Breaking the Killchain

Table of contents
The “Kill Chain” is a military term that the cybersecurity industry has widely adopted. While it is a valuable educational tool, its usefulness in planning is more tenuous. Instead of the typical seven-step “kill chain” here at CybelAngel, we focus on a simpler three-step model that helps cybersecurity professionals understand when and where they can interrupt a cyberattack.
The Three-Step Model:
At CybelAngel, we see cyber attacks having three steps: reconnaissance, weaponization, and attack. 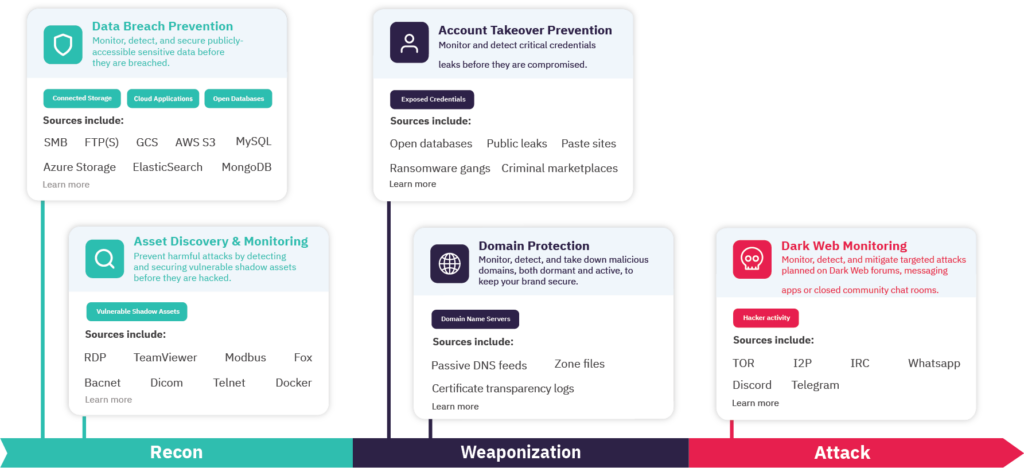 The first is reconnaissance. During the reconnaissance phase, threat actors collect information on your company, such as leaking data, vulnerable assets (like RDPs), and commonly used websites. This phase is all about finding mistakes that can be taken advantage of during the weaponization and attack phases. Weaponization is the second step of a cyber attack. This is the phase in which threat actors will interact with their targets. Typically these interactions are account takeovers using previously exposed credentials to access vulnerable digital assets like RDPs. Alternatively, some threat actors will use spoofed domains to collect credential information. Using the access gained during this phase, threat actors will infect systems. The final stage is the attack phase. The attack phase is usually when data encryption and exfiltration occur. Once this is accomplished, a company’s best option is to turn to the dark web to locate leaked data or remove it.
The first is reconnaissance. During the reconnaissance phase, threat actors collect information on your company, such as leaking data, vulnerable assets (like RDPs), and commonly used websites. This phase is all about finding mistakes that can be taken advantage of during the weaponization and attack phases. Weaponization is the second step of a cyber attack. This is the phase in which threat actors will interact with their targets. Typically these interactions are account takeovers using previously exposed credentials to access vulnerable digital assets like RDPs. Alternatively, some threat actors will use spoofed domains to collect credential information. Using the access gained during this phase, threat actors will infect systems. The final stage is the attack phase. The attack phase is usually when data encryption and exfiltration occur. Once this is accomplished, a company’s best option is to turn to the dark web to locate leaked data or remove it.
Breaking the Chain:
With this model it is clear that the first two phases have more opportunities to interrupt a cyber attack or, in our words, to break the chain. During the reconnaissance phase, two digital risk protection tools can help to reduce a company’s cyber attack chances:
- Data Breach Prevention is helpful in preventing cyber attacks by locating exposed company data on the publically available internet. This restricts data collection by threat actors, reducing access to credentials, documents, or information used in social engineering.
- Asset Discovery and Monitoring helps companies locate exposed or vulnerable digital assets such as remote desktop protocols that threat actors use to gain access to company networks.
During the weaponization phase, there are two digital risk tools that will allow a company to interrupt an incipient cyber attack:
- Account Takeover Prevention locates exposed credentials and informs SOC teams which user accounts need to be resecured. This helps to remove the credentials that threat actors use during cyber attacks.
- Domain Protection is another digital risk protection tool that allows companies to locate fraudulent domains used to infect users or collect credentials.
During the final attack phase, a company’s best option is to use Dark Web Monitoring to locate leaked data for remediation. This, however, is often an after-the-fact level of protection.
Proactive Actions:
As seen above, interrupting a cyberattack during the first two phases is the most effective option. Research bears this out, with IBM noting that companies with proactive AI security see an 80% decrease in the costs associated with a data breach or cyber attack. Even in a digital world, the maxim “an ounce of prevention is worth a pound of cure” holds true.
