How to Prevent DDoS Attacks

Table of contents
DDoS attacks can paralyze websites, disrupt online services, and jeopardize businesses’ reputation and financial stability.
This blog will explore the scope of DDoS attacks, recent examples, and most importantly, the best practices to prevent such attacks.
With the best DDoS network security measures in place, any organization can protect themselves from DDoS malware and get ahead of cybercriminals.
Looking to learn more about DNS attacks? Read our sister guide, “How to Prevent DNS Attacks.”
1. What are DDoS Attacks?
DDoS stands for ‘Distributed Denial of Service’. DDoS attacks involve overwhelming a target system with a flood of traffic from multiple sources, rendering it incapable of serving legitimate requests.
These cyberattacks leverage a network of compromised computers, often referred to as a “botnet”, to bombard the target system with traffic spikes.
But, what is denial of service? This refers to how the sheer volume of traffic exhausts the target’s resources, leading to service disruption or a complete outage.
Types of DDoS attacks
Here are some of the most common types of DDoS attacks to be aware of.
- Volumetric attacks: Volumetric DDoS attacks flood the target server or network with a high volume of traffic to consume the available bandwidth and resources, causing the network or system to slow down or crash.
- Protocol attacks: Hackers can exploit weaknesses in network protocols, consuming server resources and rendering them unavailable to legitimate users. Common examples of protocol attacks include TCP SYN floods.
- Application layer attacks: Also known as layer 7 attacks, these target specific services or applications on a server, taking advantage of vulnerabilities in the web application layer to exhaust server resources.
- Low-rate attacks: These attacks are designed to appear as legitimate traffic, bypassing traditional anti-DDoS defense measures. Internet traffic may occur at a low rate, making it difficult to detect and prevent.
- IoT-based attacks: These cyberattacks leverage vulnerabilities in unsecured connected devices such as cameras and routers to overload a targeted system with malicious traffic. An example is the Mirai botnet.
- Spoofed attacks: These attacks use a fake source IP address to hide the attacker’s identity and bypass authentication measures, making it difficult to detect any malicious traffic.
- Application-layer DOS: These attacks target specific applications or services. Common examples include HTTP floods, which overload servers with HTTP requests, and DNS amplification attacks, which exploit vulnerabilities in the domain name system.
A quick DDoS glossary
Before we go any further, here are some keywords that you might hear mentioned frequently in the DDoS landscape.
- Content delivery network (CDN): A group of web servers that cache content geographically near to their users
- Latency: The delay that a user experiences when they run a specific action
- Network bandwidth: The capacity of any given network, and a reflection of its speed and quality
- Load balancers: A technique to distribute network traffic across different resources to process them more efficiently
- Firewalls: A network security system that surveys and monitors traffic
- Web application firewall (WAF): Protects web applications by tracking traffic to and from the Internet
- User Datagram Protocol (UDP): A time-sensitive Internet communication protocol that sometimes falls victim to ‘UDP flood attacks’
- DDOX: Finding someone’s personal details and leaking them
- Internet Control Message Protocol (ICMP): A network layer protocol that can diagnose any communication issues
2. Are DDoS attacks illegal?
DDoS attacks are generally considered illegal in most jurisdictions. These attacks can cause significant harm to targeted systems, networks, and users, disrupt services, and result in financial losses for businesses.
Is DDoS illegal in the US?
In the United States, DDoS attacks are considered cybercrimes and can be prosecuted under the Computer Fraud and Abuse Act (CFAA). The CFAA makes it illegal to intentionally cause damage to a computer or computer network without authorization. DDoS attacks fall under this definition as they aim to disrupt or deny service to legitimate users.
Is DDoSing illegal in the UK?
In the UK, DDoS attacks could lead to a prison sentence or a fine, as the Computer Misuse Act makes it illegal to impair or block access to computer programs and data without prior authorization.
The bottom line
Laws and regulations may vary between countries, so the legality of DDoS attacks may differ depending on the jurisdiction. However, in general, launching or participating in a DDoS attack is considered illegal due to the harm and damage it can cause.
