Domain Impersonation is Costing Banks Millions. Here’s What to Do About It.

Table of contents
Phishing isn’t a lone hacker with a fake email anymore. It’s an industrial-scale business. And financial institutions are prime targets, with domain impersonation and lookalike sites draining millions in trust and revenue every year.
Threat actors run entire phishing factories: automating domain typosquatting, deploying plug-and-play phishing kits with QR code phishing, and spinning up fake websites in minutes. Let’s unpack how these cybercriminals operate, and how to stop them in their tracks.
How large-scale brand impersonation works
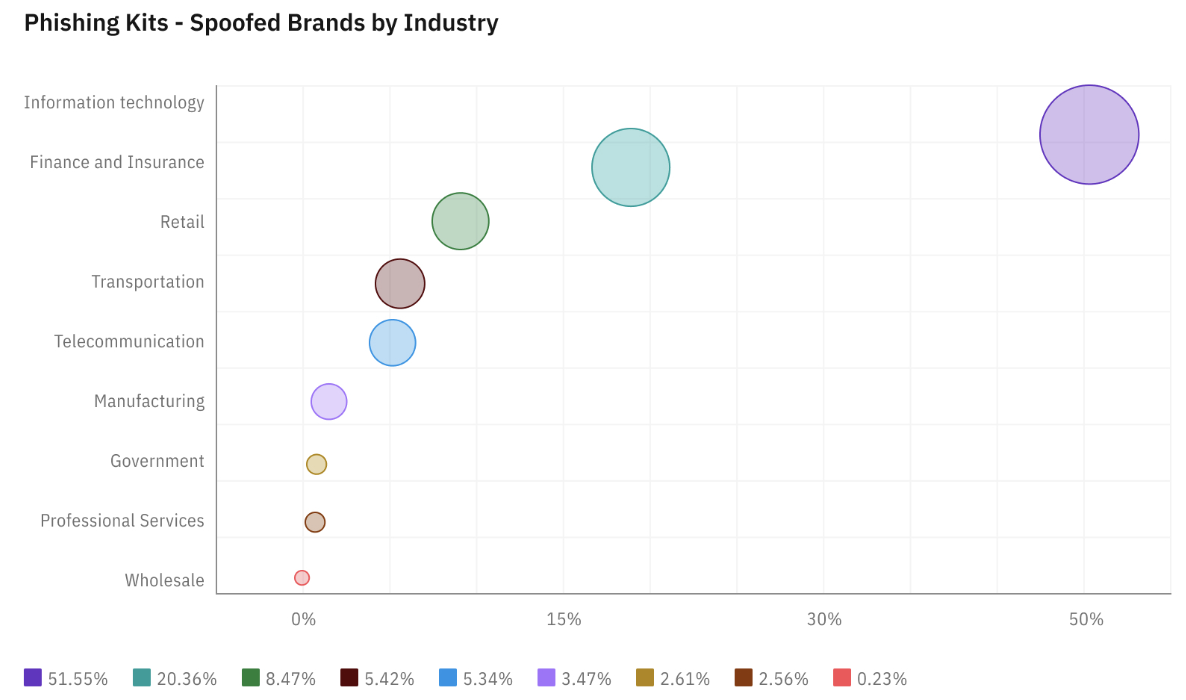
Brand impersonation is no longer a side hustle for opportunistic scammers. It’s a structured, profit-driven operation targeting banks and financial services around the clock. In fact, the finance sector is one of the most-impersonated industries.
Domain typosquatting is one of the simplest tricks in the playbook. Attackers register domains that look nearly identical to legitimate domains, such as by swapping a letter, adding a hyphen, or using a different top-level domain like .info instead of .com. A single typo is enough to fool customers into handing over sensitive information or login credentials.
Beyond typos, attackers can abuse subdomains and free hosting to mirror your brand’s pages perfectly. Combined with stolen logos, cloned CSS, and fake SSL certificates, these lookalike domains pass casual checks and evade basic email filters.
Financial brands are hit hardest because trust is everything. A single spoofed email or fake login page can drive fraud losses, customer churn, and compliance headaches.
