Supply Chain Vulnerabilities: How to Combat Hidden Threats

Table of contents
Supply chains are the driving force of modern businesses. They connect manufacturers, suppliers, and customers. But when it comes to cyber threats, this interconnectedness can also be their downfall.
With the rise of technology, supply chain vulnerabilities have increased in equal measure. Supply chain attacks can spiral through an entire network, causing widespread harm—from disrupted operations, to damaged company reputations.
Let’s explore the reasons behind supply chain risks and how to mitigate them.
1. What are the drivers of supply chain vulnerability?
Supply chain vulnerability refers to the weaknesses within a supply chain that can be exploited by cyber threats, leading to data breaches, operational disruptions, or unauthorized access to systems.
There are two main drivers behind supply chain threats…
High dependence on technology
Most (if not all) businesses are heavily dependent on interconnected systems, IoT devices, and cloud-based platforms—all of which increase their attack surfaces.
Case in point: According to Security Magazine, 91% of organizations have suffered a software supply chain attack in the past year. Top incidents included…
- Exploiting vulnerabilities in third-party code
- Taking advantage of misconfigured cloud servers
- Attacking open-source software and container images
- Creating API data breaches
The world is undergoing rapid digital transformation, but often, new technologies and third-party software are introduced without proper vetting.
For instance, more suppliers are making artificial intelligence (AI) a crucial aspect of their processes. However, we’re still learning the extent to which cybercriminals can exploit this new technology.
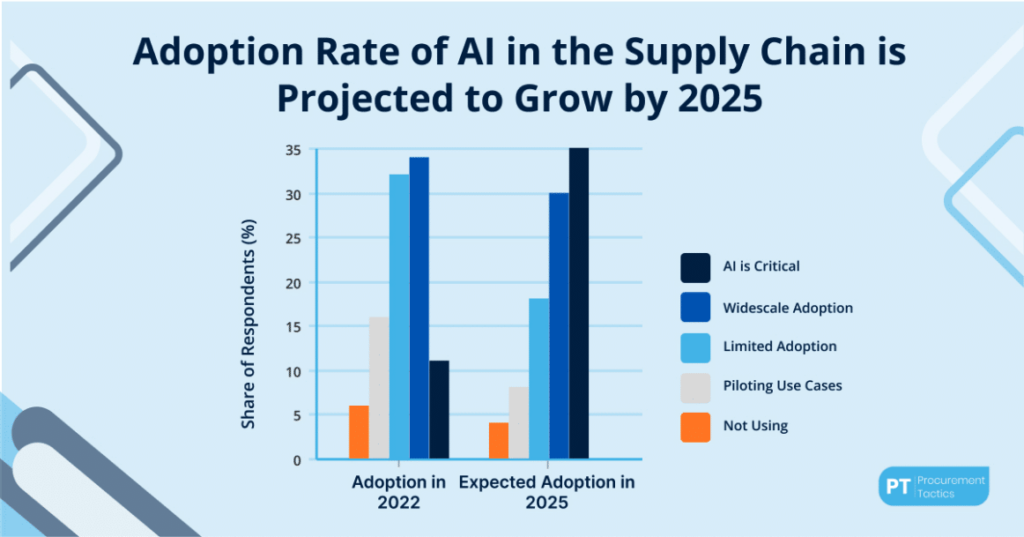
Globalization, economic instability and political tension
Global supply chains have become the norm, with international sourcing and complex networks. National security regulations aren’t always the same across the world, meaning that different service providers will have different cybersecurity standards.
Similarly, economic and political instability—as well as geopolitical tensions—can expose vulnerabilities in any international supply chain network.
A recent study found that, since 2017, the entities affected by supply chain cyber attacks has increased by 2227% in the US alone. And ultimately, software supply chain attacks will cost the world $60 billion in 2025, and $138 billion by 2031.

2. What is the biggest threat to supply chain security?
When it comes to supply chain risk management, cybersecurity is the biggest threat.
We can think of supply chain cybersecurity like a house of cards. Rather than attacking a large organization directly, hackers often target smaller, less well-equipped suppliers. And just by compromising one system, the entire supply chain can come crashing down.
There are lots of types of supply chain risks. In particular, cybercriminals will:
- Implement ransomware and data breaches: By injecting malicious code into supply chain operations, they can encrypt sensitive information until a “ransom” is paid—or use the data for identity theft, scams, or dark web sales.
- Exploit insider threats: Cybercriminals can take advantage of employees or contractors with malicious intent or unintentional negligence. For example, they might send a phishing email to trick a vendor into sharing personally identifiable (PII) data.
