated. But it does demand consistency. It starts with good housekeeping and ends with knowing what’s happening across your network before attackers do. Here are some cybersecurity best practices to do just that.
First, close off misconfigurations before they become headlines.
Database security is your first priority. Always require authentication on MongoDB, Elasticsearch, Redis, and other cloud databases. It’s shocking how many still run with default settings, accessible to anyone with a simple scanning tool. Restrict access by IP address, encrypt traffic, and review user permissions regularly. Better yet, automate this with a solid vulnerability management solution that flags risky settings as soon as they appear.
Next, get serious about IoT security.
A single vulnerable camera or router can drag your whole infrastructure into a botnet. Replace default usernames and passwords immediately. Many Mirai variants thrive because no one bothers to change factory logins. Securing IoT devices on their own network segment can fix this, by keeping them separate from critical systems and customer data. When vendors push firmware updates or security patches, apply them without delay. Too many attacks succeed because a patch was available but never deployed.
Then, watch for signs that someone is testing your doors.
Deploy data leak detection to catch exposed credentials fast, before they’re resold or reused for a pivot attack. Tap into threat intelligence feeds that track new botnet activity and suspicious IPs scanning for weak points. Some security teams even deploy IoT honeypots, which are fake devices designed to catch brute-force attempts typical of Mirai-like malware.
A slip in one area can undo all the effort elsewhere. But done together (secure configs, strong IoT hygiene, continuous monitoring), these steps shrink your IoT attack surface and make it far less likely that your network becomes part of someone else’s bot army.
What to do if you suspect a compromise
Even with strong defenses, cybercriminals can sometimes slip through. If you think an IoT device, router, or database has been compromised or pulled into a botnet, act fast.
- Isolate it: Disconnect the device from the network to stop it from communicating with command and control servers.
- Reboot: Many Mirai variants don’t survive a reboot. Restarting can clear the malware temporarily, but make sure you patch immediately to stop reinfection.
- Update: Apply all available firmware updates, security patches, and change default passwords.
- Check logs: Look for unusual traffic spikes, unknown IP addresses, or suspicious DNS requests.
- Strengthen the firewall: Block known malicious IPs and tighten inbound rules.
- Engage your DDoS mitigation partner: If you see signs of a large-scale DDoS attack, coordinate early to reduce impact.
- Review configurations: Double-check database settings, IoT device credentials, and network segmentation to prevent repeat attacks from threat actors.
Frequently asked questions
Got more questions? Here are quick answers to some common concerns about Mirai, IoT botnets, and protecting your infrastructure.
How do I know if my IoT devices are infected with Mirai malware?
Watch for unexpected bandwidth spikes, unusual outbound connections, or strange login attempts. Mirai bots often scan the internet or launch traffic floods without notice. IoT honeypots and deep traffic inspection can help detect this behaviour early.
Does a firewall stop Mirai botnets?
A properly configured firewall can block brute-force login attempts on Telnet and SSH, and restrict access to IoT ports. It won’t remove malware if a device is already infected, but it does help reduce the chance of compromise.
What role does DNS play in large-scale DDoS attacks?
Many big distributed denial-of-service campaigns target DNS providers (like Dyn in 2016). Disrupting DNS means taking whole websites offline, from banks to social platforms. Keeping your own DNS resilient and working with trusted providers is key.
Can rebooting a device remove Mirai malware?
Yes. Most original Mirai malware doesn’t persist after a reboot because it runs in memory. But if you don’t fix the weak passwords or update firmware, the botnet will just reinfect the device within minutes.
How do Mirai variants evolve?
Since the original Mirai source code leaked in 2016, attackers have tweaked it to exploit new vulnerabilities (like other remote code execution flaws). Some variants target routers, DVRs (digital video recorders), and even gaming servers, adapting to find fresh weak spots.
What’s the best DDoS protection for financial services?
Layered security. Use a mix of network-level defenses (like rate limiting and firewalls), upstream DDoS mitigation, and real-time monitoring. Combined with strong patching and credential management, this lowers your risk of being taken offline.
How does phishing connect to IoT botnets?
Phishing often targets people, not devices, but stolen credentials can unlock admin panels, routers, or database consoles. Once inside, attackers can pivot to vulnerable IoT endpoints. So good phishing defense supports strong IoT security, too.
Closing thoughts
Misconfigurations and weak IoT controls don’t just leak data. They open the door to bigger risks that can hit your business hard. Staying ahead means fixing small gaps before they become headline breaches.
CybelAngel helps you find these weak spots fast, and shut them down before attackers do. Book a demo to see how you could enjoy more peace of mind this year.