Inside a modern phishing kit
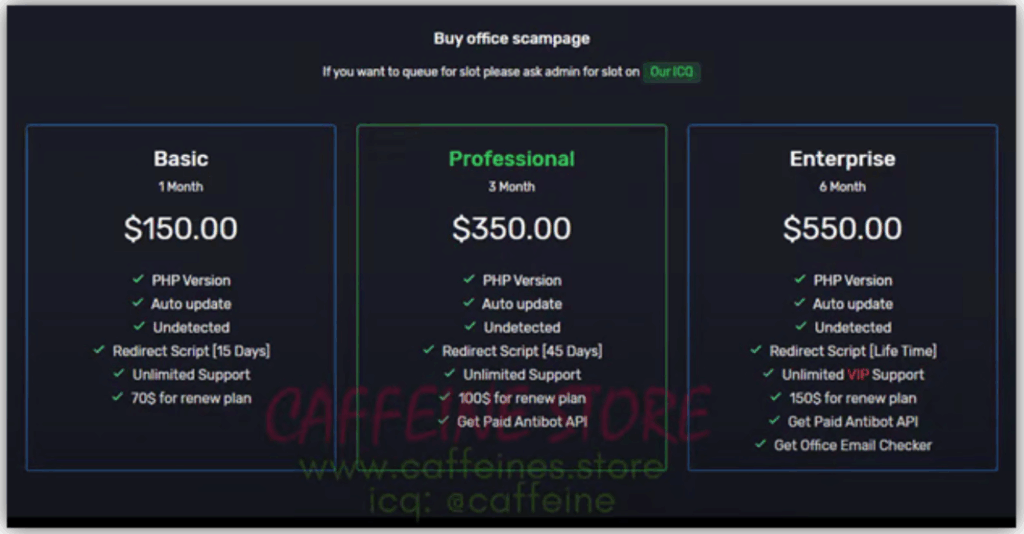
A single phishing kit can give even an amateur scammer the tools to impersonate your brand in minutes. These kits are cheap, easy to buy on the dark web, and increasingly sophisticated.
Today’s kits don’t just mimic your email domain or clone a login page. Many come packaged with:
- Pre-written phishing emails designed to dodge email security filters.
- Automated domain spoofing and subdomain setup to launch multiple fake sites at once.
- Built-in support for QR code phishing, social media lures, and SMS scams.
- Back-end dashboards for cybercriminals to track stolen login credentials and export data in real-time.
This “plug-and-play” model means the same kit can impersonate a bank one week and a credit union the next, changing only the logo and display name. Some advanced kits even update themselves to bypass new security measures automatically.
For SOC teams and brand managers, this industrial approach means you’re up against a supply chain of impersonation attempts, not just a lone hacker.
How cybercriminals scale their impersonation attacks
Modern phishing gangs run like businesses. They don’t handcraft every scam. They automate, outsource, and sell access to ready-made kits and bulletproof hosting.
This is called phishing-as-a-service. Operators sell subscriptions to other scammers, who pay for fresh fake domains, phishing templates, and backend dashboards. Some services even bundle in malware payloads, or fake support chatbots to make the spoofed sites look legitimate.
Big brands (especially financial services and Microsoft logins) are constant targets. Attackers register hundreds of lookalike domains, blast out spoofed emails, and share victim lists. One group can hit thousands of customers in a day, redirecting them to a fake website that harvests sensitive data and bank credentials.
These large-scale hijacking campaigns don’t stay up for months. Many fake sites can vanish within hours or days, only to pop up again under new top-level domains. This rapid churn keeps brand owners and SOC teams under constant pressure to detect and takedown fast.
Takedowns and brand defense: What works
Every impersonation attack has a weak spot—the fake domain. Finding it fast and shutting it down is one of the most effective ways to protect your brand and your customers.
Domain monitoring tools watch for suspicious registrations, like lookalike domains using your bank’s name with slight typos or unusual top-level domains. When a match appears, your security team can issue a takedown request through the hosting provider or domain registrar.
Speed also matters. Many phishing sites stay live just long enough to steal login credentials and disappear before law enforcement or your SOC can react. A fast, automated takedown service cuts the window of damage and reduces customer complaints and fraud losses.
But takedowns alone aren’t enough. Phishers switch domains, shift to new registrars, or hide behind privacy services. That’s why real-time monitoring, threat intelligence, and continuous hunting for fresh impersonated domains are critical.
Securing your legitimate domain
Protecting your brand means locking down your real domain name as tightly as possible. Many spoofing attacks work because basic email safeguards are missing or misconfigured.
Start with the big three email authentication protocols:
- SPF (Sender Policy Framework): Defines which servers can send emails for your domain.
- DKIM (DomainKeys Identified Mail): Adds a digital signature to prove the email is genuine.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Tells recipient servers how to handle suspicious emails that fail SPF or DKIM checks.
Together, these block many spoofed emails before they reach your customers. Yet, many financial institutions still leave gaps, or never monitor DMARC reports to catch misuse.
Check your DNS records regularly. Review SSL certificates to ensure no rogue subdomains exist. Watch for unusual changes in email headers that hint at email spoofing or impersonation attempts.
Finally, remember that technical controls stop a lot, but not everything. Combine them with vigilant domain monitoring, fast takedowns, and user training to keep ahead of evolving scams.
How to spot and block impersonation attempts
Even with strong security measures, some phishing slips through. That’s why spotting the signs early is critical for SOC teams and brand managers.
