Lumma Stealer: Inside the Malware-As-A-Service Threat

Table of contents
Infostealers are a subtle (but devastating) threat. They sneak in, grab credentials, cookies, and files, then hand them off for fraud or ransomware. LummaC2 Stealer is one of the most prolific, and one of the hardest to keep down.
Active since 2022, it’s sold as Malware-as-a-Service and widely deployed through phishing and malvertising. Even after Europol and Microsoft disrupted its infrastructure this spring, Lumma reappeared within weeks. The cycle continues… and so does the risk for businesses.
What is LummaC2 Stealer?
LummaC2, often shortened to Lumma, is an information-stealing malware written in C and first observed on Russian-speaking forums in mid-2022. It’s sold as Malware-as-a-Service (MaaS), and marketed to cybercriminals who want a plug-and-play way to harvest sensitive data.
The malware targets web browsers, cryptocurrency wallets, and two-factor authentication extensions before exfiltrating data to command-and-control/ C2 servers.
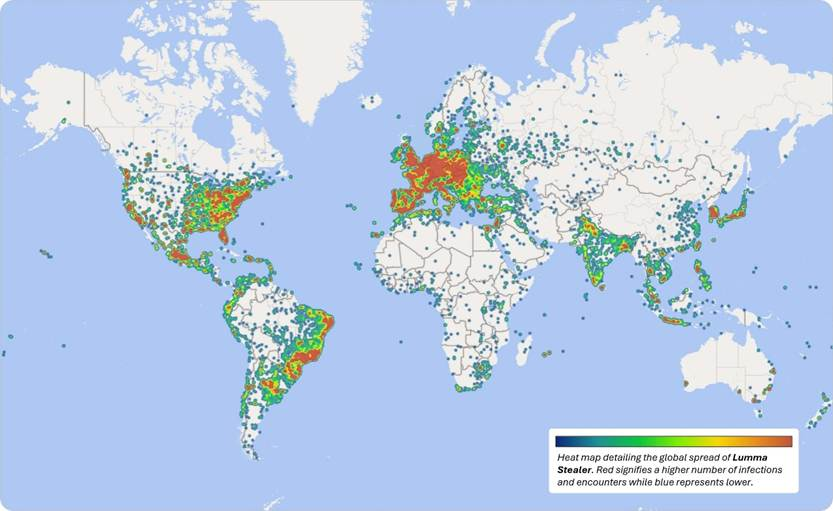
And it’s popular, with Lumma compromising nearly 400,000 Windows machines between March and May 2025 alone.
Despite a coordinated takedown from Europol and Microsoft in May 2025, Lumma’s operators quickly restored their infrastructure. For security teams, this resilience makes Lumma a persistent cybersecurity threat.
How Lumma Stealer infects victims
Lumma Stealer malware doesn’t rely on one delivery method. Its operators spread it through several common but effective initial access vectors, ensuring a steady stream of new infections.
- Phishing emails: Often delivered with HTML attachments or fake Captcha pages that push the user to run a malicious executable.
- Malvertising: Malicious ads and poisoned search results distributing loaders, cracked software, or fake installers.
- Fake repositories: GitHub and file-sharing sites seeded with bogus tools such as game cheats, serial key generators, or “free” utilities.
- Fake CAPTCHA pages: Compromised websites can use ClickFix techniques to lure people into clicking on fake CAPTCHA forms (see below).
