Understanding Cyber Threats Targeting Healthcare [2025 Guide]

Table of contents
The healthcare industry is facing a rapid fire of security threats as ransomware attacks become more common, crippling the industry‘s ability to remain resilient and provide care to patients.
On average, healthcare organizations lose $900,000 a day due to operational outages caused by ransomware attacks, without taking into account the billions paid in ransoms. As healthcare operations become digitized, the attack surface of medical clinics and their vendors grows.
Let‘s dive into why the healthcare industry is becoming a target for cybercriminals, the effect on society, and how healthcare providers can protect themselves against an evolving threat landscape.
The rising threat of cyberattacks in healthcare
The rush to adopt technology advancements in healthcare, such as AI, poses great security risks, warns Reuters. While innovative technology can help healthcare providers address bottlenecks and make processes more efficient, using new technology also creates potential threats.
In 2022, there were 1,463 cyber attacks per week in the healthcare industry. By 2024, healthcare providers reported they had experienced medical data breaches of 500+ patient records. As AI cybercrime becomes more prominent and accessible, these attacks will continue to grow.
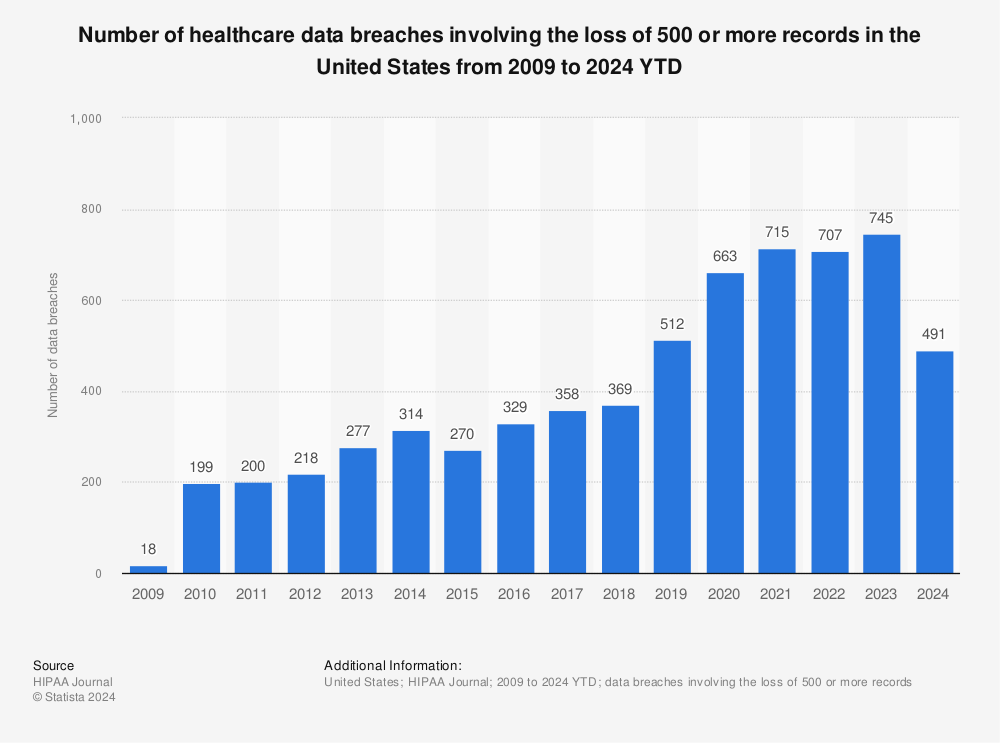
In 2023, the Office for Civil Rights (OCR) reported a 239% increase in security breaches in healthcare between 2018 and 2023. Over the same period, they documented a 278% increase in ransomware attacks.
In 2024, 67% of surveyed healthcare organizations said they had encountered a ransomware attack in the past year.
The numbers highlight a disturbing trend. Cybercriminals are now targeting healthcare providers due to the lack of preparedness in the industry.