Common red flags:
- Phishing emails with slight domain variations or suspicious display names.
- Unexpected attachments or links asking for login credentials.
- Generic greetings instead of personalised info, which is a trick scammers use to hit large lists fast.
- Urgent requests for sensitive information, or scare tactics that push quick clicks.
- Links that hide malicious links behind QR codes or shortened URLs.

On the tech side, monitor your email security gateway for spikes in spoofed emails, unusual senders, or odd email header patterns. Cross-check suspicious messages with threat intelligence feeds to catch known phishing kit fingerprints.
For employees and customers, training still works. A quick gut check before clicking can stop even advanced social engineering.
Free resources like Banks Never Ask That make scam awareness easy for staff and customers alike, with free resources, games, and videos. Pair that human filter with strong email protection, and your risk of serious impersonation attacks drops sharply.
Real-world wins: Takedown success stories
Industrial-scale phishing campaigns don’t stop on their own. They’re dismantled by swift, coordinated takedowns. And recent headlines prove it works when security teams and law enforcement move fast.
1. ONNX
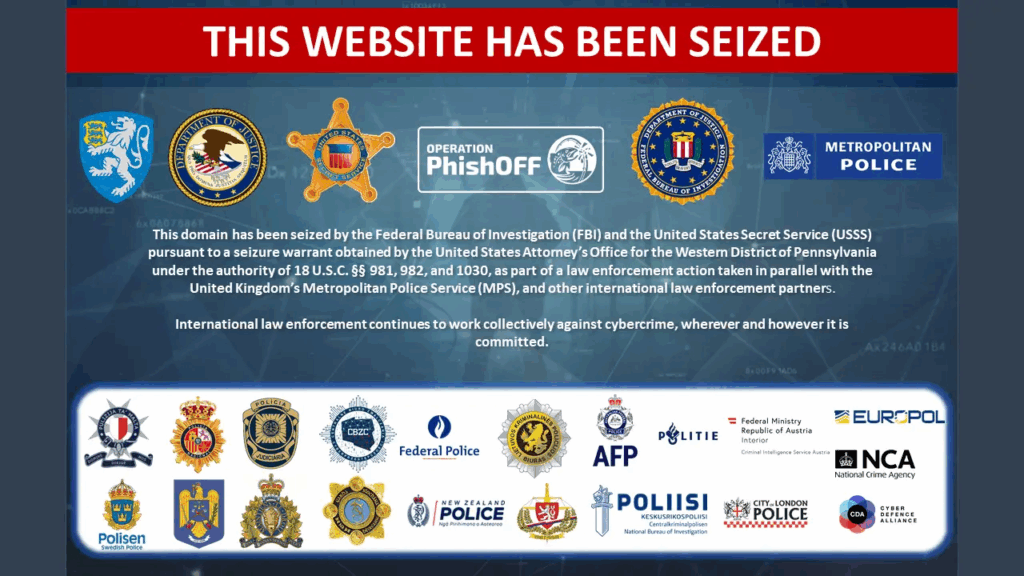
In November 2024, Microsoft’s Digital Crimes Unit (DCU) and international partners seized control of around 240 malicious domains linked to “ONNX,” a phishing-as-a-service network run by an Egypt-based cybercriminal known as MRxC0DER. These fake sites helped scammers bypass multi-factor authentication and targeted major brands, especially banks and Microsoft logins.
2. LabHost
Just a few months earlier, in April 2024, global law enforcement shut down LabHost, one of the world’s largest phishing kit operations. The FBI released a list of over 42,000 fake domains impersonating more than 200 well-known banks, government portals, and streaming brands. This takedown disrupted credential theft schemes that had hit tens of thousands of victims worldwide.
3. Lumma Stealer
In May 2025, Microsoft and the US Department of Justice dismantled Lumma Stealer’s infrastructure, which had about 2,300 domains that delivered info-stealing malware via phishing campaigns. This malware harvested banking credentials, cryptocurrency wallets, and sensitive data from nearly 400,000 infected devices.