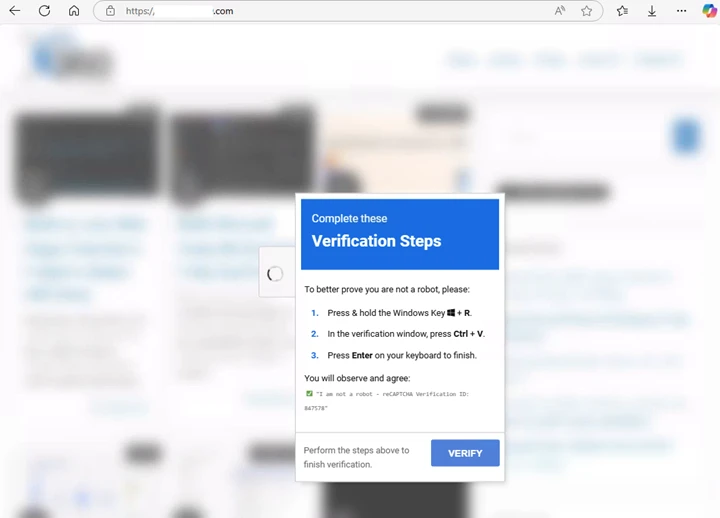
Each method has one common denominator: social engineering. In other words, they exploit human vulnerabilities. By disguising malware as something helpful or urgent, threat actors exploit human trust rather than breaking through hardened defenses. Once launched, Lumma immediately begins data exfiltration.
What information Lumma targets
Once installed, Lumma casts a wide net. Its modules are designed to harvest sensitive information that can be immediately sold, reused for fraud, or leveraged in further intrusions.
- Web browsers: Extracts saved credentials, cookies, autofill data, and browsing histories from Chrome, Edge, and other major browsers.
- Cryptocurrency wallets and 2FA extensions: Steals wallet files and intercepts authentication plugins, putting digital assets and MFA-protected accounts at risk.
- VPN clients and productivity apps: Collects session tokens and config files from VPN tools, Telegram, and email clients.
- Clipboard monitoring: Monitors clipboard contents and swaps cryptocurrency wallet addresses with attacker-controlled ones.
- Screenshots and system data: Captures desktop screenshots, system specs, and IP addresses to give attackers context for further exploitation.
Each data point has value. For example, credentials feed account takeover campaigns, cookies enable session hijacking, and system profiles help attackers tailor ransomware or fraud.
Evasion and anti-analysis techniques
Lumma’s operators invest heavily in staying invisible. The information stealer malware is engineered to frustrate static and dynamic analysis, rotate quickly, and hide C2 traffic in plain sight.
Here are some examples.
- Obfuscated code: Lumma’s internals are deliberately scrambled, making it harder for analysts and antivirus tools to see what’s going on.
- Constant updates: New versions appear frequently (Microsoft has tracked at least six), each tweaked to slip past security tools.
- Sandbox awareness: The malware can spot when it’s running in a virtual lab or sandbox, and will shut down to avoid detection.
- Payload delivery: Lumma is most often delivered as a Windows executable (EXE), fetched through loaders or malicious attachments such as HTML/ HTA files. These trigger PowerShell commands to download and run the Lumma binary.
- Hidden C2 servers: Command-and-control domains sit behind Cloudflare, with backups on Telegram and even Steam profiles. They’re encrypted and rotated often, which makes them tough to block for long.
All these methods mean that detecting Lumma isn’t straightforward.
Obfuscation hides its code… Sandbox checks block analysis… And fast-rotating C2 domains mean that indicators of compromise expire quickly.
This is why defenders need behavior-based detection and real-time intelligence to stay ahead. This is the kind of visibility that CybelAngel delivers when new infrastructure spins up.
Command-and-control infrastructure
Lumma doesn’t function on a single server. Instead, it layers its command-and-control, with domains hardcoded into the malware and fallback options if those fail.
In some builds, Telegram channels are checked first, while Steam profile pages provide another way to reach updated C2 addresses. All of this traffic runs through Cloudflare, making the servers harder to block or take down.
This is why stopping the Lumma Stealer campaign is so difficult. In May 2025, Microsoft and Europol seized over 1500 Lumma domains. But it was a short-lived victory. Within weeks, new Lumma Stealer infrastructure was online, and campaigns were once again active.

