What are the Top Risks of Internet-Connected Devices?

Table of contents
It is Cybersecurity Awareness month so let’s tackle a common headache for SOC teams.
What do weak processing power, poor network security and basic passwords have in common? The simple answer is IoT devices.
IoT devices or internet connected devices are difficult to secure and easy to compromise. It is why they are also beloved of cybercriminals, from the launching large-scale botnets to using them for other malware infused phishing.
In this guide, we look at why interconnected assets like mobile apps, IoT devices, hybrid cloud infrastructure, websites, operational technologies, and even BYOD devices, are still spelling trouble for CISOs and SOC teams. We’ll also explore the why behind how hackers can access and source personal data from operating system vulnerabilities and beyond.
If you want to review the myriad of weaknesses that arise from unsecured devices and smartphones, this is the perfect way to catch up.
But firstly, let’s explore the rise of cyberattacks linked to networked devices.
Why are cybersecurity risks increasing with the internet of things?
Actually there is a long list of reasons why this is the case, which is frustrating given how sales and service providers continues to expand. After all, data projects that the total number of connected IoT devices will double to approximately 40 billion by 2030 (desite supply chain issues!).
Let’s review the top 5 of these threats:
1: IoT devices equate explosive growth: The attack surface for IoT devices keeps on expanding alongside the massive proliferation of devices, year on year. According to the IoT Analytics’ State of IoT Summer 2024 report, we can expect a growth of 2.2 billion devices year-over-year in the 2023-2024 period.
2: Poor security measures are the standard: With speed comes cutting corners. It seems that security priorities take a back seat with manufacturers, from weak default passwords to a lack of encryption. According to a study by the Ponemon Institute, around 32% of organizations perform vulnerability scanning on IoT devices, and only 31% conduct pre-certification testing of devices prior to deployment.
3: Complexity is king: IoT ecosystems, characterized by their complexity, involve a diverse array of devices, platforms, and protocols that interact in intricate ways, often leading to potential security vulnerabilities. A report from HP indicated that 70% of IoT devices are vulnerable to attacks due to the complexity of their environments, which can leave gaps in security.
4: Data privacy issues: Another issue that is raised consistently is the data collected by IoT devices. raises significant privacy issues, especially when data is shared with or sold to third parties.Once remote working trends are added to the mix it becomes even more complicated thanks to IoT devices connecting to unsecured wifi public networks.
5: Denial-of service attacks and botnet attacks: In the first half of 2023 DDoS attacks surged by 300% alone! Compromised IoT devices are favorable for hackers to scale attacks with sustainability. For example, BlackCat’s Sphynx ransomware variant incorporates the Impacket framework for credential dumping and the RemCom tool for remote command execution, enabling more advanced lateral movement within compromised networks.
We all know that RaaS is big business. But as more and more cloud shares, data storage, and IoT devices become exposed, you can expect attackers to explore all types of sophisticated methods thanks to data alteration and increased computing power.
Takeaways for your team:
Improperly secured or misconfigured IoT devices pose various risks, including unauthorized access, data exposure, data theft, and DDoS attacks.
Let’s take a further look at preventative measures and steps to educate your information technology department
How to mitigate the cybersecurity risks of connected devices?
It is as clear as day that every endpoint offers an entry point for hackers, and the more devices connected to the web, the more endpoints there are. It is critical to review data protection as a whole subject. As each new web-enabled device connects to your network, it greatly increases the attack surface of your network.
So, what about mitigation?
Firstly, involving cybersecurity experts into early stages of business planning is critical for organizations to mitigate digital risks effectively. When decisions are made without considering the digital landscape—such as enabling work from home policies or BYOD (bring your own device) practices—organizations leave themselves vulnerable to data breaches.
CISOs who are involved in these decision-making process can significantly reduce these risks by ensuring:
- Proper authentication protocols
- Automation of security processes for efficiency
- Boosted functionality of security tools to handle various threats.
The landscape of cybersecurity is further complicated by the rapid expansion of Internet of Things (IoT) devices. As of 2023, an estimated 15.14 billion IoT devices are in use globally, with expectations for continued growth. This proliferation expands the attack surface for cybercriminals, drawing attention to the importance of comprehensive security strategies that encompass both traditional computing devices and the burgeoning IoT ecosystem. Automation in threat detection and response becomes invaluable here, as the vast number of devices makes manual monitoring impractical.
Moreover, IoT devices, including routers and security cameras, have increasingly become prime targets for attackers, leading to sizeable uptick in malware attacks on these devices. Routers, in particular, account a large amount IoT related infections, offering hackers a gateway to other connected devices within networks.