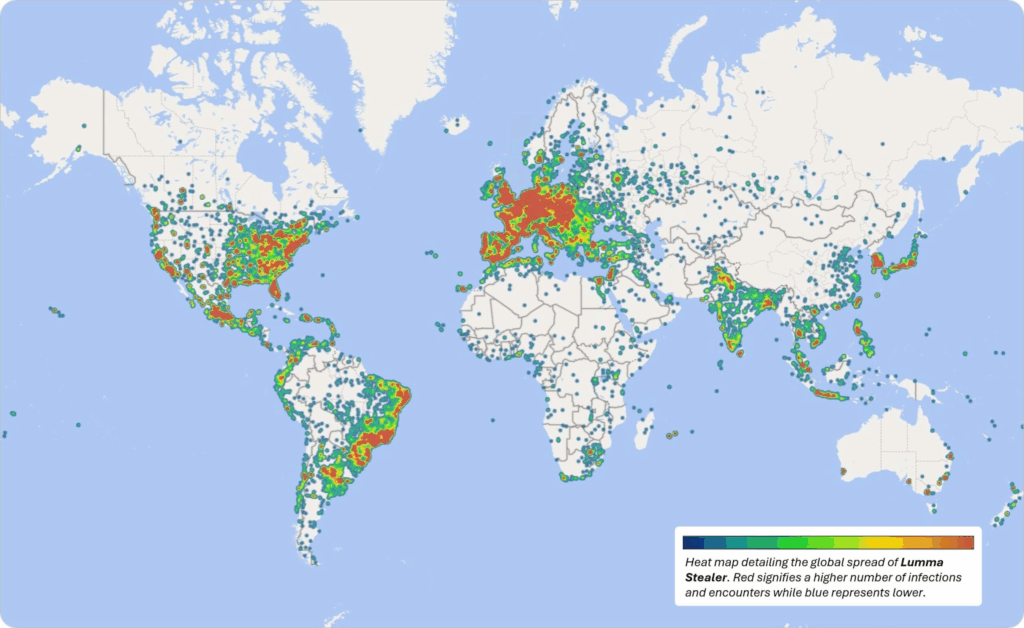
These victories show that while criminals will keep registering fake domains and deploying phishing kits, real-time domain monitoring, fast takedown service, and strong partnerships can choke their revenue and protect your customers before they click.
FAQs
Still wondering about domain impersonation? Here are some quick bonus insights to boost your impersonation protection efforts.
How common is domain impersonation in phishing attacks?
Extremely common. Reports show domain spoofing and typosquatting are among the top tactics used to trick customers and bypass basic email security.
Do SPF, DKIM, and DMARC stop all spoofing attacks?
They block a lot but not everything. Attackers often register lookalike domains outside your control. That’s why continuous domain monitoring and fast takedowns are critical too.
Why do phishing kits use QR codes now?
It’s a sneaky trick. QR code phishing hides malicious links from scanners and security filters, luring mobile users into entering login credentials on fake sites.
Can domain impersonation lead to business email compromise (BEC)?
Yes. Stolen credentials from phishing often fuel BEC scams, wire fraud, or ransomware. One well-crafted phishing email can trigger big financial losses.
What can we do to protect our brand today?
Use layered cybersecurity defense measures. Set up SPF, DKIM, and DMARC; train staff and customers; monitor new domains in real time; and take down fake sites quickly. CybelAngel’s brand protection service makes this easy.
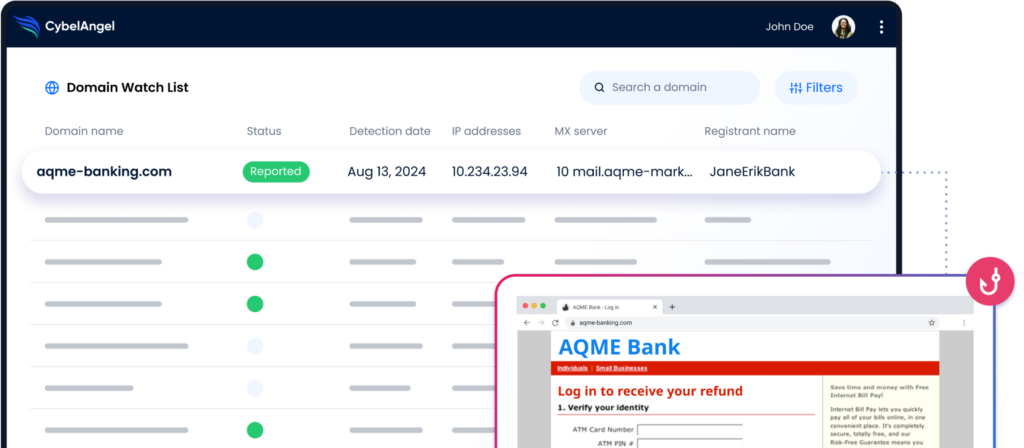
Figure 7: Brand protection security solutions in action. (Source: CybelAngel).
Final thoughts
Domain impersonation is an industrial cyber threat now. Scammers deploy automated kits, spin up thousands of fake domains, and drain trust from financial brands every day.
But you don’t have to stay reactive. With financial services cybersecurity, you can prioritize real-time domain monitoring, swift takedowns, and smart email authentication. This will cut cyberattacks off before your customers ever see a fake link.
You can protect your brand and your customers with CybelAngel’s domain monitoring and takedown service. Book a demo today.

