Threat Bulletin – Smishing

Table of contents
Cyber threats are always evolving and innovating making it difficult to keep up with the latest developments. To help your company or organization stay protected from external digital risks CybelAngel REACT (REsearch and Analysis of Cyber Threats) is releasing our threat bulletins to the public. We hope that this information helps you, your organization, and your clients stay safe.
I. What is smishing?
Smishing is a type of attack carried out by text message (SMS), the word being a portmanteau of SMS and phishing. Akin to phishing, the victim receives an unsolicited message on their phone asking them to give out information through a link, by calling a number or texting back. It relies on techniques similar to traditional phishing attacks, namely Social Engineering, playing on feelings such as intimidation or emergency to get the victim to interact with the message. Despite relying on the same mechanics, smishing has a much higher success rate compared to phishing, due to a few factors:
- No auto “spam” folder on most smartphones,
- Lack of awareness on smishing attacks,
- More trust given to SMS vs email,
- Difficulty to authenticate the sender.
1. Common smishing schemes
- Debt scam: The attacker impersonates a debt collector administration to get you to give out personal information.
- Refund scam: A message states that you were overcharged for a service and that you are eligible to receive a refund.
- Reactivation scam: One of your accounts was disabled, you need to reply or send a specific text to another number in order to reactivate it.
- Fake delivery scam: The attacker presents itself as a delivery service, usually telling you that you missed a delivery or that you need to pay a fee in order to get your package.
- Family scam: The attacker poses as a family member or a friend in urgent need of monetary help to get out of a tricky situation.
- Malware scam: The attacker tricks you into downloading malware disguised as a legitimate application.
- CPF scam (France): In France, each employee has an account on a platform dedicated to training in order to gain professional skills called “Compte Personnel de Formation”. The trainings are proposed by certified training centers, but some scammers will create fake trainings and trick you into subscribing to them, to drain your account of its money.
2. Social engineering techniques
In the context of information security, social engineering is a form of psychological manipulation whose goal is to stir the target into a predetermined behavior defined by the attacker. All social engineering techniques are based on exploiting cognitive biases in the human decision making process. We all use these biases on a daily basis to process information in an effective and efficient manner but as they are often unconscious and automatic, they can be used to manipulate our decision making process. There are six key biases that are used in social engineering:
- Authority, attacker may impersonate someone who has authority over the victim (police, manager, …).
- Intimidation, attacker intimidates the victim by threatening them of negative consequences if they don’t perform the desired action.
- Consensus (or Social Proof), we are more likely to execute an action if the majority of people around us seems to have done the action.
- Scarcity, by creating an artificial feeling of scarcity, the target is more likely to execute the action faster, by fear of missing out.
- Urgency, used to get the target to act fast, for example: “Please fill the form below in the next 24hr to apply to our raffle”.
- Familiarity, we are more likely to be receptive to people we like or that are close to us. Attackers may exploit this bias by posing as a friend or family member.
II. Malicious Actor Modus Operandi
1. Information gathering
A. OSINT
OSINT or Open Source Intelligence is the collection and analysis of data gathered from open sources to produce actionable intelligence. It is mostly used in case of targeted phishing attacks. Example: I want to target Elisa S., who is an accountant working for Black Cat Incorporated, to get her to do a wire transfer to my account. Through OSINT I’m going to gather information concerning her and her boss, the company, her hobbies, etc. Using social networks, search engines and specialized tools, I’m going to do the best I can to understand her and how she works. As for her phone number, I could search and/or deduce her professional email address and send an email, hoping the signature in her answer will reveal her number, or pose as an ex-colleague on a social media wanting to reconnect with her and asking for her number – with a little imagination the possibilities are endless.
B. Leaks
Everyday, platforms get hacked and the information retrieved from the hack are usually sold, shared or exploited immediately by the attacker. Example: Earlier this year, cryptocurrency platform Poulp was hacked but the company assured that the stolen passwords were correctly hashed and salted (impossible to reverse), and that only their names, email addresses and phone numbers were stored in plain text and leaked. Furthermore they stated that no accounts were breached and that mandatory 2FA would protect the users even if the passwords were leaked. Despite this statement and the 2FA protection, hackers were able to trick some users into connecting to a phishing website by crafting the following message. Once the link clicked, the user was asked to enter its information alongside the 2FA code that would be sent by the legitimate platform, arriving in the same conversations on their phones. 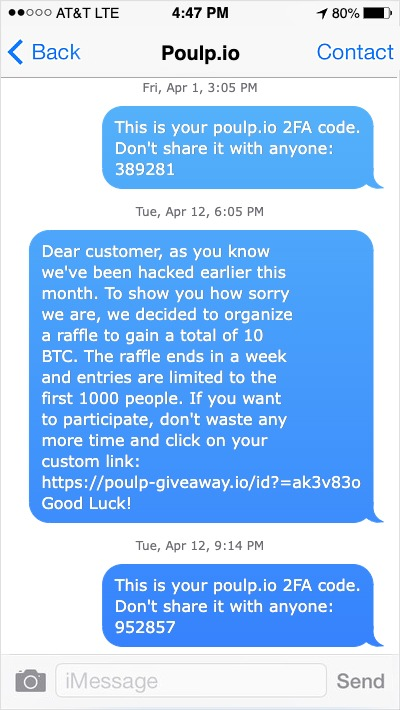 An example of smishing. This screenshot is manufactured, Polup is a fake company, to illustrate an attack.
An example of smishing. This screenshot is manufactured, Polup is a fake company, to illustrate an attack.
