Cybersecurity vs. Risk Management

Table of contents
Frank worked in Information Security as a System Administrator. He had spent most of the day thwarting bad guys and was frustrated. After five years, he was in the same job as when he started. Frank felt locked in a cage, working from home day in and day out, fighting off threats to his company’s IT infrastructure. It seemed like the more data they moved to the Cloud, the more data was vulnerable to attack. Frank was concerned. His job seemed increasingly stressful as the number of threats to their network increased.
Prove value
 As a Systems Administrator in InfoSec, Frank wondered how he could get a promotion — and a pay raise. How could he prove the value of his work? Frank ran a report to see how many trouble tickets he addressed in the last year. He was stunned to find that each month, he addressed more tickets than the previous month. When he started, he was addressing about 100 threats per week. Now five years later, he was addressing about 100 threats per day, sometimes more. Whenever there was a vulnerable time, like over the holidays, it seemed like the threats increased. In the last five years, Frank’s work volume had increased by 5x. This realization made him eager to get out of his stuffy office. He needed fresh air. Frank stepped out the door and walked to the local park. There was a bench in the shade where an elderly gentleman sat. Frank asked the man, “Mind if I sit?” “I’d be glad for the company,” said the man. Frank sat down and stared into the distance, distress written on his face. After a while, the two men started to chat. It turned out, the man was a retired Chief Operations Officer. When the man asked Frank what he did, it all came tumbling out.
As a Systems Administrator in InfoSec, Frank wondered how he could get a promotion — and a pay raise. How could he prove the value of his work? Frank ran a report to see how many trouble tickets he addressed in the last year. He was stunned to find that each month, he addressed more tickets than the previous month. When he started, he was addressing about 100 threats per week. Now five years later, he was addressing about 100 threats per day, sometimes more. Whenever there was a vulnerable time, like over the holidays, it seemed like the threats increased. In the last five years, Frank’s work volume had increased by 5x. This realization made him eager to get out of his stuffy office. He needed fresh air. Frank stepped out the door and walked to the local park. There was a bench in the shade where an elderly gentleman sat. Frank asked the man, “Mind if I sit?” “I’d be glad for the company,” said the man. Frank sat down and stared into the distance, distress written on his face. After a while, the two men started to chat. It turned out, the man was a retired Chief Operations Officer. When the man asked Frank what he did, it all came tumbling out.
Wisdom of strangers
The gentleman asked, “What do you do for work?” “I work in Information Security at a large company,” Frank answered. “Yes, but what do you do?” the man asked. “I fight off bad guys —I stop unauthorized people from accessing our company data,” Frank answered proudly. “And how is that going?” the man asked. Frank’s frustration with his job and his increasing workload spilled over. He explained about sensitive data going to the Cloud and increasing the chances for hackers to steal that data. The man’s face lit up and he said, “You mean the more you share data in the Cloud, the more your risk goes up?” “Yes,” Frank said. “No matter how hard I work, I feel like I’m on a hamster wheel, running to fight off threats that never end.” After some silence, the man turned to Frank and said: “It’s all about Risk. The two main drivers of business are Opportunity and Risk. To get ahead, you need to show your company that you can diminish their Risk.”Frank thought about that awhile and said, “but I am diminishing risk with each threat that I prevent.” “Yes, but you are talking about threats,” said the man, “I am talking about risk. Cybersecurity is a business risk. You can never diminish the onslaught of threats — but you can diminish the risk.” Frank thought about that awhile and said, “but I am diminishing risk with each threat that I prevent.” “Yes, but you are talking about threats,” said the man, “I am talking about risk. Cybersecurity is a business risk. You can never diminish the onslaught of threats — but you can diminish the risk.” He said to Frank, “Let’s get to basics, okay?” “Okay,” Frank said. The gentleman asked, “For your company, what are your top risks? Would a cybersecurity hack risk your Finances, Operations, Productivity, or Reputation?” Frank let out a puff of air, “Yes, a cyber hack could risk our Finances, Operations and Productivity — and what was the last risk?” “Reputation” said the man. “Yes, definitely, our Reputation is at risk, too,” said Frank, “Now what?” “Now rank your business risks from greatest priority to least priority, according to which risk poses the greatest harm to your company,” the man said. Frank thought about it and said, “We run an online software company. Our software needs to be available 24 hours a day, 7 days a week. If that software is hacked, our business would likely stop,” Frank said. “Aha!” exclaimed the man. “Your greatest risk might be Operations. You need to keep your network running to host your software. Is that right?” “Yes,” Frank answered. “So, you now know your top risk,” the man continued, “if you want to get ahead in your career, you need to quantify the risk of network outage to your business, then diminish that risk. When you can prove — quantifiably — that you have diminished business risk for your company, you will get ahead in your career.” Frank looked at the man, wide-eyed. The man continued, “You know, son, you could spend the rest of your life fighting off threats one-by-one. Or you could address the biggest risk to your business — and do something about it.” The retired businessman nodded to himself in satisfaction, feeling like his old self. Frank no longer saw an elderly man sitting next to him. Frank saw a COO with a wealth of knowledge and experience.