What’s an unmanaged device?
When your employee accesses your company’s database via their iPad on a wireless device, that makes for two unmanaged devices accessing your data — their iPad and the wireless router. When organizations allow unmanaged devices to tap into their networks, these devices increase the attack surface. Hackers can then easily access these networks and exploit their data.
Are you prepared to protect your sensitive data accessed by unmanaged devices?
Another key question, do you have the endpoint security tools to support policies to remote work? And also to bring your own device? For many organizations this is not the case.
In the list below, see the ways that internet-connected devices jeopardize network security. The risks are high when it comes to allowing unmanaged web-connected devices to tap into your organization’s network.
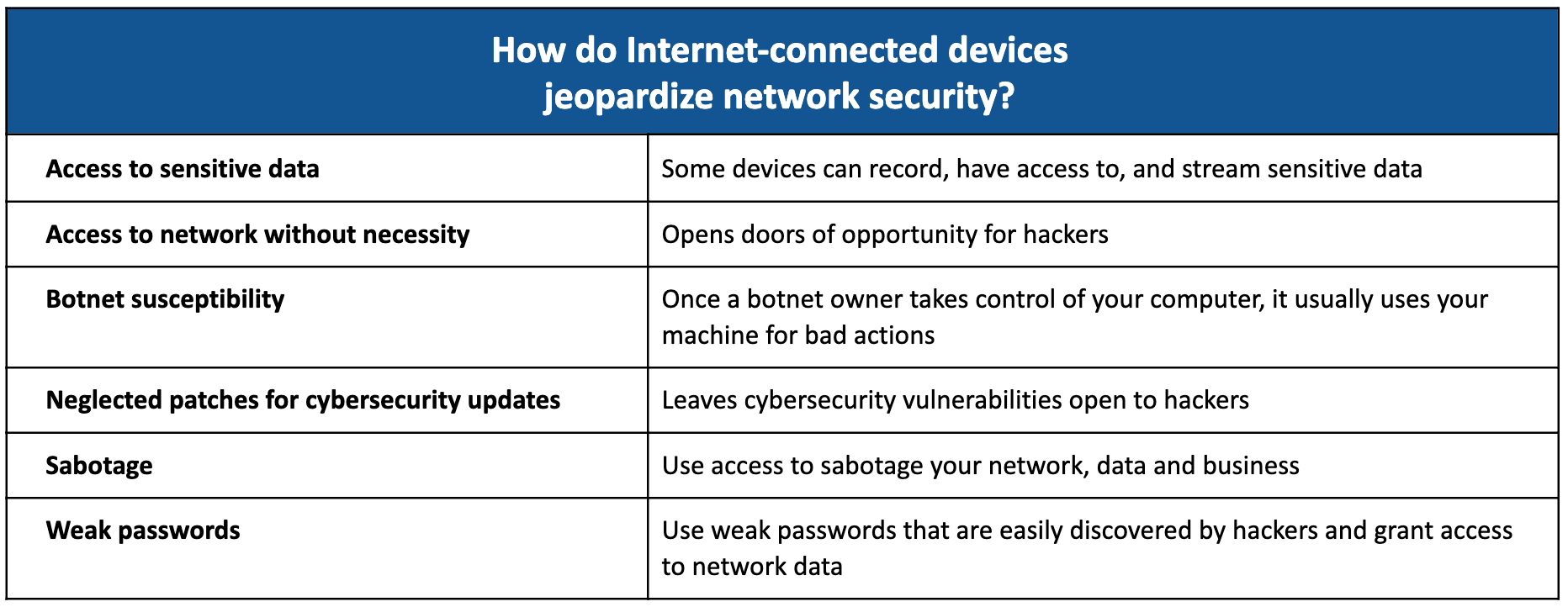
Although data leaks are inevitable; damage is optional. Let’s look at specific steps you need to take to prevent security risks.
5 steps to prevent security risks via connected devices

- Know your risk: Discover all web-connected devices on your network.
- Patch up your life: Patch printers and other easily patchable devices.
- Segment all web-connected devices across VLANs: Segment your devices! This will help you to know how many and the kind of devices are accessing your data.
- Enable active monitoring: Use augmented intelligence (machine learning + human analysis) to actively discover and investigate critical data leaks.
- Receive instant alerts: For sensitive data leaks via a web-enabled device or other methods.
Wrapping up
So, how can you know if your attack surface is under surveillance? At CybelAngel we protect your external attack surface through our EASM suite. If it is too late and you’ve been hacked, you can avail of our remediation service. You’ll reduce your time to take down by 85%.
That is it for this blog. We hope you’ll review your IoT ecosystem’s data security!