Your digital security is only as good as your partners’ digital security. Your IT vendors, manufacturers, suppliers, and service providers all pose some risk to your network.
Asset Discovery and Monitoring, the Foundation for CybelAngel EASMX
Stay ahead of cyber criminals with the one ADM solution that discovers assets using the same ‘outside-in’ perspective. CybelAngel ADM is the only asset discovery solution powered by multiple search methodologies to provide an exhaustive, real-time, living map of your entire external digital landscape so you can uncover security flaws, evaluate, and address vulnerabilities before systems can be compromised.
Protect Your External Attack Surface in Four Easy Steps
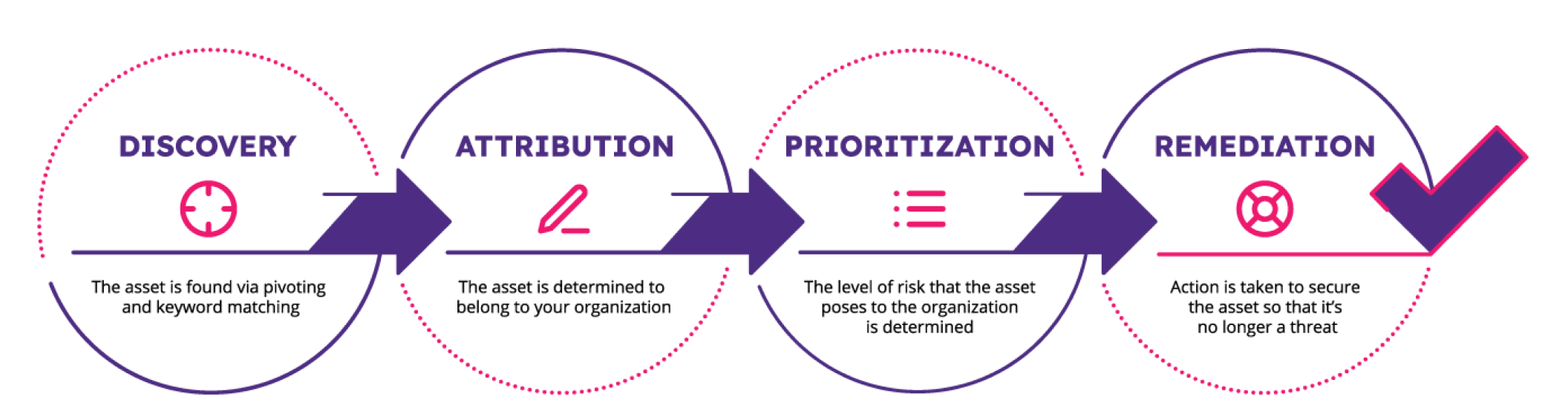
How it Works
CybelAngel’s Asset Discovery and Monitoring is the only solution of its kind to combine two complementary discovery techniques to enable the most exhaustive mapping of unknown external assets. This combination technology searches deeper and broader to find shadow IT that other solutions can’t.
Pivoting:
- Finds the “owned unknowns” by starting from a list of known assets to uncover shadow services and assets deployed without the knowledge of your IT or security departments.
Keyword matching:
- Finds the “unknown unknowns,” usually belonging to external parties in your ecosystem or supply chain such as suppliers, partners, contractors or service providers.

Complete
CybelAngel’s advanced search technology offers the most exhaustive asset search available.

Relentless
Continuous monitoring means you find internet-facing assets within 24 hours of exposure so you find it before the bad actors do.

Prioritized
Eliminate alert fatigue by letting CybelAngel’s AI and experienced analyst team sift mountains into meaning to provide contextualized, assessed and severity-scored findings.
Actionable
Each incident report includes detailed asset and threat information so you have the full context needed for faster response and remediation.
Cutting-edge features for advanced analytics
Powerful, self-serve product and growth analytics to help you convert, engage, and retain more users. Trusted by over 4,000 startups.
Asset Inventory
The first step in protecting it, is to know that it exists. A detailed asset inventory is the foundation of a strong security posture.
Third-Party Security
Your company systems are only as safe as the systems it and its employees interact with. Secure your supply chain ecosystem by identifying exposures before they can escalate into issues.
Proactive Monitoring
Continuously updated every 24 hours, your security team always has the accurate and timely information needed to immediately respond as a threat arises.
Secure M&A Activity
Uncover potential deal breakers with real-life cybersecurity due diligence pre-acquisition, then maintain full visibility to ensure continuous coverage during the ‘cyber-vulnerable’ systems integration process after the deal is sealed.
Built on trust since 2013
We take pride in protecting a global network of 100’s of enterprise clients.




