Our Investigation of the CNSS Data Leak [Flash Report]

Table of contents
On April 8th, 2025, a threat actor operating under the alias “Jabaroot” surfaced on BreachForums with a bold claim. In a thread titled “Morocco National Social Security Fund (CNSS) – FULL DATABASE LEAKED 2025”, the actor allegedly released sensitive data exfiltrated from Morocco’s national social security fund. The leak reportedly includes financial information tied to both Moroccan companies and their employees—and alarmingly, much of the data appears to have been left exposed in clear text on compromised servers.
What has been happening at CNSS?
A massive data breach at Morocco’s National Social Security Fund (CNSS) has exposed a trove of sensitive information. The leaked dataset includes over 53,000 PDF files and two CSV files containing detailed records of nearly 500,000 companies and close to 2 million employees. The documents range from company affiliation details to individual employee identification numbers, salaries, and contact information—much of it dated as recently as November 2024.
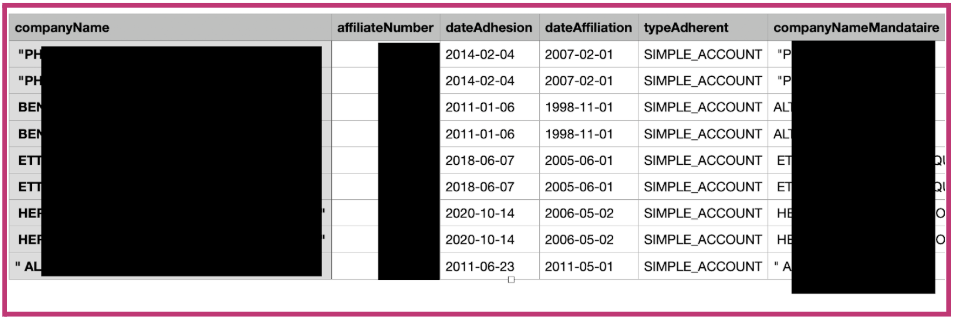
The breach appears to involve administrative and financial data, including bank details and personal identifiers, with PDFs revealing full employee names and declared salaries. While the data has been publicly posted and the attack claimed, the method of intrusion remains unclear. Early speculation ranges from a zero-day exploit to a compromise via third-party software, possibly involving Oracle platforms.
A threat actor profile: Who is Jabaroot?
The alias Jabaroot first appeared on the cybercrime forum BreachForums and on Telegram on April 8th, 2025. Since then, the threat actor’s Telegram channel [hxxps://t[.]me/JabarootDZ/] has quickly gained traction, amassing over 8,000 subscribers at the time of writing. So far, Jabaroot has published only a single thread on BreachForums—the one claiming responsibility for the CNSS data leak affecting Morocco’s national social security fund.
fresh sample.
While little is known about the actor behind the alias, open-source intelligence (OSINT) work by the Hack4Living team has shed some light on their potential identity. On April 8th, 2025, several files posted to Jabaroot’s Telegram channel were observed as having been forwarded by a user named “3N16M4”—a possible operational security lapse. Interestingly, this forwarding indicator disappeared from the same files the very next day, suggesting that the attacker may have accidentally shared content from a personal account instead of the anonymized one created for leaking the data.
Further pivots from this username led investigators to credentials linked to “3N16M4” across multiple code-sharing platforms (like GitHub) and Capture The Flag (CTF) competition sites. While we have opted not to publicly share the full personal details uncovered, OSINT analysis strongly suggests that the person behind Jabaroot may be a computer engineer currently based in Germany. Although their exact origin remains unconfirmed, the actor has self-identified as being from Tunisia in a Telegram profile.
It’s important to note that this information is based solely on open-source research and should be treated with caution, as attribution in cyber investigations can be notoriously complex and prone to error—especially in the early stages.
A Breach Born of Geopolitical Tensions
According to statements made by the threat actor on Telegram, the CNSS breach appears to be politically motivated. Jabaroot claims the attack was carried out as retaliation for a previous compromise of the Algerian Press Service (APS) Twitter account—an incident attributed to Moroccan-affiliated threat actors. In that incident, the APS account was renamed “Sahara Marocain”, referencing the long-standing geopolitical dispute between Morocco and Algeria over the Western Sahara region. The Twitter account was later suspended following widespread media coverage.
Shortly after announcing the CNSS breach on Telegram, Jabaroot shared additional content, including a screenshot allegedly showing the defacement of the Moroccan Ministry of Labour’s website. The actor stated this defacement was part of a broader campaign to respond to what they described as Moroccan-led online operations targeting Algerian institutions. As of this writing, the official website of the Moroccan Ministry of Labour appears to be suspended.
This activity underscores how cyberattacks are increasingly being used as tools of political messaging, blurring the lines between hacktivism and state-aligned retaliation in an already volatile regional context.
This marks only the initial phase of our investigation, and we are committed to closely monitoring the situation while delving deeper into ongoing developments.