Flip the view from threat to risk
All Frank ever thought about were threats. How could he get into the risk game? Frank chatted with the man a bit more and thanked him for his insights. Frank flew home thinking every step of the way about what the man said. What were the top risks to our business? And how could he quantify them? Back at his computer, Frank googled “cybersecurity risk and threats.” And he found that the COO was right. Threats were one thing — but risk was something else entirely. Frank made a chart of threats and risks so he could organize his thoughts: 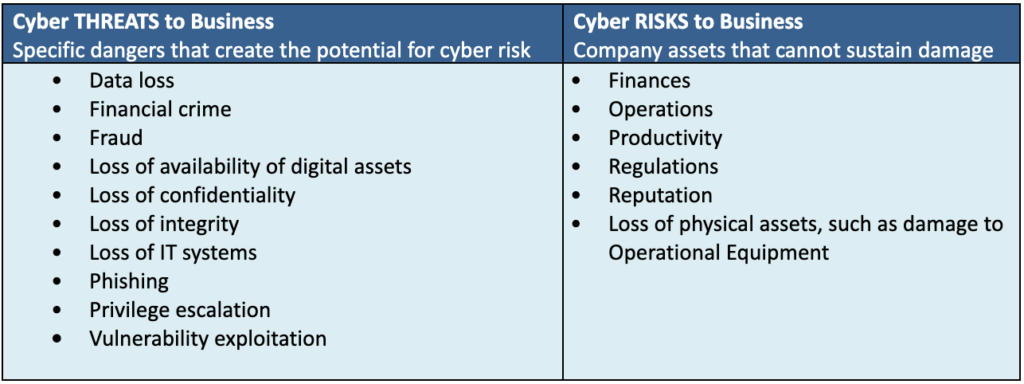 The gentleman’s words echoed in Frank’s mind: “if you diminish risk for your entire organization, you’ll get that promotion you want.” Frank found a chart that showed the evolution of cybersecurity at large enterprises. He found that his company was in the same stage as most companies, according to McKinsey. For most companies, the risk-based approach is the next stage of their cybersecurity journey.
The gentleman’s words echoed in Frank’s mind: “if you diminish risk for your entire organization, you’ll get that promotion you want.” Frank found a chart that showed the evolution of cybersecurity at large enterprises. He found that his company was in the same stage as most companies, according to McKinsey. For most companies, the risk-based approach is the next stage of their cybersecurity journey. 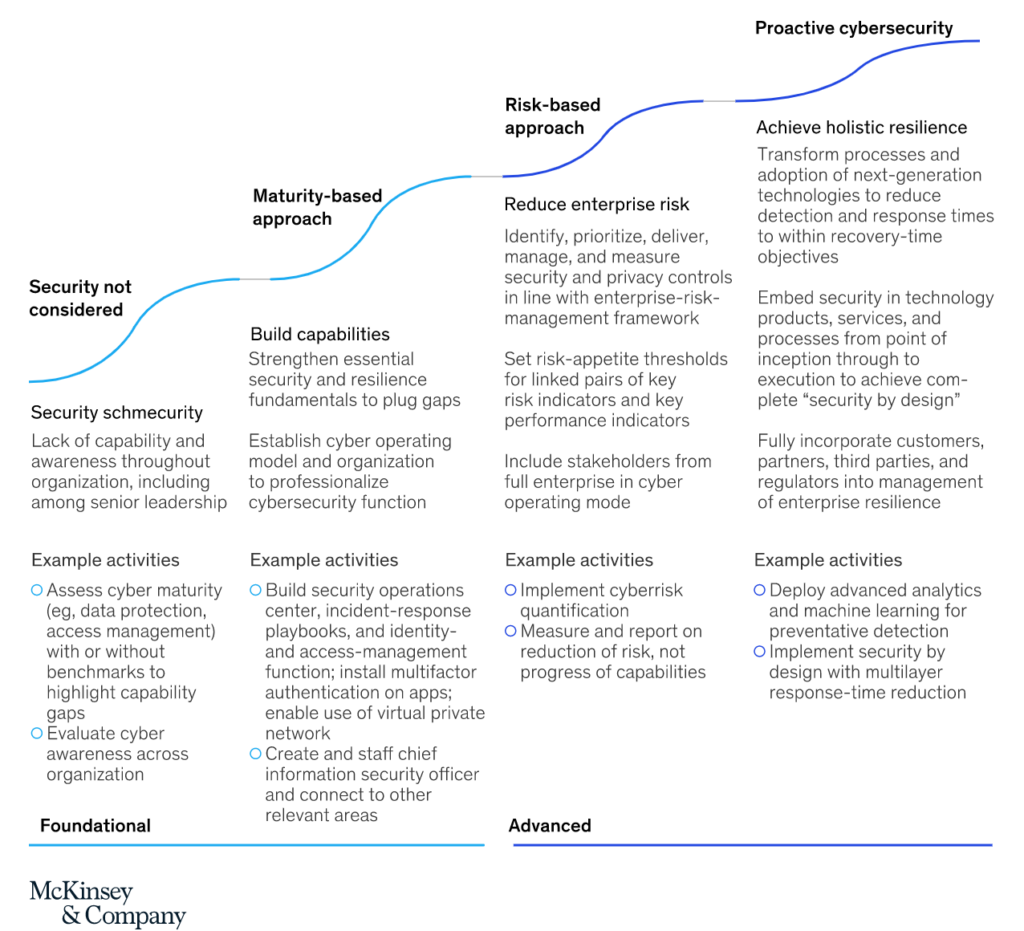 For cybersecurity, his company was using an approach based on maturity. His company needed to evolve to an approach based on risk, then move on to proactive cybersecurity.
For cybersecurity, his company was using an approach based on maturity. His company needed to evolve to an approach based on risk, then move on to proactive cybersecurity.
From cybersecurity to risk management
Now Frank was thinking about risk, not threats. Frank could prevent threats all day, but he would never get ahead in his InfoSec career. To get a promotion, he needed to focus on diminishing risk to his organization. He thanked the old man for opening his eyes to cybersecurity versus risk management. Frank also saved the chart from McKinsey for the presentation he would prepare for work.
Concerned with your risk?
If your company is evolving its approach to cybersecurity, learn your risk for a data breach. Click here for a free data leak score. At CybelAngel, we help global organizations decrease risk to their sensitive data. Because data leaks are inevitable; but damage is optional.