From stolen data to real-world threats

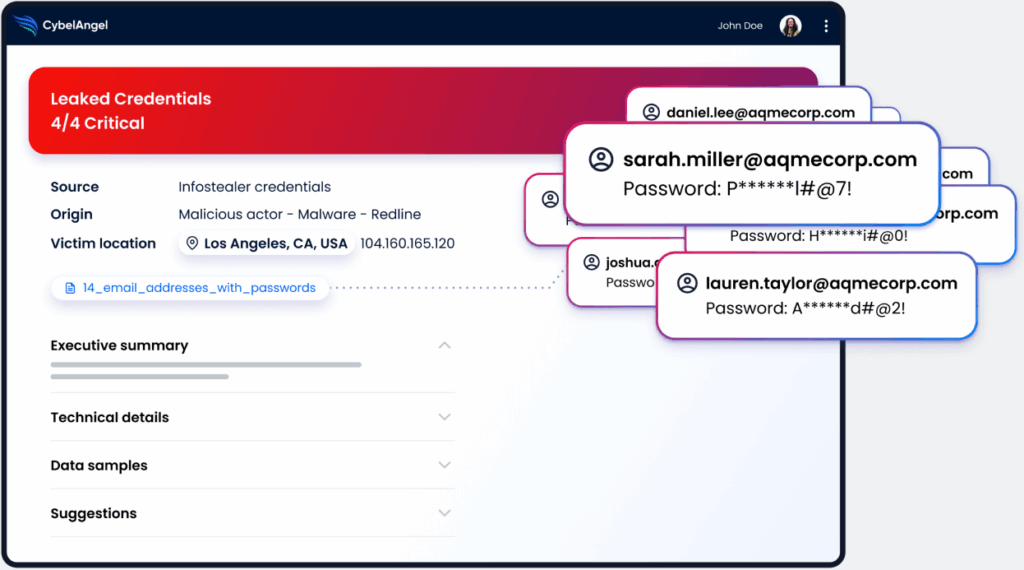
Stolen data is just the beginning. Once credentials and cookies are exfiltrated, they’re bundled and sold on dark web forums or shared directly with other cybercriminals. This fuels a thriving cybercrime market where access to corporate accounts is traded like currency.
From there, the risks escalate. Ransomware crews buy stolen logins to move laterally through networks. Fraud groups use them to hijack accounts or drain cryptocurrency wallets.
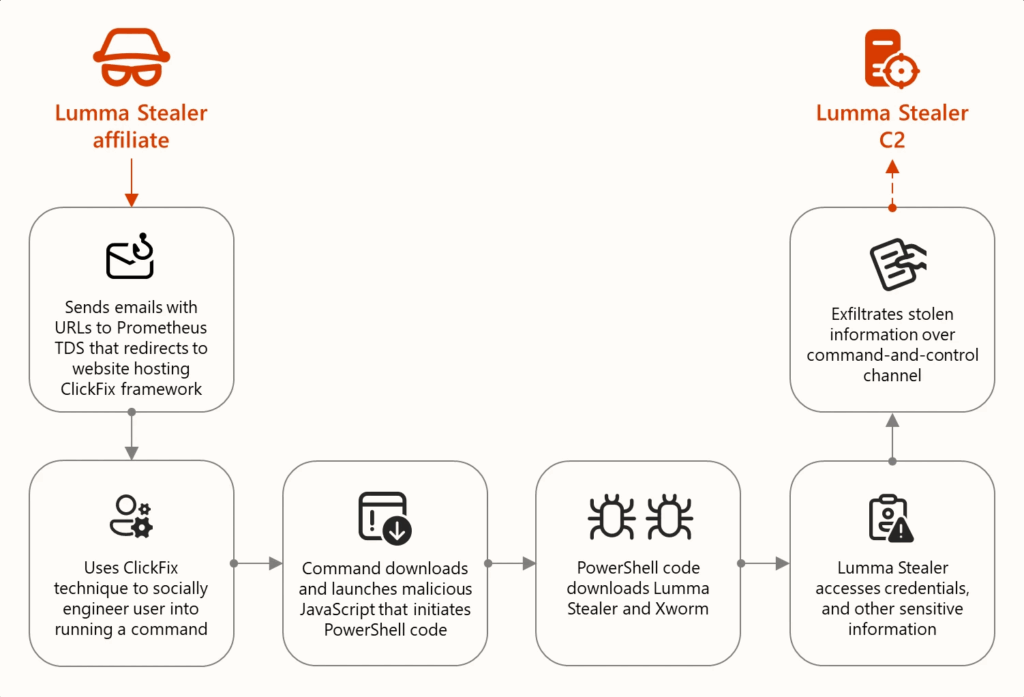
Consider a simple chain: a single employee’s VPN credentials are stolen, after they clicked a malicious link, and launch a JavaScript that starts the Powershell script.
