Hospitals and Ransomware: An Invasive Sickness

Table of contents
Ransomware is so malicious it now holds both your data and your healthcare needs hostage.
And, what once was seen as an off-limits target is now a preferred income generator for cybercriminals.
In the healthcare industry, attacks are encrypting complex patient records, cancelling appointments, delaying life saving surgeries, and even rerouting ambulances, to name some of the more serious incidents that occur.
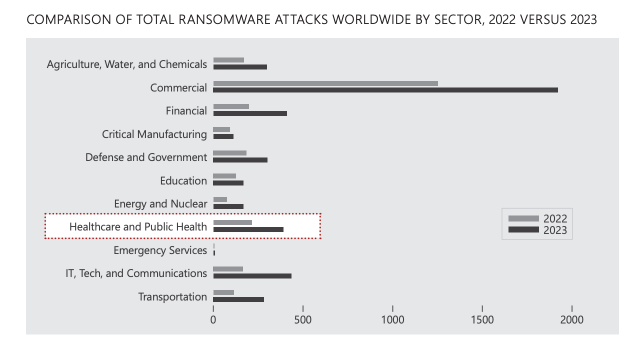
A 2023 data review from the CTIIC shows that within the United States, attacks against the healthcare sector
were up 128%, with 258 victims in 2023 versus 113 in 2022.
If the healthcare organization doesn’t pay the ransom, usually in the millions, hackers release the patient information they have stolen to the public or sell it on the dark web. At a minimum, the result is financial damage and patients lost.
But other invasive consequences are just as jarring.
For example, one study by the University of Minnesota found that the number of Medicare patients in hospitals who pass away actually increases during a ransomware attack. The author, Professor Hannah Neprash, noted that, “Despite this increased risk, information about the frequency and scope of these attacks is limited to anecdotal news coverage.”
In terms of cost, IBM’s “Cost of a Data Breach Report 2024” study found that the average cost of a single data breach in the healthcare sector came close to the $11 million.