- Push counterfeit and fraudulent services: By tampering with a third party’s software development, cybercrime gangs can introduce compromised components into the supply chain. They can also disrupt physical shipping supply chains (as we’ll see in Maersk’s case, later on).
3. What are the main risks facing a supply chain?
Before we discuss third-party risk management in a moment, it’s important to understand the consequences of supply chain attacks, which include:
- Data theft: Hackers can expose sensitive data such as trade secrets or customer information. The average cost of a data breach is thought to be $4.45 million.
- Operational disruption: Just like natural disasters, cyberattacks can cause severe downtime and supply shortages. For instance, a global cyber outage in July 2024 led to $1 billion in losses across the world.
- Reputational damage: Supply chain disruptions can lead to loss of customer trust due to compromised products or service delays. A Canadian survey discovered that 28% of businesses found that a cyber attack damaged their reputation.
- Financial loss: Software supply chain attacks can lead to direct costs from ransom payments, legal expenses, and indirect costs from lost business opportunities.
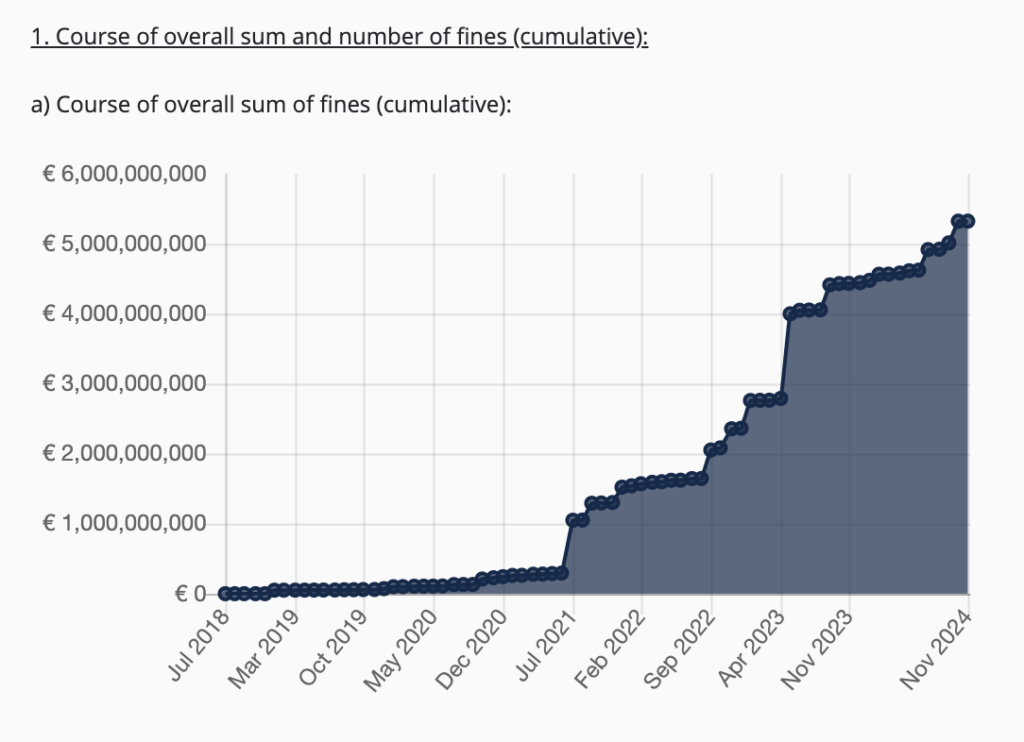
- Regulatory non-compliance: Failing to meet cybersecurity standards could result in fines or penalties. For example, we can see the cumulative increase in GDPR fines in recent years for poor data processing standards.
4. Supply chain risks examples: 5 case studies
Let’s look at 5 real-life examples of what happens when implementing supply chain vulnerability protection fails.
- The SolarWinds hack (2020): In one of the ‘biggest cybersecurity breaches of the 21st century’, hackers infiltrated the SolarWinds Orion system, an IT monitoring platform. Backdoor malware was delivered to more than 30,000 companies and government agencies. More than 18,000 customers installed it. Worst of all, the attack wasn’t publicly announced until over a year later.
- The Target data breach (2013): After a phishing email was sent to a Target employee who worked with a third-party vendor, Fazio Mechanical, 11 gigabytes of data was leaked, including up to 70 million people’s names, addresses, numbers, emails, and credit card details.
- The Maersk shipping disruption (2017): A ransomware attack encrypted thousands of devices across the Maersk shipping network, and their operations ground to a halt, affecting the supply chains of thousands of businesses worldwide. Maersk was responsible for about a fifth of all global trade, so this attack was hugely damaging.