Experts have warned that 37% of healthcare organizations do not have a cyberattack incident response plan in place, putting the industry in a precarious situation.
Healthcare organizations are vulnerable to cyberattacks because they possess high-value patient information to cybercriminals and nation-state actors. Electronic health records (EHR) with limited cybersecurity measures, vulnerabilities in legacy systems, and human error in high-stress environments, create the perfect storm for criminals looking to harvest data.
What kinds of cyberattacks are most common in the healthcare industry?
According to reports, in 2024 the most common cyberattacks in the healthcare sector were:
- Cloud compromise: hackers gain entry into an organization‘s IT cloud infrastructure.
- Ransomware: when a threat actor spreads malicious software to extort data and funds.
- Supply chain attacks: cybercriminals infiltrate an organization by exploiting vulnerabilities in third-party vendors or service providers.
- Business email compromise (BEC): scammers use a spoofed email address or compromised account to trick employees into initiating a fraudulent money transfer.
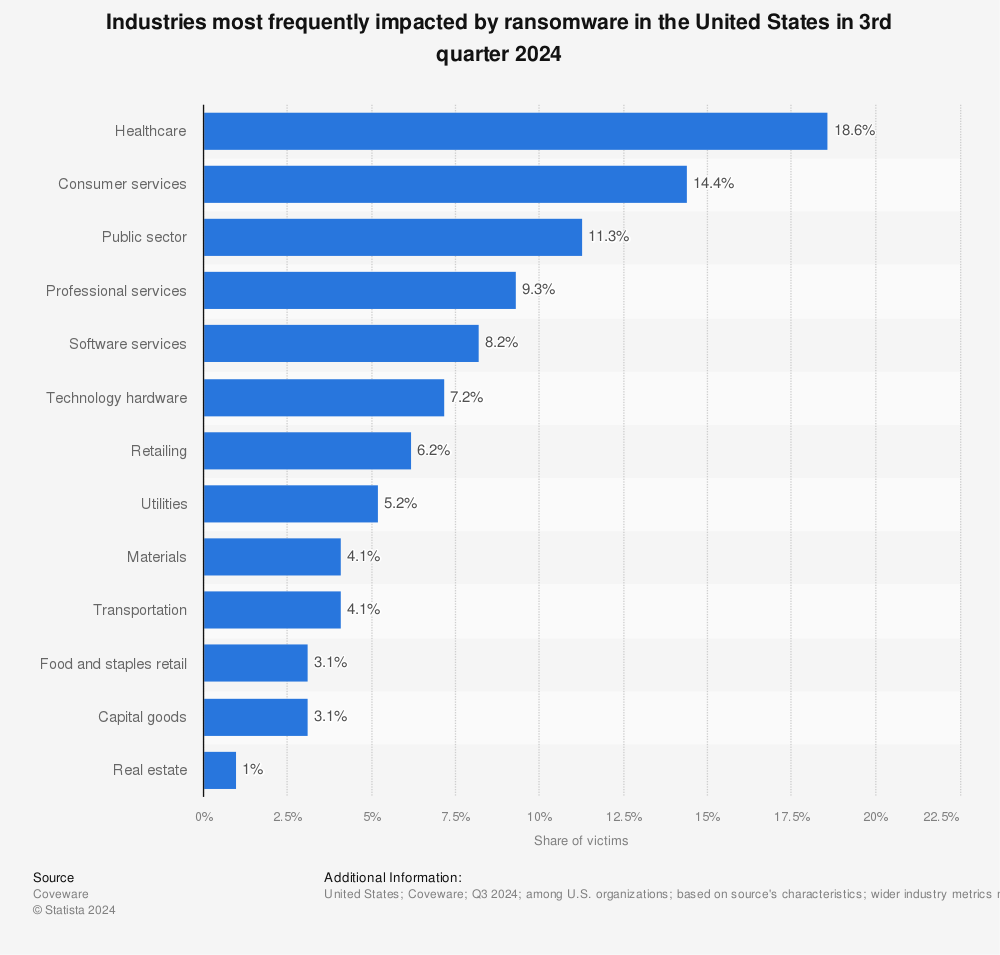
Ransomware makes it easy for threat actors to attack
Ransomware as a Service (RaaS) has become more commonly used by threat actors due to the low cost and little technical expertise needed.