Unfortunately, cybercriminals will continue their attacks because the number of appealing data records in healthcare organizations keeps increasing annually.
It leads to the penultimate question of what can be done when motive, ease of access and much more, makes this target so pleasant for cybercriminals.
But first, let’s explore hospitals and ransomware further and discuss possible solutions.
Why is healthcare a hot target for cyber attacks?
There has been a 93% increase in large cyber attacks in the period between 2018 and 2022 says the U.S. Department of Health and Human Services (HHS). The FBI are in agreement which the mounting scale of attacks with their 2023 Internet Crime Report revealing that healthcare faced more attacks of this kind than any other sector.
Below a slew of malicious tweets posted by hackers who posted on behalf of NHS hospital, Andover War Memorial Hospital in 2020, as reported by the BBC.
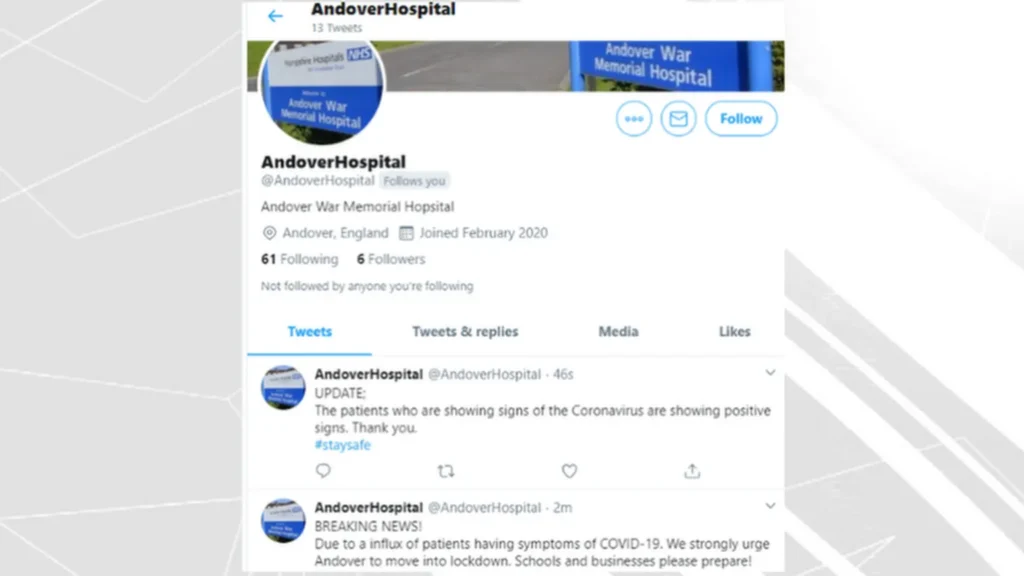
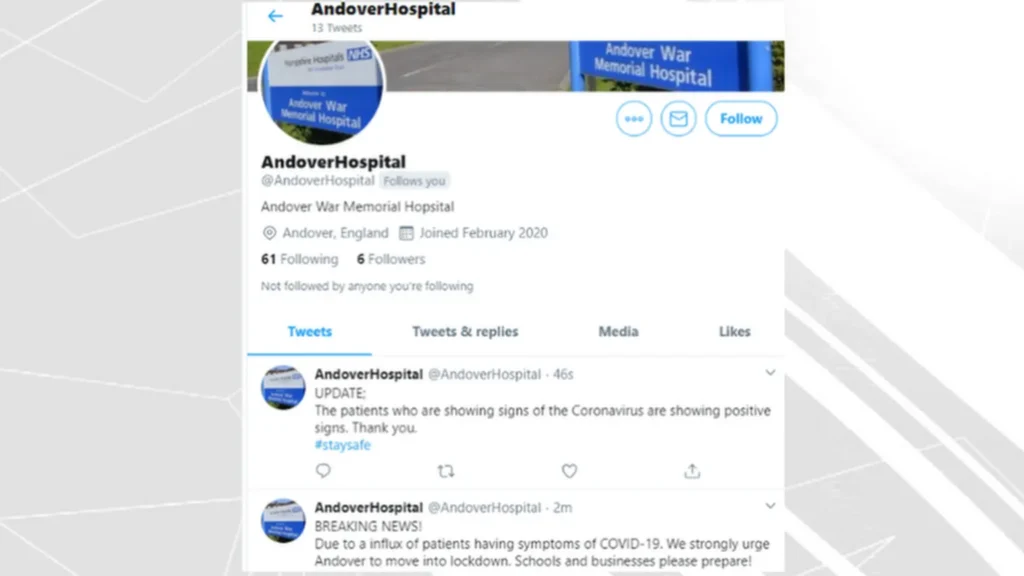
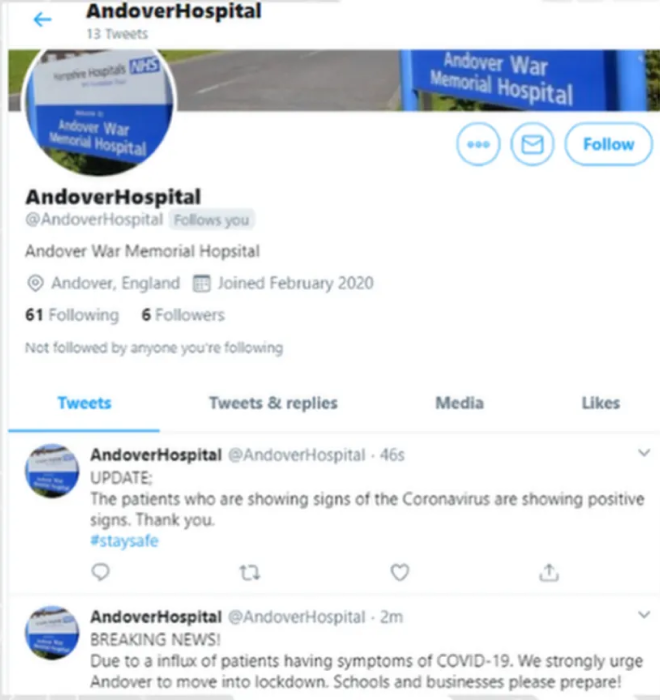
Additionally, the federal government suggests that some cyberattacks on critical sectors, including healthcare, come from state sponsors. Countries that view others as rivals might back hacking efforts to disrupt important infrastructure, according to the American Hospital Association. Infamous examples include the North Korean WannaCry, the Russian Nonpetya, and Iran’s SamSam attack.