3. What is the scope of DDoS attacks in 2024?
As technology rapidly advances, so do the methods and scale of DDoS attacks. Here are 5 insights to keep in mind for 2024.
- DDoS attacks are on the rise: A study from Cloudflare found that distributed denial of service attacks reached a record high in 2023—and they’ve already jumped by another 50% at the start of this year.
- Organizations are increasingly vigilant: 25% of survey respondents agreed that DDoS attacks formed a part of their companies’ threat outlook for 2023.
- The United States is the main target: Almost half of DDoS attacks are directed at US-based organizations.
- The European Union is also on high alert: Alongside ransomware, DDoS attacks are considered to be one of the greatest cybersecurity threats in the EU.
- Geopolitical conflicts can also lead to more DDoS attacks: A Netscout report has found that DDoS attacks are partly escalating due to global conflicts and political “hacktivism.” For example, we can see this in the DDoS attacks targeting Russia and Ukraine.
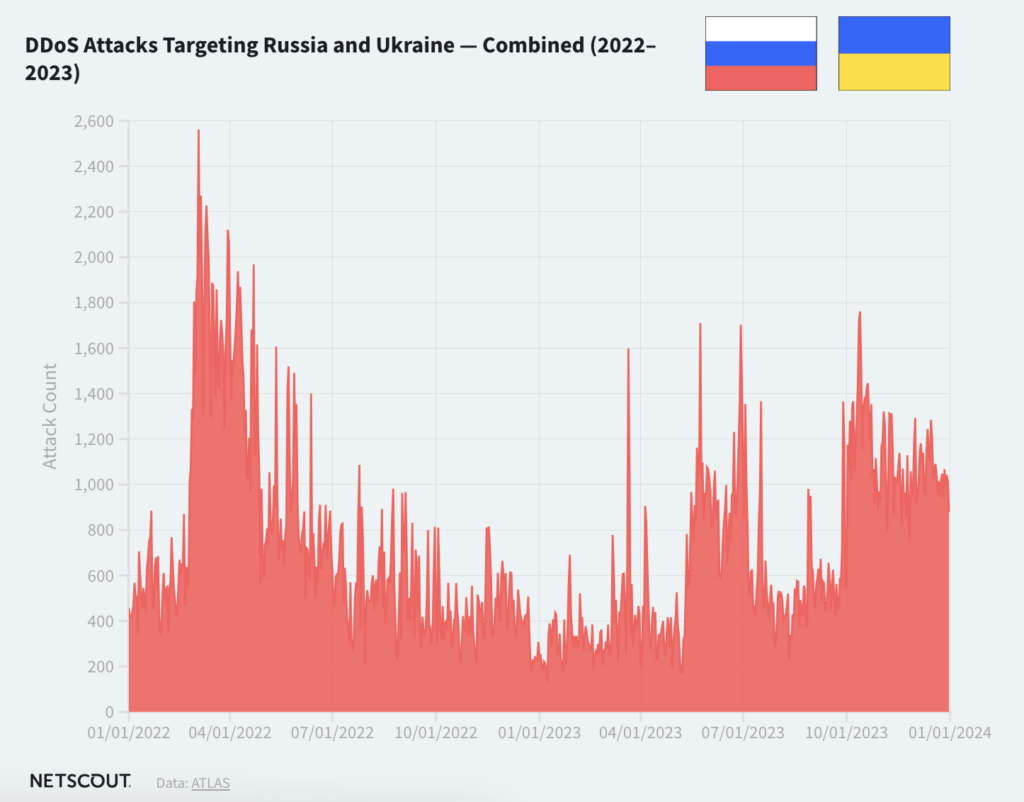
4. What are the consequences of DDoS attacks?
So what happens when you get DDoSed? DDoS attacks can have severe repercussions on organizations, individuals, and the overall digital ecosystem.
Service disruption
The primary impact of a successful DDoS attack is the disruption of online services. This can lead to downtime, making websites and applications inaccessible to legitimate users—affecting the overall user experience.
