Emotet Malware: Wild, Wild Trojan
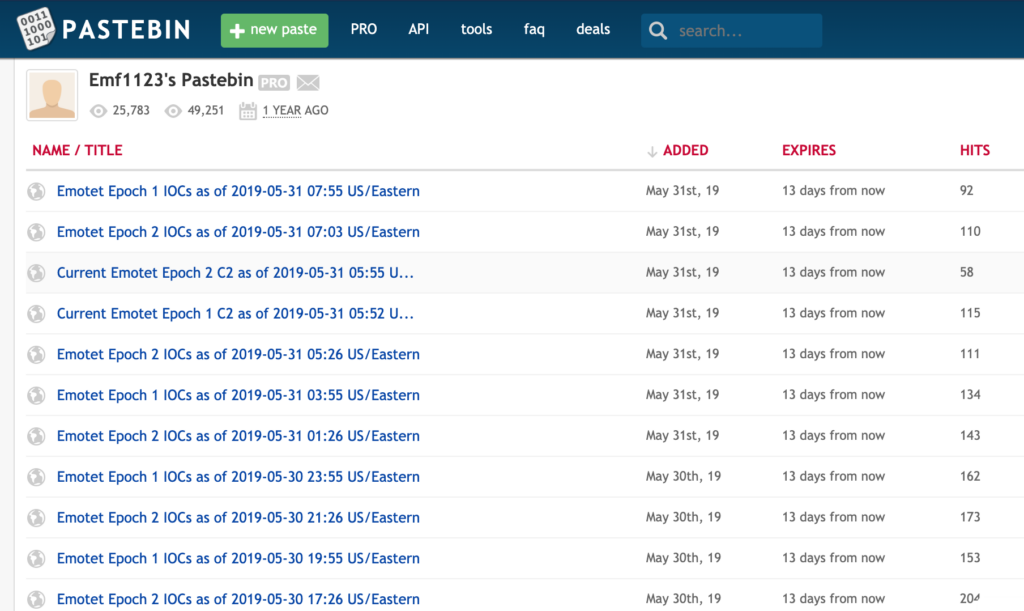
Here at CybelAngel, we’ve spent a significant amount of R&D effort focused on protecting our customers from compromises relating to exposed data found on Pastebin and other paste sites. But beyond leaked documents and exposed PII, paste sites also host the hard work of researchers and security actors that compile lists of sites compromised by malware. CybelAngel monitors these “Indicator Of Compromission” lists (IOCs), and if properties belonging to any of our customers are found on these lists, we use a variety of antivirus services to verify the infections and alert our customers accordingly. With the reemergence of the Emotet trojan near the end of 2018, these alerts are, sadly, becoming more frequent. Emotet, known since 2014, is an advanced and modular banking Trojan, mostly disseminating through malspam, and delivering a large variety of payloads. While the first version of Emotet was a simple Trojan (a malicious JavaScript file), the program has regularly gone through modification since then and is now a global polymorphic malware that can stealthily evolve and deliver other malicious payloads for further attacks. According to the US-CERT, “Emotet is one of the most widely distributed and actively developed malware families on the crimeware landscape today.”
