
How Secure Is Your Data in AWS S3 Buckets?
For AWS S3 Storage Buckets: Data Leak Risk?
Use of Amazon Simple Storage Service (AWS S3) storage buckets is expanding exponentially. Key drivers of this growth are AWS S3’s file sharing between employees and its ability to host Internet-facing services. This rapid growth and collaborative functionality makes concerns about their cybersecurity emblematic of 2020. The quick shift to remote workforce, combined with the extreme flexibility of AWS S3 storage makes S3 buckets the choice for many businesses and individuals. AWS S3’s flexibility also charms numerous malicious actors, who are increasingly targeting open Amazon S3 buckets in their attempt to steal data from companies and individuals. Thanks to common misconfiguration of AWS S3’s Access Control Lists, attackers can gain access to the S3 bucket and read the files, gathering consistent information businesses’ activities. Furthermore, the adversary can also write and upload files to the S3 bucket, or they can change access rights to block legitimate users to access the information stored inside the bucket. As CybelAngel discussed in a previous blog post, if done correctly, this operation – known as reconnaissance – can provide the hacker with precious insights to eventually carry out more in-depth and tailored attacks.
How many unsecured AWS S3 buckets are out there?
To gain a better understanding of the open AWS S3 buckets data leak issue, CybelAngel studied 409,166 publicly exposed AWS S3 storage buckets from September 1st, 2020 – November 27th, 2020. The analysts detected:
- 211,790 in September
- 84,849 in October
- 112,527 in November
Of the files detected by CybelAngel analysts, the number of potentially sensitive files included 124,212,145 Microsoft Office Suite (.docx, .xlsx, .pptx… ) documents and 987,925,686 PDFs. The majority of these documents were from the finance, logistics, asset management, tourism, hospitality, and IT industries.
How to Secure AWS S3 Buckets
An S3 bucket can be accessed through its URL. The URL format of a bucket is either of the two options below:
- http://[bucket_name].s3.amazonaws.com/
- http://s3.amazonaws.com/[bucket_name]/
To test if your S3 bucket is publicly accessible, click on the bucket’s URL from any web browser. A secured bucket will return a blank page displaying the message “Access Denied,” with no bucket content shown. A public or unsecured bucket will display a list of the first 1000 files contained in that bucket. It may happen that the bucket’s Access Control Lists have some misconfigurations, or that some users have been granted an excessive level of privileges in the bucket. 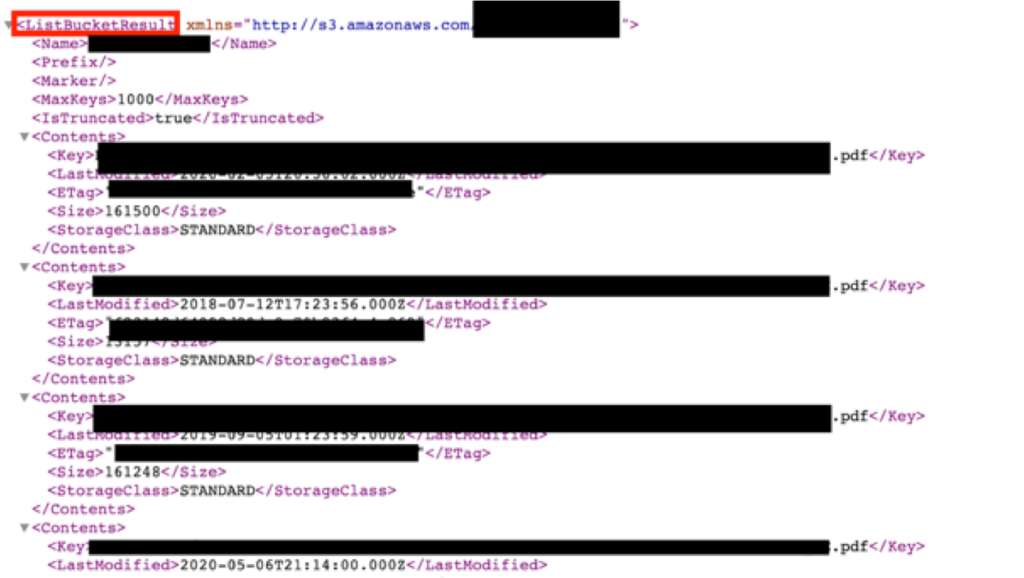
Tips to ensure the security of your data contained in S3 buckets
- Remove public access from all your S3 buckets unless it’s absolutely necessary. This can be done through the S3 administration services. Manage your AWS accounts, users, and roles – including access to files within the bucket, as well anonymous access.
- Disable Access Control Lists (ACL): Even if an S3 bucket is private, it’s still possible to modify its policy to make folders or files public. By disabling this option, the bucket and the files inside will be managed with the same conditions of privacy.
- Ensure access granularity: Ensure the AWS S3 permissions are as granular as possible. If a certain user does not need access to an S3 bucket, don’t grant that access. Whitelisting versus blacklisting users increases the security of your bucket. It also allows more efficient access management control.