Who is the Black Basta Ransomware Gang?

Table of contents
What do you get when a ransomware group launches with 20 victims in its first two weeks, and never slows down? You get Black Basta.
First spotted in early 2022, Black Basta has quickly become a prolific ransomware operation. Let’s explore how they work, who they’re targeting, and how to fight back. Plus, we’ll take a look at their recent takedown, and what it might mean for cybersecurity this year.
Black Basta’s origins and background
The Black Basta ransomware group was first identified in April 2022, but signs suggest it had been in development as early as February of that year. In its first two weeks, the group listed over 20 victims on its Tor-based leak site called Basta News. Since then, it’s known to have targeted over 500 organizations globally.
While Black Basta operates as its own ransomware-as-a-service (RaaS) group, it didn’t come out of nowhere. Many researchers believe it may be a rebrand (or at least a splinter group) of Conti, the notorious Russian-speaking ransomware gang. The theory is supported by shared tactics, similar infrastructure, and even overlapping victim recovery portals.
Here’s a screenshot of their chat log IP addresses from a security analyst, showing where most of their activity is distributed.
There are also links to other Russian cybercriminal groups, including FIN7 and BlackMatter, reinforcing the idea that Black Basta is part of a broader, evolving ecosystem rather than an isolated actor.
Black Basta keeps a low profile. Unlike other RaaS groups that recruit publicly, it appears to work with a tight circle of trusted Black Basta affiliates, if any. Its attack cadence has focused on critical infrastructure, including healthcare, manufacturing and construction across the US, UK, Canada, Australia, and several EU countries.
They’ve also faced a recent takedown after a leak of their chat logs in February 2025 (more on this later).
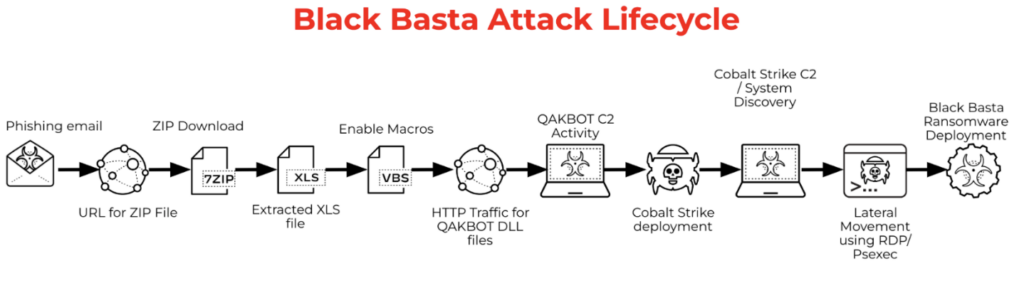
How Black Basta operates: Tactics, Techniques, and Procedures (TTPs)
Let’s break down what a Black Basta ransomware attack often looks like.
- Initial access: Black Basta typically breaks in through phishing. Their affiliates craft convincing emails to trick employees into clicking malicious links or downloading remote access tools like AnyDesk or Quick Assist. In some cases, they escalate the social engineering by flooding targets with spam emails, then posing as IT support via phone or even Microsoft Teams to “fix” the issue.
- Execution and persistence: Once inside, Black Basta affiliates scan the network using tools like SoftPerfect NetScanner, often disguised with filenames like “Intel” or “Dell” to avoid detection. For persistence and lateral movement, they lean on a mix of legitimate and attacker-favorite tools: Cobalt Strike, PsExec, BITSAdmin, ScreenConnect, and Splashtop. For privilege escalation, they use Mimikatz and exploit vulnerabilities like ZeroLogon and PrintNightmare.
- Data exfiltration: Before launching encryption, Black Basta affiliates siphon off sensitive data using tools like RClone and WinSCP. This step is critical to their double-extortion strategy.
- Encryption: The ransomware itself uses ChaCha20 encryption with RSA-4096 public keys. Once files are locked, extensions like
.bastaor other random strings are added. Volume shadow copies are deleted usingvssadmin.exe, making recovery harder. A ransom note titledreadme.txtis dropped across the network. - Extortion: Black Basta doesn’t usually state a ransom amount up front. Instead, their notes provide a unique code and a Tor-based URL. Victims are typically given 10 to 12 days to respond before stolen data is published on their leak site, known as Basta News.
What makes Black basta distinctive?