Cybercriminals also attack healthcare organizations for the following reasons:
- Hospitals can’t afford to be offline for long because they must tend to sick patients promptly, which is why they often pay the ransom, despite the FBI advising against it.
- Hospitals hold personal, financial, and medical records, which bad actors see as valuable because they can sell them on the black market.
- Many healthcare systems use outdated software with security flaws. This makes it easier for hackers to break in. They also don’t update their systems on time, as they lack the time and people to do it, which increases the risk of a cyber attack.
- Hospitals use interconnected systems like electronic health records, patient monitors, and telemedicine. This makes it easier for a cyber attack to spread and cause more damage.
- Most hospitals don’t train their hospital staff on how to recognize phishing emails, making them good ransomware targets. Clicking on malicious links gives hackers a way into the system. The same can happen with weak passwords and poor setups for remote access tools. During the pandemic, hospital staff used these tools more, which made their workplace more vulnerable to cybercrime.
- Hospitals work with many partners and suppliers causing ransomware attacks because they also have weak security.
- There are a clear lack of cybersecurity experts working in healthcare. What is more is that and smaller institutions like rural hospitals, don’t even have the budget for cybersecurity.
Hospital and ransomware examples
A 2023 survey by the Ponemon Institute found that over 80% of healthcare providers faced at least one cyberattack in the previous year. Here’s a breakdown of some of the most recent cyber attacks on hospitals involving ransomware:
Change Healthcare attack (February 2024)

In February 2024, Change Healthcare, a major health insurance company was attacked by the ALPHV/BlackCat group. The ransomware attack disrupted healthcare claims processing, billing, and patient eligibility checks across America. It caused delays in prescriptions, patient discharges, and medical worker paychecks.
UnitedHealth Group, Change Healthcare’s parent company, paid $22 million in ransom to regain access to their systems. However, the response to the attack has cost the company over 2 billion, therefore it’s one of the worst cyberattacks on the U.S. healthcare system so far.
The ransomware gang is being pursued by international law enforcement, but no arrests have been made so far. The good news is that this cybersecurity incident has increased cooperation between private and public sectors to boost cybersecurity in healthcare.
Ascension ransomware attack (May 2024)
In May 2024, the Ascension health system with 140 hospitals in 10 states was hit by a ransomware attack. This incident caused delays in patient care and issues with electronic health records.
With systems down, staff relied on handwritten notes, faxes, and basic spreadsheets, which caused various care lapses. A nurse at a hospital in Wichita, Kansas almost gave a baby the wrong dose of medicine because the paperwork was confusing.
There were also delays in receiving lab results, which caused severe incidents like a woman going into cardiac arrest and dying after waiting four hours for crucial lab results.
Ascension used emergency procedures and worked with cybersecurity experts to handle the attack, which made them lose millions of dollars in payouts, recovery efforts, and operational losses.
Synnovis ransomware attack (June 2024)
In June 2024, a ransomware attack hit Synnovis, disrupting services at King’s College Hospital and Guy’s and St Thomas’ NHS trusts in London.
Over 800 surgeries and 700 outpatient appointments were postponed. Some C-sections were delayed, and 18 organs were sent to other trusts. Many tests were stopped, with only urgent blood tests being done.