Attackers log in, escalate privileges, and begin exploring the network. Within days, sensitive files are copied out, backups deleted, and ransomware deployed. What started as “just an infostealer” ends as a full-blown breach.
That’s why CISOs can’t dismiss Lumma or its peers. Each credential theft is a potential entry point, and without early detection, it can escalate quickly.
Detecting and defending against Lumma
Spotting Lumma cyber threats requires a mix of endpoint visibility and external intelligence. Traditional indicators fade fast, so defenders need layered methods to stay ahead.
1. Detection methods
Before fighting back, threat intelligence teams need to know what they’re up against. Here are some ways to track Lumma’s activity.
- Endpoint alerts: Flag unusual execution of EXE files or suspicious PowerShell activity.
- IOC hunting: Track domains, IPs, and file hashes tied to known campaigns.
- Sandbox analysis: Detonate suspicious files in a controlled environment to reveal behavior.
2. Defensive measures
Once teams understand the threat landscape, they can take steps to block Lumma Stealer in its tracks. Here are several techniques every team should follow.
- Enforce MFA: Hardware tokens reduce the value of stolen passwords.
- Monitor browser extensions: Keep an eye on unexpected browser plugins, especially those linked to 2FA.
- Block malvertising: Use secure browsing controls to cut off a key delivery vector.
- Leverage real-time intel: Map shifting C2 infrastructure and stop connections before data leaves the network.
CybelAngel strengthens this last line of defense by detecting compromised credentials and newly spun-up domains in real time. This gives security teams the chance to cut off exposure before attackers weaponize it.
FAQs
What is an infostealer?
An infostealer is malware designed to quietly collect sensitive information from an infected device (such as passwords, cookies, or wallet keys) and send it back to attackers.
How do infostealers work?
Once executed, infostealers run quietly in the background. They scan browsers, apps, and files for stored credentials, cookies, or wallet data, then exfiltrate that information to attacker-controlled servers. Some even use plugins to capture screenshots or monitor clipboard activity.
How do infostealers like Lumma spread?
They are usually delivered through phishing emails, malicious ads (malvertising), or fake software downloads that trick users into running the malware.
Why are cryptocurrency wallets targeted?
Wallets store private keys that give direct access to digital assets. Stealing them allows attackers to transfer funds instantly and anonymously.
What is Malware-as-a-Service (MaaS)?
MaaS is a business model where cybercriminals rent out malware to other attackers. It lowers the barrier to entry, letting even low-skill actors launch campaigns.
How do you detect and remove Lumma Stealer?
Detection involves monitoring for unusual executables or PowerShell activity, scanning for known indicators of compromise (IOCs), and detonating files in sandboxes. Removal requires isolating the endpoint, wiping the infection, and rotating all exposed credentials.
Why is credential theft so dangerous for businesses?
Stolen logins often lead directly to account takeover, ransomware, or data breaches. Even a single set of compromised credentials can open the door to wider compromise.
Conclusion
LummaC2 shows how fast infostealer campaigns adapt. Takedowns slow it down, but new versions and infrastructure appear almost immediately.
CybelAngel helps teams close that gap. By detecting exposures linked to Lumma and other infostealers in real time, it gives defenders the chance to act before stolen data turns into a breach. Book a demo to learn more.