Financial losses
Downtime resulting from DDoS attacks can translate into significant financial losses for businesses. In addition to direct revenue impact, organizations may also incur additional costs associated with remediation efforts from response teams, legal implications, and reputational damage control.
Reputational damage
The aftermath of a DDoS attack can tarnish an organization’s reputation. Following any issues or blockages, users may perceive the organization as being unreliable, leading to erosion of trust and potential loss of business.
Opportunity costs
Beyond immediate financial implications, DDoS attacks can result in missed business opportunities. Organizations may lose out on potential sales, partnerships, or strategic initiatives due to the unavailability of their online services.
Legal implications
Depending on the nature of the targeted industry and the impact of the attack, organizations may face legal consequences. Regulatory bodies may impose penalties for failing to protect customer data or maintain service availability.
Service degradation
Even if a DDoS attack does not completely disrupt services, it can still lead to significant degradation in service quality. Slow response times, unresponsiveness, and intermittent outages can all result from DDoS attacks.
Psychological impact
DDoS attacks can have a psychological impact on users and employees. Users may feel vulnerable and hesitant to engage with a platform that has been targeted, while employees may experience stress and anxiety when trying to restore services under attack.
5. What are some recent examples of DDoS attacks?
The world has witnessed several high-profile DDoS attacks in recent years, including:
- GitHub: In 2018, GitHub faced a DDoS attack which used an amplification technique to send huge amounts of traffic to their site
- Amazon: In 2020, Amazon Web Services announced that it had to counteract a huge DDoS attack
- Google: In 2023, Google stopped a DDoS attack that was 7.5 times larger than previous attacks on record (see chart below)
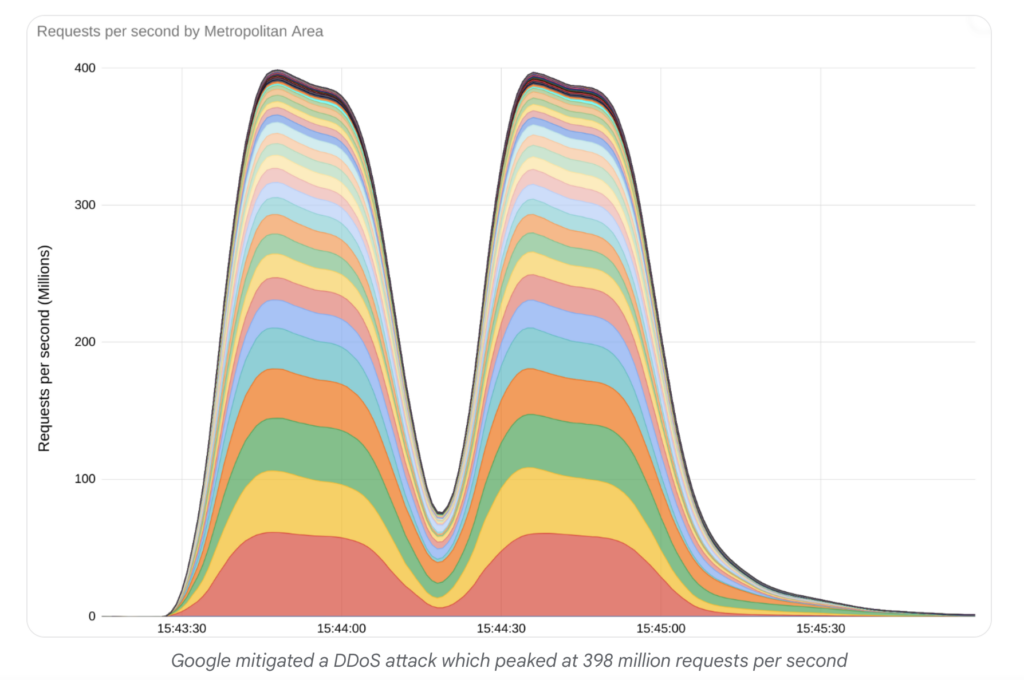
These examples show that any company can face DDoS attacks—no matter how established they are. So, what can protect your network from DoS attacks?