- The Toyota supply chain cyberattack (2022): After one of Toyota’s suppliers, Kojima Industries, was hit by a malware infection, it had to suspend operations in 28 production lines across 14 plants for a day, cutting down global production by a third.
- The Uber data breach (2022): Uber employee data, including internal documents and email addresses, was believed to be exposed after a third-party incident at its mobile device management (MDM) platform, Teqtivity. It is thought that almost 80,000 employees were affected by the data breach.
6. How businesses can mitigate supply chain risks
There are lots of mitigation strategies that businesses can adopt to protect their supply chain sustainability in the long run. For example, the UK’s National Cyber Security Centre offers 12 principles to secure supply chains and partnerships.
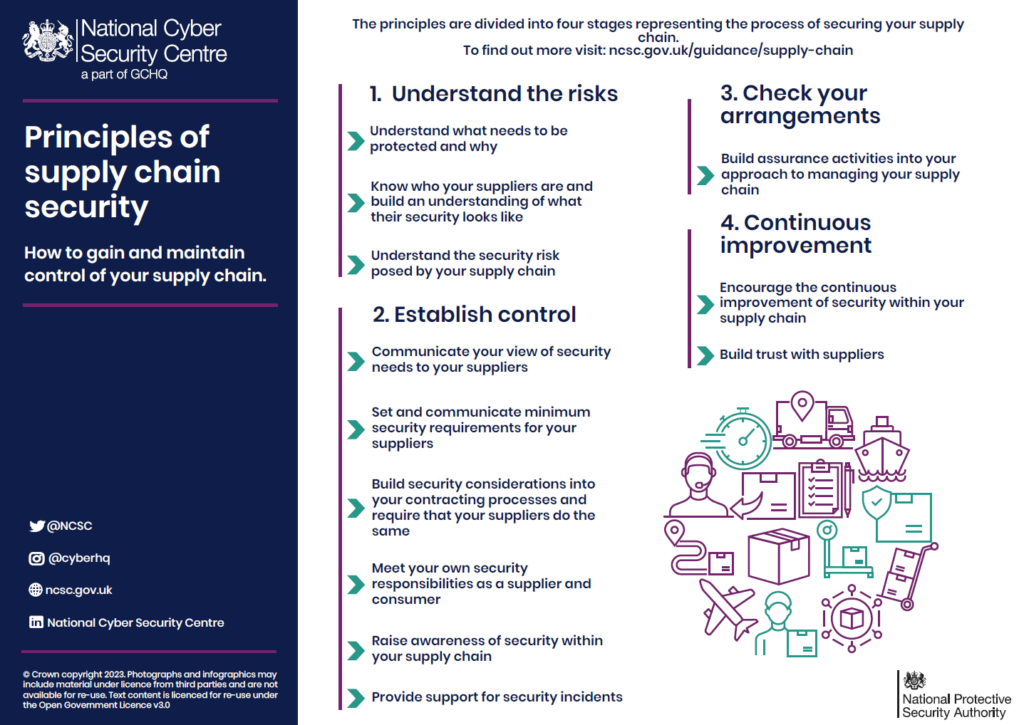
Here are some general guidelines for CISOs and IT departments to support supply chain security advancements.
- Strengthen your vendor management protocols: Make sure you vet your suppliers thoroughly, ask them to fulfil specific cybersecurity protocols, and include them in your contract.
- Conduct risk assessments: Less than half of businesses have conducted third-party risk assessments. As a starting point, you could use CybelAngel’s special threat investigation service, helping you to map vulnerabilities across your supply ecosystem—and resolve them before they become a problem.
- Invest in cybersecurity technology solutions: Use supply chain vulnerability detection software to safeguard your systems in real-time. For example, CybelAngel can protect your company from the outside, protecting public-facing digital assets from cybercrime.
- Prioritize employee training and awareness: Once your staff and suppliers understand the importance of cybersecurity, you can take a united approach against hackers, making the ecosystem harder to exploit.
- Have an incident response plan: For instance, businesses can protect themselves from the risk associated with lost shipments by regularly testing their business continuity and disaster recovery plans.
- Stick to relevant laws and frameworks: Follow NIST’s cybersecurity framework, and adhere to other national security laws, such as the EU’s GDPR, or international frameworks ISO/IEC 27001 guidelines for securing information systems.
Wrapping up
By combining proactive measures, strong partnerships, and smart investments in EASM technology such as CybelAngel, businesses can significantly improve their supply chain resilience.