Black Basta’s operations use a familiar toolkit—PowerShell, Cobalt Strike, and Mimikatz—but with a few notable twists. Their use of social engineering through Microsoft Teams is rare, and it’s an elaborate way to gain their victims’ trust before delivering the malware.
Another tactic is their creation of an automated tool to compromise network devices with weak passwords. Not every ransomware group can claim the same degree of in-house development.
Black Basta’s victim list spans at least 12 of the 16 critical infrastructure sectors, with a focus on healthcare, manufacturing, and other high-value targets. They’ve hit over 500 organizations across North America, Europe, and Australia, suggesting a wide reach and a clear focus on English-speaking regions.
In terms of their communication and branding, Black Basta maintains a consistent presence through its leak site, Basta News. They don’t use flashy branding, like groups such as Akira, which suggests they’re less interested in reputation, and more so in results.
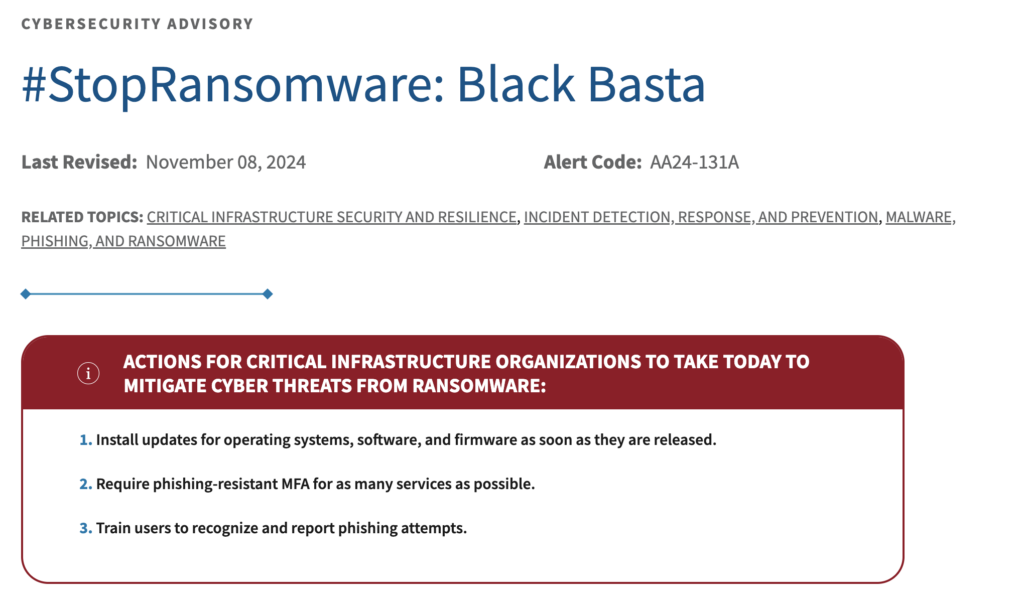
For more details, CISA, the American Cyber Defense Agency, has released a detailed advisory on Black Basta’s operations, IOCs, and MITRE ATT&CK indicators.
Black basta and recent attacks
According to a Bleeping Computer article, in May 2024, Black Basta targets received thousands of non-malicious emails, mostly newsletters and sign-up confirmations, designed to flood inboxes. The attackers then called employees, posing as IT support, and offered help resolving the issue.
During the call, they convinced users to install remote access tools like AnyDesk or use Quick Assist. Once connected, they deployed tools such as ScreenConnect, NetSupport Manager, and Cobalt Strike to maintain access, move laterally, and begin staging the ransomware attack.
By October, the group shifted to using Microsoft Teams instead of phone calls. Employees were contacted via external Teams messages, again under the guise of IT support, continuing the same remote access playbook.
In another example, Black Basta launched a cyber attack on Ascension, a St. Louis-based nonprofit network, forcing them to redirect ambulances and revert to backup processes.
