How the Internet is Getting Safer Thanks to Cloud-based Services
No reader will be surprised to learn that cloud service adoption has been skyrocketing in the last few years. According to the Cisco Global Cloud Index: Forecast and Methodology, 2016-2021 whitepaper, “by 2021, 94 percent of workloads and compute instances will be processed by cloud data centers; 6 percent will be processed by traditional data centers.” From the same report, one can spot another interesting statistic: “(…) traffic within the data center and traffic between data centers will represent 85 percent of total data center traffic by 2021, and traffic exiting the data center to the Internet or WAN will be only 15 percent of traffic associated with data centers.” As cloud companies provide more and more services to businesses, just like network traffic, end users will interact more and more with workloads and content hosted by cloud providers and less and less with on-premise resources.
Cloud Services Making the Internet Safer?
And, despite the handful of cloud-related data leaks and breaches that sometimes dominate the news cycle, the adoption of cloud services should actually make the Internet safer, in part by reducing the attack surface of enterprises. How? Let’s take a simple, real-life example: a bank looking for a way to back up user data from its website. The standard process would be to rent a server on-premise, configure it, run a database program on it – for example, PostgreSQL – and make the bank’s website communicate with it. Now, this kind of configuration comes with some immediate security considerations:
- Is the firewall correctly configured?
- Is PostgreSQL up-to-date security-wise?
- What about authentication?
Such security considerations are too often overlooked. As evidence, CybelAngel detects over 2 billion documents on wide-open, unsecured Rsync servers per week. We know that servers with manual configurations often turn human negligence into data leaks. While enterprises often cite better scalability and improved cost management as the reasons for embracing cloud-based services and Infrastructure as a Service (IaaS), these solutions in themselves also provide extra security. Using a cloud provider’s packaged service often suppresses some of the risks of data exposure. For example, with Google Cloud SQL, PostgreSQL is automatically kept up-to-date, and most of the network security considerations are delegated to Google.
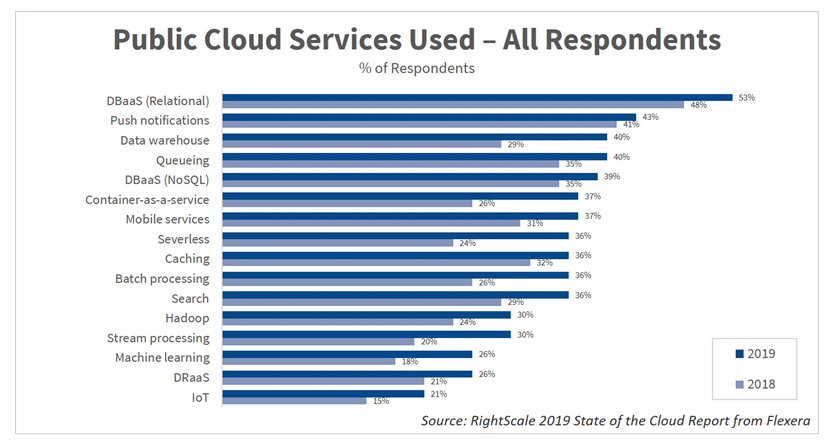
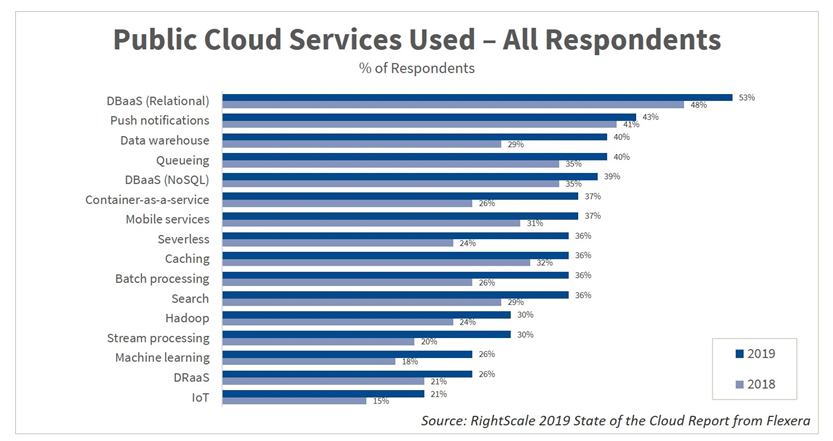
Cloud-based services adoption is rising over the years
Consider a company choosing a cloud-based, software as a service (SaaS) office productivity suite like Office 365 or Google Suite for document storage and sharing. Given the complexity of managing an Active Directory, delegating most of the responsibility of Identity Access Management (IAM) to the service provider reduces the attack surface on the company’s assets.
Cloudflare Argo Tunnel
Cloud service providers will be integral in the development of new paradigms in safer computing. The rapid adoption of serverless services permits the cloud service providers’ global takeover of modern infrastructure systems, leaving to enterprises only application responsibility. Consider the recent release of Cloudflare’s Argo Tunnel. Argo Tunnel “lets you expose a server to the Internet without opening any ports.” In fact, one can use it to deploy an application and “instead of managing DNS, network, and firewall complexity,” it is going to “serve traffic from their origin through Cloudflare.” The idea is to allow users to host an application on their own server, but delegate the network work to Cloudflare’s infrastructure, via a simple program. Thus, this product, on top of simplifying application hosting, ensures that “Cloudflare’s security features always stand between your server and the rest of the Internet.” These security features include Distributed Denial of Service (DDoS) protection, no IP exposure, and simplified firewall rules. Here, a cloud service provider’s protection effectively reduces the attack surface of a company’s software environment. But while cloud-based services are clearly improving enterprises’ cybersecurity posture, nobody should be led to believe that the proliferation of these services is not without any risk at all. Facts prove that not every single cloud-based service will come preconfigured for increased security. Consider the 40+ million documents CybelAngel finds daily on unprotected AWS S3 buckets, and McAfee’s reporting that 5.5% of all AWS S3 storage buckets have world read permissions. And, while packaged cloud services may offer always up-to-date programs, application security (e.g., injections) remains a major stake. A hardened infrastructure cannot cover vulnerabilities directly linked to the program running on the cloud. Furthermore, 92% of companies still have cloud credentials for sale on the Dark web, though McAfee reports that the risk of such credential leaks will be reduced by the multifactor authentication that many business critical cloud services support. The key point to understand is that when data was primarily held on-premise by enterprises, the probability of any given enterprise’s IT department misconfiguring a server was quite high compared to the probability that a sophisticated cloud service provider might neglect the security of their infrastructure. But while the probability that a lapse in security configuration is reduced in an ecosystem with greater cloud adoption, the severity of the impact of the lapses that do occur is increased. Cloud storage and services consumption is being concentrated in just a handful of providers, who consequently manage incredibly large networks that maintain the data of tens of thousands of enterprises. Accordingly, one security incident at a major cloud provider, however improbable it may be, can lead to the compromising of a mass of enterprises’ data. The recent Cloudflare outage illustrates this concept, as although we might anticipate that such outages will be rare, in this instance, a portion of the Internet was essentially taken down. CybelAngel is a proud supporter of the embrace of cloud computing, and we aim to help enterprises adopt cloud storage and services in the safest manner possible. We believe that the enterprises that do not rely unduly on all cloud vendors, that heed the severity of potential cloud service incidents, and that maintain responsibility for their application-level security, will be the enterprises that avoid the data leaks and breaches that would garner them much unwanted press.