Threat actors use malicious software to encrypt files, causing disruptions for healthcare providers. When sensitive data is lost to hackers, healthcare professionals cannot access the necessary information needed for treatment.
According to Microsoft, between 2015 and 2024 ransomware attacks have surged by 300%, causing delays to procedures and tests for patients.
Business email compromises are a “billion-dollar scam”
According to the FBI, business email compromises (BEC) are a billion-dollar scam costing the industry financially and in their ability to provide care to patients. BEC scams have increased by 1,300% since 2015, becoming the preferred attack method by most cybercriminals.
BEC attacks are a type of spear-phishing attack that aims to extort funds from the organization. Once a scammer infiltrates a legitimate email, they can trick employees into handing over thousands by pretending to be a CEO or CFO. Threat actors usually conduct detailed research about their targets beforehand, making it difficult to filter out cybersecurity threats.
In one study, 62% of participants ranked BEC incidents as their top cybersecurity concern yet only 45% of respondents had implemented response strategies to these kinds of attacks.
Supply chain attacks in the healthcare sector threaten lives
Healthcare organizations rely on an interconnected web of third parties to provide service and care to patients. This can span anywhere from cloud service providers to orchestrate internal procedures to electronic health record vendors and third-party labs.
Once threat actors gain entry and begin disrupting the supply chain, providers are unable to provide care in the usual ways, posing a grave threat to life.
When healthcare organizations were surveyed about supply chain attacks, 50% stated that the attack escalated the severity of an illness, while 48% confirmed that the attack resulted in prolonged hospital stays.
How do security breaches occur in the healthcare industry?
The spike in cybercrime led the Attorney General in 2023 to enforce consequences for HIPAA violations. After an investigation, it was discovered that most healthcare institutions did not adequately protect sensitive data, violating the HIPAA Security Rule that requires physicians to protect electronically stored patient data.
The majority of cases showed a lack of reasonable and appropriate security measures such as multifactor authentication (MFA), access controls, encryption, security testing, data logging and monitoring, data retention, and up-to-date asset inventories.
- Healthplex in New York was fined $400,000 for failing to implement MFA, security measures for data logging, and failing to perform data security assessments.
- Telehealth company Cerebral Inc. was fined $3.1 million for using a Pixel to track customers on its website, sending the transferred HIPAA-protected data of its customers to third parties such as Meta (Facebook), Google, TikTok, and others.
- Broomfield Skilled Nursing and Rehabilitation Center in Colorado was fined $60,000 for using email forwarding to send sensitive emails to an external email address.
The recent healthcare data breaches above illustrate how healthcare providers are failing to adequately protect patients from threat actors. Basic cybersecurity practices are simply unknown or ignored, threatening patient safety.
When ransomware limited blood supply to hospitals
OneBlood, a blood center that services hundreds of hospitals in the southeastern U.S., was hit by a ransomware attack in July 2024. The attack temporarily shut down internal systems, causing staff to quickly move to manual methods of distributing blood, affecting the supply to hospitals.
Hospitals responded by implementing a blood conservation process after the attack, but it took days for hospitals to begin receiving their usual quantity of blood for patients.
A ransomware attack shut down pharmacies
Ascension Healthcare, one of the largest health systems in the US, was hit by a ransomware attack in May 2024. They operate 140 hospitals across 19 states, affecting every part of the healthcare system.
The attack forced pharmacies connected to Ascension in multiple states offline, with some resorting to accepting cash payments for prescriptions. In other areas, clinicians turned to regional pharmacies by fax or telephone to fill orders.
In June 2024, it was revealed that the threat actors had also stolen the data of 5.6 million patients from electronic health records and Ascension‘s patient portal.