6. How can DDoS attacks be prevented?
What is the best defense against a DDoS attack?
If you’re wondering how to defend against DDoS, here are 7 cybersecurity best practices and anti-DDoS software recommendations to protect any organization.
- Regular network monitoring: Real-time monitoring helps proactively identify and mitigate suspicious traffic patterns.
- Scalable infrastructure: Designing a scalable infrastructure with excess capacity can absorb sudden spikes in traffic and ensure business continuity.
- DDoS mitigation services: Employing professional DDoS mitigation services, such as CybelAngel, allows organizations to leverage the expertise of specialized providers who can monitor web traffic and apply necessary filtering techniques to thwart attacks.
- Traffic rate limiting: Implementing rate-limiting measures detects abnormal traffic patterns and restricts traffic from suspicious sources.
- Application Layer Security: Ensuring robust application layer security prevents attacks targeting vulnerabilities in web applications and APIs.
- Intrusion Prevention Systems (IPS): IPS systems detect and block malicious traffic by inspecting them and comparing them against known attack patterns.
- Incident response planning: Having a well-defined incident response plan enables organizations to mitigate attacks promptly and minimize the impact on services.
So, can you stop a DDoS attack? These measures can certainly make a difference.
Prevention is better than cure, and the best DoS protection strategies will safeguard your organization against external cyber threats.
7. How to recover from a DDoS attack?
What if, in spite of your best efforts, a DDoS response is required?
To recover from a DDoS attack, organizations can take the following steps:
- Analyze and understand the attack: After a DDoS attack, it is essential to analyze the scale, duration, and attack vectors used. This analysis guides the recovery strategy to prevent future attacks.
- Mitigate the attack: Implement measures to mitigate the ongoing attack and minimize its impact. This may involve filtering and blocking malicious traffic, deploying DDoS protection services or solutions, and working with Internet service providers (ISPs) to block traffic originating from the attack.
- Restore services: Once the attack is mitigated, organizations should restore affected services and systems. This may involve checking the integrity of affected systems, repairing any damage caused, and verifying the functionality of associated applications and services.
- Learn and improve: After recovering from a DDoS attack, it is important to conduct a post-incident analysis to identify vulnerabilities, weaknesses, and areas for improvement. This analysis can help organizations enhance their security measures and develop a more robust defense strategy against future network traffic attacks.
It is also crucial for organizations to have proactive measures in place to prevent and mitigate future DDoS attacks. This includes implementing comprehensive DDoS protection solutions, conducting regular security assessments, staying updated with security patches, and educating employees about the risks and signs of DDoS attacks.
Every DDoS attack is unique, and the recovery process may vary based on the specific circumstances. Engaging with cybersecurity professionals, such as CybelAngel, and consulting industry-specific guidelines can provide organizations with tailored guidance for recovery.
8. What can we expect from DDoS attacks in the future?
With the evolution of technology and the increasing number of connected devices, the future of DDoS attacks is likely to witness more sophisticated and large-scale assaults.
How are DDoS attacks related to the Internet of Things (IoT), for example? With more connected devices, the scope and scale for potential DDoS attacks is wider than ever. IoT devices also have weaker cybersecurity protocols, making them easier to exploit.
Artificial intelligence and machine learning can also play a role. For instance, AI algorithms could be used to analyze and control more effective DDoS attacks, or to adapt the attack strategy depending on the defences in place.
Conclusion
By understanding the nature of DDoS attacks and implementing proactive prevention measures, organizations can safeguard their online infrastructure.
Following the best practices discussed in this blog and staying informed about emerging attack techniques will be instrumental in mitigating the risk of DDoS attacks and ensuring a secure online environment for businesses and users alike.
Interested in our threat note analysis of unrelenting DDoS attacks carried out by Anonymous Sudan? You might like our latest guide, ‘Anonymous Sudan’s Post Arrest Cyber Chaos [A Threat Note Guide].’