C. Data brokers
Another way to get information is to buy it from data brokers, which are companies that specialized in the collection and resell of personal data. They get their data by different means: scrapping, getting information from public registries (eg. enterprise directory), buying information from retail stores, banks, etc. The largest data brokerage companies claim to have categorized information on hundreds of millions of consumers worldwide. Thanks to this massive collection of data, they can provide buyers lists of people according to precise details such as their age, gender, salary, work, hometown, hobbies, pets, etc. But while these services are legitimate in most countries and used by firms for marketing purposes, malicious actors can get their hands on the data and resell or use it themselves. 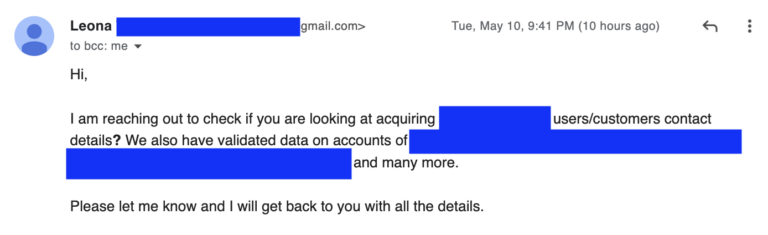
D. Dark Web
In addition to the aforementioned sources of information, cybercriminals can also get their information from a middleman by buying the data directly off the dark web. Malicious actors operating in underground communities are selling information on individuals or groups, most of the time the information sold are categorized into geographical targets as well as industries. 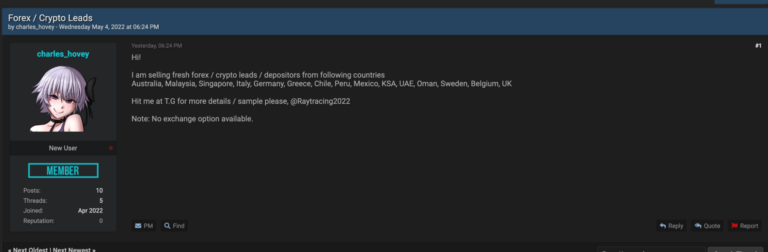
2. Message crafting
A. Spray and Pray
Spray and Pray (mass phishing) is a traditional and unsophisticated form of phishing. The goal is to send the message to the largest number of people possible, counting on the fact that even if a very low percentage of targets falls into the trap, the campaign will be profitable for the attacker. These attacks usually do not rely on any additional personal information acquired on the targets and are impersonal messages that have a low chance of success – but not zero. Like the previous steps, malicious actors may use legitimate tools to massively send their texts, by creating accounts with fake information or taking over an already existing account. Below, the Cybelangel REACT team identified a stolen customer account on SMSAPI to prepare a smishing attack, impersonating American bank JPMorgan Chase: 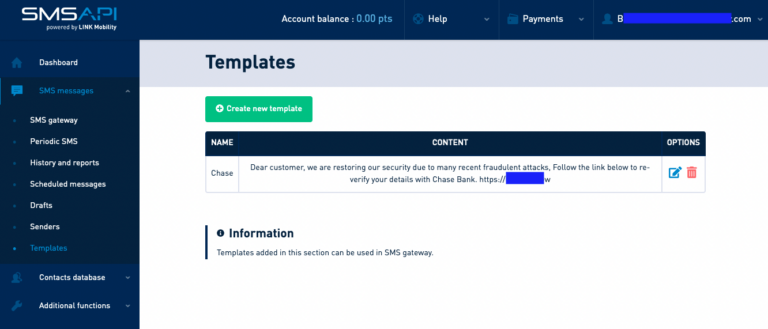
B. Spear Phishing
Spear Phishing (tailored phishing), unlike its counterpart mass phishing, is a form of phishing that will use information gathered on the victims before conducting the attack. Gaining information on the victims or targeting a specific persona for a phishing attack allows the attacker to craft a more convincing message to the eyes of the victim, leading to a higher yield. These types of attack are more costly for the attacker and mobilize more resources, hence they are less common but have a much higher chance of success and can have devastating consequences.
III. Protecting employees from smishing
Successful smishing campaigns can indeed have disastrous consequences for the targeted company:
- Wire fraud and money loss, through “fake president scams” and BEC,
- Lower trust from the consumer, when malicious actors impersonate famous brands,
- Possibility of having a corporate device infected by malware or get one’s credentials stolen, which can in turn provide an initial access vector or a spying access to the attacker.
As such, employers should include smishing exercises to raise awareness and train their employees, just like traditional fake-phishing campaigns. The following tips will defeat most smishing attempts:
- Do not trust any text message that comes from an unknown number. Usually, legit companies will have short or named number whereas malicious message are more likely to come from a regular phone number.
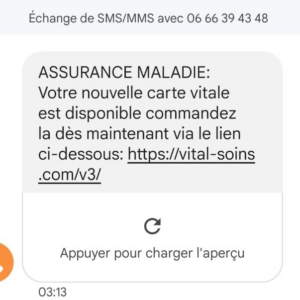 Example of smishing attempt asking the user to click a link to receive its new social security card (we can see at the top that it comes from a regular French number)
Example of smishing attempt asking the user to click a link to receive its new social security card (we can see at the top that it comes from a regular French number)
- Actors often use the “intimidation” trigger by impersonating a C-level. Still, even if you seem to receive a message from any colleague from your enterprise, double-check with the sender to confirm the authenticity of the message and the demand.
- Look out for suspicious links (uncommon domain extensions like .top are commonly used by hackers, mainly because they are cheap to acquire) or links that seem too obvious, containing “help”, “payment” or “delivery” in the URL.
- If you are not waiting for such a specific event, just ignore the message. If you are, check directly on the site you are waiting the event for (eg. delivery company).
