Fake Domains, Banks, and Malware
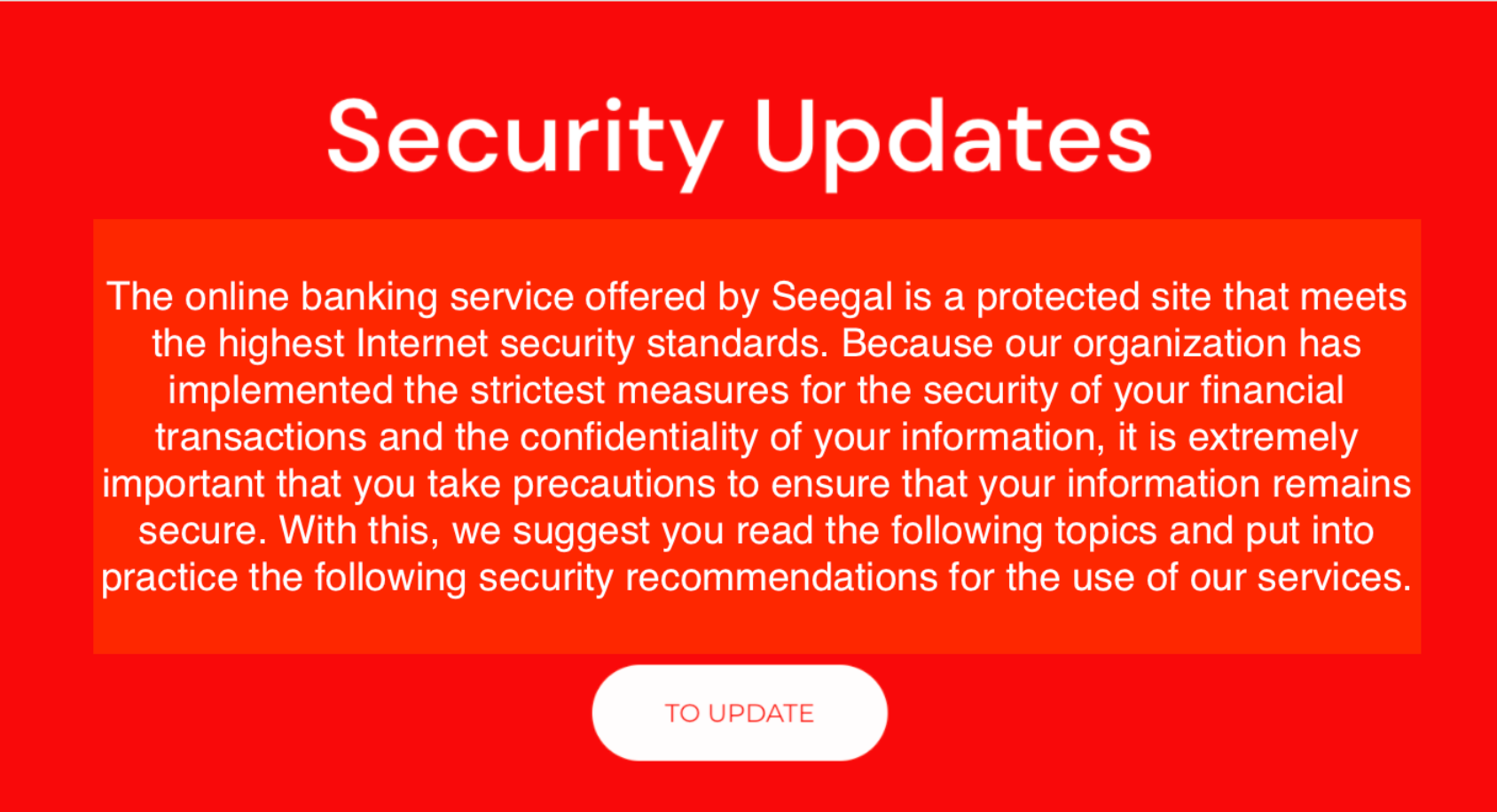
Table of contents
The Alert of the Month for March 2022 is a fraudulent domain targeting bank customers. Domain Spoofing is a classic cyber threat for a reason. It works very well. You can read on to learn what happens or if you want you can watch Oleg Lypko walk you through this month’s alert!
A well-designed fake can convince users to disclose personal and financial information or download a file. In recent years this type of fraud has seen a resurgence. Several industries, such as airlines, retailers, and banking, are targeted daily for billions in losses. On 24th February 2022, CybelAngel detected a fraudulent domain impersonating a client in the financial industry.
An analyst’s report
CybelAngel analyst Oleg reviewed the report from Toucan, the refined machine learning generated alert feed. Oleg confirmed the webpage had all the hallmarks of a fraudulent domain: created the same day, a different domain name registrar from the legitimate client’s website, and a slightly different URL. The fraudulent web page reveals a bright red background with an update button. A message in white font read: Oleg noted the quality of the forgery. “It is well done and professional. It’s not just a fake login; it uses social engineering. The bright red color, warning message, and instruction to download a new update to securely access their banking application. That “update” was malicious.”
The supposed update directed visitors to download a malicious software installation package targeting Android OS. After the installation, threat actors aimed to leverage the popular hacking framework Metasploit, on the victim’s mobile device. This way, they gain persistent access to the victim’s mobile device, they can easily access the victims’ banking details, and they can even bypass two-factor authentication codes. Oleg noted that even with the quality of the webpage, “it requires a user to download an application outside of Google Marketplace. More tech-capable users could quickly see the application is fake, but if you are in a hurry or don’t know that, it would be an easy mistake to make. Also, some smartphone vendors block or warn users about the installation of software packages from unauthorized application marketplaces.
Security features: What to keep in mind
Users shouldn’t bypass those security features unless they are 100% sure about the origin and intent of the application. With these findings in hand, Oleg informed the client of the risk and laid out their remediation options, “Domain fraud is a daily occurrence, so many financial institutes have good relationships with domain registrars. There are well-known points of contact and legal processes, so taking domains down is done quickly. The next step would be to block the fake webpage on the client’s infrastructure to prevent a phishing campaign against their internal users. Finally, communicate to their clients to be on their lookout for phishing attempts.” “Domain Protection is different. A data leak can be caused by mistake.
Fake domains like this are 100% malicious. We see three or more fake domains a day with some clients,” Oleg explained. CybelAngel’s latest research report reveals that 21% of all incident alerts for financial customers are related to domain fraud. CybelAngel customers are protected from fraud by our Domain Protection module. Our powerful scanning technology and machine learning filter out false positives to locate critical external threats. By proactively searching for these leaks, you protect your company, customers, and employees in one go.