A HealthEquity data breach exposed the social security numbers of 4.3 million people
HealthEquity, a US company that manages healthcare benefits such as health savings accounts, flexible spending accounts, and health reimbursement arrangements, had patient data stolen from their systems in July, 2024.
The data stolen included patient names, addresses, telephone numbers, employee IDs, employer names, Social Security numbers, dependent information, and payment card information.
The threat actor entered the system through unauthorized third-party access to a data repository outside its core systems. It was confirmed by the Office for Civil Rights that the attack affected over 4.3 million people in the US.
Change Healthcare lost the data of 190 million patients to ransomware
In February 2024, [Change Healthcare suffered a ransomware attack on an estimated 190 million individuals.) that encrypted files and stole the protected health information of 190 million patients. To date, this is the largest healthcare data breach ever recorded.
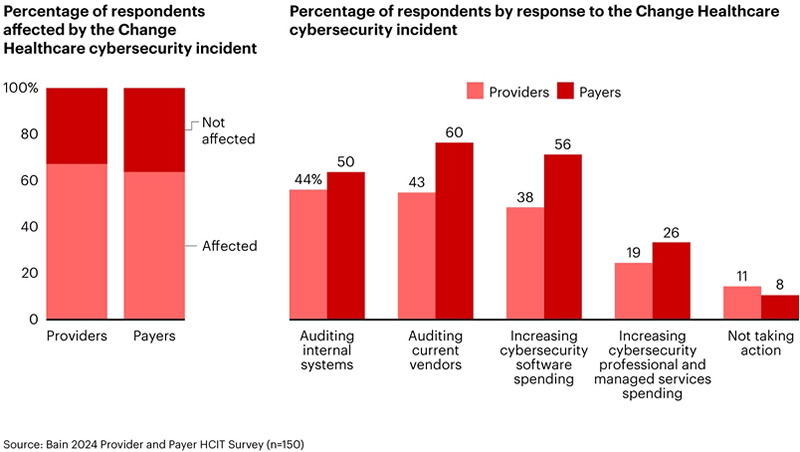
The scammers stole names, contact information, dates of birth, Social Security numbers, and medical information from across the US. To avoid public backlash, Change Healthcare paid the $22 million ransom to release the stolen data, however, the ransomware group BlackCat pocketed the ransom and did not return the data.
After the ransomware took hold of the internal systems, there was an outage that prevented healthcare providers and health insurers from operating normally. The outage lasted several weeks, prompting an investigation from the Office of Civil Rights to see if the company was compliant with HIPAA‘s Security Rule.
In the aftermath, victims of the data breach issued a class action lawsuit against Change Healthcare, which is still ongoing.
As Microsoft reports, “Email remains one of the largest vectors for delivering malware and phishing attacks for ransomware attacks,” especially within the Healthcare industry. Threat actors are counting on the lack of regulatory compliance and minimal threat detection to perform their attacks.
What are the effects of cyberattacks on healthcare?
Rising cyber threats in healthcare is worrying for both patients, the industry, and the governments of affected countries. In the worst case, breaches can cause death or delays in treatment, reducing patient care as a whole.
Here are some of the effects of cyber threats on healthcare:
- Cyberattacks threaten patients’ lives. Cyber threats pose great risk to the lives of patients. Delays in treatment and testing, increase in waiting times, and diverting patients when attacks cause medical facilities to shut down, all increase the risk of premature patient death.
- Medical supply chains and third-party vendors are affected. Supply chain attacks make it more difficult for medical facilities to operate normally. If a hospital isn‘t able to contact a third-party provider for medication or other services, patient care will be compromised.
- Attacks cost the healthcare industry billions in ransomware payments. When medical providers fold to the pressure of threat actors, it not only results in a financial loss but also increases the likelihood of the attack occurring in the future. In 2024, $133.5 million of confirmed payments were sent to ransomware groups.
Trends for cybersecurity in healthcare 2025
In 2025, healthcare organizations find themselves at a critical junction regarding safety and compliance.