By late June, Synnovis restored most services. However, some problems persisted. The attackers leaked some stolen data online, but it didn’t include complete patient test results. The investigation into the breach is still ongoing.
What patient-care experiences are under attack from ransomware?
Ransomware attacks affect both hospitals and patients, which is why the healthcare industry must take cybersecurity seriously going forward. Here’s how ransomware attacks can impact patients:
Delayed treatments
When hackers lock a hospital’s computer systems with ransomware, doctors and nurses can’t access electronic patient information or medical histories. This means they have to spend extra time gathering information manually, which delays the diagnosis and treatment of patients.
Canceled appointments
Ransomware can force the cancelation of regular check-ups, surgeries, and other medical procedures. This happens because hospitals can’t use their scheduling systems or access patient records to prepare for these appointments.
Disrupted emergency services
If a hospital is hit by ransomware, it might have to redirect ambulances to other hospitals because it can’t provide necessary care. This means patients who need immediate help might have to wait longer to get to a hospital that can treat them.
Medication errors
When doctors and nurses can’t access electronic medical records easily, they can’t check what medications patients take. This can result in mistakes in prescribing new medications, such as giving the wrong drug or dosage, which can harm patients.
Communication problems
Hospital staff usually exchange important information through email and internal messaging systems. Ransomware can shut down these systems and prevent doctors, nurses, and other staff from coordinating patient care and handling urgent cases.
Diagnostic equipment down
Ransomware can also disable advanced medical devices like MRI and CT scanners in hospitals because they’re all connected to their computer networks. This can prevent doctors from testing and diagnosing patients.
Increased patient deaths
All of the issues we just discussed can cause more patient deaths in hospitals, especially if urgent cases don’t get the treatment they need in time.
What is the main fear that ransomware attacks center around?
The main worry about ransomware attacks isn’t the lost finances, although the true cost of ransomware attacks is high. It’s the disruption of patient care that can cause medical errors and higher death rates when computer systems are necessary to process all treatments. In 2022 a 3-year-old patient received a dangerous overdose of pain medication because the hospital’s computer systems were down during a ransomware attack. This goes to show how important it is for healthcare providers to have accurate patient information on hand at all times.
Ransomware attacks can also delay procedures and tests, increase hospital stays, and cause more complications for patients.
Overall, the main fear that ransomware attacks center around increased death cases. Of course, there’s also the fear of sensitive patient data being sold on the black market, which can harm both the patients and ruin a hospital’s reputation.
How can hospitals protect themselves from cyber-attacks?
The evolution of ransomware has come a long way, which is why federal regulators constantly push for better healthcare cybersecurity.
The Cybersecurity and Infrastructure Security Agency (CISA) released new guidelines for hospitals, whereas the Department of Health and Human Services (HHS) introduced a cybersecurity strategy with similar goals.
However, CISOs can prevent ransomware attacks by taking the following steps against ransomware and other types of malware:
- Regular software updates: Hospitals should keep all their systems and software up-to-date. Hackers often exploit old software with security holes. Regular updates fix these weaknesses and protect against cyber threats and attacks.
- Strong password policies: Hospitals need strong password policies. This means using complex passwords, changing them regularly, and not reusing them across different systems.
- Employee training: Hospitals should regularly train hospital staff to spot phishing emails to mitigate the risk of phishing attacks. Training also helps employees recognize other common attack methods and reduces the chance of accidental breaches.
- Backup systems: Regularly backing up all data helps hospitals quickly restore their systems if a ransomware attack happens. These backups should be secure and separate from the main network.
- Access controls: Limiting access to sensitive information to only those who need it can help prevent unauthorized access. Adding multi-factor authentication provides extra security.
- Incident response plan: Hospitals should have a clear and practiced incident response plan to respond quickly and effectively to a cyber attack, reducing damage and downtime. For example, during a suspected cyber attack, the staff at St. Margaret’s Health turned off their phones and computer systems to stop the attack from spreading and to protect patient data.