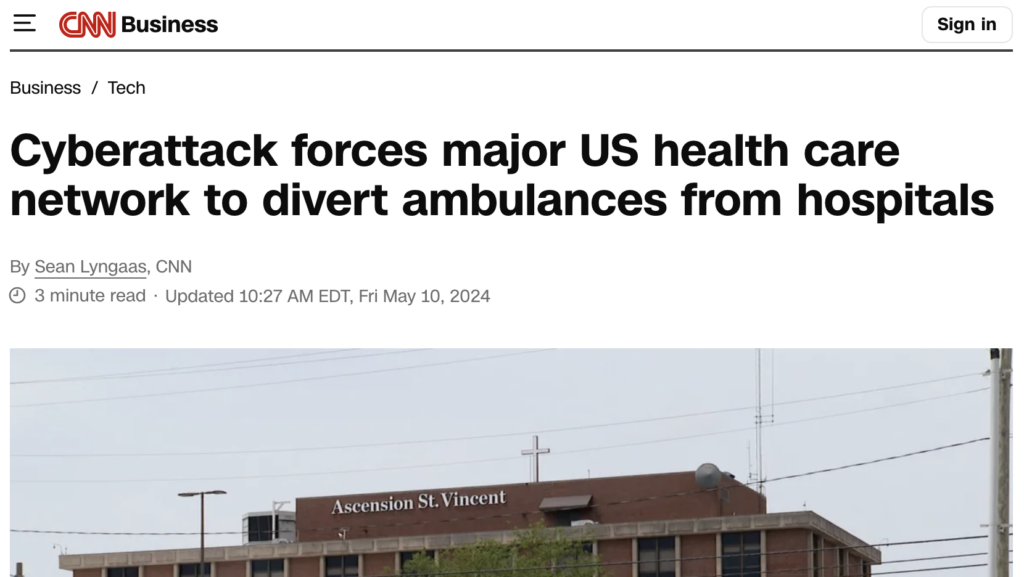
Figure 6: News headline of the attack. (Source: CNN).
Black Basta attacks often lead to system encryption and data theft. Ransom notes direct targets to negotiate over Tor, usually without an upfront payment demand.
Victims deal with numerous consequences, including:
- Service disruption
- Credential loss
- Recovery costs
- Reputational damage
- Legal and compliance consequences
However, Black Basta threat actors have recently faced a takedown, due to a combination of law enforcement and some leaked chat logs.
Let’s break this down…
The recent Black Basta takedown
Black Basta’s operations have slowed significantly following two major setbacks: a law enforcement takedown and an internal leak.
The Black Basta ransomware group was hit hard by Operation Duck Hunt, the 2023 takedown of the Qakbot botnet, which had been a key part of its infection chain.
Figure 7: Press release detailing the takedown. (Source: @BushidoToken)
Then, in early 2024, a leak of internal chat logs and operational details exposed the group’s tools, tactics, and some members’ identities. The leak included more than 200,000 messages from a Matrix server used by the group and revealed internal disagreements, development efforts, and hints at the admin’s identity.
Since the leak, Black Basta has gone quiet. But researchers warn the group’s members haven’t disappeared. They’re already surfacing in other ransomware operations, including BlackSuit, INC, Lynx, Cactus, and Nokoyawa.
While the leak damaged Black Basta as a brand, the people behind it remain active in the ransomware ecosystem. As with past groups like Conti, they’ll likely continue operating, just under different names.
Cybersecurity tips to defend against Black Basta
Black Basta uses a mix of social engineering, known vulnerabilities, and legitimate tools to breach networks, so defending against them requires strong fundamentals across prevention, detection, and response.
Prevention
- Apply patches quickly, especially for VPNs, RDP services, and tools like ConnectWise.
- Enforce multi-factor authentication across all remote access tools.
- Limit admin privileges and regularly audit accounts and access.
- Educate employees to spot phishing, fake IT calls, and social engineering over Microsoft Teams.
- Disable or restrict the use of remote tools like Quick Assist if they’re not needed.
Detection
- Monitor for lateral movement tools like PsExec, Cobalt Strike, and ScreenConnect.
- Look for unusual use of remote access tools or newly installed remote monitoring software.
- Set alerts for shadow copy deletions (vssadmin.exe) and suspicious PowerShell activity.
- Track data transfers to cloud services using tools like RClone or WinSCP.
Response & recovery
- Have a clear, rehearsed incident response plan, and make sure teams know their roles.
- Isolate compromised systems quickly to stop the spread.
- Preserve logs and forensic evidence, even if devices are encrypted.
- Report incidents to law enforcement or CISA to aid broader threat tracking.
- Test backup restoration regularly, and store backups offline or in a separate environment.
Wrapping up
Black Basta may be quiet for now, but its methods (and its members) are still active across the ransomware ecosystem. Staying ahead means having visibility not just inside your network, but outside it too.
CybelAngel’s external threat intelligence platform helps SOC teams and CISOs detect exposed assets, leaked credentials, and early signs of compromise before ransomware groups can strike.
Ready to see more?