Strengthening cyber resilience and exploring new security solutions will be imperative to curbing cyberattacks and improving healthcare cybersecurity.
Here are some top trends to look out for in 2025:
- Zero-trust architecture is reaching popularity In our digital world, users are primed to trust that IT systems are safe and secure. With the advent of AI and systems being more interconnected than ever, scams and attacks are becoming more prevalent, causing users to be more cautious. Healthcare institutions can bring back trust by implementing zero-trust policies to create frameworks for data protection and mitigate risk.
- Securing data and devices will be a challenge One challenge healthcare providers will face is securing all medical IoT devices. Medical devices are usually not created with security in mind, making thwarting cyberattacks more difficult. Institutions will have to work backwards and implement more security to ensure that systems are not as vulnerable to attacks.
- AI safety strategies will need to be considered Integration of AI into everyday work has exploded in the last 2 years. However, AI also introduces new risks into the threat landscape. AI contingency plans will be essential for healthcare providers to mitigate cybersecurity risks and reduce security threats.
- Tech sprawl is becoming a major obstacle Across all industries, the IT landscape is becoming a patchwork of cloud solutions, with organizations reporting 76 security tools to manage on average. While this may help increase efficiency, it has also created security silos. Managing a sprawling tech ecosystem can be made easier by carefully selecting security tools and ensuring they are active across all systems. Managing security in one place allows for better risk management and reduction of cyber threats.
What are the best practices for preventing medical cyber attacks in 2025?
To keep sensitive patient data safe, healthcare providers will need to adopt new security policies and tools to improve functionality and security posture.
Focus on the whole system to mitigate risk
With many intersecting tools across the IT ecosystem, it can be difficult to keep track of safety at each point. Having a tool like CybelAngel that can monitor an entire ecosystem ensures not only compliance with regulatory bodies, but also transparency for security teams.
Implement cybersecurity basics
The healthcare industry falls behind the industry standard for cybersecurity. Implementing security features such as multi-factor authentication (MFA), firewalls, and saving secure backups of patient data means ransomware or phishing attacks won‘t be as effective for scammers.
Meet compliance for GDPR and HIPAA
Risk assessments and audits are becoming more important. Updating policies and procedures to remain compliant with HIPAA (US) and GDPR (Europe) will foster patient trust and ensure healthcare personnel are on the same page.
Strengthen third-party risk management
Disruption of medical supply chains has devastated the industry in recent years. Security teams must evaluate and manage third-party vendor risks to prevent vulnerabilities from being exploited.
Adopt AI threat protection
Leveraging AI models to detect and respond to cybersecurity threats in real-time can help healthcare providers stay ahead of evolving attack methods. CybelAngel‘s innovative AI model can process billions of data points daily to help teams stay ahead of healthcare data breaches.
Build zero-trust architecture to reduce the attack surface
Zero-trust architecture can help healthcare providers regain patient and user trust, ensuring security into the future. Continuous monitoring of devices, validation of devices and user identities, and implementing controls across IT systems are essential components. Assuming a system can be breached rather than assuming safety will ensure data protection and reduce healthcare breaches.
Implement network segmentation
Dividing networks into sub-regions provides a simple way to close off sensitive patient data, preventing potential healthcare data breaches from occurring. Ransomware attacks, for example, won‘t spread as quickly through an ecosystem, reducing potential losses.
Introduce endpoint detection and response (EDR)
Endpoint detection refers to the continuous monitoring of end-user devices to detect and respond quickly to threats like ransomware. Keeping a log of all endpoint users allows teams to detect anomalies or suspicious behaviour before an attacker can disable systems.
Get in touch with our experts to overcome any healthcare security challenges
Preventing healthcare breaches in 2025 can feel like an impossible mountain to climb—but by implementing cybersecurity best practices and using the right tools, healthcare providers can pivot to protect patients and systems.
CybelAngel‘s platform gives teams a holistic overview of anomalies and potential threats across all tools.
Protect patients and ensure no care is lost.

