CybelAngel’s 2024 State of the External Attack Surface Report

Table of contents
Read the ultimate cybersecurity primer for your 2024 EASM strategy.
192 trillion data points and counting.
In 2023 we scanned 6 billion data points on the internet each day to keep our clients’ data secure.
Our 2024 State of the External Attack Surface Report, written by CybelAngel’s CISO, Todd Carroll, is a deep dive into delves into the realm of preventing cyber risk from an external attack surface management perspective.
It is for CISOs and SOC teams everywhere to review and use as a primer for a securer 2024.
This blog details what you can expect to encounter in our bumper 2024 report on the state of external attack surface management.

Unveiling 2024’s EASM outlook: A dive into the report’s framework
2023 witnessed significant global challenges including an explosion of AI and ChatGPT technology, escalating global conflicts, market volatility, and a major cyberattack on Wall Street that affected trillions of dollars in assets.
Cybercriminals seized opportunities, capitalizing on global conflicts and human error to infiltrate and cause havoc.
Amidst an unprecedented surge in threats, what steps should CISOs take moving forward?
This report’s framework tackles this question in four core areas outlined below.
More interested in skipping to the executive summary? You can read it here.
How can CISOs improve their EASM security posture?
Within this report, our CISO Todd Carroll has provided all CISOs with a guide to emerging EASM threats, risk management and actionable insights for better prioritization for your SOC team to side step cyber issues that impact your external IT perimeter.
Here is a breakdown of the 4 core areas of focus found in the report:
1: The external attack surface management landscape.
2: 8 cyberattack use cases and key learnings for CISOs
3: Recommendations for better prioritization in 2024
4: 3 Critical EASM threats to watch out for this year
EASM data report highlights you need to note
The key highlights of this CybelAngel are a window into how companies are facing increasingly numerous and sophisticated attacks, especially when it comes to third party risk and ransomware.
- The number of exposed assets and data doubled in 2023, from 740,000 to 1.5 million TBs.
- 79% of cyber risks are found outside a company’s internal IT perimeter.
- Ransom demands have increased by 40% due to the development of RaaS (Ransomware-as-a-Service) services.
- Exposed data from cloud services increased by 11% verus 2022 data.
Discover more data points within this EASM report by accessing it here.
8 cybersecurity use cases to evaluate with your team
What can we learn from examining 8 use cases from the vulnerabilities that spawned last year’s biggest cyber attacks?
When it comes to a shifting web of security issues and risks, we still have a lot to learn. Within this EASM report we take a look at organizations who experienced everything from exposed assets to ransomware attacks, to help you avoid the same devastating outcomes.
In this report we take a share how 8 CISO dilemmas can become 8 actionable insights.
- Deep Diving into the Biggest Breach of 2023
- How Human Error Exposed 3.8 Billion Records
- Why is Ransomware so Lawless?
- How are Resurgent Infostealers Fuelling Unease?
- Exploring Cloud Exposure Risks in Healthcare