Emotet, or the one-malware-band
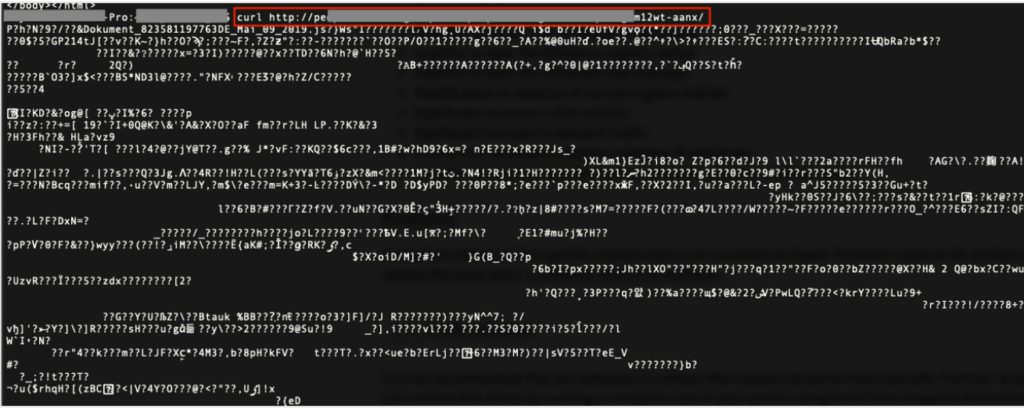
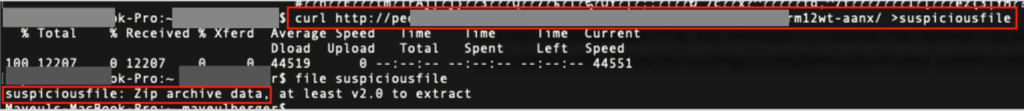
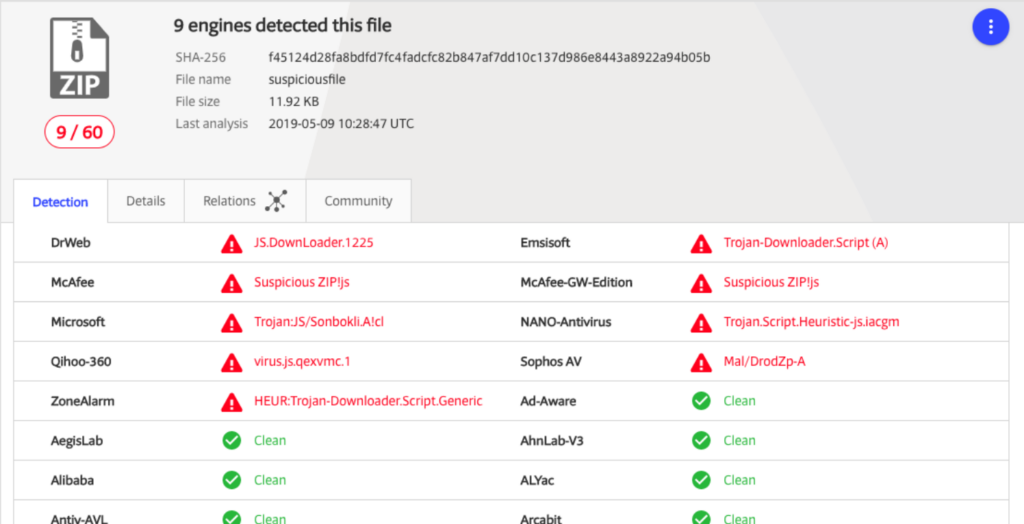
Indeed, Emotet appears to be extremely persistent: as a polymorph program, it can change its own appearance and signature and thus escape most anti-virus detections, as these are based on signature or hash recognition. The malware is also VM-aware and can deceive a sandbox analysis. Since it’s connected to a C2 server, the malware can receive the latest updates and adapt its modus operandi on the attacker’s input. Worse still, that connection allows it to download and drop secondary payloads on compromised machines, like other banking Trojans – particularly “Epoch2” and “Heodo”, or more recently “Trickbot” and “IceID”. As a particularly efficient and vicious program, Emotet entails severe risks for impacted companies: loss of data and internal information, destroyed by the malware; eventually leading to interruptions of regular operations. Financial losses can follow, as costs mount to both restore/replace infected systems and to resolve the aforementioned operations disruptions. Moreover, both corporate and employees’ financial data may get hacked, potentially leading to fraud schemes and robbery. Lastly, being hit by an Emotet campaign may induce severe harm to an organization’s reputation.
November 2018: reminiscence & new dissemination process
In November 2018, after months of low activity, a huge Emotet infection campaign was launched, targeting German and English-speaking users. Mass-phishing and malspams remain the primary infection vector since Emotet’s creation. However, some details have evolved: while the earliest spam campaigns were mostly based on infected attachments (the malware being activated thanks to the files’ Macros), the recent campaigns instead share links to compromised websites, from which the Emotet trojan is downloaded. Once the first payload is active, Emotet assures its persistence (by implementing itself in the registry) and establishes a connection with a C2 server that sends it back secondary payloads and attack modules that extend Emotet’s capabilities to network propagation, certificate theft, data gathering, and more. As this new infection process transforms compromised corporate websites into powerful leverages to spread Emotet, their number has been increasing dramatically. Lists of sites and lists of Indicators Of Compromission are regularly published and updated by researchers and security actors.