- Regular security audits: Conducting regular security audits helps find and fix vulnerabilities in the hospital’s network before attackers can exploit them.
- Investment in cybersecurity: Hospitals should invest in advanced cybersecurity tools and technologies to protect their health information and systems.
What are the latest cyber security measures for hospitals in 2024?
The Advanced Research Projects Agency for Health (ARPA-H), a new agency within the National Institutes of Health, has launched the $50 million UPGRADE program to help hospital IT teams enhance their cybersecurity.
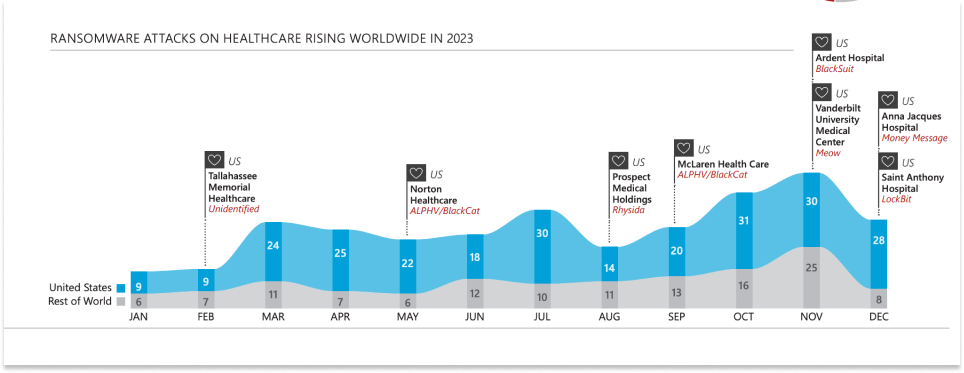
Data Source: Cyber Threat Intelligence Integration Center (CTIIC) report entitled, “Ransomware Attacks Surge in 2023; Attacks on Healthcare Sector Nearly Double.”
The UPGRADE program (Universal PatchinG and Remediation for Autonomous DEfense) will help hospitals quickly fix vulnerabilities in their systems and reduce patch times from months to days or weeks.
This is great news because as we’ve just discussed, healthcare has experienced some of the biggest ransomware attacks in 2024. However, hospitals should also take matters into their own hands and implement some of the most recent cyber security practices, such as the following:
1: Third-party management
Consider involving reputable cybersecurity firms like CybelAngel for better protection. You can request a demo here to see how our EASM platform defends against external attacks.
By using CybelAngel’s services, hospitals can avoid big financial losses, protect patient data, and keep their operations running smoothly.
2: Regular backups and network segmentation
Hospitals should do regular data backups and use network segmentation to fight ransomware. Regular backups make sure data can be restored if attacked, while network segmentation keeps critical systems separate to stop ransomware from spreading.
3: Multi-factor authentication (MFA) and endpoint security
Many hospitals have started using multi-factor authentication (MFA) and improved endpoint security, following advice from CISA. MFA adds extra steps to verify a user’s identity, making it harder for unauthorized access, while endpoint security protects devices connected to the network.
4: Education and anti-phishing training
Hospitals should train their staff to recognize phishing emails and follow good cybersecurity practices. Many hospitals have suffered ransomware attacks through phishing, leading to financial losses and compromised patient data.
5: Public-private partnerships and government guidelines
Hospitals should work more closely with cybersecurity firms and government agencies like CISA and HHS. These partnerships help share information and resources to fight cyber threats.
Inspired by Australia’s proactive defense during the COVID-19 pandemic, U.S. Senators want similar actions in the U.S. This cooperation could help prevent large-scale attacks like those on Change Healthcare and Ascension, which caused major disruptions and increased costs.
Prevent a crisis with your organization’s healthcare data
Ransomware is a growing threat to hospitals, endangering people’s lives and destroying financial stability. Don’t wait for a ransomware attack to improve your cybersecurity.
Request a demo today to see how we can help you protect your organization’s health care data to keep your operations secure and threat proof.