- Third Parties, Threats and Stolen Data
- Future Threats and File Servers Spell Trouble
- Available Assets and Vulnerabilities
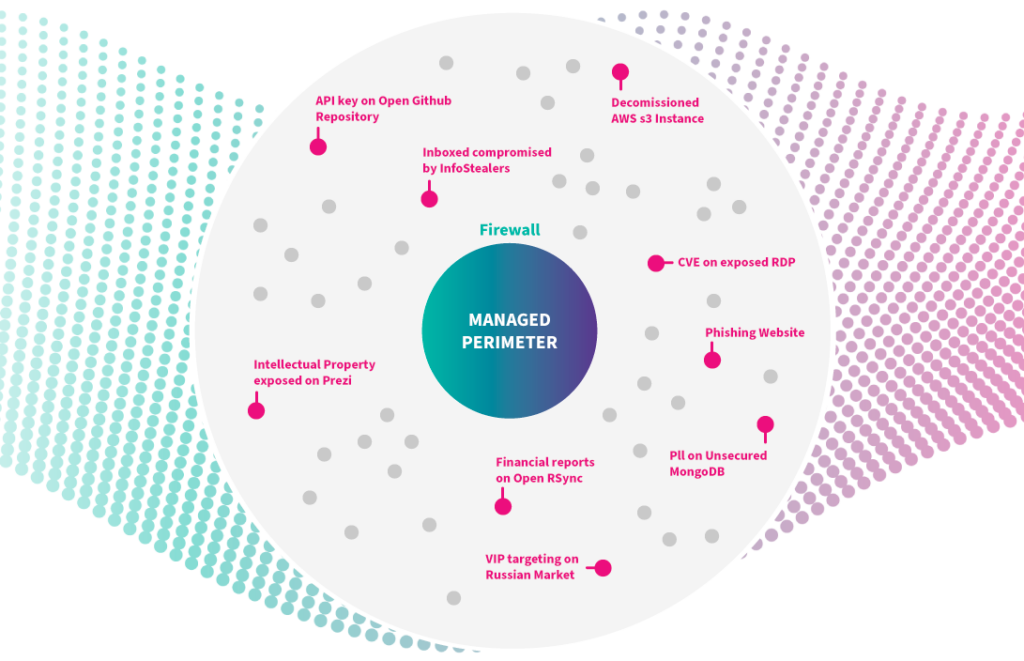
Above is an overview of what is occurring outside of your managed IT perimeter.
Here are the focus areas that our recommendations touch on:
- Continuous asset discovery: How can we continuously monitor and identify of all assets in an organization’s external attack surface?
- Vulnerability scanning and management: Why is there a need for regular vulnerability scans to identify weaknesses in your infrastructure?
- Automated alerting and threat intelligence: Is an automated alert system helpful if threat intelligence is non-stop? Are there alternatives?
- Supply chain risk management: What are major risks associated with third-party vendors and supply chain partners that CISOs need to review?
- Dark web monitoring: How can SOC teams better use dark monitoring tools to find sensitive data or credentials associated with their organization?
- Brand protection and anti-phishing: What can be done when it comes to brand reputation versus stealthily orchestrated phishing attacks?
- Data leakage prevention: Can mor proactive monitoring prevent of data leakage incidents in 2024?
- Regulatory compliance: Is there a way for CISOs to ensure compliance with relevant data protection regulations and also cut down insurance premiums?
The unique CybelAngel vantage point
How does CybelAngel have such a unique vantage point to share with CISOs and SOC teams?
It is clear that the vast amount of data we analyzed is just one part of the story.
We’ve woven our unique EASM vantage point alongside these insights to create the most comprehensive overview of external attack vectors.
Here is how.
We provide EASM coverage to top-tier organizations
EASM is a potent vector.
The biggest brands in the world including Pfizer, Trimble, Sanofi, Signify and Cushman & Wakefield understand this cyber risk and trust us to protect outside their managed IT perimeter.
We block cyber risks to business ops
We fortify organizations via preventative cybersecurity and the continuous monitoring of their external attack surface management
We only share real cybersecurity alerts
We go further than other EASM providers when it comes to continuously monitoring cyber risk. Experienced analysts at CybelAngel mean that we share contextualized reports that cut through the noise and avoid false positives.
We provide accurate risk assessment
Our technology allows us to comb through 6 billion data points every. We combine machine learning models alongside our dedicated analysts to accurately assess risks and speed up remediation.
Get CybelAngel’s 2024 State of External Attack Surface Management report now

Here is a recap of why this report is essential reading:
- Discover the importance of external attack surface management, and why proactive strategies help to mitigate risks in 2024.
- Understand how EASM strategies can help you against evolving cyber threats like infostealers, ransomware and third party sensitive data breaches.
- Find actionable recommendations, from one CISO to another; from how to implement best practices, identify vulnerabilities, to prioritizing remediation efforts for enhanced cybersecurity in 2024.
Access the complete annual report for comprehensive information here.